
2023-11-1 01:18:47 Author: securityboulevard.com(查看原文) 阅读量:3 收藏
3 things to consider before you develop a custom risk dashboard for your software supply chain
TL;DR – BUY
Seriously though. If you’re contemplating a build vs. buy decision, buying gets you a working DevSecOps dashboard sooner and usually at lower cost than building something in house.
And whether you build or buy a dashboard solution, this article will help you understand how to ensure your entire development team embraces it.
A DevSecOps risk dashboard — good to have and hard to build
Gartner predicts that by 2026, 70% of platform teams will integrate application security tools to scale DevSecOps practices. In order to make this happen, many organizations begin by creating a DevSecOps risk dashboard.
The objective is to integrate information from a portfolio of security tools into a single dashboard, making the risks more visible and actionable to security and development teams. It’s a worthy goal, and the strategic question for many organizations is whether to build it in house or license a commercial DevSecOps dashboard. Here are three thoughts to help you make that decision.
1. Buying saves money and makes a more immediate impact
The software supply chain – from requirements to deployment – is extensive and dynamic. It can take several person-years to design and build a portal and integrate data from the team’s DevSec tooling into it. Trying to unify security risk data from your various systems into a coherent dashboard is tedious and error prone. Most companies we talk to find it difficult to integrate even just a few of their security systems.
If you succeed in building your own risk dashboard, you’re now faced with expensive annual maintenance. As your DevSec tooling and new vulnerabilities and threats evolve, so must your dashboard. This costs you more development time and money.
Subscribing to a commercial DevSecOps dashboard and configuring it to connect and integrate your security tooling is the more cost- and time-efficient way to go versus coding your own. There are plenty of solid DevSecOps dashboards on the market (we’re partial to OX Security of course). Besides saving money, buying gets you a solution immediately, thus improving your security ASAP rather than waiting until after months of custom development.
2. Avoid the “low signal-to-noise” trap
Whether you build or buy, you definitely want to avoid the low signal-to-noise trap. Security systems generate a lot of risk alerts. It’s not uncommon to see thousands of risks raised at any given moment across the software supply chain. There’s so much risk alert noise in fact, that developers often tune them all out. If you don’t solve this problem in your dashboard, your initiative is likely to fail.
It’s a hard problem to solve. After you overcome the challenge of harmonizing risk data from multiple systems, formats, and terminology, you can deduplicate risks and sort them by severity. But that usually only reduces a list of thousands of issues down to a list of hundreds. Several hundred is still a big number for your engineers, so you have to do even more to increase your “signal-to-noise ratio.”
OX Security accomplishes this via advanced, automatic issue prioritization. Its advanced technology can tell the difference between a live attack kill chain (i.e., a vulnerability with a direct path to exploitation in your system) versus less-critical “good hygiene” issues. This ability helps your development team know where to focus:
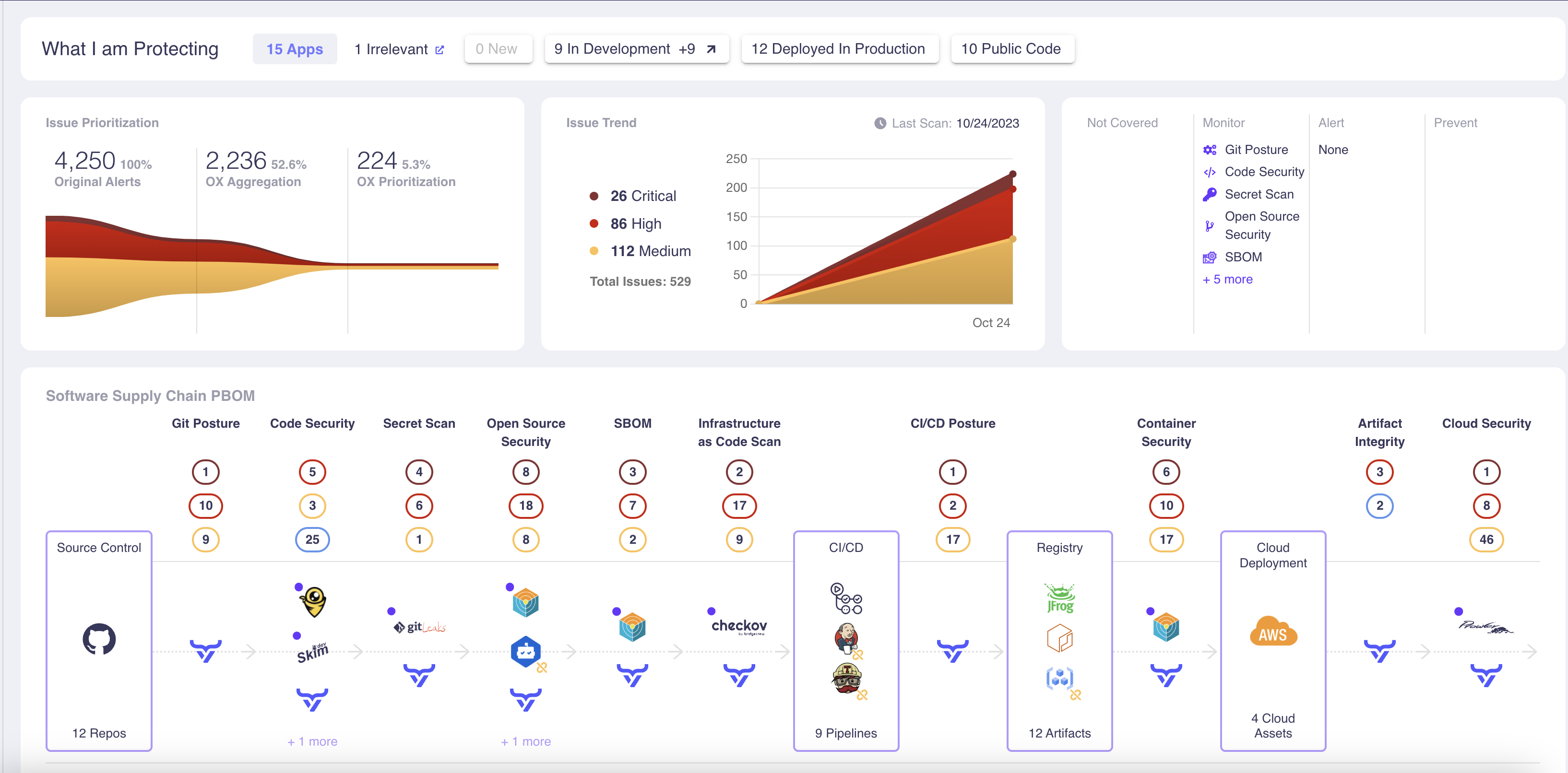
3. Win your developers over with context and a frictionless experience
If, like OX Security, your DevSecOps dashboard does a good job of prioritizing issues for developers, the next task is to help them resolve the issues. A good developer experience that builds trust and reduces friction for developers is a very important feature of a successful DevSecOps dashboard.
How to assign: Many dashboards notify developers of issues via emails or popup messages in their IDEs. Coming from a development background, we know that while focused on engineering tasks, the last thing needed is more emails coming in about security alerts. We also don’t want to see pop-ups within our IDE. We simply don’t want anything that is outside of our normal way of completing engineering tasks. Ideally, your DevSecOps dashboard works within your existing developer workflows (e.g., using the same mechanism for engineering ticket assignment and scheduling).
When to assign: You also want to assign issues revealed by the dashboard in a timely way. As new prioritized issues are raised by the dashboard, try and assign them in real time. Spending two minutes right now while the code is still fresh in someone’s head is much easier than spending more time a few weeks afterwards because the engineer has to re-familiarize themselves with the code they wrote.
What to assign: It is very important for developers to know exactly why they’re working on something. If your dashboard is assigning work by generating Jira tickets, it must give the developer context that makes it clear why the issue matters and why they should spend time resolving it. If possible, it should also communicate a best practice recommendation for resolving the issue. Don’t make your developers reinvent the wheel!
In summary
If you urgently need a DevSecOps dashboard to help secure your software supply chain, then buying a commercial solution is the fastest and most economical path to a solution.
And don’t underestimate the amount of development that a successful DevSecOps risk dashboard requires. It goes far beyond just integrating risk data into a central portal. It must help engineering improve the security of the software supply chain by also:
- Prioritizing security issues — active kill chains vs. hygiene issues
- Integrating with developer processes and technologies
- Assigning issues in real-time as code is created
- Providing context to developers – why an issue is important to resolve and recommendations for resolving it.
OX Security gives you all of this, and it’s one of the reasons Gartner named OX Security a “2023 Cool Vendor.”
We invite you to give OX Security a try. You can do that for free, and also be up and running within minutes by simply connecting it to your development and AppSec infrastructure.
The post DevSecOps Dashboard – Build vs. Buy? appeared first on OX Security.
*** This is a Security Bloggers Network syndicated blog from OX Security authored by William Penfield. Read the original post at: https://www.ox.security/devsecops-dashboard-build-or-buy/
如有侵权请联系:admin#unsafe.sh
