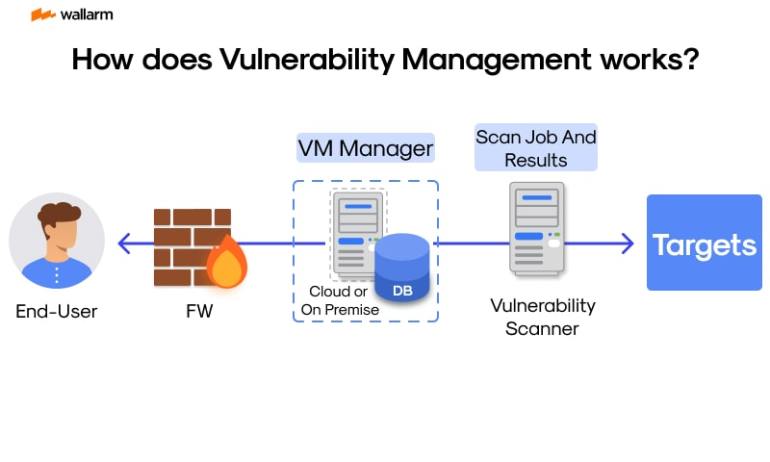
In any strategy aimed at combating cyber threats, the essential peace is the adequate regulation of possible frailties or susceptibility points. This concept embodies a broad spectrum of actions covering the spotting, categorizing, ranking, and rectification of possible risk areas within a digital infrastructure or network. These areas of risk, stemming from programming errors, system misalignments, or frail security codes, may act as hidden gateways for invasions if not appropriately addressed.
Imagine your digital network or system as a safeguarded fortress. Entryways such as doors, windows, or concealed entrances are analogous to susceptibility points. Absent appropriate safeguards, these points might transform into tools that cyber invaders use to breach your digital fortress (your system or network, in this illustration). Therefore, susceptibility regulation operates as the initial line of defense, constantly scrutinizing and shielding potential gateways to thwart unwanted breaches.
<code class="language-python">class SusceptibilitySupervisor:
def __init__(self, digital_entity):
self.digital_entity = digital_entity
self.risk_areas = self.uncover_risk_areas()
def uncover_risk_areas(self):
# Complete an extensive system inspection to aggregate a list of potential
risk areas
pass
def categorize_risk_areas(self):
# Sort the exposed risk areas based on their potential hazard level
pass
def rank_risk_areas(self):
# Organize the risk areas in the list considering the urgency of their remediation
and mitigation
pass
def rectify_risk_areas(self):
# Address the emphasized risk areas suitably
pass</code>
The Python code fragment above underscores the rudimentary elements of a susceptibility management strategy, outlining the discovery, categorization, ranking, and neutralization of potential risk areas in a specified system.
Susceptibility management isn't a process that stands alone. It's a recirculating, ongoing process that encompasses the following stages:
-
Discovery: Digital infrastructures and networks undergo exhaustive inspections to expose potential risk areas. Tools such as Nessus, OpenVAS, and Nexpose are typically deployed for this purpose.
-
Categorization: Upon exposure, risk areas are sorted based on the latent hazard they represent. The Universal Risk Area Valuation System (URAVS) is a renowned tool for this task.
-
Ranking: Each risk area doesn't represent a homogeneous hazard level. Some necessitate immediate resolution, while others can be addressed later. This phase involves ranking risk areas based on their threat level, potential to be exploited, and business impact.
-
Rectification: Concrete actions are taken to neutralize these risk areas, which may require updating software, executing backup systems, or even accepting the risk if a cure isn't cost-effective.
-
Verification: After rectification, it's necessary to ensure that the risk areas have been suitably dealt with. This usually involves reassessing the system or running penetration tests.
-
Documentation: Following all the stages of risk area management, a comprehensive report detailing each step of the process should be compiled and shared with all relevant entities.

In sum, susceptibility management facilitates a proactive approach to handling security threats. It enables enterprises to detect hidden risk areas in their digital infrastructure, rank high-risk areas, and execute apt solutions to eliminate these threats. This procedure plays a pivotal role in forestalling data breaches and safeguarding the integrity, privacy, and accessibility of digital systems. Just as one maneuvers through an elaborate labyrinth, handling digital safeguards requires deft skill and attention, especially in taking care of inherent system shortcomings which might compromise company's online resources. A forward-thinking approach consists of differentiating between, ranking, and refining any potential liabilities that could be lurking within a network or system.
Picture cybersecurity as a vast, tempestuous ocean filled with a myriad of lurking threats and clandestine access paths. Cyber culprits exploit these loopholes to illicitly infiltrate systems, snatch classified data, impede smooth operations, or administer extensive digital assaults.
Thus, the act of addressing system vulnerabilities transcends being a purely preventive measure; it is an essential cog in a company's inclusive digital defense strategy. This ongoing technique involves multiple stages, from the discovery of fragile points to their repair.
Allow us to explore the indispensable role of liability management in the world of cybersecurity.
- Identifying Fragile Areas
The initial stage in managing vulnerabilities involves locating potential fragile areas within the system. A plethora of methodologies can be utilized for this purpose, such as liability assessments, perforation trials, and code scrutiny.
<code class="language-Python"># Example code showing a rudimentary vulnerability scan using Nmap import os os.system("nmap -sV -p- Target_IP")</code>
The sample Python code given uses the Network Mapper (Nmap) to perform a liability scan for the given IP address. The -sV entity aids in obtaining the service-related version information of the open ports while the -p- entity scans every possible port, amounting up to 65535 in sum.
`
`
- Categorizing and Assessing Fragile Areas
Once identified, the vulnerabilities need to be sorted according to their potential harm and the possible ramifications they may cause. For this purpose, a grading system is often employed, such as the Common Vulnerability Scoring System (CVSS).
| Fault | CVSS Value | Intensity |
|---|---|---|
| SQL Injection | 9.0 | Acute |
| XSS Attack | 6.1 | Average |
| CSRF Attack | 6.0 | Average |
In the mentioned table, the SQL Injectionfault holds a greater CVSS value and is determined 'Acute' as it may breach the entire database records.
- Rectifying Fragile Areas
The subsequent step in managing vulnerabilities demands the implementation of appropriate measures to neutralize recognized shortcomings. These actions could range from amending the fault, adopting an alternative solution, to completely removing the flawed component.
- Validating the Amendments
Post rectification of vulnerabilities, it is vital to confirm the success of the implemented measures. This can be commenced by conducting the vulnerability scans again and confirming that the reported issues have been truly rectified.
- Ongoing Oversight
The operation of managing vulnerabilities is not a one-off task but a repeated responsibility. It necessitates constant oversight of the system for fresh vulnerabilities, reassessment of present ones, and enhancing the corrective methods as dictated by the circumstances.
To conclude, the governance of vulnerabilities constitutes a significant element within the overarching digital defense structure. This activity empowers companies to actively seek and mend fragile points, thus lowering the probability of possible digital assaults and guaranteeing the sturdiness and safekeeping of their online resources.
Fundamentals of an Effective System Weakness Management Strategy
The defense against cyber threats requires a finely tuned strategy for managing system weaknesses. The steps involved in this include pinpointing, categorizing, rating in terms of priority, and remedying the detected weak spots in digital systems as well as software applications. The sturdy backbone of potent system weakness management strategy primarily stands on numerous fundamental principles.
- Wide-Ranging Identification of Resources
A key element to effective system weakness management lies in acquiring a detailed idea about every resource on your network, which encompasses hardware components, software applications, and information repositories.
<code class="language-python">#An instance of code for enumerating resources
def list_resources(network):
resource_array = []
for unit in network:
if unit.is_resource():
resource_array.append(unit)
return resource_array</code>
This piece of code demonstrates a straightforward way of enumerating resources on a network. It checks every single unit on the network to confirm if it's a resource, and if so, adds it to the resource array.
- Periodic Scanning for System Weakness
Another core principle is to consistently scan for system weaknesses using automated tools that swiftly detect any known weak spots.
| Scanning Tool | Function |
|---|---|
| Nessus | A popular scanning tool proficient in discovering weak spots in various systems. |
| OpenVAS | An open-source scanner lauded for uncovering weak spots in Linux-based systems. |
These are only a few among numerous scanning tools. The trick is to frequently employ these scanners to nab the weak spots as soon as they manifest.
- Evaluating Risks and Establishing Priorities
The third principle centers on evaluating the potential after-effects of each weak spot and rating them concerning this evaluation.
<code class="language-python"># Code fragment for risk judgment
def judge_risk(system_weakness):
if system_weakness.is_severe():
return "High Risk"
elif system_weakness.is_mild():
return "Moderate Risk"
else:
return "Low Risk"</code>
This piece of code is an illustration of how to evaluate the risk linked to a particular system weakness. It rates the risk depending on the intensity of the system weakness.
- Rectification and Updates
Rectifying weaknesses by deploying updates or employing other measures for rectification forms the fourth principle.
| Action Plan | Outline |
|---|---|
| Fixing via updates | Deploying a software update to rectify a weakness. |
| Alteration in setup | Changing a system's setup to obliterate a weak spot. |
These are a few of many possible rectification steps that can be undertaken to remedy weaknesses. It's crucial to rapidly execute these actions to curtail any opportunity for possible attacks.
- Constant Surveillance
The final principle concerns persistent surveillance. The need is to keep a close eye on your network to detect any signals pointing towards the exploitation of weaknesses, and to promptly respond to such signals.
<code class="language-python"># Code snippet for regular surveillance
def conduct_surveillance(network):
for unit in network:
if unit.is_breach():
notify_defense_team(unit)</code>
This piece of code illustrates how to perform regular surveillance on a network. It checks each unit if there's any breach, and if found, alerts the defense team.
To sum it up, an effective system weakness management strategy is rooted in the principles of resource enumeration, regular scans for system weaknesses, risk evaluation and setting priorities, implementing rectifications and updates, and finally persistent surveillance. By adhering to these principles, a resilient strategy can be developed to shield your network from cyber threats.
Digital Defense: Innovative Approaches to Safeguarding Cyber Territories with Vulnerability Management Instruments and Techniques
Guarding virtual assets in today's tech-centric era is of utmost significance. This endeavor, termed as vulnerability control, is paramount to fortifying the digital standing of an entity. This multifaceted course of action encompasses the detection, evaluation, ranking, and rectification of vulnerable entities within a corporation's digital surroundings. The mastery of handling these susceptibilities harnesses an array of cutting-edge devices and game plans, this post will offer a novel viewpoint on few commonly utilized examples.
Unraveling Vulnerability Detection Applications
These are meticulously designed digital mechanisms devised to independently reveal vulnerable elements within networks or systems. Their aim is to uncover ubiquitous susceptibilities such as outdated software, potentially risky configurations or missed updates. Renowned specimens of such solutions include Nessus, OpenVAS, and Nexpose.
Examine a handful of specifics of these applications:
| Vulnerability Detection Solution | Merits | Drawbacks |
|---|---|---|
| Nessus | Comprehensive inventory of vulnerabilities, User-friendly | Requires investment, may not agree with the financial constraints of smaller entities |
| OpenVAS | Available at no cost with customizable traits | Demands profound technical knowledge for effective usage |
| Nexpose | Superb integration with various cybersecurity apparatus, provides real-time updates | Might burden system resources, could pose financial hurdles for smaller operations |
Tailor-made Patch Deployment Systems
Formulated to aid businesses in the smooth incorporation of system patches, these mechanisms can streamline and expedite the patching task, facilitating efficient system refurbishing. SolarWinds Patch Manager, ManageEngine Patch Manager Plus, and Automox are few instances of such systems.
Here's a simple program snippet to comprehend these systems' operations:
<code class="language-python">def integrate_patch(system, patch):
if system.is_prone(patch):
system.integrate_patch(patch)
else:
print("This system isn't vulnerable to this specific patch.")</code>
Intrusion Detection Systems (IDS)
IDS are continually monitoring network interaction, vigilantly spotting sketchy undertakings, and issuing warnings upon detecting such behavior. Some focus on probing network activity while others center on monitoring operations on particular hosts. Snort, Suricata, and OSSEC are popular IDS.
Data Protective Analytics Instruments (DPAI)
DPAI accumulate and scrutinize log data from numerous sources within the organization's technological structure. They present real-time evaluation of protective notifications and have a crucial role in highlighting patterns indicating potential compromise. Splunk, LogRhythm, and IBM QRadar are frequently employed DPAI.
Cyber Intrusion Simulations
Commonly known as penetration testing, this technique involves emulating cyber threats on a system to showcase possible vulnerabilities. Automated apparatus like Metasploit can be utilized for this purpose, or this can be executed manually by a skilled cybersecurity specialist.
As a closing note, insightful vulnerability control necessitates a potent mixture of varied devices and techniques, chosen wisely considering the unique requirements of the entity. With the strategic employment of these tools and techniques, corporations can notably elevate their resilience against cyber threats and amplify their security fortification across their digital territories.Building a robust mechanism to handle potential vulnerabilities is paramount in safeguarding your enterprise's digital properties. This robust model involves the identification, classification, evaluation, and rectification of weak points within your technological configurations and installations. Here's a comprehensive manual on how to construct a foolproof vulnerability governance system:
-
Ingrain a Vulnerability Governance Manifesto
The first stage in constructing a firm vulnerability governance routine is to ingrain a manifesto, picturing your enterprise's tactical approach to identify and rectify weak spots. The manifesto should clearly define roles and responsibilities, offer pathways for weakness identification and mitigation, and set milestones for reporting and appraisals.
<code class="language-python">class WeakSpotMitigationManifesto: def __init__(self, responsibilities, pathways, reporting, appraisals): self.responsibilities = responsibilities self.pathways = pathways self.reporting = reporting self.appraisals = appraisals</code> -
Unearth and Classify Resources
The next stage involves finding all the resources related to your enterprise. These could include hardware, software, data, and network components. Once all resources are unearthed, classify them as per their significance to the enterprise. This classification will assist in prioritizing governance activities concerning vulnerabilities.
<code class="language-python">class EnterpriseResource: def __init__(self, kind, significance): self.kind = kind self.significance = significance</code> -
Perform Habitual Weak Spot Assessments
Regular weak spot assessments are vital for identifying potential glitches in your configurations. These evaluations can be done using automated utilities or manual strategies. The observations are then chronicled and scrutinized to determine necessary actions for remediation.
<code class="language-python">class WeakSpotAssessment: def __init__(self, strategy, observations): self.strategy = strategy self.observations = observations</code> -
Grade Weak Spots
Not every weak spot carries the same threat level. Hence, it's vital to grade vulnerabilities based on factors like potential breach repercussions and the likelihood of misuse.
Weak Spot Repercussion Likelihood Grade WS1 High High High WS2 Medium Low Low WS3 High Medium Medium -
Implement Preventive Actions
After the weak spots are identified and graded, the following step is to implement preventive actions. These may include patching, adjusting configurations, or even replacing defective installations.
<code class="language-python">class PreventiveAction: def __init__(self, action, status): self.action = action self.status = status</code> -
Monitor and Reassess
The final stage in ingraining a firm vulnerability governance routine is continuous oversight and review of the routine's potency. This involves tracking preventive measures, reassessing weak spots, and modifying the vulnerability governance manifesto as needed.
<code class="language-python">class MonitorAndReassess: def __init__(self, oversight, reassessment, manifesto_modify): self.oversight = oversight self.reassessment = reassessment self.manifesto_modify = manifesto_modify</code>
By following this manual, you will construct a strong vulnerability governance system that efficiently identifies, grades, and addresses weak spots in your enterprise's configurations and networks. Remember, handling vulnerabilities is a continuous effort requiring ceaseless monitoring and reassessment to maintain its potency.In the world of cybersecurity, constant observation plays a key part in failure defense management. It adopts an anticipatory approach that supports establishments in spotting, examining, and dealing with weak links in their web structure. In this text, we'll shed light on the profound influence constant observation has within failure defense management, its operation, and the apparatus and methods which aid its potent application.
Perpetual observation is a method that involves non-stop investigation and breakdown of a firm's network for the purpose of exposing weak spots and potential threats. This includes the application of automated apparatus for the purpose of ceaselessly overseeing and determining the security state of a firm's data technologies.
The Significance of Constant Observation in Failure Defense Management
There are several reasons why perpetual observation is cardinal in failure defense management:
-
Swift Notice of Weak Spots: Through constant observation, weak spots are discovered in good time which can then be dealt with before infiltrators may exploit them.
-
Adherence to Regulatory Guidelines: Numerous regulatory frameworks necessitate continuous monitoring to uphold their compliance stipulations.
-
Enhanced Security State: Constant observation supports establishments in maintaining a current understanding of their security status, empowering them to make enlightening decisions about danger management.
The Mechanism of Constant Observation in Failure Defense Management
There are multi-step procedures involved in constant observation within failure defense management:
-
Asset Recognition: The first move in constant observation is recognizing all assets found in an establishment's network, including hardware, software, and data.
-
Weak Spot Inspecting: After recognizing all assets, they are then subjected to non-stop inspecting for weak spots, employing the use of automated tools capable of exposing known weak spots in the system.
-
Weak Spot Appraisal: Once weak spots have been exposed, they are then evaluated based on their harshness and prospective influence on the establishment.
-
Fixing: Depending on the appraisal, weak spots are then fixed, possibly by applying patches, altering configurations, or employing other buffering schemes.
-
Reporting: Lastly, particulars of the observation procedure are communicated to relevant parties, specifically the details surrounding the weak spots discovered, their harshness, and steps taken to remedy them.
Instruments and Methods for Constant Observation
There are numerous tools and tactics employed for constant observation in failure defense management:
-
Weak Spot Inspectors: These are automated tools designed for inspecting networks for known weak spots, such as Nessus, OpenVAS, and Nexpose.
-
Security Data and Event Handlers (SIEM) Mechanisms: SIEM mechanisms compile and breakdown security-centered data from an organization-wide network. These tools can help in revealing patterns and trends that might suggest the presence of a weak spot or threat.
-
Invasion Detection Systems (IDS): IDS can notice suspicious activities on a network that might signal a possible violation attempt.
-
Patch Management Instruments: These instruments assist in managing the application of patches to software to repair weak spots.
Applying Constant Observation
To apply constant observation in failure defense management, the following steps are necessary:
-
Set Goals: Initially, decide what your anticipation for constant observation is. This could be adhering to regulatory guidelines, enhancing security status, or spotting weak spots promptly.
-
Recognize Assets: Afterward, recognize all assets on your network, including hardware, software, and data.
-
Choose Instruments: Decide on the tools you desire to use for constant observation. This could include weak spot inspectors, SIEM mechanisms, IDS, and patch management instruments.
-
Apply Observation: Once you've settled on the tools, apply the observation procedure. This involves setting up your chosen tools to continually inspect and break down your network.
-
Analyze and Upgrade: Finally, on a regular basis, examine the outcomes of your observation procedure, making adjustments as necessary.
In summary, constant observation is a cardinal element of failure defense management. It allows for spotting weak spots before they can be harnessed, assists in complying with regulatory requirements, and enhances an establishment's comprehensive security status. By applying constant observation, establishments can notably augment their failure defense management endeavors.Emerging further into the digitally inclined era, we counter increasingly sophisticated and varied cyber risks. The formidable arsenal of black-hat strategists is continually optimizing, using resourceful techniques to exploit vulnerabilities in diverse online ecosystems and infrastructures. This underscores the pivotal role of effective governance in bridging these security pitfalls.
As we visualize the ensuing digitized landscape, certain progressive trends are discernible in the realm of vulnerability oversight. Key among these are the significant incorporation of autonomous technologies like Cognitive Computing (CC) and Predictive Analysis (PA), the escalating demand for uninterrupted digital scrutiny, and the value of a preventive stance in tackling digital breaches.
`
`
The Advancement of CC and PA in Managing Digital Disorder
CC and PA are set to become indispensable constituents in the cybersecurity landscape. These cutting-edge technologies can streamline the chore of detecting and hierarchizing cyber risks, effectively making these automatic procedures thereby conserving substantial effort and work force.
To illustrate, Cognitive Computing can decode voluminous datasets, revealing patterns indicating probable vulnerabilities. In parallel, Predictive Analysis algorithms can draw on past patterns to detect potential threats and suggest corresponding preventive strategies.
Here's a succinct example of Python code illustrating the role of Predictive Analysis in identifying online risks.
<code class="language-python"># Sample code showcasing use of PA for addressing online threats from sklearn.ensemble import RandomForestClassifier # Training Dataset X_train = [...] # Data like system characteristics, previous incidents y_train = [...] # Result data such as cyber threat occurrences # Construct and teach the PA model model = RandomForestClassifier() model.fit(X_train, y_train) # Applying the model to predict possible cyber threats X_test = [...] # Fresh data predictions = model.predict(X_test)</code>
The Amplified Significance of Sustained Surveillance
Navigating through an era swarming with cyber risks, the criticality of continuous vigilance in vulnerability management becomes evident. This necessitates regular audits of systems and networks to identify potential hazards and quickly counteract them.
Continual monitoring enables organizations to spot and pacify vulnerabilities ahead of any mishap. This procedure gains dominance considering the skyrocketing frequency at which new gaps surface and fall prey to misuse.
The Advent of a Preemptive Approach
Triggered by the mounting surge of digital threats, businesses need to pivot from a responsive mode to a strategic, future-oriented mindset in preventing cyber breaches. This implies being foresighted, identifying and mitigating vulnerabilities before a potential exploitation.
Implementing a strategic procedure in governing vulnerabilities entails consistent vulnerability evaluations, practicing initiatives like penetration tests and vulnerability screenings, and architecting sturdy security policies to curtail the chances of successful invasions.
The following example demonstrates a command-line instruction for executing a vulnerability scan using Nmap.
<code class="language-bash"># Command guide for using Nmap for vulnerability scanning nmap -p 1-65535 -T4 -A -v [target IP address]</code>
To sum up, the prospective trajectory of vulnerability regulation is veering towards the full embrace of advanced tools like Cognitive Computing and Predictive Analysis, the cultivation of ceaseless alertness, and fostering an anticipatory approach in identifying and addressing vulnerabilities. It is imperative that our strategies in managing these gaps keep abreast with the evolving panorama of digital threats.
如有侵权请联系:admin#unsafe.sh