2023-11-7 20:14:54 Author: lab.wallarm.com(查看原文) 阅读量:15 收藏
Unpacking the Cloud: Appreciating its Importance & Uncovering its Weak Points

The cloud has utterly transformed our methods of data storage and retrieval. It has flawlessly woven itself into the fabric of our everyday lives, from a repository for precious memories to a platform that supports mission-critical applications. However, this readily accessible feature brings along its own set of security hazards that we must proficiently counter.
The cloud is a mammoth assortment of servers, strategically located in various data processing units dispersed across the globe. These servers are responsible for storing and administering data, executing applications, and offering a variety of services which range from video streaming, utilitarian office software, to online social interactions.
<code class="language-python">class Cloud:
def __init__(self, servers, data_nodes):
self.servers = servers
self.data_nodes = data_nodes</code>
The cited Python segment portrays a rudimentary blueprint of a cloud, where 'servers' and 'data_nodes' constitute its primary components.
There's no disputing the cloud's relevance. It confers scalability, adaptability, and it's economically prudent. Enterprises can expand or taper down according to demand dynamics, obtain their data at any location, any hour, with payment applicable only for consumptions made.
| Merits of Cloud Computing |
|---|
| Expandability |
| Adaptability |
| Economic Prudence |
| Anywhere Access |
| Disaster Resilience |
However, the cloud's scattered configuration also exposes it to vulnerabilities. Data housed in the cloud can be retrieved from any point, opening the window for potential attacks from these externals too. Furthermore, the collective, requisition-based distribution of cloud services engenders added weak points.
Below mentioned are a few prominent weak spots affiliated to cloud computing:
- Data Infiltrations: Unauthorized perspectival shifts leading to data pilferage, manipulation, or obliteration.
- Unsecured APIs: APIs facilitating services can be manipulated if not adequately safeguarded.
- Common Technology Weak Points: Single tenant's application anomaly in a multi-tenant cloud setup could resonate impacting others.
- Data Depletion: Data could be wiped clean given disaster strikes at the data node or during data transit mishaps.
- Inadequate Preliminary Analysis: Moving to the cloud oblivious of potential hazards could lead to serious security lapses.
Recognizing these weak spots sets the preliminary course to securing your cloud. In the ensuing sections, we will probe further into the dozen cloud security concerns, comprehend the potential risks, intimidation, and complications conjoined to them, and scratch the surface of solution strategies to confront these security threats.
While the cloud is a formidable tool, it's not free of vulnerabilities. As we brave the digital threat landscape, it is imperative to apprehend these risks and apply effective protective measures for our precious data.
Decoding the Dozen Dilemmas of Cloud Safety
Securing the cloud is a multifaceted task. It isn't merely about safeguarding data but involves recognizing the explicit threats associated with cloud usage and crafting risk mitigation strategies. This chapter focuses on delineating the dozen primary cloud safety challenges.
-
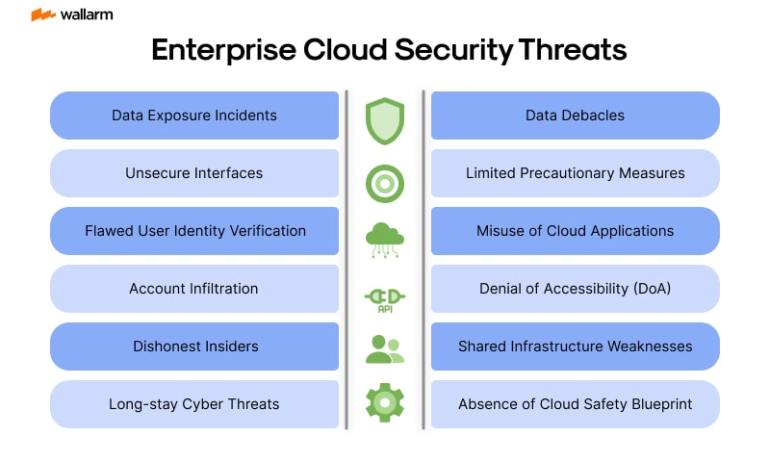
Data Exposure Incidents: These are prevalent issues when utilizing cloud technology. They occur due to a variety of reasons such as weak safety measures, internal dangers, or high-level digital threats. Exposure of confidential data, during these incidents, can tarnish the organizational image and cause financial repercussions.
-
Unsecure Interfaces: The programming interfaces (APIs) unite cloud applications seamlessly. However, such interfaces, when unsecure, create a loophole that intruders can exploit, leading to unauthorized excess, data debacle, exposure events, and service interruptions.
-
Flawed User Identity Verification: An ineffective system of verifying users and managing access increases unauthorized cloud service engagement, resulting in exposure events, data debacle, and service interruptions.
-
Account Infiltration: This is a prominent danger associated with cloud usage. Infiltrators can access user's accounts through phishing scams, exploiting software vulnerabilities, or deciphering easily guessable passwords. Once access is gained, they can alter data, secretly monitor transactions, and misdirect clients to deceptive websites.
-
Dishonest Insiders: These individuals pose a substantial risk within the realm of cloud governance. They have official access to cloud services and can instigate considerable harm, such as exposure events, data debacles, and service interruptions.
-
Long-stay Cyber Threats: Also known as Advanced Persistent Threats (APTs), these stealthy perpetrators penetrate network defenses and reside undetected for a prolonged period, leading to exposure events, data debacles, and service disruptions.
-
Data Debacles: These mishaps can ensue due to a variety of factors like unintentional erasures, harmful attacks, or catastrophic incidences like fire or flood at the data management facility.
-
Limited Precautionary Measures: With the transition to cloud services, companies must undertake comprehensive precautionary measures to comprehend potential safety risks. The absence of these can induce exposure events, regulatory non-conformance, and other safety incidents.
-
Misuse of Cloud Applications: Cloud applications can be manipulated for unsavory objectives, such as initiating Distributed Denial-of-Service (DDoS) attacks, disseminating malicious software, or illicit activities like digital fraud and espionage.
-
Denial of Accessibility (DoA): These DoA intrusions present themselves as significant threats. By using up system resources, they render the system inaccessible to authorized users.
-
Shared Infrastructure Weaknesses: In the cloud, the infrastructure is used mutually by different users. If there are weak points in this pooled technology, it could impact all users, leading to exposure incidents or other safety concerns.
-
Absence of Cloud Safety Blueprint: Not having a well-designed cloud safety blueprint and game plan can result in numerous safety issues, including exposure events, data debacles, and regulatory non-compliance.
Each challenge poses a distinctive risk to cloud safety. Subsequent chapters will thoroughly explore these dilemmas, examining their origins, effects, and potential remedies.
`
`
Exploring Dangers: Revealing the Hidden Threats of Cloud Security
As we undertake a broader study of cloud technology, it becomes evident that besides its bountiful benefits, there lurk unseen snags within the cloud. This chapter delves into the lesser-explored aspects of cloud security and the potential booby traps looming for organizations amidst their transition of operations and information into the cloud realm.
Unauthorised Data Access
One of the primary concerns surrounding cloud usage is unauthorised penetration into data storage spaces. The shared nature of data storage in the cloud makes it more susceptible to illicit breaches.
<code class="language-python"># A simple depiction of a data breach
def cloud_data_breach():
unauthorised_user = False
if unauthorised_user:
print("Potential Data Breach Detected!")
else:
print("Data Remains Protected.")
cloud_data_breach()</code>
This rudimentary Python script gives a glimpse into the real-world complexities associated with data breaches in the cloud by simulating unauthorised system entry.
Lack of Robust Access Management
Robust access management is a cornerstone of cloud security. Inadequate execution of access controls can lead to confidential data straying into risky territories.
| Access Management | Description |
|---|---|
| User Permissions | Regulate who can access |
| Resource Permissions | Regulate access to specific resources |
Inadequate Risk Assessment
In-depth risk assessment is indispensable when migrating operations to the cloud. Misunderstanding the cloud and its potential risks may leave weak spots unguarded within the security parameters.
Risks stemming from Shared Infrastructure
The shared use of technology infrastructure in the cloud can open up potential vulnerabilities if not managed effectively.
Data Vanishing
Storage in the cloud presents a concern regarding possible data evaporation. Various factors such as accidental deletion, targeted attacks, or unpredictable natural disasters could result in data loss.
<code class="language-python"># A simplified representation of data loss
def cloud_data_loss():
valuable_data = "Sensitive Data"
valuable_data = None # Accidental deletion
if valuable_data is None:
print("Data Erased!")
else:
print("Data Remains Secure.")
cloud_data_loss()</code>
The Python script above demonstrates a data loss scenario by nullifying the value associated with 'valuable_data'.
Illicit Account Seizure
Illicit takeover of user accounts poses a significant threat in the cloud computing sphere. Illegitimate individuals could seize the reins of a user's cloud account, tamper with the stored data, disrupt operations or lead customers to sham websites.
Weak APIs
APIs, usually provided by cloud service providers, can turn into security vulnerabilities if they aren't fortified with strong protective measures, which can invite unauthorised access.
Denial-of-Service (DoS) Attacks
DoS attacks can wreak havoc within the cloud ecosystem by overloading the system's resources, rendering it useless for legitimate system users.
Hostile Insiders
Malicious elements within an organization pose significant threats in a cloud environment with damages ranging from unauthorised data access to complete data obliteration.
Abuse of Cloud Resources
Cloud platforms can also be exploited for malicious intentions, such as initiating targeted attacks, distributing malicious software, or unfounded data distribution.
Inefficient Cloud Security Planning
The lack of a resilient cloud security blueprint and a forward-looking security strategy exposes organizations to a range of security threats, from unauthorised data access to complete data loss.
Compliance Risks
Adherence to regulatory norms is a non-negotiable aspect of cloud environments. Failing to maintain this compliance could result in legal complications and hefty fines.
In closure, although the cloud offers a wealth of opportunities, it isn't without potential hazards. Recognizing these threats primes us for their mitigation, building a strong foundation towards a secure cloud ecosystem.
Decoding Emerging Disruptions Threatening the Integrity of the Cloud
The encryption of cloud security ceaselessly changes as hidden cyber threats skilfully morph and hoodwink even the best of our current protective measures. This section paves a path through looming roadblocks to cloud protection, offering a detailed insight into the possible hazards and weak spots that enterprises confront in the cyber landscape.
- Illegitimate Access to Data:
This alludes to the unlawful intrusion into proprietary information, typically called data violations, which persistently compromise cloud integrity. Unlawful intruders can breach and steal critical information, triggering a ripple effect of adverse impacts from fiscal damage to credibility erosion and potential litigations.
<code class="language-python"># Showcasing illegitimate data ingress
def illegitimate_data_access():
unsanctioned_entry = True
if unsanctioned_entry:
print("Illegitimate data access detected!")
else:
print("Data is secure.")
illegitimate_data_access()</code>
This Python snippet offers a bare-bones scenario where illegitimate data incursion happens when unsanctioned access is detected. However, the actual complexities of data infringements greatly surpass this elementary depiction.
- Inadequately Shielded APIs:
APIs (Application Programming Interfaces), vital channels of cloud-powered solutions, facilitate interaction between various software processes. Unfortunately, weakly shielded APIs can leave fissures in the system that intruders can exploit to breach the cloud network.
| Threat | Explanation |
|---|---|
| Inadequately Shielded APIs | Insufficiently protected APIs could be exploited by intruders seeking to unlawfully penetrate the cloud network. |
- Network Overload (DoS) Offences:
DoS (Denial of Service) attacks aim at overwhelming a system to its limit, thereby obstructing access to authentic users. Within the domain of cloud security, a DoS offence involves bombarding a cloud server with excessive internet traffic, culminating in a system failure and disruption of service availability to authorised users.
<code class="language-python"># Portrayal of a DoS offence
import socket
def network_overload():
target_ip = "192.1.1.1"
target_port = 80
message = "This is a Network Overload attack!"
client = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
while True:
client.sendto(message, (target_ip, target_port))
network_overload()</code>
This Python code offers a basic depiction of a DoS offence by continuously sending a message to a defined IP and port. In practice, DoS offences could employ a myriad of systems for execution, a strategy infamously known as Distributed Denial of Service or DDoS attack.
- Internal Hazards:
Frequently termed as internal hazards, these risks stem from individuals within a company who have legitimate access to the cloud network. This group can include anyone from discontented employees to alliances who misuse their access rights either to gather data or incite service disruptions.
| Threat | Explanation |
|---|---|
| Internal Hazards | In-organisation individuals with cloud network access rights can misuse them to accumulate data or instigate service interruptions. |
- Illegitimate Account Takeovers:
Often coined as account takeovers, this menace involves an unauthorized entity illicitly gaining control over a user's cloud service account typically through sly methods like phishing, fraud, or by utilizing software flaws. Once the control is possessed, the intruder can steal data, modify files, and cause service disruptions.
<code class="language-python"># Demonstrating possible illegitimate account seizures
def illegitimate_account_takeover():
unsanctioned_access = True
if unsanctioned_access:
print("Cloud account compromised!")
else:
print("Cloud account is secure.")
illegitimate_account_takeover()</code>
This Python code portrays a likely scenario of illegitimate account takeover detected through unsanctioned access. However, real-world scenarios of account seizures involve intricate strategies such as phishing, keylogging, or exploitation of software vulnerabilities.
To conclude, comprehending these potential threats is the first necessary stride towards crafting comprehensive safety protocols for securing cloud data. As we progress into upcoming chapters, we'll broaden our knowledge of challenges that dwell in the realm of cloud security to enhance our understanding of the hazards and weak points on the digital cloud horizon.
Diversifying Outlook - Evaluating Twelve Obstructions to Safe Cloud Navigation

As we chalk out the terrain of cyber-securing the cloud, identifying and emphasizing the crucial obstacles businesses confront becomes significant. This section is intended to supply an elaborate probe into twelve key impediments to secure cloud navigation, deciphering their complexities and revealing possible repercussions on your cloud-based framework.
- Invasion of Privacy: This issue poses a prominent and destructive threat in cloud defence. Such scenarios transpire when unsought intruders pry into confidential data situated in the cloud, paving way for acute financial setbacks and tarnished goodwill.
<code class="language-python"># An illustrative case of privacy invasion
def non-permissible_infiltration():
try:
obtain_info = cloud_storehouse.retrieve('confidential_data')
except UnpermittedAccessError:
print("Invasion of Privacy discovered!")</code>
-
Deficiency in Verification and Access Rights: Frail verification measures and poor access management could prompt unsolicited usage of cloud-based assets. Culprits could be feeble passwords, absence of numerous-step verification, or blurred delineation of user roles and access privileges.
-
Exposed Portals: A prevalent feature of cloud providers is furnishing interfaces for clients to engage with their services. Conversely, unshielded portals can render your cloud-based assets susceptible to cyber transgressors.
<code class="language-javascript">// Demonstration of exposed portal
app.post('/client/data', (req, res) => {
let info = req.body.details;
// No validation or verification
info_hub.stash(info);
res.send('Successful data accumulation!');
});</code>
-
System Fragility Spots: These relate to feeble areas within a system that could become the hunting grounds for cyber predators. Fragility spots could exist anywhere in the cloud framework, spanning from the central system down to distinct software programs.
-
Account Usurpation: Alluding to instances when cyber transgressors commandeer a cloud account via fraudulent schemes like phishing. Once at the helm, the cyber marauder can alter data, monitor activities, and mislead customers to unapproved destinations.
-
Malicious Insiders: Identifiable as individuals inside an establishment who might abuse their authorized cloud access to inflict harm. These can range from employees to contractors, or even business partners.
-
Advanced Persistent Threats (APTs): APTs denote enduring, targeted threats where malefactors infiltrate a system and remain undetected for an extended duration. Their primary aim is data extraction over time.
-
Evaporating Data: This alarming scenario might unfold due to accidental erasure, harmful breaches, or a catastrophic event damaging the physical infrastructure hosting the cloud service.
-
Lax Due Investigation: This failure draws attention to an absence of meticulous scrutiny and comprehension of a cloud service provider's defence strategy before embracing their services.
-
Cloud Service Malign Usage: Ill-intentioned individuals might misuse cloud services to carry out deleterious activities, such as triggering Distributed Denial of Service assaults or spreading malware.
-
Service Disruption (DoS): Characterized by inundation of a system's resources resulting in its unavailability to users. Regarding cloud technology, this would suggest flood-loading a cloud service, rendering it overloaded or unresponsive.
-
Shared Technological Deficits: Ordinarily, in a cloud environment, the infrastructure is communal. Thus, glitches in the core technology might potentially affect all the users exploiting that technology.
Different impediments carry unique risks to cloud defence. Yet, armed with a robust security tactic and a deep comprehension of these tribulations, institutions can effectively maneuver around these risks and fortify their cloud structure. The ensuing chapter will dive into assorted tactics for navigating these security impediments.
Strengthening Cloud Systems: Counteractive Solutions Against Security Threats
Addressing 12 cloud safety concerns isn't merely a matter of incorporating a handful of protective actions. It necessitates the establishment of a detailed, sturdy defense mechanism capable of adapting to the ever-changing world of cyber threats. This section will scrutinize and provide different counter-measures that can help tackle these protection issues.
- Securing Data: To safeguard your cloud-stored information, encrypt it. This method transforms your data into an unreadable format barring unsanctioned access. It's essential to encrypt both dormant and in-transit data.
<code class="language-python">from cryptography.fernet import Fernet # Form a Key and Develop a Fernet Instance key = Fernet.generate_key() cipher_env = Fernet(key) # Construct a message cipher_text = cipher_env.encrypt(b"A classified message. Not for intruding eyes.") # Disassemble a message plain_text = cipher_env.decrypt(cipher_text)</code>
-
Managing Identity and Access (IAM): IAM serves as an operational structure for overseeing electronic identities, enabling control over a user's functions, monitoring user activities, generating activity reports, and consistently applying relevant policies.
-
Periodical Scrutiny and Upgrades: Periodic reviews can expose possible weak points in your cloud safety. Keeping your systems and software up-to-date is essential for warding off emerging threats.
-
Protection and Retrieval Plans: A solid protection and retrieval plan can reduce the impact of data compromise or loss. This involves habitual data backups and quick, efficient data recovery.
-
Double Check Authentication (MFA): MFA provides added safety by necessitating at least two proofs of identification before allowing access.
-
Security Evaluation and Event Tracking (SIEM): SIEM solutions offer instant insights into security warnings created by applications and network equipment.
| SIEM Instruments | Characteristics |
|---|---|
| Splunk | Instant overview, Scalability, Flexibility |
| LogRhythm | AI-driven, Comprehensive, User-friendly |
| IBM QRadar | Superior threat exposure, Offense administration |
-
Intrusion Sensing and Determent Mechanisms (IDPS): These mechanisms inspect the flow of network traffic for unexpected behavior and issue alarms when such is found.
-
API Protection: APIs are frequently utilized by intruders as an entry point into cloud systems, so their fortification is pivotal. This can be achieved by executing encryption, usage of API portals, and regular tests.
-
Team Education: Often, human mistakes play a part in cloud safety violations. Periodical training keeps your team informed about newly arising threats and protective measures.
-
Secure Software Construction Cycle (SDLC): Infusing safety into every segment of the software construction cycle enables early discovery and addressing of weak points.
-
Full-proof Authentication Architecture: This defense model enforces firm verification for every individual and device attempting to access resources inside a private network, regardless of their location relative to the network boundaries.
-
External Vendor Safety Management: If external collaborators are involved, it's necessary to guarantee their adherence to high standard protection practices.
In summation, cloud system security involves a multi-dimensional strategy. Rectification isn't just about incorporating preventive steps, but it is about facilitating continuous supervision, regular updates, and inculcating a sentiment of safety within the organization.
Deciphering Cloud Protection in a Cyber Crisis Horizon
Reaching our final point of studying the dozen pressing concerns, hazards, perils, and predicaments surrounding safety within the cloud milieu, it's key to acknowledge that this domain isn't static. Instead, it is an arena that evolves and adapts continually, influenced by ceaseless progression in technology, paralleled by the unyielding endeavors of cybercriminals to utilize every potential loophole.
The numerous advantages of the cloud landscape - scalability, adaptability, and cost-efficiency - have made it an essential tool in contemporary business operations. This wide-spread acceptance has also, however, turned it into a coveted prey for cyber predators. We have tackled 12 pivotal security concerns in the cloud throughout this text. While this list isn't exhaustive, it captures the most demanding hurdles companies currently face.
Let's take a brief look at these twelve cloud security predicaments:
- Data Intrusions
- Vulnerable APIs
- System Weaknesses
- Account Usurpation
- Harmful Insiders
- Persistent Advanced Threats (PATs)
- Data Depletion
- Lack of Thorough Due Diligence
- Misuse of Cloud Solutions
- Service Denial (SD)
- Common Technology Weak Spots
- Need for Firm Cloud Protection Strategy and Structure
Addressing each of these predicaments requires careful evaluation of risks and unique countermeasures. Still, there are several overarching tactics to aid organizations in deciphering the labyrinth of cloud protection.
`
`
The first vital step is to adopt a forward-thinking stance towards cloud protection, implying constant surveillance and evaluation of your cloud's security disposition. Tools such as Cloud Safety Posture Management, CSPM, are beneficial in identifying configuration errors and non-compliance cases, offering real-time insight into your cloud protection.
<code class="language-python"># Example of a CSPM utilization
class CloudSafetyPostureManagement:
def watch(self, cloud_area):
# Watch the cloud area for potential problems
pass
def evaluate(self, cloud_area):
# Evaluate the safety disposition of the cloud area
pass</code>
The second important measure is to establish sturdy cloud safety structure. It encompasses applying protective controls at every stratum of the cloud stack, from the network and storage components to application and data segments. A strategically designed cloud safety structure can aid in alleviating hazards like data intrusions, susceptible APIs, and system weaknesses.
<code class="language-python"># A layered cloud safety structure sample
class CloudSafetyStructure:
def apply_network_protection(self):
# Apply protective controls at the network segment
pass
def apply_storage_protection(self):
# Apply protective controls at the storage segment
pass
def apply_application_protection(self):
# Apply protective controls at the application segment
pass
def apply_data_protection(self):
# Apply protective controls at the data segment
pass</code>
The third essential element is cultivating a mindset of security vigilance. This includes training the workforce about the importance of cloud safety and the possible perils of non-compliance. An enlightened team forms a substantial defense-line against threats like account usurpation and harmful insiders.
In conclusion, deciphering the cloud protection horizon amidst a realm of cyber crises is a challenging yet vital process. By grasping the threats, perils, and predicaments, and implementing forward-thinking and robust safety procedures, organizations can harness the cloud's advantages while shrinking their susceptibility to cyber predators.
如有侵权请联系:admin#unsafe.sh