2023-12-4 02:58:13 Author: securityaffairs.com(查看原文) 阅读量:16 收藏
New Agent Raccoon malware targets the Middle East, Africa and the US
Pierluigi Paganini
December 03, 2023

Threat actors are using the Agent Raccoon malware in attacks against organizations in the Middle East, Africa and the U.S.
Unit42 researchers uncovered a new backdoor named Agent Raccoon, which is being used in attacks against organizations in the Middle East, Africa, and the U.S.
The malware was used in attacks against multiple industries, including education, real estate, retail, non-profit organizations, telecom companies, and governments.
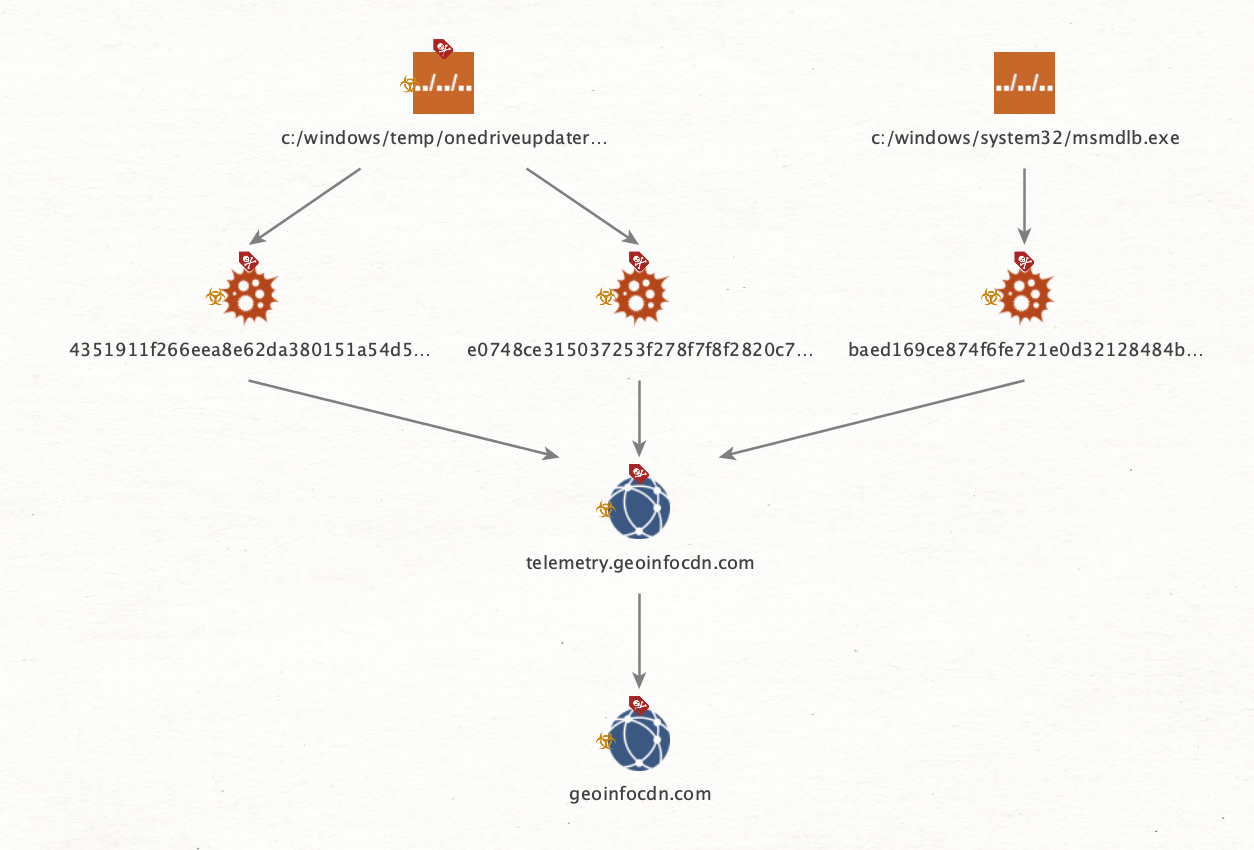
The backdoor is written in .NET and leverages the domain name service (DNS) protocol to establish a covert communication channel with the command and control infrastructure. The Agent Raccoon backdoor was used in conjunction with other two tools in multiple attacks, a Network Provider DLL module dubbed Ntospy which was designed to steal user credentials and a customized version of Mimikatz called Mimilite.
The analysis of the C2 infrastructure revealed that it dates back to 2020.
Unit42 is tracking this threat activity cluster as CL-STA-0002, it is suspected to be a state-sponsored cyberespionage campaign.
The attackers attempted to disguise the Agent Raccoon binary as Google Update and MS OneDrive Updater binaries.
The authors of the malware made small modifications to the source code to evade detection. The experts discovered a domain hard-coded in plain text in the code, it was used to establish the DNS covert channel. In other samples, the authors used a Base64 encoded string.
“All the C2 domains identified fulfill the same base pattern, with unique values for the four character identifier across different samples: [4 characters].telemetry.[domain].com” reads the report.
The backdoor uses Internationalizing Domain Names for Applications’ (IDNA) domain names with Punycode encoding for evasion.
Agent Raccoon supports backdoor functionality, including command execution, file uploading, file downloading.
The backdoor does not provide persistence mechanisms, threat actors noticed it was executed by using scheduled tasks.

“Unit 42 researchers believe this threat activity cluster aligns with medium confidence to nation-state related threat actors” concludes the report. “for the following reasons:
- The detection and defense evasion techniques used
- The exfiltration activity observed
- The victimology
- The customization level of the tools used
- The TTPs observed”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, malware)
如有侵权请联系:admin#unsafe.sh