2023-11-28 20:32:43 Author: securityaffairs.com(查看原文) 阅读量:7 收藏
Daixin Team group claimed the hack of North Texas Municipal Water District
Pierluigi Paganini
November 28, 2023

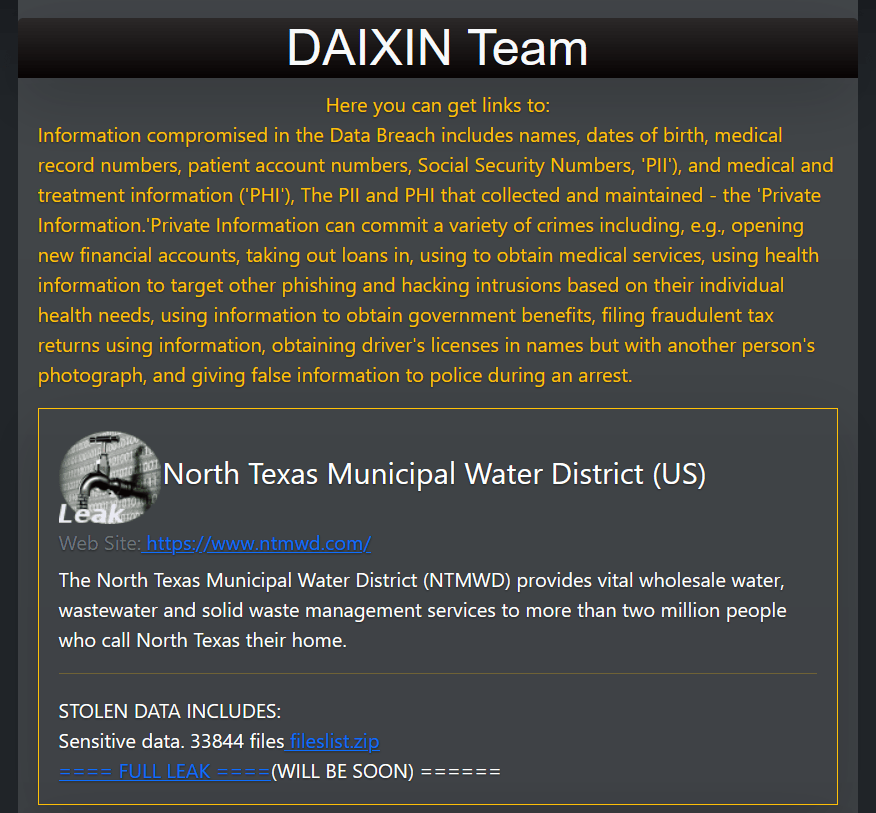
The Daixin Team group claims to have hacked the North Texas Municipal Water District (US) and threatened to leak the stolen data.
The North Texas Municipal Water District (NTMWD) is a regional water district that provides wholesale water, wastewater treatment, and solid waste services to a group of member cities and customers in North Texas, United States. It is a governmental entity established to address the water supply needs of its member communities and promote responsible water resource management.
The Daixin Team group added NTMWD to the list of victims on its Tor leak site. The gang claims to have stolen a huge amount of sensitive data from the company and threatens to publish it.
The ransomware gang claims the theft of board meeting minutes, internal project documentation, personnel details, audit reports, and more. The leak of the data puts the company at risk of frauds in the next months.
In the meantime, the company declared they are just “Experiencing Interruption in Phone Service”.
At the time the group has published a .txt file that contains the list of the alleged stolen data.

The group claims to have stolen a total of 33844 files.
In October 2022, CISA, the FBI, and the Department of Health and Human Services (HHS) warned that the Daixin Team cybercrime group is actively targeting U.S. businesses, mainly in the Healthcare and Public Health (HPH) Sector, with ransomware operations.
The Daixin Team is a ransomware and data extortion group that has been active since at least June 2022. The group focused on the HPH Sector with ransomware operations that aimed at deploying ransomware and exfiltrating personal identifiable information (PII) and patient health information (PHI) threatening to release the stolen data if a ransom is not paid.
The Daixin Team group gains initial access to victims through virtual private network (VPN) servers. In one successful attack, the attackers likely exploited an unpatched vulnerability in the organization’s VPN server. In another compromise, the group leveraged on compromised credentials to access a legacy VPN server. The threat actors obtained the VPN credentials through phishing attacks.
After gaining access to the target’s VPN server, Daixin actors move laterally via Secure Shell (SSH) and Remote Desktop Protocol (RDP).
The alert published by the federal agencies includes indicators of compromise (IOCs) and MITRE ATT&CK tactics and techniques.
The attackers use to escalate privileges through various methods, such as credential dumping and pass the hash, to deliver the ransomware.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, North Texas Municipal Water District)
如有侵权请联系:admin#unsafe.sh