2023-11-29 23:17:16 Author: www.sentinelone.com(查看原文) 阅读量:7 收藏
A little over a year ago, we described how ransomware operators had evolved their tactics from simple file locking to more sophisticated forms of extortion in Ransoms Without Ransomware, Data Corruption and Other New Tactics in Cyber Extortion. Since then, cybercrime actors have not stood still, and we are currently seeing the emergence of a brace of new tactics to wrest funds out of organizations and their clients in the wake of a business network compromise.
We observe that data theft and data destruction continue to be primary tools in the cybercriminal’s arsenal, along with partial and full file encryption. Added to that, however, we have begun to see the use of new levers that attempt to shame, blame or otherwise coerce victims into paying the ransom demanded by attackers.
In this post, we describe the emergence of these new tactics in cyber extortion to help defenders better understand the continuing development of threat actor behaviors.

Extortion Through Leveraging the Law
In mid-2023, the United States Securities and Exchange Commission approved updated requirements around cybersecurity incident reporting. These new requirements require that all companies disclose cybersecurity incidents, along with all the pertinent details, with the SEC within four days of becoming aware of a breach incident.
The new rules will require registrants to disclose on the new Item 1.05 of Form 8-K any cybersecurity incident they determine to be material and to describe the material aspects of the incident’s nature, scope, and timing, as well as its material impact or reasonably likely material impact on the registrant. An Item 1.05 Form 8-K will generally be due four business days [our emphasis] after a registrant determines that a cybersecurity incident is material.
The new requirements are set to take effect from 18th December, 2023 for larger organizations and from June 2024 for all others. However, some ransomware operators have already adopted tactics that seek to leverage the new rules about breach disclosure to threaten victims even before they have taken effect.
On November 7th, the ALPHV gang breached MeridianLink in a data theft operation that did not involve the deployment of ransomware. The victim – a large financial services enterprise with dealings in mortgage lending, credit unions and banking products and services – subsequently stated that they became aware of the breach on November 10th.
According to the attackers, the victim was threatened with being reported to the SEC if they failed to pay within 24 hours.
On November 15, ALPHV added MeridianLink to its TOR-based data leaks website along with excerpts and screenshots of the complaint they filed to the SEC alleging that the enterprise had failed to report the breach within four days.
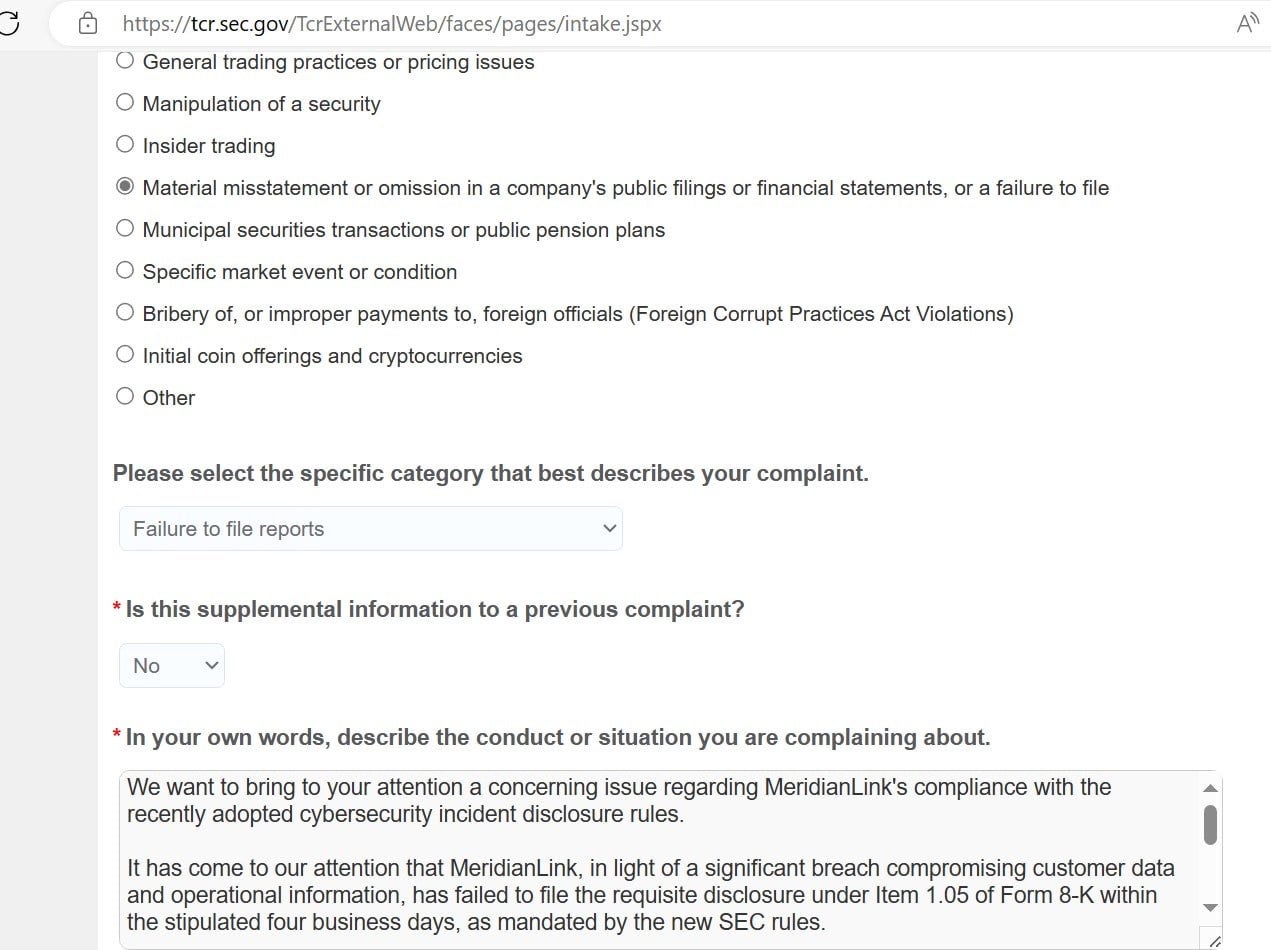
Although in this case the rules were not in force at the time, it is clear that going forward threat actors will use this as a tactic to pressure victims. The aim would appear to be to prevent organizations stalling for time while trying to mitigate the damage, negotiate the payment amount, or otherwise avoid revealing the disclosure to their partners, clients and other affected parties.
The Threat of Exposing Incriminating Data
While the threat of exposing stolen data has now been used for some time as an additional form of leverage, there have been few cases where the nature of the data itself has been used to pressure a victim to pay. Where those have occurred, they have centered around sensitive, proprietary data that companies would not wish to fall into the hands of competitors.
However, a recent breach by affiliates of the Rhysida ransomware operation was followed by a threat to publish data that itself constitutes a criminal offense for the victim to possess. In this case, the ransomware operators allege that data stolen from Mount St. Mary’s Seminary, a school that prepares “candidates for the Catholic priesthood”, contained “child erotica”.
“Ready to provide evidence of child erotica stored on this network. Willing to cooperate with detectives and journalists. These materials will not be published on our site.”
The implications here are complex and concerning. Even the allegation of such threatens the reputation of the victim organization, even if untrue. It is easy for threat actors to make damaging claims and refuse to provide the evidence. As a tactic, threatening to publicize such claims can exert pressure on victim organizations, particularly if they cannot verify for themselves whether such data exists.
If true, there are obvious legal implications and reputational consequences for the organization even if the crime is the sole responsibility of a single individual. In such circumstances, threat actors can ramp up the pressure on victims to pay in the hope that the data will not be exposed to law enforcement.
While the specific nature of the incriminating data in this incident may not be (one would like to think) something widely found on business networks, the greater lesson is that threat actors can and will leverage not only business data but also personal employee data that may be stored on compromised business computers.
Enterprises need to ensure that strict policies are in place to prevent employees using organizational computers for personal use, and that these policies are enforced, along with ensuring all endpoints are properly protected against compromise.
Trading Victims Off Against GDPR & Other Regulators
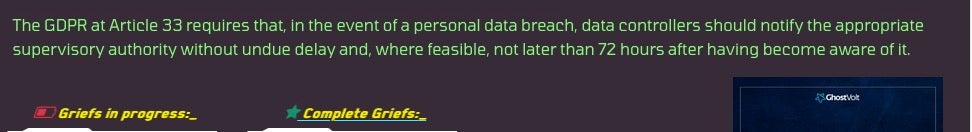
Ever since 2018, GDPR and similar regulations have had an important impact on the way companies store and retain data. Backed by the threat of heavy financial penalties, GDPR is a powerful motivator to ensure organizations prioritize data privacy in their operations.
Threat actors have leveraged the threat of penalties for breaching GDPR rules in the past. For example, in 2021, DoppelPaymer successor Grief (aka PayorGrief) cited GDPR violations to exert pressure on victims.
However, more forceful GDPR-related threats have been observed in 2023. The previously mentioned ALPHV gang attempts to pressure victims by scaring their customer base. On November 14, 2023, the organization “Naftor and Groupa Pern” was added to the ALPHV blog with scare text claiming the company did not observe GDPR rules and that its customers’ data could be leaked as a result.
WARNING!
COOPERATION WITH NAFTOR AND GRUPA PERN MAY RESULT IN THE LEAKAGE OF YOUR DATA. THESE COMPANIES DO NOT COMPLY WITH THE LAWS OF THE EUROPEAN UNION AND IN PARTICULAR THE GDPR. YOU MAY INCUR LEGAL AND FINANCIAL RISKS BY WORKING WITH THEM!
More direct leverage of GDPR was recently seen as a tactic used by the short-lived and now-defunct Ransomed.VC gang. This group threatened victims with disclosure of GDPR violations in the event they did not conform to the ransom demands. The extortion demands would be purposefully set at a price lower than the potential GDPR fines in an attempt to entice the victim to pay by offering a less financially-painful option.
Conclusion
Legal frameworks such as the SEC’s new cybersecurity incident reporting rules, GDPR regulations and standing laws on prohibited data are being exploited to exert further pressure on vulnerable organizations. These latest cyber tactics attempt to force victims into meeting ransom demands by raising fears of both legal liability and reputational damage.
The emergence of such tactics underscores the need for organizations to strengthen their cybersecurity posture, ensure compliance with regulatory requirements and to remain prepared for the evolving nature of today’s cyber threats. Cybercriminals are highly motivated to develop new and creative ways to extort businesses, and cyber defenders need to remain vigilant and adaptive in their strategies to defend against these evolving threats.
To learn about how SentinelOne can help protect your organization from ransomware and other threats, contact us or request a free demo.
如有侵权请联系:admin#unsafe.sh