2023-12-1 05:31:22 Author: therecord.media(查看原文) 阅读量:15 收藏
The Black Basta cybercrime gang has raked in at least $107 million in ransom payments since early 2022, according to research from blockchain security company Elliptic and Corvus Insurance.
The group has infected more than 329 organizations with ransomware throughout its time operating, and the companies’ analysis of blockchain transactions shows links between Black Basta and the Conti ransomware gang — which shut down its operations last year following attacks on the government of Costa Rica.
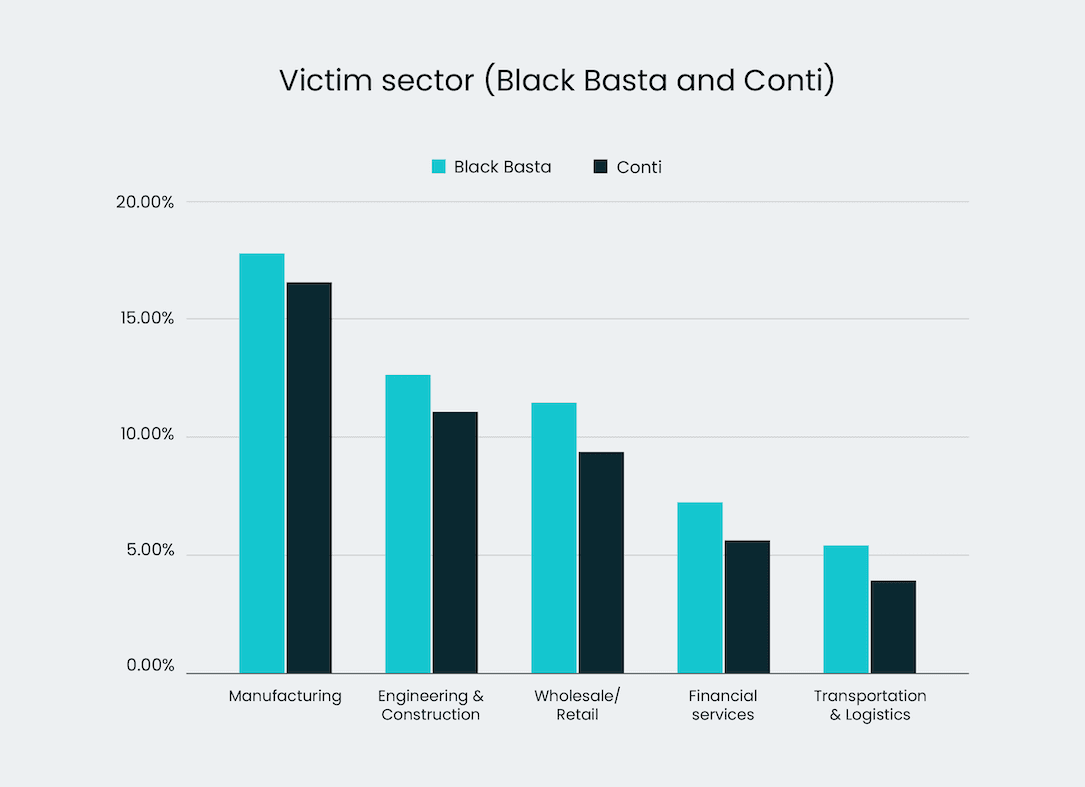
Black Basta, according to Elliptic and Corvus Insurance, emerged around the same time Conti stopped operating and much of the laundered ransom payments can be traced back to Garantex, a sanctioned Russian cryptocurrency exchange. Like Conti, Black Basta shows particular focus on organizations in construction, law and real estate.
“Our analysis suggests that Black Basta has received at least $107 million in ransom payments since early 2022, across more than 90 victims. The largest received ransom payment was $9 million, and at least 18 of the ransoms exceeded $1 million,” the researchers said. The average ransom payment was $1.2 million.
“It should be noted that these figures are a lower bound — there are likely to be other ransom payments made to Black Basta that our analysis is yet to identify — particularly relating to recent victims. Due to the overlap between the groups, some of these payments may also relate to Conti ransomware attacks,” the researchers said.
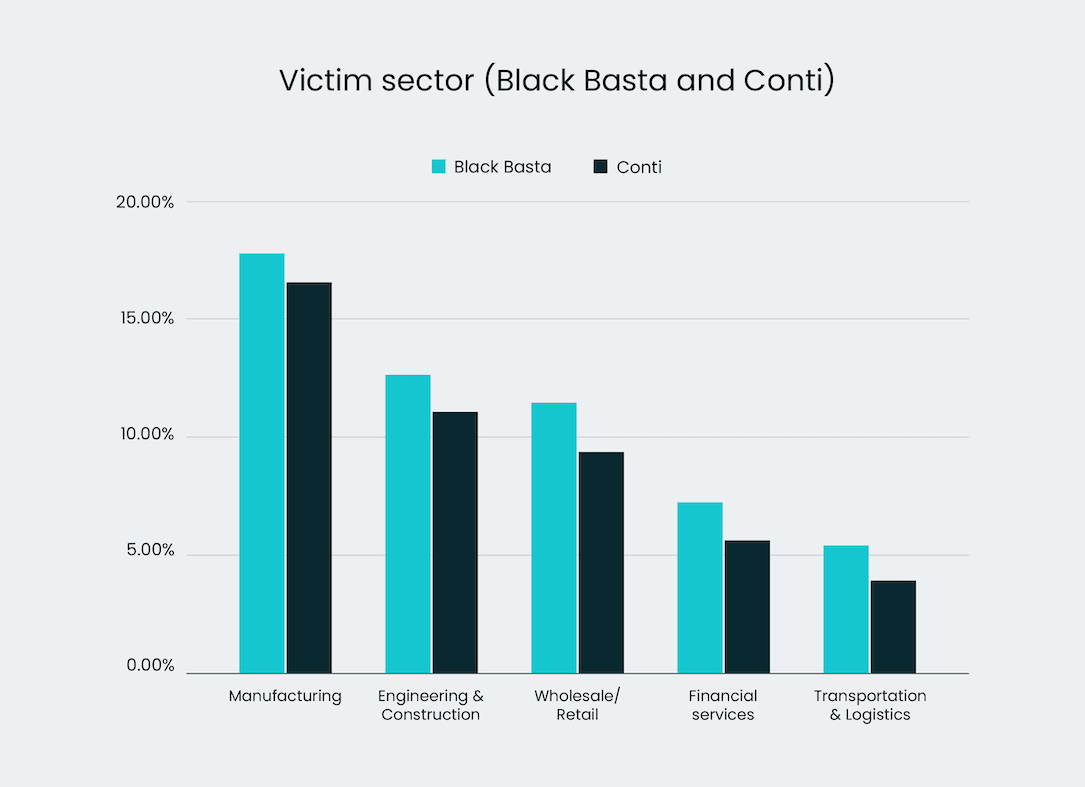 Image: Elliptic
Image: Elliptic
Black Basta has been one of the most high-profile ransomware groups currently operating, taking credit for brazen attacks on the Dish Network, the American Dental Association, British outsourcing company Capita, Swiss tech giant ABB and German arms company Rheinmetall.
Since emerging, it has become the fourth-most active strain of ransomware based on the number of victims tracked over the last year, the report said.
The gang recently has leaked information from organizations such as the Raleigh Housing Authority in North Carolina; a television advertising sales and technology company jointly owned by the three largest U.S. cable operators; and Chile's government.
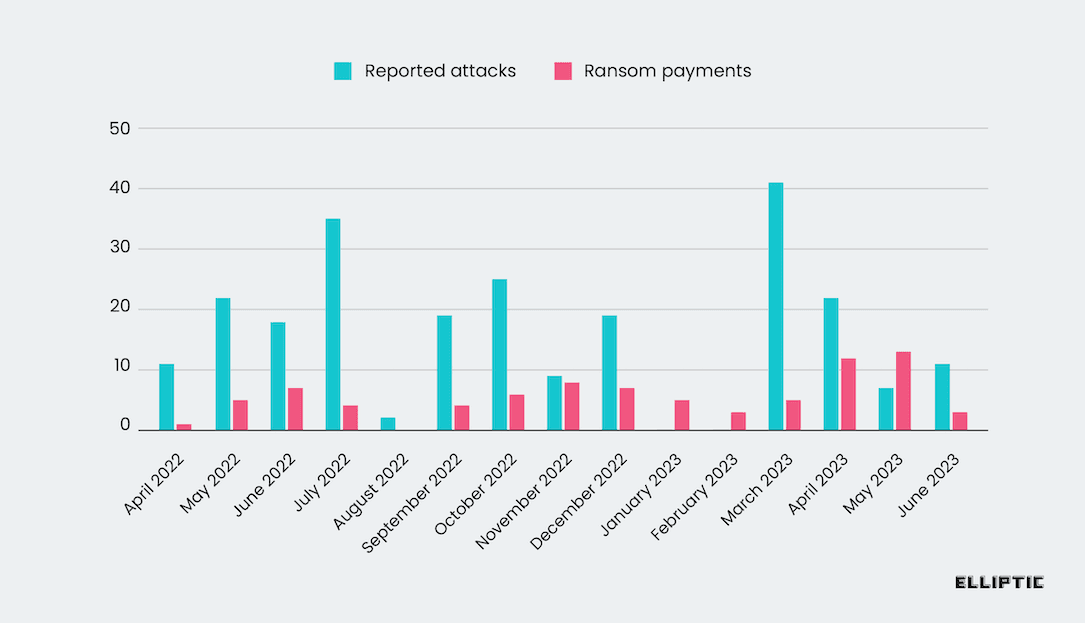 Image: Elliptic
Image: Elliptic
The data shows that about 35% of all Black Basta victims paid a ransom.
The researchers noted that the figures in the report are likely a fraction of the group’s true earnings because most gangs use a variety of cryptocurrency wallets to receive payments and victims typically do not share the details of what wallet they used to pay ransoms.
Qakbot connections
In addition to the links between Conti and Black Basta, the researchers found ties between the ransomware and the Qakbot malware — which was disrupted by the FBI and international law enforcement agencies in August.
Qakbot, also known as Qbot and Pinkslipbot, had become the initial access method of choice for multiple high-profile ransomware gangs, including REvil, Black Basta, Conti, Egregor and MegaCortex.
After infecting victim computers with the Qakbot malware through malicious attachments in spam email messages, gangs could deploy their own ransomware and extort victims. Cybersecurity experts previously noted that the Black Basta ransomware gang used Qakbot during its attack on Capita.
Elliptic said the Qakbot malware was typically used to deploy the Black Basta ransomware and there were clear links between the two operations visible on the blockchain.
Portions of ransoms received by Black Basta went to wallets associated with Qakbot, they found.
“These transactions indicate that approximately 10% of the ransom amount was forwarded on to Qakbot, in cases where they were involved in providing access to the victim,” they said.
Cybersecurity researchers at SentinelOne previously tied the long-running cybercrime cartel known as FIN7 to Black Basta in a report published late last year.
Elliptic noted that leaks of Conti’s online chats hinted that it had ties to the Russian government and provided support for the invasion of Ukraine.
The U.S. State Department last August said that it was offering a $10 million reward for “information leading to the identification or location” of hackers linked to the Conti operation as several experts expressed concerns that the group would splinter off into gangs like Black Basta.
The department’s Rewards for Justice program shared an image of a man it said is tied to the group who goes by the name “Target,” and said it is searching for other members who use the handles “Reshaev,” “Professor,” “Tramp” and “Dandis.”
Get more insights with the
Recorded Future
Intelligence Cloud.
No previous article
No new articles
如有侵权请联系:admin#unsafe.sh
