
2023-11-15 12:31:22 Author: therecord.media(查看原文) 阅读量:12 收藏
The top cybersecurity agency in the U.S. warned that hackers are exploiting three vulnerabilities disclosed by Microsoft on Tuesday.
The Cybersecurity and Infrastructure Security Agency (CISA) added CVE-2023-36033, CVE-2023-36025 and CVE-2023-36036 to its Known Exploited vulnerabilities catalog on Tuesday, giving federal civilian agencies until December 5 to patch the issues.
Several different cybersecurity experts said the three vulnerabilities stood out among the dozens of bugs disclosed by Microsoft in the company’s latest Patch Tuesday release.
CVE-2023-36033 — which affects Microsoft Windows Desktop Window Manager — was of particular concern because it is a zero-day vulnerability with a CVSS score of 7.8 and can be exploited without the need for high-level privileges or user interaction. A zero-day is a vulnerability that was previously unknown to developers or defenders.
“Attackers exploiting this flaw could gain SYSTEM privileges, making it an efficient method for escalating privileges, especially after initial access through methods like phishing. It affects Microsoft Windows 10 and later, as well as Microsoft Windows Server 2019 and subsequent versions,” said Mike Walters, president and co-founder of cybersecurity firm Action1.
Walters noted that Microsoft has confirmed that a proof of concept is available and that it is currently being exploited.
Immersive Labs’ Natalie Silva said the Windows Desktop Window Manager handles tasks like window composition, visual effects, and desktop rendering. After sending a malicious document, for example, a hacker could use the vulnerability to elevate their access in a victim network.
Similarly, CVE-2023-36036 was concerning to Saeed Abbasi, manager of vulnerability and threat research at Qualys, because it affects the Windows Cloud Files Mini Filter Driver, a component essential to the functioning of cloud-stored files on Windows systems.
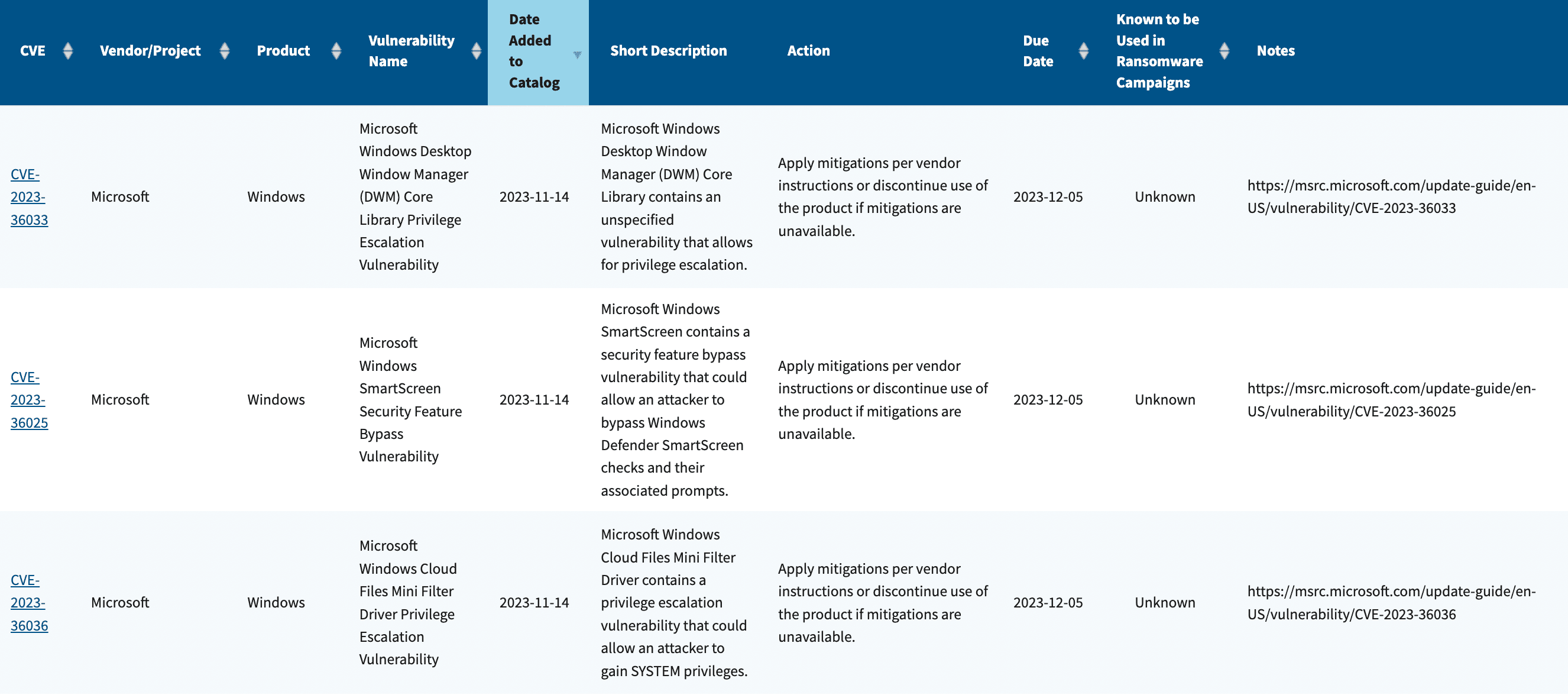 Image: CISA
Image: CISA
“The widespread presence of this driver in almost all Windows versions amplifies the risk, providing a broad attack surface. It is currently under active attack and poses a significant risk, especially when paired with a code execution bug,” Abbasi said.
Immersive Labs senior director of threat research Kev Breen added that Mini Filters Drivers are also used by security products, and depending on the nature of the vulnerability and exploit — it could be missed by security tools.
Walters said CVE-2023-36036 shares traits with CVE-2023-36033, carries a CVSS score of 7.8 and affects Microsoft Windows 10 and later, as well as Microsoft Windows Server 2008 and onwards.
The third vulnerability added is CVE-2023-36025 — which carried the highest CVSS score of them all. Breen said it was rated an 8.8 out of 10 and affects a Windows SmartScreen Security Feature.
“Listed as actively exploited in the wild by attackers and a SmartScreen Security Feature Bypass, Microsoft is very light on the details here, only saying that the exploitation has been detected and – in order to exploit this vulnerability – a user would have to click on a specially crafted shortcut link (.url) or a hyperlink to a shortcut file,” he said.
“SmartScreen is used by Windows to prevent phishing attacks or access to malicious websites and the download of untrusted or potentially malicious files. This vulnerability suggests that a specially crafted file could be used by attackers to bypass this check, reducing the overall security of the operating system.”
Breen noted that organizations should not solely rely on SmartScreen, and that this should be part of an in-depth defensive posture that includes other tools and processes to help provide overall cyber resilience.
The bug is not complex and does not require high privileges to exploit. Walters said it allows hackers to circumvent Windows Defender SmartScreen checks and prompts. Exploitation allows attackers to prevent Windows Smart Screen from blocking malware.
CISA said it is unclear whether ransomware gangs are exploiting these vulnerabilities. In total, Microsoft unveiled 58 vulnerabilities and five zero-days, three of which were added to CISA’s catalog.
Cisco, Adobe, Google, Fortinet, and other companies announced vulnerabilities alongside Microsoft.
Get more insights with the
Recorded Future
Intelligence Cloud.
No previous article
No new articles
Jonathan Greig
Jonathan Greig is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.
如有侵权请联系:admin#unsafe.sh
