2023-11-20 17:5:53 Author: securityaffairs.com(查看原文) 阅读量:19 收藏
DarkCasino joins the list of APT groups exploiting WinRAR zero-day
Pierluigi Paganini
November 20, 2023

The DarkCasino APT group leveraged a recently disclosed WinRAR zero-day vulnerability tracked as CVE-2023-38831.
Researchers at cybersecurity firm NSFOCUS analyzed DarkCasino attack pattern exploiting the WinRAR zero-day vulnerability tracked as CVE-2023-38831. The economically motivated APT group used specially crafted archives in phishing attacks against forum users through online trading forum posts.
“DarkCasino is an APT threat actor with strong technical and learning ability, who is good at integrating various popular APT attack technologies into its attack process. In the early days, the APT group DarkCasino mainly drew on the attack idea of an APT attacker named Evilnum and used malicious shortcuts, image steganography and other technologies to realize phishing attacks.” reads the report published by NSFOCUS.
NSFOCUS Research Labs pointed out that exploitation of the CVE-2023-38831 flaw can be integrated into watering hole and phishing attacks. The researcher explained that some CVE-2023-38831 vulnerability exploitation variants are hard to detect and can allow bypassing endpoint protection solutions.
During its initial phase, DarkCasino primarily conducted operations in Mediterranean countries and various other Asian nations, utilizing online financial services
Recently the group changed phishing methods and aimed at users of cryptocurrencies worldwide, even including non-English-speaking Asian countries such as South Korea and Vietnam.
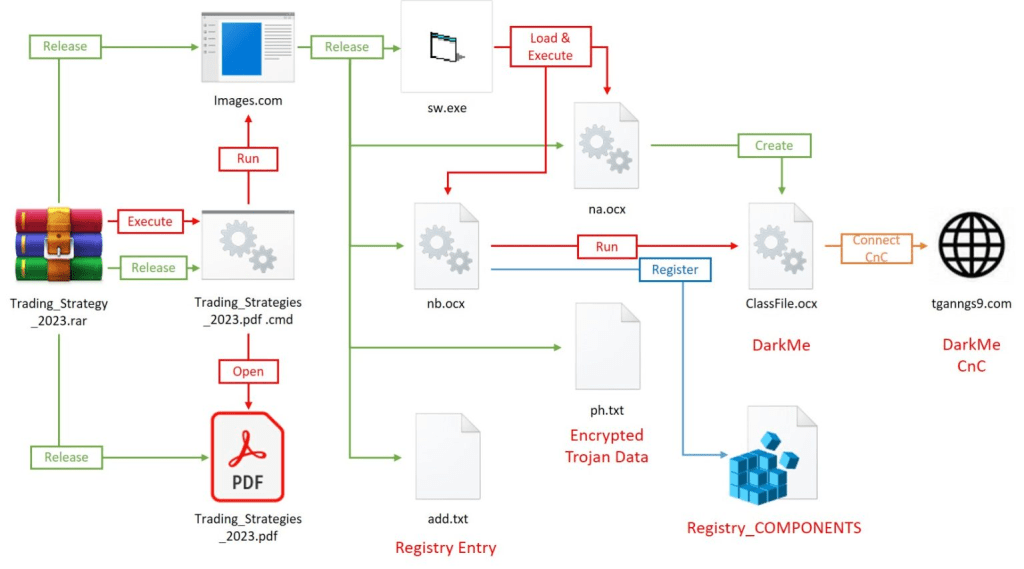
Since April 2023, the DarkCasino APT group has started exploiting the vulnerability to deliver the Trojan DarkMe. The malware supports multiple features, such as collecting host information, taking screenshots, file manipulation, registry manipulation, cmd command execution, self-update, and maintaining persistence.
NSFOCUS Research Labs observed DarkCasino implementing two attack processes using specially crafted weaponized archives. The main difference between the two processes is the storage form of the Trojan.
Multiple APT groups have been observed exploiting the CVE-2023-38831 vulnerability, including Dark Pink, APT28, APT29, Sandworm, APT40, Ghostwriter, and Konni.
“The WinRAR vulnerability CVE-2023-38831 brought by the APT group DarkCasino brings uncertainties to the APT attack situation in the second half of 2023.” concludes the report. “NSFOCUS Research Labs has also captured batch-generated vulnerability exploitation files decoyed by transaction bills. This phenomenon indicates that large phishing attack controllers have also incorporated this vulnerability into their phishing attack processes, which heralds more victims of WinRAR vulnerability exploitation in the future.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, DarkCasino APT)
如有侵权请联系:admin#unsafe.sh
