A set of novel attack methods has been demonstrated against Google Workspace and the Google Cloud Platform that could be potentially leveraged by threat actors to conduct ransomware, data exfiltration, and password recovery attacks.
"Starting from a single compromised machine, threat actors could progress in several ways: they could move to other cloned machines with GCPW installed, gain access to the cloud platform with custom permissions, or decrypt locally stored passwords to continue their attack beyond the Google ecosystem," Martin Zugec, technical solutions director at Bitdefender, said in a new report.
A prerequisite for these attacks is that the bad actor has already gained access to a local machine through other means, prompting Google to mark the bug as not eligible for fixing "since it's outside of our threat model and the behavior is in line with Chrome's practices of storing local data."
However, the Romanian cybersecurity firm has warned that threat actors can exploit such gaps to extend a single endpoint compromise to a network-wide breach.
The attacks, in a nutshell, rely on an organization's use of Google Credential Provider for Windows (GCPW), which offers both mobile device management (MDM) and single sign-on (SSO) capabilities.
This enables administrators to remotely manage and control Windows devices within their Google Workspace environments, as well as allows users to access their Windows devices using the same credentials that are used to login to their Google accounts.
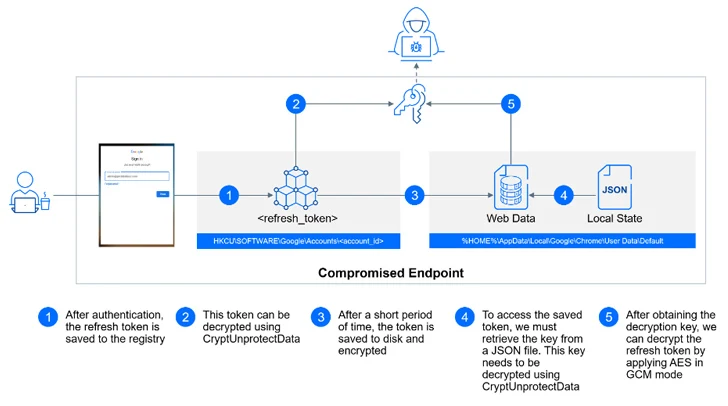
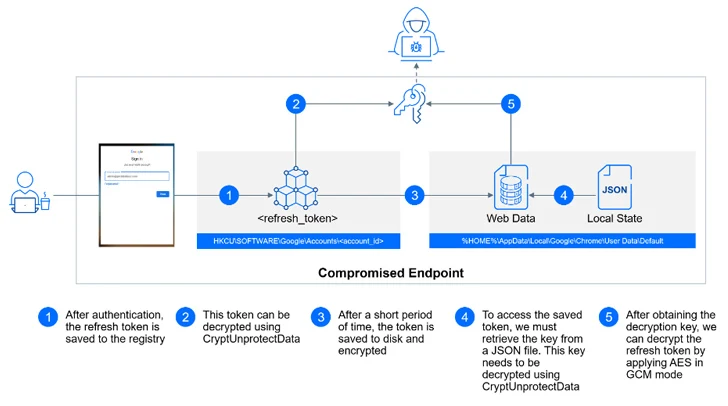
GCPW is designed to use a local privileged service account named Google Accounts and ID Administration (GAIA) to seamlessly facilitate the process in the background by connecting to Google APIs for verifying a user's credentials during the sign-in step and storing a refresh token to obviate the need for re-authentication.
With this setup in place, an attacker with access to a compromised machine can extract an account's refresh OAuth tokens, either from the Windows registry or from the user's Chrome profile directory, and bypass multi-factor authentication (MFA) protections.
The refresh token is subsequently utilized to construct an HTTP POST request to the endpoint "https://www.googleapis[.]com/oauth2/v4/token" to obtain an access token, which, in turn, can be abused to retrieve, manipulate, or delete sensitive data associated with the Google Account.
A second exploit concerns what's called the Golden Image lateral movement, which focuses on virtual machine (VM) deployments and takes advantage of the fact that creating a machine by cloning another machine with pre-installed GCPW causes the password associated with the GAIA account to be cloned as well.
"If you know the password to a local account, and local accounts on all machines share the same password, then you know the passwords to all machines," Zugec explained.
"This shared-password challenge is similar to having the same local administrator password on all machines that has been addressed by Microsoft's Local Administrator Password Solution (LAPS)."
The third attack entails access to plaintext credentials by leveraging the access token acquired using the aforementioned technique to send an HTTP GET request to an undocumented API endpoint and get hold of the private RSA key that is required to decrypt the password field.
"Having access to plaintext credentials, such as usernames and passwords, represents a more severe threat," Zugec said. "This is because it enables attackers to directly impersonate legitimate users and gain unrestricted access to their accounts, potentially leading to complete account takeover."
Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post.