Enhanced Discovery and Resolution, or more commonly known as XDR, serves as a revolutionary model in cybersecurity. It works by combining multiple security apparatuses into a solitary system, thus uplifting the ability for threat detections and subsequent responses. Unlike the standard perimeter-fixed defenses, XDR offers a more exhaustive and anticipatory method towards cyber defense.
The scope of XDR's defensive structure is all-inclusive, incorporating a wide spectrum of tools and systems such as protection of endpoints, securities within networks, emails, and cloud services. It works by amassing and juxtaposing data from varied sources. Leveraging state-of-the-art analytics and artificial intelligence, it actively observes, scrutinizes, and tackles threats as they occur in real-time.
Below is a typical illustration of the functioning of XDR in Python code format:
<code class="language-python">class XDR:
def __init__(self, protection_endpoints, security_networks, security_emails, security_clouds):
self.protection_endpoints = protection_endpoints
self.security_networks = security_networks
self.security_emails = security_emails
self.security_clouds = security_clouds
def gather_data(self):
# Accumulating data from diverse sources
pool = []
pool.append(self.protection_endpoints.gather_data())
pool.append(self.security_networks.gather_data())
pool.append(self.security_emails.gather_data())
pool.append(self.security_clouds.gather_data())
return pool
def dissect_data(self, pool):
# Utilize superior analytics and AI to perceive threats
perils = []
for p in pool:
perils.extend(self.dissect(p))
return perils
def confront_perils(self, perils):
# Encounter detected perils in real-time
for peril in perils:
self.confront(peril)</code>
This code signifies the XDR entity as a single security framework. It function by accumulating data from assorted sources (endpoint, network, email, and cloud protections), studying the data to identify threats, and subsequently counter the recognized threats in real-time.
Here's a comparative analysis of the traditional security procedures and XDR's approach:
| Conventional Security Protocols | Strategy of XDR |
|---|---|
| Utilizes multiple unrelated security products | Integrates varied security apparatus within a single system |
| Counters cybersecurity re-actively | Predictive method towards cybersecurity |
| Restricted insight and non-correlated across security products | Comprehensive understanding and interlinked across diverse security products |
| Detection and tackling threats manually | Threat identification and resolution automated via hi-tech analytics and AI |
In essence, XDR symbolizes a holistic, all-inclusive, and anticipatory stance towards cyberspace security. It supersedes orthodox security mechanisms by enhancing threat detection, and responses through the automation of processes using superior analytics and AI. This leads to a more competent and effectual resolution for cybersecurity.
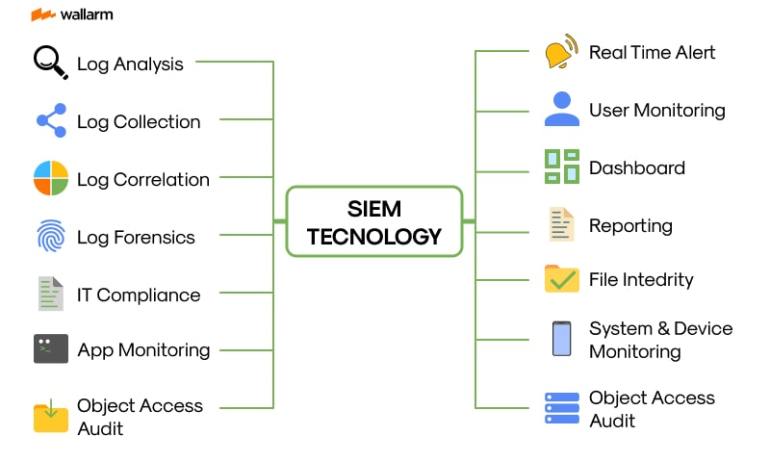
Unravelling SIEM: Harmonising Protective Analytics and Event Watchfulness
The integration of SIEM, an exceptional blend of Safety Analytics Management (SAM) and Protective Event Supervision (PES), carves a tactical path in the landscape of security control. This inclusive notion facilitates a holistic grasp of an enterprise's cybersecurity strategies by effectively compiling, assessing, and disclosing security-relevant data from a range of sources in a systematic manner.
To enrich the comprehension of SIEM, let's disassemble it into its core components:

-
Safety Analytics Management (SAM): This procedure is essential for capturing, preserving, and analysing log data derived from a myriad of sources entrenched in the IT framework. The information is culled from network mechanisms, operational systems, software suites, and safeguarding instruments like firewall and anti-malware programs.
-
Protective Event Supervision (PES): PES rotates around real-time monitoring, consolidating related incidents, triggering alerts, and dashboard evaluations. It endows the IT sector with indispensable tools for instantaneous event response.
When SAM and PES amalgamate, they deliver an extensive outlook of an enterprise's all-embracing security position, laying the groundwork for identifying patterns and templates hinting at probable security violations or intrusions.
The ensuing Python code illustrates how log data can be seized in a SIEM context:
<code class="language-python">import logging # Create a custom logger custom_logger = logging.getLogger(__name__) # Establish handlers screen_handler = logging.StreamHandler() file_handler = logging.FileHandler('logfile.log') screen_handler.setLevel(logging.WARNING) file_handler.setLevel(logging.ERROR) # Define formatters and attach them to handlers screen_format = logging.Formatter('%(name)s - %(levelname)s - %(message)s') file_handler.setFormatter(screen_format) screen_handler.setFormatter(screen_format) # Add handlers to the logger custom_logger.addHandler(screen_handler) custom_logger.addHandler(file_handler) custom_logger.warning('Log Note: Warning detected') custom_logger.error('Log Note: Error noticed')</code>
In this instance, the logger records operations about warnings and errors, which are later evaluated within the SIEM framework.
This comparison matrix highlights the central functionalities of SIEM:
| Features | Meaning |
|---|---|
| Log generation | Accumulates data from diverse inputs within the IT surroundings |
| Persistent scrutiny | Executes continual system inspection to identify potential hazards |
| Incident fusion | Merges disparate events to emphasize patterns indicating security deviations |
| Alert initiation | Disseminates a heads-up to the IT crew upon spotting a likely security breach |
| Graphical assessment | Provides a pictorial synopsis of the security strategies for easy understanding |
| Emergency handling | Affords tools for the IT squad to manage a security breach |
In summary, for any enterprise zealous about adopting robust security protocols, SIEM proves to be an invaluable asset. Offering a comprehensive inward look into security norms, SIEM eases the process of threat detection and enables professionals to tackle security issues promptly. The ensuing chapter will juxtapose SIEM with another protective tactic, Expanded Detection and Response (XDR), to assist you in identifying their disparities and choosing the option that aligns best with your organisational needs.
Understanding the Rise of XDR: Distinctness from SIEM
Within the cybersecurity terrain, pivotal solutions such as Extended Detection and Response (XDR) and Security Information and Event Management (SIEM) reside in parallel dimensions, exhibiting unique traits. Specifically, these two heavenlies portray differing operational tactics, application prospects, and the extent of their security circumference. Let's delve into the basic disparities that underscore the contrasts between XDR and SIEM.

-
Harmonized Security Data Collation and Review
SIEM: A SIEM structure methodically observes and dissects log metadata pulled from diverse components dwelling in an organization's virtual sphere. This range includes servers, databases, software, and others, while the examination uncovers potential cybersecurity gaps.
<code class="language-python"># SIEM data gathering exemplification
def aggregate_data(source):
log_information = source.obtain_log_info()
analyze_information(log_information)</code>
XDR: Overcoming the confined use of log details, XDR uniformly amalgamates security info from a myriad of operations such as terminal points, internet endeavors, servers, cloud-triggered occurrences, and all email-related interactions. This bestows a more comprehensive comprehension of the security perimeter.
<code class="language-python"># XDR data amalgamation exemplification
def compile_data(sources):
for source in sources:
details = source.gather_details()
sync_data(details)</code>
-
Identifying Subtle Threats and Tackling Them
SIEM: With the central objective to pinpoint hazards, SIEM components actively explore for plausible risks following established standards, thus proactively alerting the security staff upon the discovery of odd patterns. However, it falls short when it comes to automatic threat averting operations.
<code class="language-python"># SIEM threat pinpointing exemplification
def point_out_hazard(details):
if details.comply_with_standards():
alert_security(details)</code>
XDR: Transcending mere hazard identification, XDR also curtails threats. It leverages sophisticated analytics and cutting-edge machine intelligence to expose concealed hazards and concurrently equips itself to independently manage threats, mitigating or expunging them.
<code class="language-python"># XDR hazard curtailment exemplification
def detect_and_tackle_hazard(details):
if details.conform_to_standards():
suggested_remedy = propose_solution(details)
implement_suggested_remedy(suggested_remedy)</code>
-
Broad yet In-depth Protection Strategy
SIEM: SIEM solutions deliver widespread safety, encapsulating the entire IT architecture. Their weakness dwells in the relatively shallow threat detection primarily rooted in log data reliance.
XDR: Conversely, XDR solutions fortify the security course by putting forth an intricate, deep-seated shielding standpoint. They comb through various security strata, scrutinizing each for superior hazard identification and alleviating actions.
-
Streamlining Processes
SIEM: SIEM instruments can be complex to install and maintain, mandating competent experts and substantial resources for efficient cyber incident management and risk alleviation.
XDR: XDR instruments, conceived for enhanced user-friendliness, computerize several procedures, consequently alleviating the burden on the security team and introducing a more easily manageable method towards digital safety crises.
It's apparent that both XDR and SIEM contribute to upholding exhaustive digital defense. However, comprehending their disparities in data amalgamation, hazard identification, counteraction tactics, protection gamut, and process facilitation can assist organizations in selecting the most suitable tool that aligns with their distinct requirements.
Benefits of Preferring XDR to SIEM
The persistent and rapidly changing world of cybersecurity provokes continuous deliberation on the comparative edge of XDR (Extended Detection and Response) and SIEM (Security Information and Event Management). Both botanicals exhibit noteworthy value, but the superiorities of XDR often make it more desirable for diverse enterprises.
`
`
Integrated Overview:
One of the shining features of XDR is its provision of a bird's eye view concerning an enterprise's cybersecurity health. It intermingles an array of security technologies onto a singular platform, fostering an integrated perspective of endpoints, infrastructure, servers and cloud payloads. This unification paves the way for more potent identification and countering of threats.
<code class="language-python"># Unveiling XDR's unified view
class XDR:
def __init__(self):
self.endpoints = []
self.networks = []
self.servers = []
self.cloud_workloads = []
def include_endpoint(self, endpoint):
self.endpoints.append(endpoint)
def include_network(self, network):
self.networks.append(network)
def include_server(self, server):
self.servers.append(server)
def include_cloud_workload(self, cloud_workload):
self.cloud_workloads.append(cloud_workload)</code>
Auto-Reaction:
XDR systems showcase their advanced engineering by not merely identifying the threats but executing the responses autonomously. This gives XDR an upper hand over SIEM systems, which are mostly preoccupied with threat identification and necessitate human interference for generating a response.
<code class="language-python"># Behold XDR's autonomous reaction
class XDR:
def identify_threat(self, threat):
# Insert identification logic here
pass
def execute_response(self, threat):
# Insert autonomous response logic here
pass</code>
Refined Threat Insight:
Thanks to first-rate analytics and machine learning, XDR solutions gain superior insights into potential threats by discerning patterns and anomalies. This results in more precise threat identification and minimizes false alerts compared to SIEM systems.
Streamlined Supervision:
XDR enables companies to command their security operations from a single suite, smoothing the processes and drastically cutting down the reliance on multiple, unconnected security tools.
| Characteristic | XDR | SIEM |
|---|---|---|
| Unified Overview | Yes | No |
| Autonomic Response | Yes | No |
| High-grade Threat Insight | Yes | No |
| Streamlined Supervision | Yes | No |
Economical:
XDR might appear more expensive than SIEM initially, but when you account for its lifetime value, it often comes out as a more economical alternative. The reason being, it shrinks the need for numerous security tools, and the corresponding expenses related to licenses, integration, and supervision.
In a nutshell, XDR outshines SIEM in numerous ways – unified overview, autonomous response, high-grade threat insights, streamlined supervision and overall better value for money. However, the final choice between XDR or SIEM should ideally be tailored to an organization's specific requirements and available resources.
Revisiting the Decision: Situations where SIEM Overpowers XDR
Even though Extended Detection and Response (XDR) is rapidly gaining popularity in the cybersecurity domain due to its cutting-edge abilities, there are particular circumstances where Security Information and Event Management (SIEM) trumps XDR. This chapter focuses on such scenarios, imparting an unbiased insight into the proverbial XDR versus SIEM conflict.
Dense and Widespread IT Infrastructure
SIEM tools display notable efficacy in intricate and large-scale IT ecosystems. Designed to amass and examine log data from a multitude of sources like servers, network appliances, databases, and apps, SIEM stands as a fitting option for corporations boasting varied IT infrastructures.
<code class="language-python"># An illustration of SIEM gathering log data
def accrue_log_info(src):
register_info = src.retrieve_log_info()
return register_info</code>
Regulatory Adherence Necessities
Having been in existence longer, SIEM tools are frequently related to regulatory adherence mandates. They offer all-encompassing log control and report generation features that aid organizations in adhering to regulatory norms such as GDPR (General Data Protection Regulation), HIPAA (Health Insurance Portability and Accountability Act), and PCI DSS (Payment Card Industry Data Security Standard).
| Protocol Adherence Requirement | SIEM Proficiency |
|---|---|
| GDPR | Impact appraisals related to data protection |
| HIPAA | Control audits |
| PCI DSS | Monitoring and tracking all network resource and cardholder data access |
Detailed Forensic Audit
SIEM provides exhaustive forensic audit faculties. They can construct an extensive chronology of events leading to a security breach which is instrumental in probing and amending the issue. Such granular detail is not always accessible with XDR tools.
Fiscal Constraints
Particularly for smaller organizations and mid-scale businesses facing budget limitations, SIEM can prove more economically viable. XDR tools may provide superior features, but they also carry a more substantial price tag. Conversely, SIEM offers indispensable security aspects at a more reasonable cost.
Pre-established Security Setup
When entities already own a sturdy security setup, comprising firewall systems, intrusion detection setups (IDS), and intrusion prevention mechanisms (IPS), opting for a SIEM tool could be the more rational option. SIEM has the capacity to meld with these pre-existing systems to afford a consolidated perspective of security occurrences.
To sum up, though XDR presents superior threat identification and response mechanisms, there remain scenarios where SIEM holds dominance. Variables such as complexity in IT ecosystems, regulatory adherence prerequisites, the necessity for detailed forensic audits, budgetary restrictions, and pre-existing security setups can all sway the decision between XDR and SIEM. As such, corporations should meticulously gauge their specific requirements and circumstances prior to making a final decision.
The Journey from SIEM to XDR: An In-depth Handbook
Transitioning from Security Information and Event Management (SIEM) to Extended Detection and Response (XDR) is indeed a noteworthy shift, demanding an insightful and discerning approach. This chapter aims to guide you through this adaptation, providing key insights and advice for a smooth shift into XDR.
-
Appreciating the Need for a Transformation
Before stepping onto this pathway of transformation, it's crucial to embrace the motives leading to it. While SIEM solutions, which have shored up countless businesses' security infrastructures in the past, have provided essential views into potential hazards, the fast-paced advancement of cybersecurity has exposed some inherent limitations of SIEM, pushing XDR into the spotlight as a fitting replacement. XDR equips a more expansive viewpoint of the threat environment, merging numerous security tools into a synergistic platform.
-
Strategizing for the Transition
A critical part of moving from SIEM to XDR involves conscientious planning. This comprises an assessment of your existing security architecture, identifying areas of improvement, and understanding how XDR can effectively address these gaps. Of equal importance is predicting the likely impacts on your organization, including workflow alterations and potential periods of inactivity.
Following is a simple comparison chart illustrating the differences between SIEM and XDR:
| SIEM | XDR |
|---|---|
| Primarily engaged in log management and reconciliation | Provides a holistic view of threats |
| Demands human intervention for risk mitigation | Enables automated detection and response to threats |
| Limited compatibility with various security tools | Effortlessly merges with a spectrum of security products |
-
Introducing XDR
On crafting your transition strategy, the next step is the assimilation of the XDR solution. This entails installing the XDR tool, integrating it with your current security protocols, and customizing it according to your specific needs.
Following is a simple code snippet exemplifying the integration of XDR with a security tool:
<code class="language-python"># Bring in the XDR module
import xdr
# Create an instance of the XDR class
xdr_instance = xdr.XDR()
# Couple XDR with a security tool
xdr_instance.integrate('security_tool')
# Customize XDR
xdr_instance.configure({
'threat_detection': True,
'automated_response': True
})</code>
-
Training and Assimilation
After XDR's incorporation, it's vital to train your staff on its utilization effectively. This involves understanding the capabilities and features of XDR, along with analyzing the data it provides.
-
Persistent Monitoring and Improvement
One key point to remember is that the journey from SIEM to XDR is not a one-time event. It's imperative to constantly monitor the performance of your XDR solution, making corrections as needed, assuring it aligns with your security requirements.
In conclusion, the progression from SIEM to XDR is a considerable challenge, but with careful planning and implementation, it can significantly elevate your organization's security posture. Getting a handle on the variances between SIEM and XDR, creating your transitory strategy, deploying the XDR solution, training your staff, and ceaselessly overseeing and refining your security infrastructure are the steps to ensuring a smooth, beneficial transition.
The Pioneers of Digital Protection: Scrutinizing XDR and SIEM Software Titans
Venturing into the vast expanse of cybersecurity, XDR and SIEM technologies stand as grand knights, crafting resilient bulwarks of defense. These digital guardians are engineered with painstaking precision to guard and identify online threats, while disabling them in a blink of an eye, thus securing your valuable online resources. In this enlightening chapter, we critically examine the cream of the crop in the XDR and SIEM landscape, juxtaposing their functionalities, merits, and overall prowess.
1. XDR Software:
a. Acknowledging Palo Alto Networks' Cortex XDR:
Acknowledged as a trailblazer in the XDR landscape, Cortex XDR unfurls a blanket of security by integrating data from diverse platforms like networks, endpoints, and the cloud to counter complex digital attacks. This tool deploys sophisticated Artificial Intelligence and machine learning strategies for efficient automation and threat interception.
<code class="language-python">class CortexXDR:
def __init__(self):
self.network_security = True
self.endpoint_protection = True
self.cloud_defense = True
self.AI_implementation = True
self.machine_learning_use = True</code>
`
`
b. Recognizing Microsoft's Defender for Endpoint:
Regarded as a powerful tool for commercial usage, Microsoft's Defender for Endpoint is a next-gen endpoint security interface designed to safeguard businesses, while also identifying, scrutinizing, and neutralizing sophisticated online threats.
<code class="language-python">class DefenderEndpoint:
def __init__(self):
self.threat_guard = True
self.threat_diagnostics = True
self.threat_analysis = True
self.threat_counteraction = True</code>
2. SIEM Software:
a. Spotlight on Splunk:
As a front runner in the SIEM software field, Splunk establishes seamless transparency across an enterprise's IT structure. It equips enhanced analytics, visual illustrations and timely notifications for proactive threat scanning and oversight.
<code class="language-python">class Splunk:
def __init__(self):
self.operational_clarity = True
self.improved_analytics = True
self.alerting_feature = True</code>
b. Honoring LogRhythm:
The software, LogRhythm executes as a complete SIEM package, merging efficient log control with network-based and endpoint monitoring for heightened security.
<code class="language-python">class LogRhythm:
def __init__(self):
self.log_oversight = True
self.network_watch = True
self.endpoint_watch = True
self.deep_dive_threat_identification = True</code>
Contrasting XDR and SIEM Software:
| Competencies | Cortex XDR (Palo Alto Networks) | Defender for Endpoint (Microsoft) | Splunk | LogRhythm |
|---|---|---|---|---|
| Defense for Network | Yes | Yes | Yes | Yes |
| Protection at Endpoints | Yes | Yes | No | Yes |
| Cloud Security | Yes | Yes | Yes | Yes |
| Execution of AI & Machine Learning | Yes | No | Yes | Yes |
| Round the Clock Surveillance | Yes | Yes | Yes | Yes |
| Elevated Analytics | Yes | Yes | Yes | Yes |
| Warning Systems | Yes | Yes | Yes | Yes |
In the final remarks, it can be stated that both XDR and SIEM systems furnish robust digital defenses. The decision between these two forms is reliant on your unique requirements and how your IT infrastructure is constructed. While XDR frameworks propose consolidated and automatic alternatives, SIEM systems provide the luxury of in-depth control over your digital security.
如有侵权请联系:admin#unsafe.sh