
2023-11-5 15:20:13 Author: securityboulevard.com(查看原文) 阅读量:10 收藏
Introduction to DDoS Threats
An understanding of DDoS threats begins with understanding the basics of DDoS attacks. DDoS attacks are coordinated attempts to flood a network or service with excessive traffic, causing disruption or complete unavailability. Moreover, small businesses are increasingly at risk, as they often lack the robust defenses that larger corporations might have against such threats.
Additionally, DDoS attacks can range from simple annoyances to severe incidents that can cripple operations, lead to data breaches, and tarnish a business’s reputation. For small businesses, the real-world impact is significant; a successful attack can mean lost revenue, compromised customer trust, and potentially devastating recovery costs.
DDoS Threats Attack Any Industry
The image below captures the indiscriminate threat of DDoS attacks, which can target any industry. It showcases a diverse array of sectors—from healthcare to finance, e-commerce to education—each represented by an icon within a network, symbolizing their connectivity and vulnerability. The encircling arrows and disruptive patterns signify the relentless and unbiased nature of DDoS attacks, serving as a stark reminder that no sector is immune. This visual underscores the critical need for businesses of all types to adopt comprehensive DDoS protection strategies.
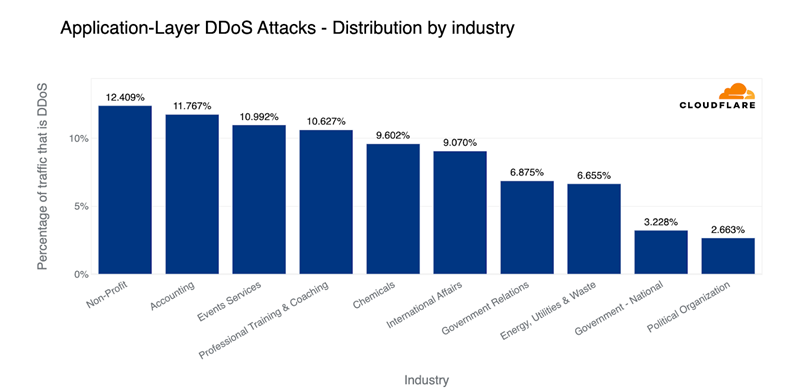
Source: DDoS threat report for 2023 Q1 (cloudflare.com)
Therefore, recognizing the gravity of these threats is the first step in developing a strong defense. It’s not just about technology; it’s about understanding the landscape of digital threats and preparing to counteract them effectively.
How can I protect my business from a DDoS Attack?
– Start by assessing your current cybersecurity posture to identify vulnerabilities.
– Educate your team on DDoS threats and ensure they understand the response protocols.
– Invest in robust DDoS protection solutions tailored to your business needs, incorporating both hardware and cloud-based defenses.
– Implement security best practices, such as regular updates, patch management, and network redundancy.
– Regularly test your system’s resilience with DDoS simulations.
– Stay updated on the latest DDoS trends and technologies, and continuously review and adapt your security measures.
A proactive, informed approach is key to safeguarding your business against DDoS disruptions.
Comprehensive DDoS Mitigation Strategies
In this section, we delve into the key components of an effective DDoS protection plan, as illustrated by the accompanying flowchart.
1. Detection: The first line of defense is the ability to detect a DDoS attack. This involves continuous traffic analysis to identify any unusual spikes or patterns that may signify an attack.
2. Response Activation: Upon detection, an immediate alert triggers the response protocol. This rapid activation is crucial to minimize potential damage.
3. Immediate Mitigation: Employing immediate mitigation techniques, such as rate limiting or traffic filtering, helps to curb the attack by blocking malicious traffic while allowing legitimate users access.
4. Assess and Adapt: After the initial response, it’s vital to assess the attack’s nature and adapt the mitigation strategies accordingly. This may involve updating rules or filters to target the specific characteristics of the attack.
5. Reinforce Defenses: Post-attack, defenses are reinforced based on the insights gained, ensuring the system is robust against similar future threats.
6. Continuous Learning: An effective DDoS protection plan is not static. It involves continuous learning from past attacks to update and improve the protection strategy.
7. Strengthen Infrastructure: Finally, the entire infrastructure must be reviewed and strengthened, incorporating the latest technologies and best practices to withstand future DDoS attempts.
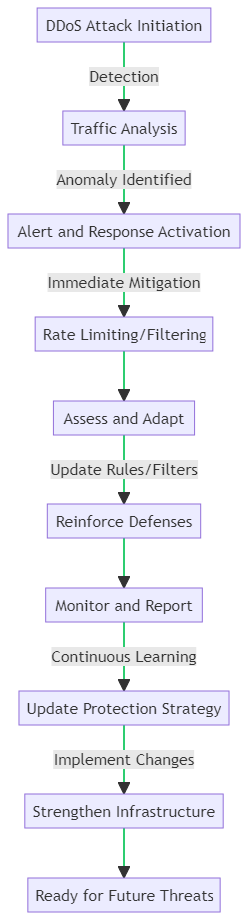
This flowchart and discussion underscore the dynamic nature of DDoS defense. Thus, emphasizing the need for vigilance, rapid response, and ongoing improvement to keep small business networks secure.
Evaluating DDoS Attack Protection Solutions
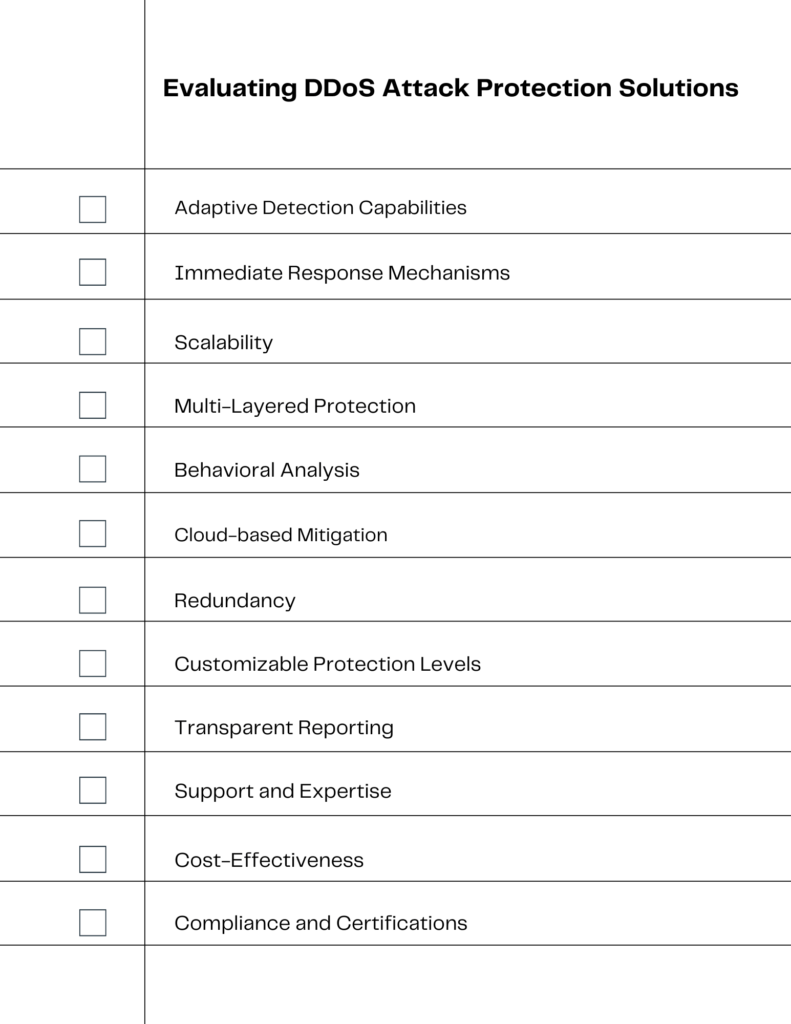
When evaluating DDoS protection solutions, it’s essential to consider several key factors that ensure you’re getting comprehensive coverage. Here’s what to look for in a DDoS protection service:
- Adaptive Detection Capabilities: The solution should have advanced detection methods that adapt to evolving DDoS tactics.
- Immediate Response Mechanisms: Look for services that guarantee rapid response times to mitigate attacks as soon as they’re detected.
- Scalability: The service must be able to scale defenses in response to the size and complexity of the attack.
- Multi-Layered Protection: Ensure the solution offers protection across various layers of your network infrastructure.
- Behavioral Analysis: The ability to differentiate between normal user behavior and potential threats is crucial.
- Cloud-Based Mitigation: Cloud-based services can provide additional bandwidth and resources to absorb large-scale DDoS attacks.
- Redundancy: Redundant systems ensure that if one part of your defense is compromised, others can take over.
- Customizable Protection Levels: Different businesses have different needs; your DDoS protection should be customizable to your specific requirements.
- Transparent Reporting: Detailed reports on attacks and defenses help you understand and improve your security posture.
- Support and Expertise: The provider should offer expert support to help you navigate the complexities of DDoS attacks.
- Cost-Effectiveness: Evaluate the cost relative to the protection offered and ensure it fits within your budget without compromising on essential features.
- Compliance and Certifications: Verify that the service complies with industry standards and holds relevant security certifications.
This checklist will serve as a visual guide to help small business managers and IT personnel make informed decisions when selecting a DDoS protection service that aligns with their security needs and business goals.
An Assessment of Top DDoS Protection Solution Providers on the Market
Comparative Table of DDoS Protection Solutions
| Feature/Solution | Cloudflare | Akamai Prolexic Routed | AWS Shield | Microsoft Azure DDoS Protection | Radware DefensePro |
|---|---|---|---|---|---|
| Global Anycast Network | Yes | Yes | – | – | – |
| Web Application Firewall | Yes | Yes | Advanced version only | Yes | Yes |
| Rate Limiting | Yes | Yes | Advanced version only | Yes | Yes |
| Scalability | High | High | High | High | Moderate to High |
| Behavioral Analysis | Yes | Yes | Yes | Yes | Yes |
| Cloud-Based Mitigation | Yes | Yes | Yes | Yes | Optional (Hybrid) |
| On-Premises Option | No | No | No | No | Yes |
| Customizable Protection | Yes | Yes | Yes | Yes | Yes |
| Transparent Reporting | Yes | Yes | Advanced version only | Yes | Yes |
| Support and Expertise | 24/7/365 | 24/7/365 | 24/7/365 | 24/7/365 | 24/7/365 |
| Cost-Effectiveness | Moderate | High | Moderate to High | Moderate to High | Moderate |
| Compliance/Certifications | Yes | Yes | Yes | Yes | Yes |
Cloudflare
Certainly, Cloudflare stands out for its global Anycast network, which distributes traffic across multiple data centers, effectively mitigating large-scale DDoS attacks.
Additionally, their service includes a Web Application Firewall (WAF), rate limiting, and a user-friendly dashboard for analytics and control.
Akamai Prolexic Routed
Akamai’s Prolexic Routed provides a robust cloud-based DDoS protection service, leveraging its expansive scrubbing centers to defend against attacks. It offers 24/7 monitoring and adaptive rate controls, making it a solid choice for businesses requiring high availability.
AWS Shield: A DDoS Protection Service for the Amazon Cloud
AWS Shield, particularly its Advanced version, offers comprehensive protection for web applications on AWS. It integrates with other AWS services seamlessly and provides DDoS cost protection, which can shield businesses from the financial impact of scaling resources during an attack.
Microsoft Azure DDoS Protection
Azure’s DDoS Protection service is designed to integrate with Azure Virtual Networks and provides turnkey protection for applications running on Azure. It features adaptive tuning, real-time metrics, and diagnostic logs for detailed insights.
Radware DefensePro: Software Providing on-premises Protection
Radware DefensePro is a local, on-premises solution that offers behavioral-based detection and real-time signature creation for zero-day attack protection. It’s suitable for businesses that require on-site protection and is often used in conjunction with cloud-based services for a hybrid approach.
Each of these services offers unique features and benefits, and the best choice will depend on the specific needs and infrastructure of the business in question. It’s crucial to assess each option carefully, considering factors like integration capabilities, cost, ease of use, and the level of customer support provided.
This table provides a snapshot of how each solution stacks up against key features. It’s important to note that the specifics of each feature may vary based on the plan and provider, and additional services may be offered that are not listed here. Always consult with the providers for the most current and detailed information.
Customizing a DDoS Mitigation Solution for Small Businesses
Customizing DDoS Solutions for Small Businesses is crucial in today’s digital landscape, where threats are becoming more sophisticated. Small businesses, often with limited cybersecurity knowledge and resources, are increasingly targeted by Distributed Denial of Service (DDoS) attacks. These attacks can overwhelm systems, disrupt services, and cause significant financial and reputational damage.
To protect against such threats, it’s essential to tailor DDoS protection solutions to the specific needs of small businesses. This involves assessing the unique vulnerabilities of a small business’s infrastructure, understanding the potential impact of DDoS attacks, and implementing a defense strategy that is both effective and cost-efficient.
By focusing on the particular challenges faced by small businesses, such as budget constraints and lack of in-house expertise, DDoS protection providers can offer solutions that not only secure businesses against attacks but also provide peace of mind and allow owners to focus on growth and innovation.
The Role of Artificial Intelligence in DDoS Defense
The Role of Artificial Intelligence (AI) in DDoS Defense is transforming the cybersecurity landscape. AI’s capability to analyze vast datasets rapidly enables it to identify and respond to DDoS threats in real-time, a task impractical for human analysts. By leveraging AI, DDoS protection solutions can adapt to new attack patterns as they emerge, ensuring that defenses are always one step ahead.
AI-driven systems can detect subtle deviations in traffic that may indicate the onset of a DDoS attack. They can then automatically reroute traffic or adjust filters to mitigate the attack’s impact. This proactive approach to DDoS defense is crucial for small businesses that may lack the resources for extensive cybersecurity teams.
Moreover, AI enhances the scalability of DDoS protection strategies, allowing small businesses to enjoy a level of security that was once only accessible to large enterprises. As AI technology continues to advance, it’s expected to become an even more integral part of DDoS defense, offering smarter, faster, and more efficient protection solutions.
Case Studies: Successful DDoS Defense in Action
The 2020 AWS Mitigation of a 2.3 Tbps Attack
In February 2020, AWS successfully mitigated one of the largest DDoS attacks, peaking at 2.3 Tbps. The attack utilized hijacked CLDAP web servers to flood the target with traffic. AWS’s robust infrastructure and advanced DDoS protection mechanisms were able to absorb and neutralize the attack, ensuring uninterrupted service for the customer. Read more about this attack on ZDNet.
GitHub’s Quick Response to a 1.3 Tbps Memcached DDoS Attack
GitHub faced a massive memcached DDoS attack in February 2018, which reached 1.3 Tbps. Thanks to their DDoS protection service, they were alerted within 10 minutes and quickly mitigated the attack, limiting its duration to approximately 20 minutes. This incident showcases the importance of having an immediate and effective DDoS response plan in place.
Building a Resilient Network Infrastructure
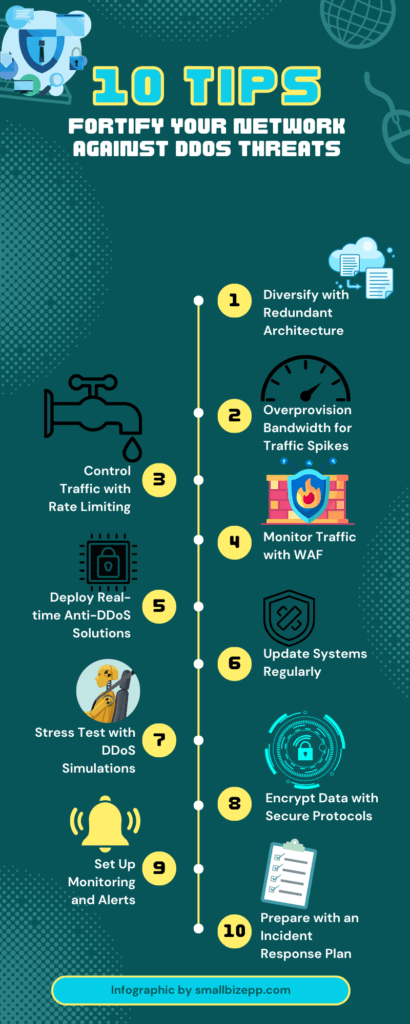
Building a resilient network infrastructure is essential for safeguarding against DDoS attacks. Here are some best practices for network security and DDoS prevention:
- Redundancy and Distribution: Implement a redundant network architecture. Distribute resources across multiple data centers to dilute the impact of an attack.
- Bandwidth Overprovisioning: Maintain bandwidth capacity well above your average peak to handle sudden traffic spikes.
- Rate Limiting: Use rate limiting to control the amount of traffic that can reach your network.
- Web Application Firewall (WAF): Deploy a WAF to monitor HTTP/HTTPS traffic and block malicious requests.
- Anti-DDoS Hardware and Software: Invest in specialized anti-DDoS solutions that can detect and mitigate attacks in real-time.
- Regular Updates and Patching: Keep all systems updated with the latest security patches to close vulnerabilities.
- DDoS Simulation Testing: Regularly conduct stress tests on your network to identify potential weaknesses.
- Secure Network Protocols: Utilize secure and robust network protocols like TLS for data encryption.
- Monitoring and Alerting Systems: Implement monitoring systems for early detection of unusual traffic patterns.
- Incident Response Plan: Have a well-documented incident response plan that includes procedures for DDoS attack mitigation.
By incorporating these practices, businesses can strengthen their network security posture and enhance their defenses against DDoS threats.
DDoS Protection as Part of a Comprehensive Cybersecurity Posture
DDoS Protection as Part of a Comprehensive Security Posture underscores the necessity of integrating DDoS defense within the broader spectrum of cybersecurity measures. Effective cybersecurity management is not just about having a robust DDoS protection solution in place; it’s about ensuring that this defense is a cohesive part of an all-encompassing security strategy.
This integration begins with a thorough risk assessment, identifying all potential vulnerabilities within the system. From there, DDoS protection should be synchronized with other security layers, such as intrusion detection systems, anti-malware tools, and data encryption protocols.
Regular security audits and employee training are also vital, ensuring that every layer of defense is fortified against potential breaches. By adopting a holistic approach to cybersecurity, businesses can ensure a more resilient defense against the multifaceted threats posed by modern cyber-attackers, including DDoS attacks.
Securing Your Business: A Step-by-Step DDoS Protection Roadmap
In the journey to fortify your business against DDoS attacks, a clear and actionable roadmap is essential. Here’s a structured plan to guide you through enhancing your DDoS defenses:
1. Assess Your Current Security Posture
Begin with a thorough assessment of your current network security. Identify any vulnerabilities that could be exploited in a DDoS attack. This foundational step ensures you understand your starting point.
2. Educate Your Team
DDoS protection is not solely a technical challenge; it’s also about awareness. Educate your team on the importance of DDoS defense, common attack vectors, and response protocols.
3. Select Appropriate DDoS Solutions
Choose DDoS protection solutions that align with your specific business requirements. Consider factors such as size, industry, and the nature of the data you’re protecting.
4. Implement Security Best Practices
Apply industry-standard security best practices. This includes regular updates, patch management, and the principle of least privilege across your network.
5. Regularly Update and Test Your Defenses
Cyber threats evolve, and so should your defenses. Regularly update your systems and conduct mock DDoS attacks to test your resilience.
6. Stay Informed on DDoS Trends
The DDoS landscape is constantly changing. Stay informed about the latest threats and innovative defense strategies to stay one step ahead.
7. Review and Adapt
Cybersecurity is an ongoing process. Regularly review your DDoS protection measures and adapt them as needed to meet emerging threats and evolving business objectives.
By following this roadmap, you can systematically enhance your DDoS defenses and ensure that your business is prepared for the challenges of the digital age.

The Future of DDoS Protection
The Future of DDoS Protection is an evolving landscape shaped by emerging trends and technologies. As attackers continually refine their methods, DDoS mitigation strategies must also advance.
Machine Learning and AI: These technologies are becoming more sophisticated, enabling predictive analytics to identify and respond to threats before they escalate.
Hybrid DDoS Defense: Combining on-premises and cloud-based solutions offers a more dynamic and scalable defense mechanism, adaptable to the changing tactics of DDoS attacks.
Software-Defined Networking (SDN): SDN’s flexibility allows networks to be reconfigured on-the-fly, providing an agile response to DDoS threats.
Blockchain for Security: Blockchain’s decentralized nature could offer new ways to secure networks against DDoS by distributing the load and eliminating single points of failure.
Zero Trust Security Model: Adopting a Zero Trust framework ensures that only authenticated and authorized users and devices can access network resources, reducing the potential impact of DDoS attacks.
These trends indicate a future where DDoS protection is more automated, integrated, and responsive, providing robust defense mechanisms to secure businesses against increasingly complex DDoS campaigns.
Conclusion: Your Next Steps in DDoS Security
Navigating the complexities of DDoS threats requires a multifaceted approach. The key takeaways for small businesses looking to bolster their defenses include:
- Customization: Tailor DDoS solutions to fit the unique needs and scale of your business.
- AI Integration: Leverage AI and machine learning for proactive threat detection and mitigation.
- Education: Stay informed about emerging DDoS trends and educate your team on best practices.
- Comprehensive Strategy: Ensure DDoS protection is part of a broader cybersecurity posture.
- Future-Proofing: Keep an eye on technological advancements to future-proof your network.
Actionable advice for small business managers and IT personnel is to begin with a thorough assessment of your current security measures, identify gaps, and integrate robust DDoS protection solutions. Regularly update your defense strategies to combat evolving DDoS tactics and foster a culture of continuous learning and adaptation within your organization.
By implementing these strategies, you can create a resilient defense against DDoS attacks, safeguarding your business’s digital assets and ensuring uninterrupted operations.
The post DDoS Protection Solutions: Safeguarding Your Business in the Digital Age appeared first on Endpoint Security.
*** This is a Security Bloggers Network syndicated blog from Endpoint Security authored by Michael Toback. Read the original post at: https://smallbizepp.com/ddos-protection-solutions/?utm_source=rss&utm_medium=rss&utm_campaign=ddos-protection-solutions
如有侵权请联系:admin#unsafe.sh
