关于Linux的安全检测,我以前的文章介绍了好几篇,有《工具:Linux Malware Detect》《工具:Linux安全检查GScan》《工具:Linux 应急检测脚本》《Windows/Linux入侵手工排查》《记录任何 Linux 进程访问了哪些文件》。
攻防*1000:1规则*:
防御者需要知道成千上万种入侵系统的方法。攻击者只需正确一次。
攻击者需要知道成千上万种掩盖踪迹的方法掩盖行踪。防御者需要发现错一次。
掌握下面的关注点,我们对入侵的检测就能做到游刃有余了;非常不错的Linux取证五个知识领域。
一、重点关注所说的 Linux 取证的五个主要领域:
进程– 可疑进程和网络活动。
目录– 包含恶意负载、数据或工具的可疑目录,允许横向移动到网络中。
文件– 恶意的、可能被篡改的或在 Linux 主机上不合适的文件。
用户– 检查可疑用户活动的区域。
日志– 日志文件篡改检测和公共区域,用于检查有人掩盖踪迹的迹象。
Processes
Large amounts of RAM:
top
Process tree:
ps -auxwf
Open network ports or raw sockets:
netstat -nalpn
etstat -plant
ss -a -e -i
lsof [many options]
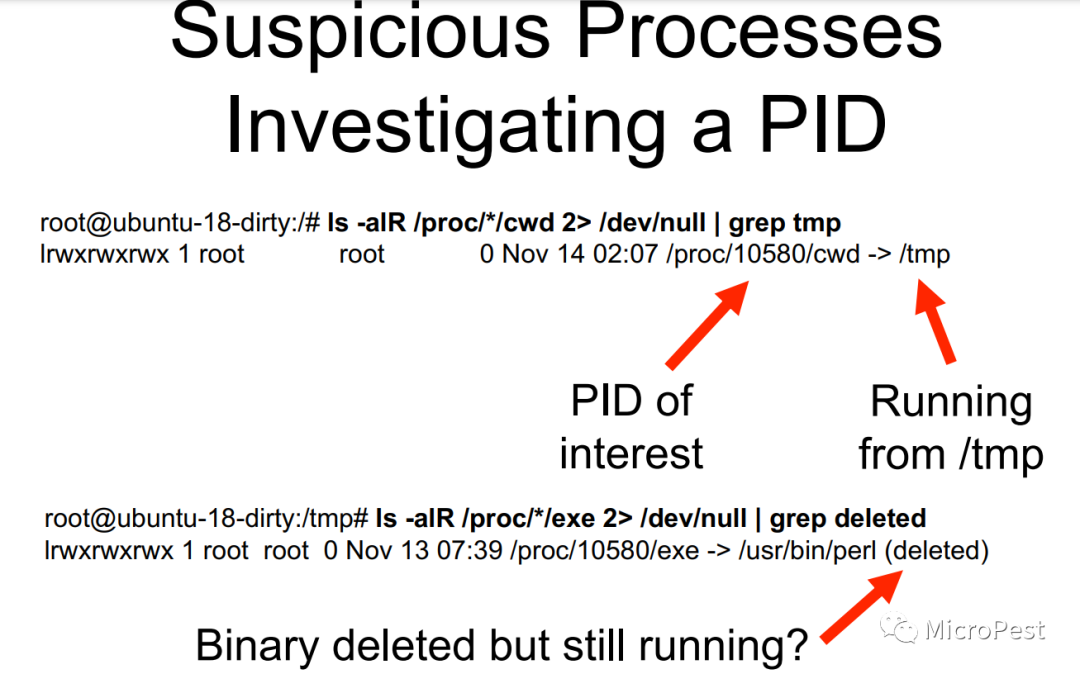
Deleted binaries still running:
ls -alR /proc/*/exe 2> /dev/null | grep deleted
Process command name/cmdline:
strings /proc/<PID>/comm
strings /proc/<PID>/cmdline
Real process path:
ls -al /proc/<PID>/exe
Process environment:
strings /proc/<PID>/environ
Process working directory:
ls -alR /proc/*/cwd
Process running from tmp, dev dirs:
ls -alR /proc/*/cwd 2> /dev/null | grep tmp
ls -alR /proc/*/cwd 2> /dev/null | grep dev
Directories
Commonly targeted directories:
/tmp, /var/tmp, /dev/shm, /var/run,/var/spool, user home directories
List and delimit spaces, etc. in names:
ls -lap
List all hidden directories:
find / -type d -name ".*"
Files
Immutable files and directories:
lsattr / -R 2> /dev/null | grep "\----i"
Find SUID/SGID files:
find / -type f \( -perm -04000 -o -perm -02000 \) -exec ls -lg {} \;
Files/dirs with no user/group name:
find / \( -nouser -o -nogroup \) -exec ls -lg {} \;
List all file types in current dir:
file * -p
Find executables anywhere, /tmp, etc.:
find / -type f -exec file -p '{}' \; | grep ELF
find /tmp -type f -exec file -p '{}' \; | grep ELF
Find files modified/created within last day:
find / -mtime -1
Persistence areas:
/etc/rc.local, /etc/initd, /etc/rc*.d, /etc/modules, /etc/cron*, /var/spool/cron/*
Package commands to find changed files:
rpm -Va | grep ^..5.
debsums -c
Users
Find all ssh authorized_keys files:
find / -name authorized_keys
History files for users:
find / -name .*history
History files linked to /dev/null:
ls -alR / 2> /dev/null | grep .*history | grep null
Look for UID 0/GID 0:
grep ":0:" /etc/passwd
Check sudoers file:
cat /etc/sudoers and /etc/group
Check scheduled tasks:
crontab -l
atq
systemctl list-timers --all
Logs
Check for zero size logs:
ls -al /var/log/*
Dump audit logs:
utmpdump /var/log/wtmp
utmpdump /var/run/utmp
utmpdump /var/log/btmp
last
lastb
Find logs with binary in them:
grep [[:cntrl:]] /var/log/*.log
二、具体例子:
这是我的第293篇,今年完成第300篇算是有点希望了!
如有侵权请联系:admin#unsafe.sh