
2023-11-8 03:16:19 Author: therecord.media(查看原文) 阅读量:22 收藏
Software company Atlassian is now saying that a recently disclosed issue is being exploited by hackers using the Cerber ransomware.
An Atlassian spokesperson said Tuesday that the company had evidence to support what cybersecurity researchers reported over the weekend: CVE-2023-22518 — a vulnerability affecting the Confluence Data Center and Confluence Server products — was being used in cybercrime.
On Sunday, cybersecurity researchers and incident responders at Rapid7 said that they were seeing exploitation attempts by hackers using Cerber — a ransomware brand thought to be long-defunct. Atlassian had previously made several announcements about the bug but didn’t specify how it was being exploited.
“Unpatched instances remain vulnerable and we continue to urge those Confluence Data Center and Server customers to take immediate action,” the Atlassian spokesperson said.
The company said it has updated its advisory with information on how customers can detect threats and remediate the issue.
Escalating warnings
Atlassian CISO Bala Sathiamurthy warned the public last week about the bug, which he said could lead to “significant data loss if exploited.” Later in the week, the company updated its advisory to say that while it did not have evidence of an active exploit, it did observe “publicly posted critical information about the vulnerability which increases the risk of exploitation.”
“After discovering the unexploited vulnerability, on October 31, 2023, we issued the Critical Security Advisory urging customers to take immediate action. While there was still no known exploit, we issued another wave of communications on November 2, 2023 that noted the increased risk for any customers that had not yet applied the patch after observing publicly posted critical information about the vulnerability,” the Atlassian spokesperson said Tuesday.
“On November 3, 2023, we warned customers of an active exploit and escalated this on November 6, 2023 following evidence of malicious activity, including ransomware attacks.”
Other companies, like Huntress and Red Canary, backed up Rapid7’s assessment that hackers were using the Cerber ransomware after exploiting the vulnerability.
The return of Cerber
The Cerber ransomware operation was active between 2016 and 2019 but was seen in 2021 targeting Confluence instances vulnerable to another bug, CVE-2021-26084. At the time, the hackers behind the 2021 campaign targeted victims in China, Germany, and the U.S., demanding 0.04 bitcoin in exchange for the decryptor.
Several ransomware experts said they had not seen the Cerber ransomware used in years.
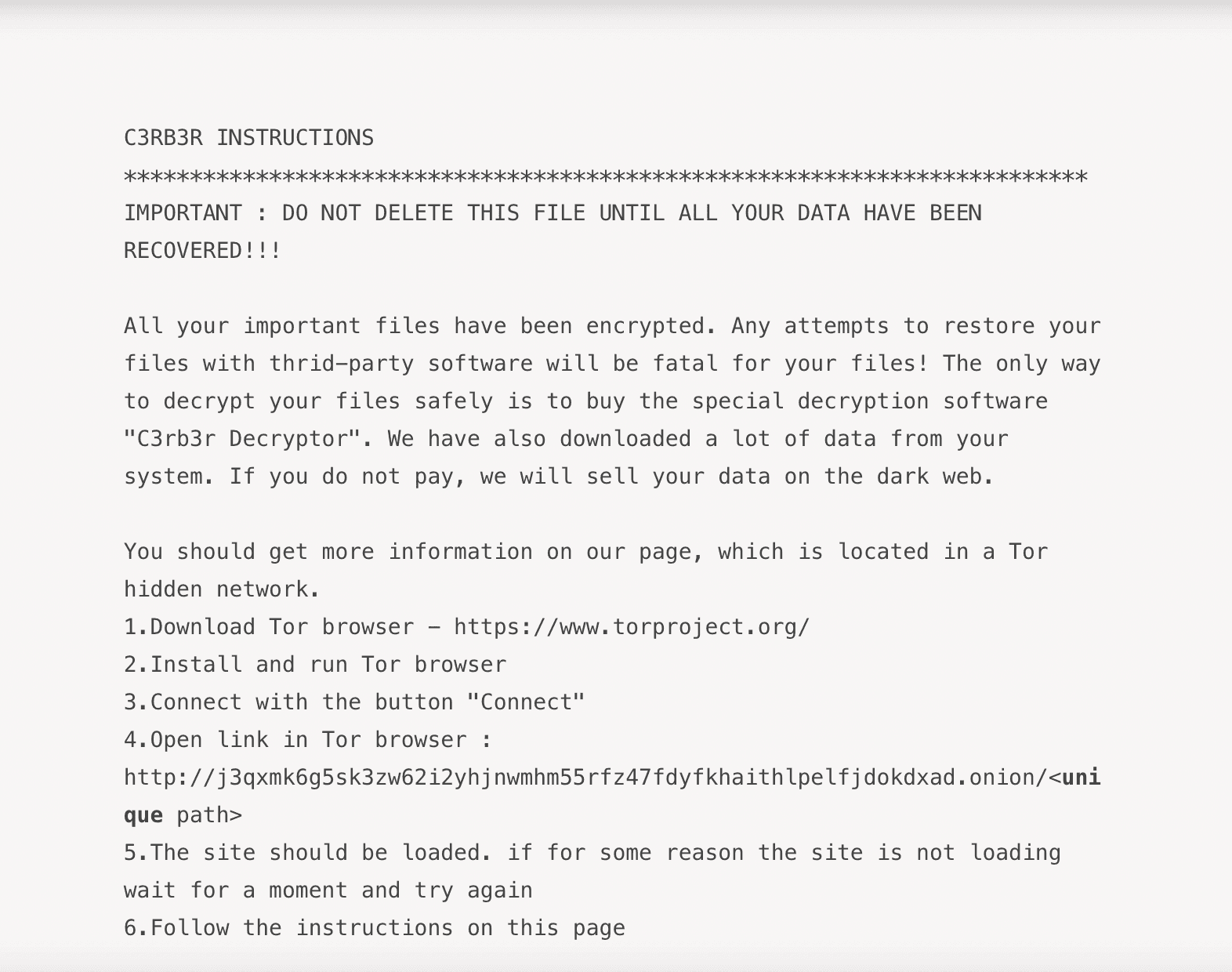 Cerber ransomware note. Image: Rapid7
Cerber ransomware note. Image: Rapid7
When asked about the situation, Rapid7 head of vulnerability research Caitlin Condon told Recorded Future News the ransomware note the team extracted was titled “C3RB3R Instructions,” and the files were encrypted with the extension “L0CK3D,” which is a common pattern for Cerber ransomware.
“It’s important to note, however, that we’re analyzing and attributing the malware, not the threat actor,” she said.
“The ransomware ecosystem has changed and diversified significantly in recent years — source code has been leaked and components reused, adversaries from prominent groups have shifted allegiance (and taken their so-called intellectual property with them), affiliates and access brokers have evolved tactics and techniques, and so on.”
Condon went on to note that in other recent attacks, the company has seen hackers use ransomware whose source code was leaked. The theory is that lone-wolf attackers are using the leaked code to “make a quick buck.”
The researchers are “analyzing the malware and the artifacts, not attributing the human adversary,” Condon said.
Rapid7 said multiple customers are being exploited through CVE-2023-22518 and Red Canary as well as Huntress said they saw the same .LOCK3D file extension in attacks.
Huntress researchers said that basic searches of “confluence” on the online Shodan search tool show more than 200,000 possibly vulnerable endpoints and more narrow searches found over 5,600 possibly vulnerable endpoints. But the company noted that neither search proves exploitability or version number and only “demonstrate that Confluence is often publicly accessible.”
Get more insights with the
Recorded Future
Intelligence Cloud.
No previous article
No new articles
Jonathan Greig
Jonathan Greig is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.
如有侵权请联系:admin#unsafe.sh
