
2023-11-15 00:46:24 Author: therecord.media(查看原文) 阅读量:10 收藏
A cyberattack on a North Carolina county has forced officials to call in the state’s national guard for assistance.
In a message to residents on Tuesday, Bladen County said it became the victims of a cyberattack last week. The county — tucked in the southern point of the state about an hour away from Wilmington — is home to nearly 30,000 residents.
While the attackers were able to access county data, the attack went beyond information theft.
Ransomware was not mentioned in the notice but the county’s IT staff discovered “irregularities” in their system and called in the North Carolina Joint Cybersecurity Task Force, a team of outside experts from the NC National Guard, the NCLGISA Cybersecurity Strike Team, NC Emergency Management, and the NC Department of IT to launch a forensic investigation and help secure their servers.
North Carolina is one of only a handful of states that have banned government entities from paying ransoms connected to ransomware attacks and have prescribed a detailed playbook for government organizations to follow in the event of attacks like this.
“It is important to share that our County has emergency preparedness plans specifically for situations like these, and at no time did any life safety services cease to operate. We followed our contingency plan and all emergency services have been fully operational throughout the incident,” said Rodney Hester, chairman of the Bladen County Board of Commissioners.
“Our dedicated IT professionals are working diligently with some of the country’s leading experts in cybersecurity to return Bladen County Government systems back to normal as quickly as possible, and they are making incredible progress.”
Hester confirmed that county data was accessed by the hackers and that the county government is operating in “limited capacity” because they do not currently have access to all of their systems.
Many of the county systems that rely on internal servers or access to the internet will be impacted, according to Hester, who added that county staff have contingency plans for utilizing alternative methods to conduct public business.
No systems relating to state or other levels of government appear to have been impacted, he noted.
The county did not respond to requests confirming whether it is a ransomware attack.
In spite of the ban on ransom payments, ransomware gangs have repeatedly targeted state and local government entities in the last year.
A Charlotte suburb was hit with ransomware in July and Raleigh’s Housing Authority was attacked by hackers in May.
The state — which was the first to ban ransom payments — drew controversy for the measure. Cybersecurity experts say that while bans are well-intentioned, they will likely be ignored and further penalize victims, who will now have to weigh the legal ramifications of payments against the need to restore business functions.
When the law was passed last year, some worried that it would effectively serve as an additional way for ransomware gangs to extort victims, allowing them to threaten organizations with not only the leak of stolen data but also with unverified claims of being paid a ransom in violation of state law.
Other experts wondered whether ransomware groups would specifically go after government organizations in North Carolina as a de facto warning to other states not to pass similar bans.
Local governments and counties across the U.S. continue to be ripe targets for ransomware groups. While incidents involving large counties like Dallas County draw the most headlines, dozens of states are affected by ransomware attacks on a weekly basis.
The Tax Collector in St. Lucie County, Florida posted a notice on its website on Monday warning residents of a county-wide network failure. All of their offices are now operating by appointment and services are limited.
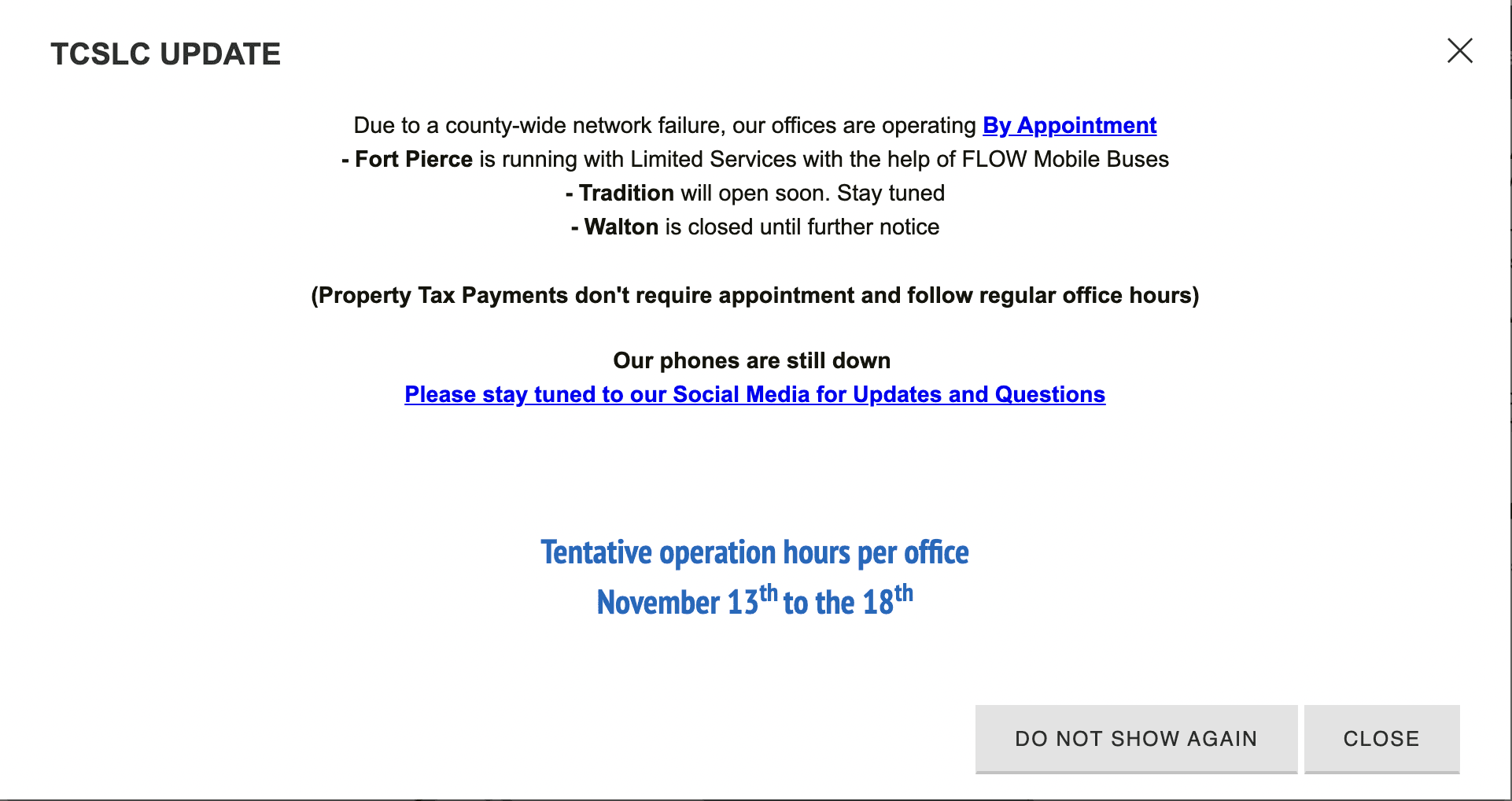
All of their phone lines are down and officials said the issues would last from Monday to Saturday.
On Monday, the AlphV/Black Cat ransomware gang claimed the attack, saying they stole an undisclosed amount of data. Florida is the only other U.S. state to have banned government entities from paying ransoms.
Get more insights with the
Recorded Future
Intelligence Cloud.
No previous article
No new articles
Jonathan Greig
Jonathan Greig is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.
如有侵权请联系:admin#unsafe.sh
