2023-12-5 13:46:5 Author: lab.wallarm.com(查看原文) 阅读量:7 收藏
In the fast-paced digital world, think of Application Programming Interfaces (APIs) as the threads that stitch together the fabric of our tech ecosystems. They're often overlooked, quietly ensuring that your apps communicate seamlessly and keep the digital world running smoothly. The majority of organizations grapple with a common challenge — limited visibility into their public API attack surfaces. And here's the twist; with all that potential for new innovative products and services via API’s, they also become a prime focus for cyber troublemakers. That's where Wallarm's API Attack Surface Management (AASM) steps in like a vigilant protector, ready to safeguard and defend.

Unraveling the Complexity of API Visibility
Despite the widespread use of APIs, many organizations struggle with limited
visibility into API attack surfaces. This lack of insight can lead to significant security vulnerabilities, as organizations may not fully understand which APIs are exposed, the specific risks they pose, and their protection status. Existing methodologies, including a mix of disparate open-source tools or incomplete commercial offerings fall short of providing comprehensive visibility and protection.
Embracing Comprehensive Security with API Attack Surface Management
Wallarm's newly introduced API Attack Surface Management (AASM) product offers a holistic, innovative solution to help organizations gain comprehensive control over their expanding API ecosystem. Wallarm's AASM distinguishes itself by offering a comprehensive perspective on and control over the API attack surface. Here are some key features:
- Domain and Subdomain Enumeration:
AASM systematically identifies all host domains and subdomains under an organization's purview. - API Discovery and Risk Assessment:
Catalogs all APIs, assessing and categorizing the risks they pose. This critical step enables organizations to understand potential attack vectors and strengthen their defenses. - Application Assessment and Protection:
AASM evaluates the presence and effectiveness guarding each API, providing insights into existing security measures and their performance. - Security Misconfiguration Identification:
AASM actively scans for security mis-configurations within API setups, a common source of vulnerabilities. - API Leak Detection:
Actively detecting and promptly informing on inadvertently leaked API secrets is another vital feature, closing a critical gap in API security.
Operational Transformation with AASM
Prior to adopting AASM, organizations often grapple with a limited grasp of their API vulnerabilities, exposing them to hidden attacks and unmitigated risks. This uncertainty can lead to surprise attacks or the discovery of publicly exposed APIs. With Wallarm’s AASM, organizations gain a comprehensive inventory of their API attack surface, including a detailed list of all APIs, the associated risks, and protective measures in place. This empowerment enables organizations to proactively utilize Wallarm's Web Application and API Protection (WAAP) for API safeguarding and governance. Additionally, AASM equips organizations with the capability to search for and catalog any leaked secrets, significantly enhancing security confidence while reducing risk.
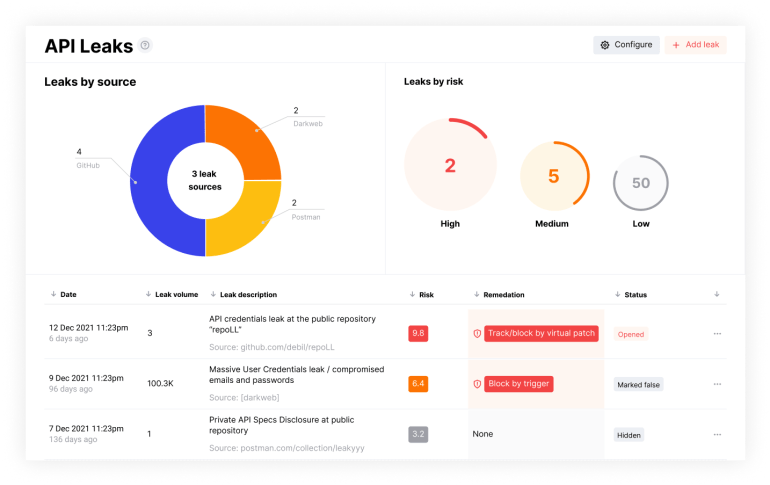
Enhancing Protection with API Leaks Detection

Complementing the robust capabilities of AASM, Wallarm's API Leaks Detection is the first generally available AASM capability designed to prevent and manage inadvertent leaks of API secrets. Key capabilities include:
- Automated Detection of Leaks:
Wallarm continuously scans public repositories and digital platforms to detect any accidental leaks of API secrets, addressing a common yet critical security issue. - Proactive Token Management:
Upon detection of a leak, Wallarm enables immediate actions to block or manage compromised tokens, mitigating potential security breaches (must also possess WAAP). - Comprehensive Tracking of Leaked Secrets:
The system ensures ongoing monitoring and tracking of leaked API credentials, providing insights into their potential use and helping prevent unauthorized access.
API Leaks Detection in Concert with AASM
While AASM provides an all-encompassing perspective of the API attack surface, API Leaks Detection introduces a specialized layer of security, concentrating on the unintentional exposure of sensitive API information. This synergy guarantees a robust and thorough defense against a multitude of API-related security threats.
Getting Started - Licensing and Packaging
AASM is available through a subscription based on the number of 'discovery seeds' an organization may wish to add. It offers flexibility as a standalone product or in conjunction with Wallarm's Cloud-Native WAAP or Advanced API Security solutions.
To embark on your journey toward fortified API security. Elevate your cybersecurity strategy with Wallarm's API Attack Surface Management and API Leaks Detection solutions. Attain unparalleled visibility and control over your API ecosystem, safeguarding your digital assets against the evolving threats of the digital age. Reach out to Wallarm today to explore how these solutions can augment your strategic approach to API security. You can find out further information here, and download the Solution Brief below.
如有侵权请联系:admin#unsafe.sh
