There is a seemingly never-ending quest to find the right security tools that offer the right capabilities for your organization.
SOC teams tend to spend about a third of their day on events that don't pose any threat to their organization, and this has accelerated the adoption of automated solutions to take the place of (or augment) inefficient and cumbersome SIEMs.
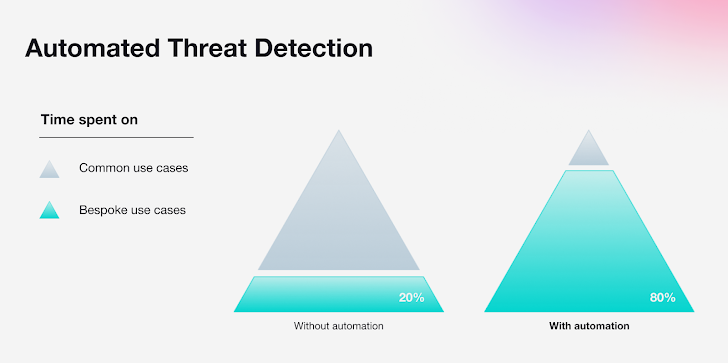
With an estimated 80% of these threats being common across most organizations, today's SOCs are able to confidently rely on automation to cover this large percentage of threat signals.
But, while it is true that automation can greatly improve the efficiency and effectiveness of security teams, it will never be able to cover all detection and response use cases infallibly.
In the recently released GigaOm Radar for Autonomous Security Operations Center (SOC), they accurately state that "the SOC will not—and should not—be fully autonomous."
As more vendors attempt to challenge the dominant players in the SIEM category, demand is increasing for solutions that offer automation, which can cover 80%, while also offering customization capabilities to cover bespoke use cases - the remaining 20%.
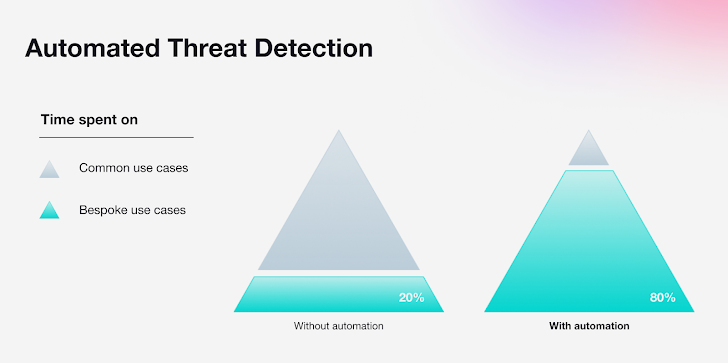 |
| Automation can free up valuable time for security teams, so they can spend the majority of their time on use cases unique to their organization. |
THE 80%: AUTOMATION
With the continual surge in global data creation, organizations are inevitably seeing an uptick in the number of alerts managed by security teams.
This may seem daunting for overworked security teams, but advanced vendor offerings are implementing automation across various stages of the SOC workflow, helping teams enhance their speed and effectiveness.
The four key phases where we are seeing automation are:
- Data Ingestion and Normalization: Automating data ingestion and normalization enables teams to process vast amounts of data from diverse sources efficiently, establishing a robust foundation for subsequent automated processes.
- Detection: Transferring the responsibility of creating a significant portion of detection rules allows security analysts to concentrate on threats unique to their organization or market segment.
- Investigation: Automation can alleviate the burden of manual and repetitive tasks, expediting investigation and triage processes.
- Response: Automatic responses to known and discovered threats facilitate swift and accurate mitigation. This can include connectivity to case management, SOAR solutions, ITSM, etc.
Modern SIEM replacement vendors, such as Hunters, leverage pre-built detection rules, integrate threat intelligence feeds, and automatically enrich and cross-correlate leads. These automated processes alleviate large amounts of tedious workloads, empowering security teams to easily manage the large majority of alerts.
 |
| Automatic enrichment and cross-correlation create comprehensive stories, making tracking lateral movements much more efficient. |
THE 20%: CUSTOMIZATION
Although automating the above phases of the workflow have been massive in boosting efficiencies for many SOCs, there will always remain the need for a certain degree of customization.
Each organization has bespoke needs and requirements depending on industry- or company-specific use cases. This means that even if automated and built-in capabilities can address 80% of the general use cases and tasks, additional capabilities are needed to cover the remaining 20%.
"Customization" can mean a lot of different things, but the main requirement for security teams is that they have both the flexibility to cover unique use cases and the ability to scale their capabilities. Let's look at a few examples of use cases where this can be beneficial:
- Ingesting custom data sources: each organization has multiple data sources they ingest with different log formats. Many vendors may not have pre-built integrations to ingest from every single data source, so if a vendor does offer that capability, it can be a huge lift. This is especially for organizations that are currently utilizing (or will soon be moving to) data lakes to maintain data for multiple purposes.
- Detection-as-code: this has become a massive buzzword in the security industry, but with good reason. Detection-as-code offers a variety of advantages for detection engineers, like improved and efficient development lifecycle, and for large organizations to more effectively manage multi-tenancy environments. If you aren't familiar with the concept, detection-as-code utilizes APIs and deployment pipelines to provide desired auditing capabilities, making the development lifecycle for security operations much closer to that of traditional software development. This approach improves processes to help teams develop higher-quality alerts or reuse code within your organization so you don't have to build every new detector from scratch. It also helps push detection engineering left in the development lifecycle, removing the need to manually test and deploy detectors.
- Scalable business context: Whether it be entities with specific sensitivity levels (like crown jewels), data from different business units or different geographies, or siloed data from different sources, it takes a lot of time and effort to piece together information in a way that's understandable and actionable. Leveraging an SIEM alternative that gives you the ability to manage all this via API brings expanded efficiencies and scalability that not every vendor provides.
Conclusion
Building out an effective SOC has always been, and will continue to be, a nuanced effort.
There is no one-size-fits-all solution when it comes to security tools. It is important to offer ways for organizations to not just customize for their use cases, but it is vital that they are able to combine this "customization" with the already existing automated capabilities that vendors offer.
It has become a necessity to look for vendors that can offer both a hands-on approach to customizing tools, but to do so in a way to bolster the autonomous portions of their offerings.
SIEM replacement vendors like Hunters, which have been named leaders in GigaOm's previously mentioned report on autonomous SOC, are known for their easy-to-use and pre-built capabilities. And, to ensure that they serve the needs of security teams, are continuing to add innovative customization features that allow organizations to tailor their security strategy to their unique requirements.
Covering the 80% is vital, but addressing the remaining 20% will set your security team above the rest.
Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post.