2023-11-8 13:33:22 Author: riskybiznews.substack.com(查看原文) 阅读量:24 收藏
This newsletter is brought to you by asset inventory and network visibility company runZero. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Chinese state-sponsored hacking operations have undergone a major shift in recent years, with groups growing in sophistication and abandoning noisy and high-volume campaigns for stealthy and extremely targeted attacks.
If you read APT reports for a living—like this newsletter's author—then nothing in the above sentence is new to you.
Over the past two or three years, there have been numerous reports across the infosec industry about how Chinese APT group "XX" or how Chinese APT group "YY" has changed their modus operandi.
Unless you're constantly reading these reports, it is hard to see the big picture, spot general trends, and notice the slow evolution of Chinese APTs from the OpSec failures of the late 2000s to apex predators in today's global cyber landscape.
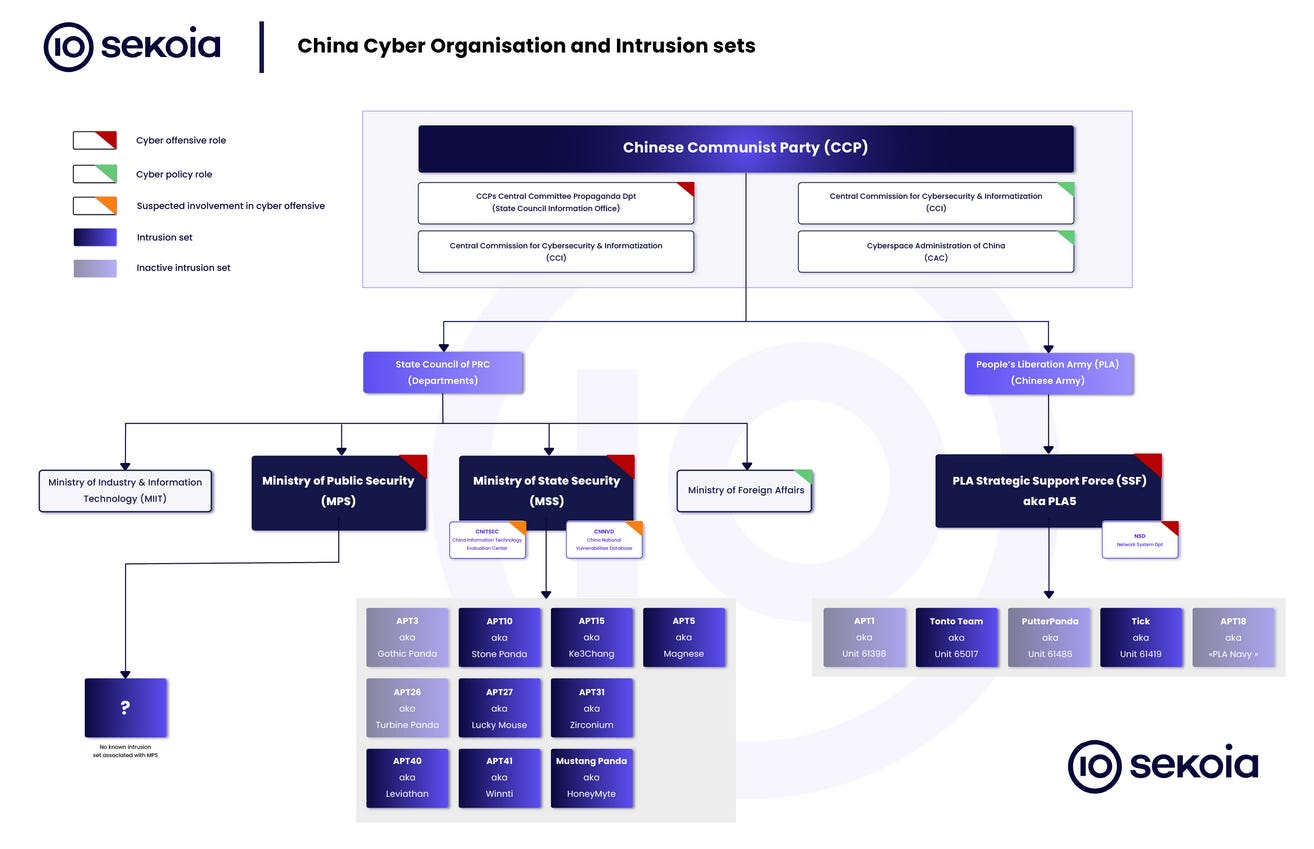
Seeing the big picture can be challenging when you're reading text on the back of small puzzle pieces, but the folks at Recorded Future published an excellent report this week that perfectly contextualizes what has been happening with China's APTs in the 2020s.
There are several main conclusions that we will list below, although we recommend you read the report for yourself since it's the most complete picture we've seen assembled on Chinese APT activity in recent years. These are not copy-pasted and include some of our own commentary and additions.
Chinese state-sponsored operations are slowly moving away from high-volume targeting. Gone are the days of spear-phishing operations targeting every diplomat under the sun and major corporations with "attractive" intellectual property. Today, Chinese APT groups are more coordinated and thoughtful when selecting targets. Recorded Future puts this on the Chinese government's restructuring of its intelligence and military apparatus in the mid-2010s.
Chinese groups are moving away from custom malware and infrastructure to using open-source tools and public exploits.
Chinese groups are using networks of compromised routers and IoT equipment as proxy/anonymization tools to hide malicious traffic and infrastructure.
Chinese groups have also been among the first APT groups to adopt LOLbins for operations, replacing highly detectable malware with the abuse of locally installed apps. See this CISA advisory here for more.
Even if past attribution has linked some Chinese APT groups to private contractors, military units, or intelligence service bureaus, many groups are now sharing tools, suggesting the existence of some sort of private exploit/tooling supply chain across the entire Chinese cyber apparatus. This is giving security companies (see SentinelOne example here) fits when it comes to attribution. This was never a problem in the past, primarily because APT clusters were often easily delineated, the malware code and infrastructure contained many OpSec mistakes, and because of each group's unique TTPs.
Since 2021, Chinese APTs have shifted towards the exploitation of public-facing appliances. Targets included appliances such as firewalls, enterprise VPNs, hypervisors, load balancers, and email security products. These are devices found in almost all government and corporate networks and are often used as initial access and pivot points to more "desirable" sections of a target's network.
This shift towards targeting public-facing appliances has stood out like a sure thumb. In fact, Recorded Future says that 85% of all the zero-days abused by Chinese APTs since 2021 have been in public-facing appliances, showing how crucial (the targeting of) these devices has become to Chinese cyber operations.
Chinese APT groups have also been among the first to exploit publicly-known vulnerabilities in these types of products, for the same reason, to get perches inside highly sought-after targets before anyone else.
Just like Microsoft in its Digital Defense Report last year and the Atlantic Council in a report this year, Recorded Future puts China's increased usage of zero-days on the country's new vulnerability disclosure law that allows the country's intelligence security agency to learn of new vulnerabilities before patches are out.
China has heavily invested in increasing the sheer size of its cyber forces, which means the country is now capable of both qualitative and quantitative operations.
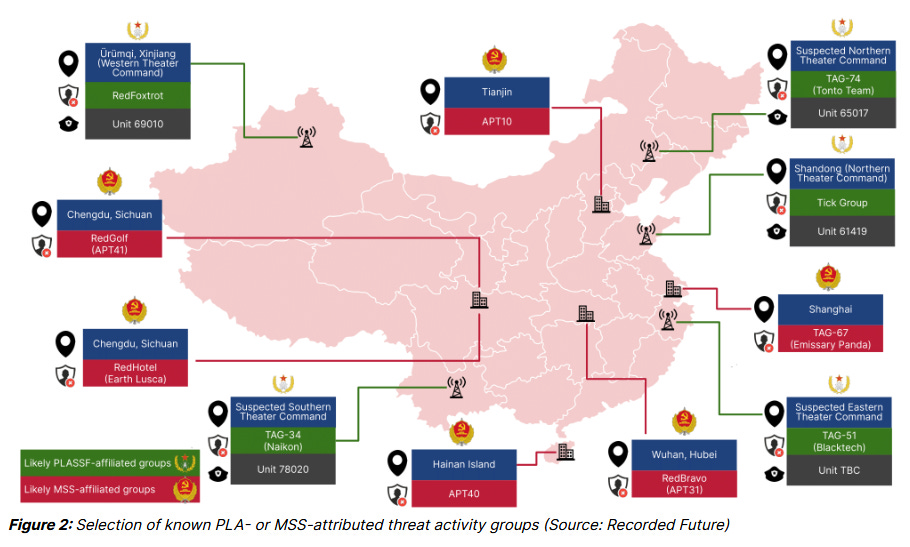
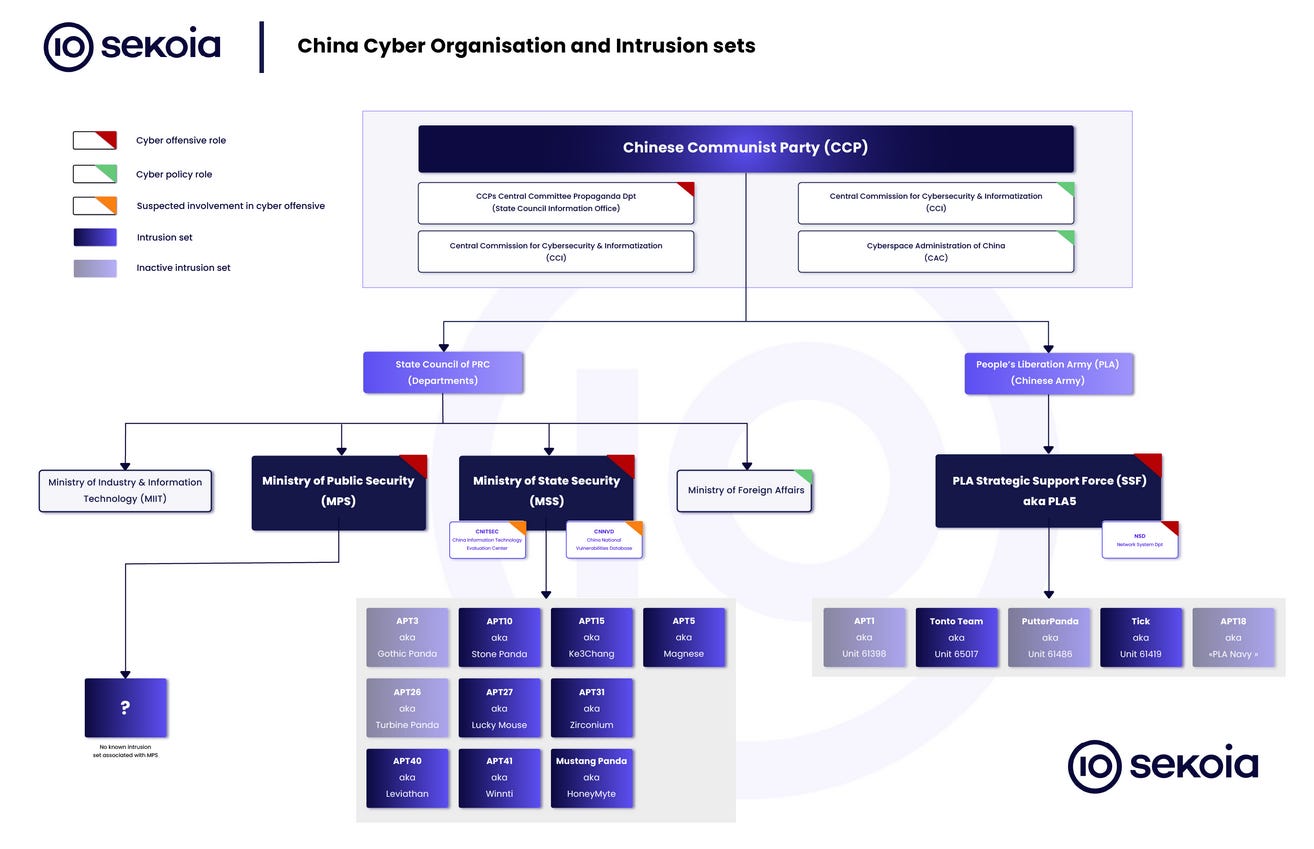
Finally, the report also includes an attribution map for China's APT groups, including their suspected geographical locations. This is in line with what Sekoia published earlier this year, too.
Monero Project hack: A threat actor has emptied the community wallet of the Monero Project and stole $450,000 worth of community donations. The hack took place on September 1st but was only discovered four weeks later, on the 28th. The Monero team says it has not found how the hacker stole the funds.
Bitfinex breach: Cryptocurrency exchange Bitfinex says a threat actor successfully phished and gained access to the account of one of its customer support agents. The company says the hacker gained access to a small amount of customer information because the support agent had limited permissions. Bitfinex says most of the affected customer accounts were either empty or inactive.
Frax Finance DNS hijack: DeFi platform Frax Finance suffered a DNS hijacking attack last week that saw its engineers lose control over its two main domains frax[.]finance and frax[.]com.
Shimano ransomware attack: Bike component manufacturer Shimano suffered a ransomware attack, and more than 4.5TB of data was stolen in the incident. The attack has been claimed by the LockBit ransomware group. [Additional coverage in CyclingNews]
Zhefengle leak: Chinese e-commerce platform Zhefengle has leaked information on more than 3.3 million orders placed on its site between 2015 and 2020. The data included the personal details of millions of Chinese citizens, such as names, phone numbers, and home addresses. For some orders, buyers also had to provide copies of their identity cards, which also leaked in the incident. According to CloudDefense's Viktor Markopoulos, the data leaked after the Chinese company left one of its databases exposed on the internet without a password. [Additional coverage in TechCrunch]
Fake LinkedIn breach: Troy Hunt, the founder of the Have I Been Pwned service, has disproven claims made this week by a hacker named USDoD that they breached social media company LinkedIn. It's fake people. Calm down!
"To lead with the conclusion and save you reading all the details if you're not inclined, the dataset so many people flagged me this week titled 'Linkedin Database 2023 2.5 Millions' turned out to be a combination of publicly available LinkedIn profile data and 5.8M email addresses mostly fabricated from a combination of first and last name."
Mandatory MFA for Microsoft admin portals: Microsoft is enabling mandatory multi-factor authentication for customers logging into any of its cloud admin portals. The change will impact Azure, Microsoft 365, and Exchange admin centers. Microsoft joins the ranks of AWS and Oracle as cloud services that require mandatory MFA to access admin accounts.
Discord switches to temp file URLs: Instant messaging service Discord will start hosting file uploads on temporary URLs by the end of the year. The company says all temporary URLs will expire after 24 hours, with files also being deleted from its servers. Discord says it is making the switch in an attempt to prevent threat actors from using its platform for hosting malware or parts of cybercrime infrastructure. [Additional coverage in BleepingComputer]
Twitter disinformation: Several social media research groups have abandoned studies of disinformation on Twitter after the company raised API access prices through the roof and after Elon Musk started suing researchers who published studies claiming the site was helping push state-backed propaganda (like we needed a study to see the obvious in Twitter's Trending section), per a Reuters report.
Anti-DPRK cooperation: Officials from Japan, South Korea, and the US launched a cooperation group to counter North Korea's cyber operations, which have been used to finance its weapons program. [Additional coverage in Reuters]
FISA reform legislation: US lawmakers have introduced a new bill to reauthorize US surveillance powers under Section 702 of the Foreign Intelligence Surveillance Act, set to expire at the end of the year. Named the Government Surveillance Reform Act, the bill adds protections for US citizens. The primary change will require US law enforcement agencies to obtain a court warrant before searching the data of US citizens against the FISA data set. The Section 702 reform comes after ODNI found multiple cases of FISA misuse over the past years. The bill also goes beyond FISA and prohibits US government agencies from purchasing Americans' data from data brokers, a tactic used in the past for warrantless surveillance. The bill has been introduced on both floors of the US Congress and has bipartisan support. [Additional coverage in JustSecurity and Cyberscoop]
In this Risky Business News sponsor interview, Tom Uren talks to Huxley Barbee, Security Evangelist at runZero, about finding the unknown unknowns and what is a security evangelist.
Indian crypto-scam group detained: Indian authorities have detained eight suspects who stole $300 million (₹2,500 crore) from a cryptocurrency investment fund. The scheme lured victims to invest saved rupees into a cryptocurrency project. More than 5,000 government employees from the Himachal Pradesh state lost funds when the scheme collapsed, and some of its administrators fled to Dubai. Four of the 18 detained suspects work for the Himachal Pradesh police force. [Additional coverage in The Times of India]
Anonymous Sudan: Netscout takes a look at the DDoS makeup and capabilities of Anonymous Sudan pro-Kremlin "hAcKtIvIsT" group. Just a reminder that the group is a Russian operation.
"Initially, all posts to Telegram were in Russian, which called into question the veracity of the group's selection of name and purported origin. As other researchers have noted Anonymous Sudan eventually started using Arabic in posts and eventually switched to Sudanese dialects. Many of the initial posts in Russian have since been deleted or removed. The group often overlooks actions taken against Sudan or Islam in non-Western countries."
D0nut ransomware: NCC Group has published a report reviewing the tactics used by the D0nut ransomware and extortion group.
Mallox ransomware: Chinese security firm Tinder has published a report on a threat actor using brute-force attacks to breach MSSQL databases and deploy the Mallox ransomware.
Jupyter Infostealer: VMWare's Carbon Black analyzes new versions of the Jupyter infostealer, a malware strain first spotted in 2020 and also known as Yellow Cockatoo, Solarmarker, and Polazert.
GootBot: IBM's X-Force team has discovered a new component of the GootLoader malware that is currently being deployed on corporate networks to facilitate easier lateral movement. The new component is named GootBot, and X-Force says the component is used instead of the Cobal Strike framework.
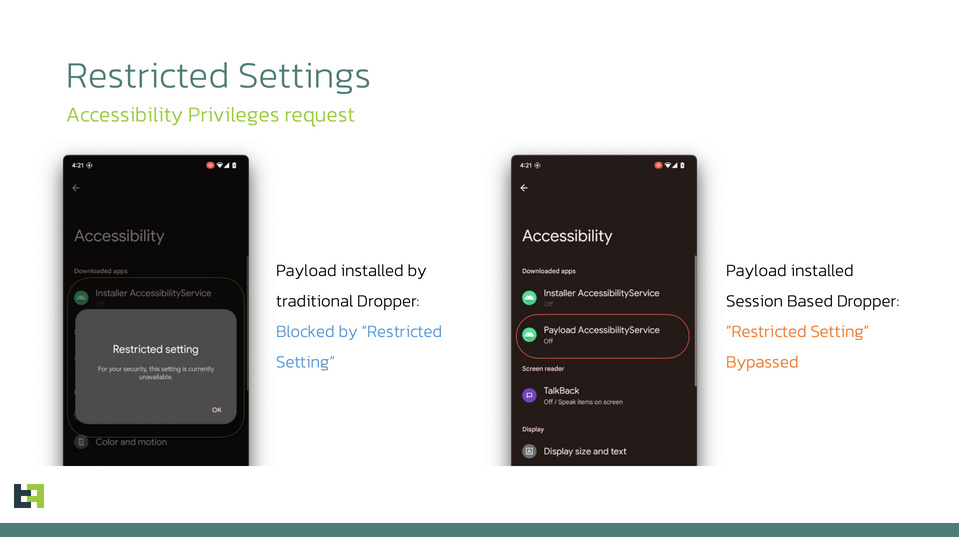
SecuriDropper: Researchers at mobile security firm ThreatFabric have discovered a new malware operation named SecuriDropper that can bypass the "Restricted Settings" security feature in Android 13. The Restricted Settings feature works by blocking side-loaded apps from accessing sensitive permissions. The SecuriDropper malware infects Android smartphones via malicious side-loaded apps, bypasses the Restricted Settings limitation, and then downloads additional malware payloads. SecuriDropper is available as a Dropper-as-a-Service, and its creator makes money by renting access to other criminal groups to drop any payload they want on the infected devices. SecuriDropper is the second known malware strain that can bypass Android 13's Restricted Settings feature after Zombinder.
Senior Sales Engineer Ali Cheikh demonstrates the runZero platform to Risky Business host Patrick Gray. runZero is a cyber asset management tool that combines active scanning, passive discovery, and API integrations to discover IT, OT, and IoT assets (both managed and unmanaged) across your network, including cloud, mobile, and remote environments.
Agonizing Serpens: An Iranian hacking group named Agonizing Serpens has conducted multiple destructive attacks against Israeli organizations in the education and technology sectors. The group has been active since 2020 and is known for breaching networks to collect intelligence and then deploying ransomware or wipers to hide its tracks and disrupt the victim's operations. According to Palo Alto Networks, the group's recent hacking campaign lasted from January to October this year and involved three data wipers named MultiLayer, PartialWasher, and BFG Agonizer. Also known as Agrius, Pink Sandstorm, and BlackShadow, Microsoft has linked [PDF] the group to Iran's Ministry of Intelligence and Security.
AridViper: SentinelOne has a report on AridViper, the APT group allegedly run by Hamas members. The report focuses on the group's operations targeting Android smartphones, also covered in this Talos report.
"Through 2022 and 2023, the actor has distributed SpyC23, an Android spyware family, through weaponized apps posing as Telegram or as a dating app called Skipped."
SideCopy: SEQRITE delves into recent SideCopy APT operations that have leveraged a recent WinRAR zero-day (CVE-2023-38831) to deploy versions of the DRat and AllaKore RATs. It also covers attacks against Linux systems with the Ares RAT.
Evilnum/DarkCasino: NSFOCUS looks at how the Evilnum/DarkCasino fin group has incorporated the same WinRAR zero-day (CVE-2023-38831) in its attacks.
BlueNoroff: Jamf has published a report on a recent campaign of the BlueNoroff DPRK APT that targeted macOS users with a new malware strain written in Objective-C and named ObjCShellz.
QNAP security updates: Taiwanese NAS vendor QNAP has released four security updates for its products.
Veeam security updates: Cloud backup provider Veeam has released security updates to patch four vulnerabilities.
Bitrix24: Researchers at STAR Labs have found and helped patch seven vulnerabilities in the Bitrix24 CRM platform.
BatSignal: Security researcher Gergely Kalman has published a technical write-up on BatSignal (CVE-2022-26704), an unprivileged user to root elevation of privilege vulnerability in macOS.
Printer vulnerabilities: Devcore has published part two of a write-up on three printer vulnerabilities it used at the Pwn2Own hacking contest back in 2021. The vulnerabilities are pre-auth RCEs and impact Canon, HP, and Lexmark printers.
Zephyr Project vulnerabilities: Security researcher Marco Ivaldi has found 12 vulnerabilities in the Zephyr real-time OS.
Atlassian exploitation: A threat actor is exploiting a recently patched vulnerability (CVE-2023-22518) in Atlassian Confluence systems to bypass authentication and encrypt servers with the C3rb3r ransomware. This version of the C3rb3r ransomware is based on the leaked Conti ransomware code and is not related to the old and more infamous Cerber ransomware from the mid-2010s. The attacks began over the weekend and were spotted by security firms Red Canary, Huntress, and Rapid7. The group is one of the many threat actors that are currently targeting Confluence systems after mass exploitation began at the end of last week. Following reports of active attacks, Atlassian also updated the bug's severity score from a 9.1 to a 10/10.
VEX guide: CISA has published a document on how companies can issue a VEX (Vulnerability Exploitability eXchange) alert when bugs in their software are being actively exploited in the wild.
Ekoparty 2023 videos: Talks from the Ekoparty 2023 security conference, which took place last week, are available on YouTube. All the talks are in Spanish.
Hexacon 2023 videos: Talks from the Hexacon 2023 security conference, which took place earlier this month, are available on YouTube.
Dutch Police podcast: The Dutch Police's cybercrime unit is launching a podcast discussing some of its biggest operations. The first episode covers the Rubella malware takedown, and the podcast will have six episodes. Obviously, the podcast is in Dutch.
Acquisition news: Palo Alto Networks has announced plans to buy browser security startup Talon Security for $625 million. The deal comes after Palo Alto also bought cloud security firm Dig Security last week for $400 million.
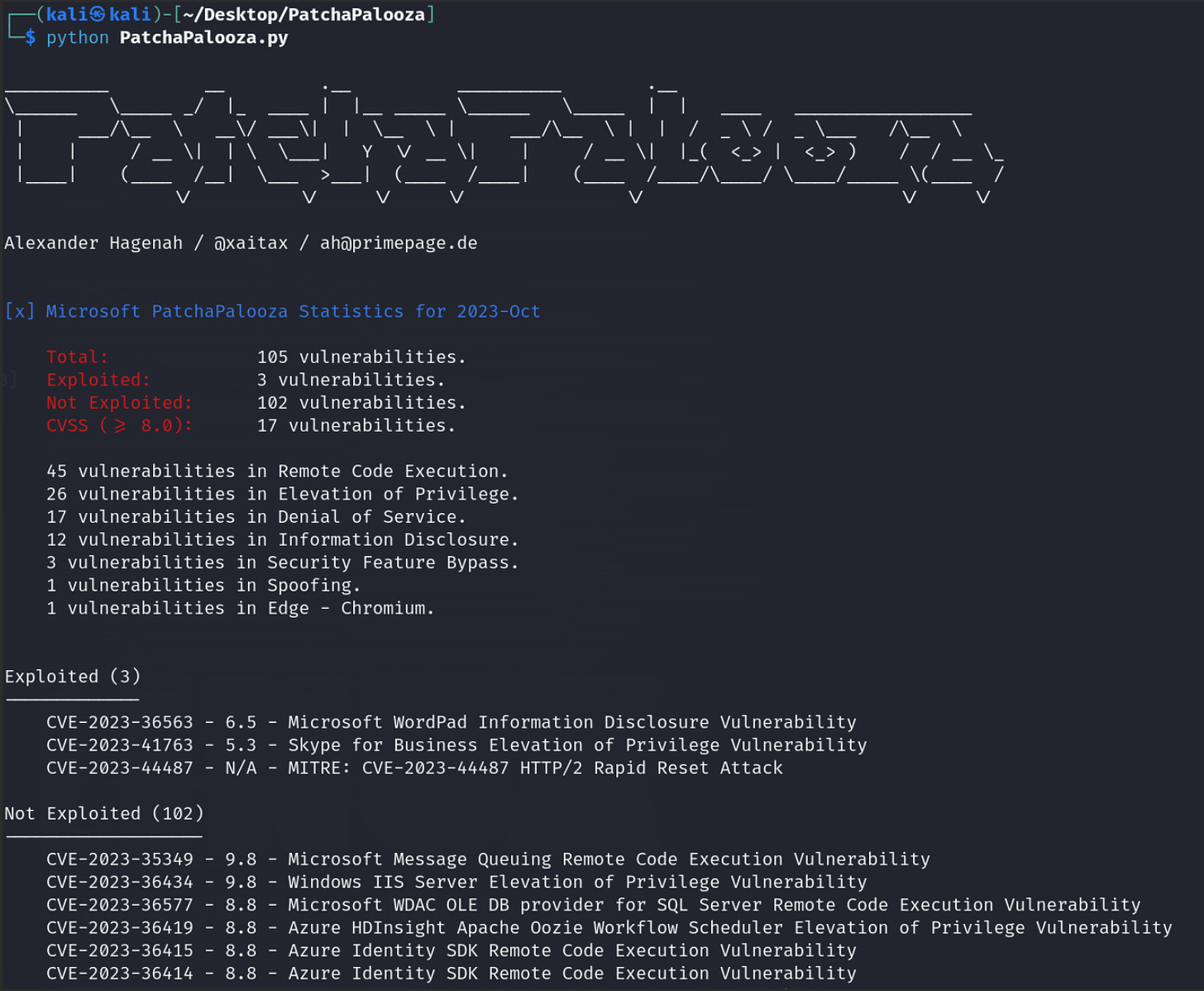
New tool—PatchaPalooza: Cybersecurity researcher Alexander Hagenah has released PatchaPalooza, a tool that provides an analysis of Microsoft Patch Tuesday updates. Also available as a standalone interactive website.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the internet-melting 1988 Morris Worm and how cyber security has changed since then.
如有侵权请联系:admin#unsafe.sh