2023-11-23 05:49:21 Author: securityaffairs.com(查看原文) 阅读量:20 收藏
New InfectedSlurs Mirai-based botnet exploits two zero-days
Pierluigi Paganini
November 22, 2023

Mirai-based botnet InfectedSlurs has been spotted exploiting two zero-day RCE flaws to compromise routers and video recorder (NVR) devices.
Akamai discovered a new Mirai-based DDoS botnet, named InfectedSlurs, actively exploiting two zero-day vulnerabilities to infect routers and video recorder (NVR) devices.
The researchers discovered the botnet in October 2023, but they believe it has been active since at least 2022. The experts reported the two vulnerabilities to the respective vendors, but they plan to release the fixes in December 2023.
In October, Akamai’s Security Intelligence Response Team (SIRT) noticed an anomalous activity to the company’s honeypots targeting a rarely used TCP port.
“In late October 2023, we noticed a small uptick in activity to our honeypots targeting a rarely used TCP port. The activity started out with a small burst, peaking at 20 attempts per day, and then thinned out to an average of two to three per day, with some days completely devoid of attempts.” reads the analysis published by Akamai. “Until November 9, 2023, the vulnerable devices being targeted were unknown. The probes were of low frequency and appeared to first attempt an authentication via a POST request and then, upon success, attempt a command injection exploitation.”
The company did not reveal the names of the impacted vendors.
The researchers determined that the bot also used default admin credentials to install the Mirai variants.
A close look at the ongoing campaign revealed that the bot also targets wireless LAN routers built for hotels and residential applications.
The InfectedSlurs is based on the JenX Mirai malware variant that in 2018 leveraged the Grand Theft Auto videogame community to infect devices.
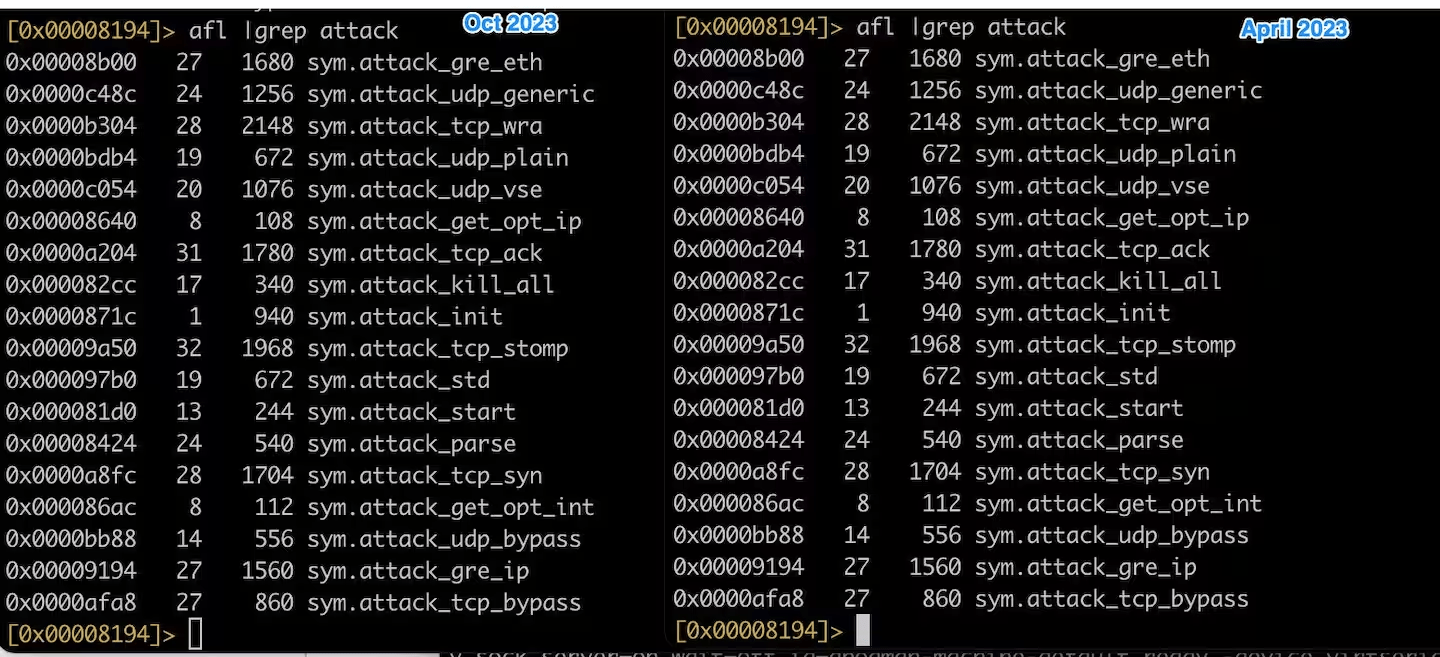
Akamai states that the InfectedSlurs code is quite similar to the one of the original Mirai botnet.
The experts noted that the variant used in the October 2023 campaign employs the same functions in the same memory locations as a Mirai variant used in April 2023.

Other botnets, such as the hailBot Mirai variant, also utilized the C2 infrastructure employed in this campaign. The researchers also noticed mentions of some of the C2 infrastructure from a deleted Telegram user in the infamous DDoS marketplace channel DStatCC.
“The Akamai SIRT is working with CISA/US-CERT, and JPCERT to notify vendors of the impacted devices. We’ve agreed to not publish full details to allow the vendor time to roll out patches, but given that these vulnerabilities are being actively exploited, we’re providing Snort and YARA rules to help defenders identify exploit attempts and possible infections in their environments.” concludes the report that includes Snort rules and Indicators of Compromise (IoCs).
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, botnet)
如有侵权请联系:admin#unsafe.sh