- Spammers are exploiting the "Release scores" feature of Google Forms quizzes to deliver email.
- The emails originate from Google's own servers and consequently may have an easier time bypassing anti-spam protections and finding the victim's inbox.
- Volumes of these messages hovered near noise levels but have recently spiked into the hundreds.
Cisco Talos has recently observed an increase in spam messages abusing a feature of quizzes created within Google Forms. In particular, spammers have discovered that they can create a new quiz in Google Forms, use the victim’s email address to respond to the quiz, and then abuse the “Release Scores” feature of the Google Form to deliver their spam to the victim. Because the spam messages emanate from Google itself, the messages have a good chance of landing in the victim’s inbox.
Cisco Talos examined a recent spam campaign in which the Subject headers all contained the text, “Score released:”. During our investigation, we quickly realized these messages were being generated through a feature of Google Forms’ quizzes. Google Forms abuse has been present in spam attacks for several years, though our investigation showed that this particular feature of Google Forms quizzes was not very heavily abused to send spam until relatively recently.
Google Forms’ quizzes
In Google Forms, when creating a new form, an author can choose to “Make this a quiz.” Choosing to release grades “Later, after manual review,” enforces the collection of email addresses in the quiz.
Elsewhere, under the settings for Responses, choosing “Responder input” allows a spammer to fill in their form using any victim’s email address.
Once the form is configured in this way, a link to the form can be obtained and accessed by the spammer. The spammer then fills out the form using the victim’s email address and submits it. Whether the question in the quiz is answered does not matter. Afterward, the fake quiz responses generated by the attacker can be viewed.
Clicking the “Release scores” dialog in the upper right will prompt the form owner to “Send emails and release” the scores. The message delivered as part of the email can be customized to include any text or URL, and the message will then be delivered by Google using the “From:” address of the Google account that created the quiz. Because the email messages generated using this technique emanate from Google’s servers, they stand a good chance of being delivered to the victim’s inbox.
Google Forms quiz spam used in an elaborate cryptocurrency scam
A recent example of one of these Google Forms quiz score release spam attacks appears below.
When the victim clicks the “View” button in this email, they are directed to the fake form response generated by the spammer.
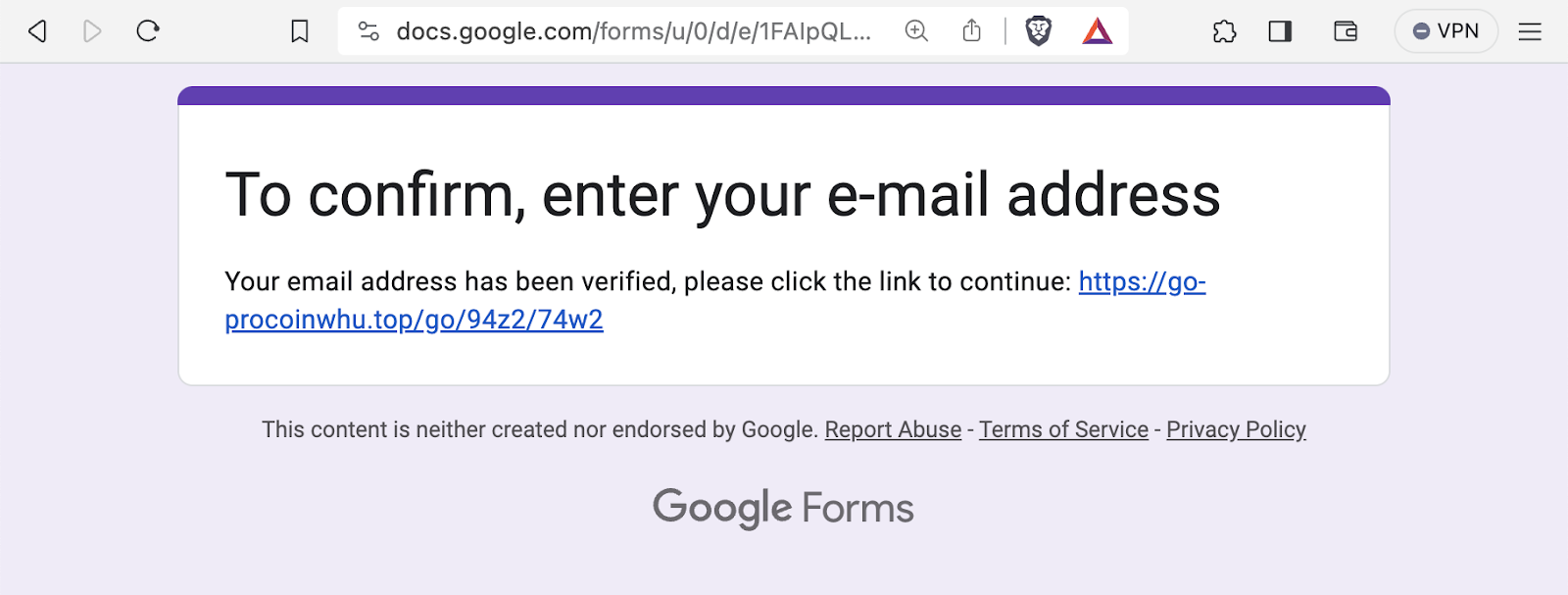
In this particular form response, the spammer has provided a link “>>> GO TO THE SITE” which points to another Google Form that asks the victim to confirm their email address. At this stage of the attack, when an email address is entered into the second form, the victim is provided a form response containing a link to an external website: go-procoinwhu[.]top.
The go-procoinwhu[.]top domain was created only just created on October 28, 2023, but it is already seeing a large uptick in the number of DNS queries requesting it.
Clicking the go-procoinwhu[.]top link in the Google Form response results in a 302 redirect from Cloudflare, which directs the victim to https://hdlgr[.]dudicyqehama[.]top/, which is also hosted by Cloudflare. This domain was also recently created (October 25, 2023), and exhibits a very similar DNS traffic pattern in Umbrella Investigate.
When the victim navigates to the dudicyqehama.top website, they are presented with an elaborate scam website that claims that the victim possesses more than 1.3 Bitcoin in their account as a result of “automatic cloud Bitcoin mining,” which the site claims is worth more than $46,000 USD.
Once the victim clicks “Continue,” they are brought into the main website “login page.” The username and password are pre-filled into the login form, so the victim only needs to click the “Sign in” button.
Once logged in, it is readily apparent that the website goes to great lengths to appear legitimate. The site even includes a group chat feature near the bottom where you can see various other users discussing cryptocurrency-related topics. As a logged-in user, the victim can even comment. Watching the text scroll by in the chat, it becomes apparent that they are recycling the same comments over and over, and these are not real users.
When the victim attempts to claim their Bitcoin from the main site, they are redirected to what looks like a live chat with an agent named “Sophia.”
Sophia chats with us for a moment before sending a form to fill out to collect the Bitcoin.
The form asks the victim to fill in their name, email address and the cashout method the user prefers.
Once the form has been filled out and submitted, the victim is again redirected back to the chat with Sophia, who proceeds to give us a button to kick off the currency exchange of BTC into USD.
Now, we can begin to see the end game for this particular scam. The victim is instructed that to claim the almost $48,000 USD, the victim must pay an “exchange fee” of 0.25%, or $64 USD.
When the victim clicks “Exchange Bitcoin,” they are presented with one last form where the victim is prompted to enter their name, email and phone number.
Clicking “Pay” brings up a QR code for the BTC wallet of the spammers. Fortunately, nobody has fallen for this scam and paid the attackers, as the connected Bitcoin wallet was empty as of November 6, 2023.
The amount of setup work necessary to conduct a spam attack such as this, combined with the extraordinary attention to detail put into the social engineering for the subsequent cryptocurrency scam, demonstrates just how far cybercriminals will go when it comes to separating victims from even a small amount of money. As is usually the case with scams such as this, when something sounds too good to be true, it often is.
IOCs for this research can also be found in our GitHub repository here.