2023-12-5 13:40:21 Author: securityboulevard.com(查看原文) 阅读量:8 收藏
In a time when advancements in technology rule these days, the constant risk of cyber attacks hangs over businesses all over the world. As part of the ‘Mind of the CISO: Behind the Breach’ project, Trellix, recently performed research. This study highlighted the difficulties Chief Information Security Officers (CISOs) encounter during cyber attacks.
This blog explores the struggles of companies with recurring cyber threats and looks into the critical role of Security Auditing and Governance, Risk, and Compliance (GRC). The significance of virtual Chief Information Security Officers (vCISOs) in protecting businesses against the changing threat landscape will also be elaborated in the further aspects of the content.
The Reactive Aspect of Cybersecurity
Trellix’s study reveals a common pattern among CISOs, which is their reactive approach until boards take a proactive one. Following a cyberattack, a staggering 97% of CISOs report that their boards have become more cooperative. Modifications to plan (70%) and increased technology budgets (67%), as well as ongoing assessments of workforce, architecture, and capabilities, are frequently the results of this reactive approach.
But the question arises here:-
Should organizations not take the initiative to promote cybersecurity measures before an attack?
How Diverse are Cyber Attacks in 2023?
Organizations face a wide range of cyber attacks in 2023 due to the complicated field of cybersecurity. Among them, malware poses the biggest threat of about 70% and so does data theft at a similar worrisome number. These figures highlight the necessity of security auditing and a comprehensive cyber security strategy for your organization. This addresses more than just technical vulnerabilities.
Organizations must adopt a comprehensive approach. This strategy should consider the interpersonal and operational factors in addition to technological ones if they are to successfully address these complex issues. Modern firewalls and security controls are essential. Training employees about the risks of digital scams (for instance in applications, web browsers, etc.) is even more crucial. Successful hacking attempts are still mostly the result of human error, which makes ongoing training and awareness outreach efforts essential.
Challenges and Impacts of Cyber Attacks for CISOs
Chief Information Security Officers (CISOs) encounter numerous challenges during and after cyber risks, navigating a complex landscape that demands strategic resilience and adaptability. Here are key difficulties faced by CISOs in the wake of cyber incidents:
Reactive Board Support:
Challenge: CISOs often face the challenge of garnering board support before a cyber attack occurs.
Impact: Boards tend to become proactive in supporting cybersecurity measures only after an incident, hindering proactive risk mitigation.
Diverse Attack Vectors:
Challenge: Cyber threats manifest in various forms, including malware, application vulnerabilities, and data theft.
Impact: CISOs must develop comprehensive defense strategies that cover a broad spectrum of attack vectors, requiring a multifaceted approach.
Technology and Process Improvement
Challenge: Identifying technology gaps and process weaknesses after an attack.
Impact: CISOs need to swiftly enhance both technological infrastructure and procedural frameworks to prevent future incidents.
Why are vCISOs Significant to Protect Organizations?
The aftermath of a cyber incident extends beyond monetary losses and rising insurance premiums. The top three repercussions are company downtime (67%), data loss (67%), and stress on Security Operations (SecOps) teams (83%). It is at this point that virtual chief information security officers, or vCISOs, become crucial. By offering strategic guidance, these cyber specialists make sure that businesses are equipped to deal with the consequences of cyber risks.
Employing a Virtual Chief Information Security Officer (vCISO) offers businesses convenient access to experienced cybersecurity expertise, easing the financial burden of a full-time CISO role. This would ensure a piece of ongoing strategic advice and insight to successfully detect and manage cyber attacks. Moreover, vCISOs contribute an array of varied sector experiences, providing a new outlook and customized solutions to tackle the ever-changing cybersecurity issues. This helps in strengthening an organization’s defenses against cyber threats.
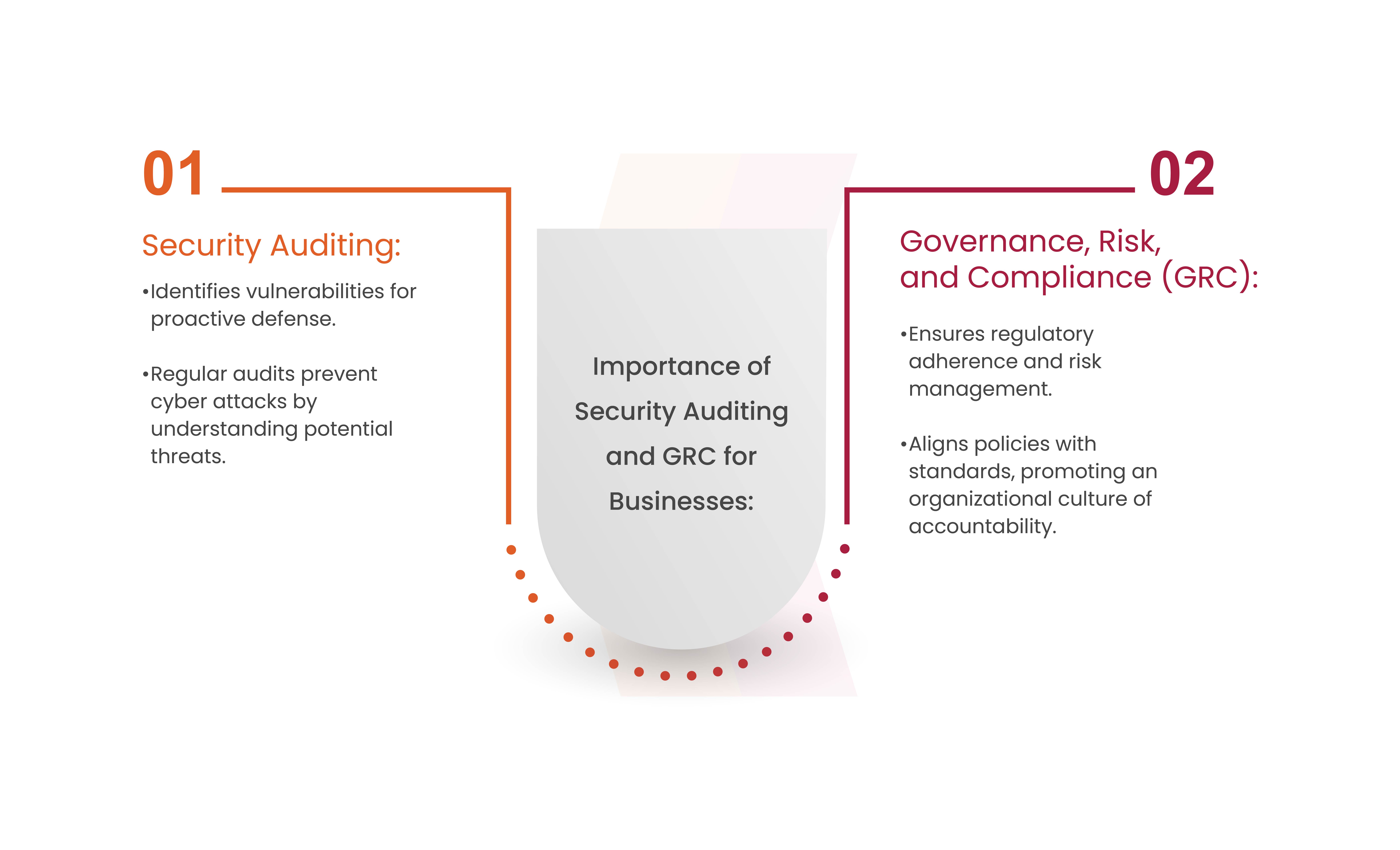
Role of Security Auditing and GRC for Cyber Resilience
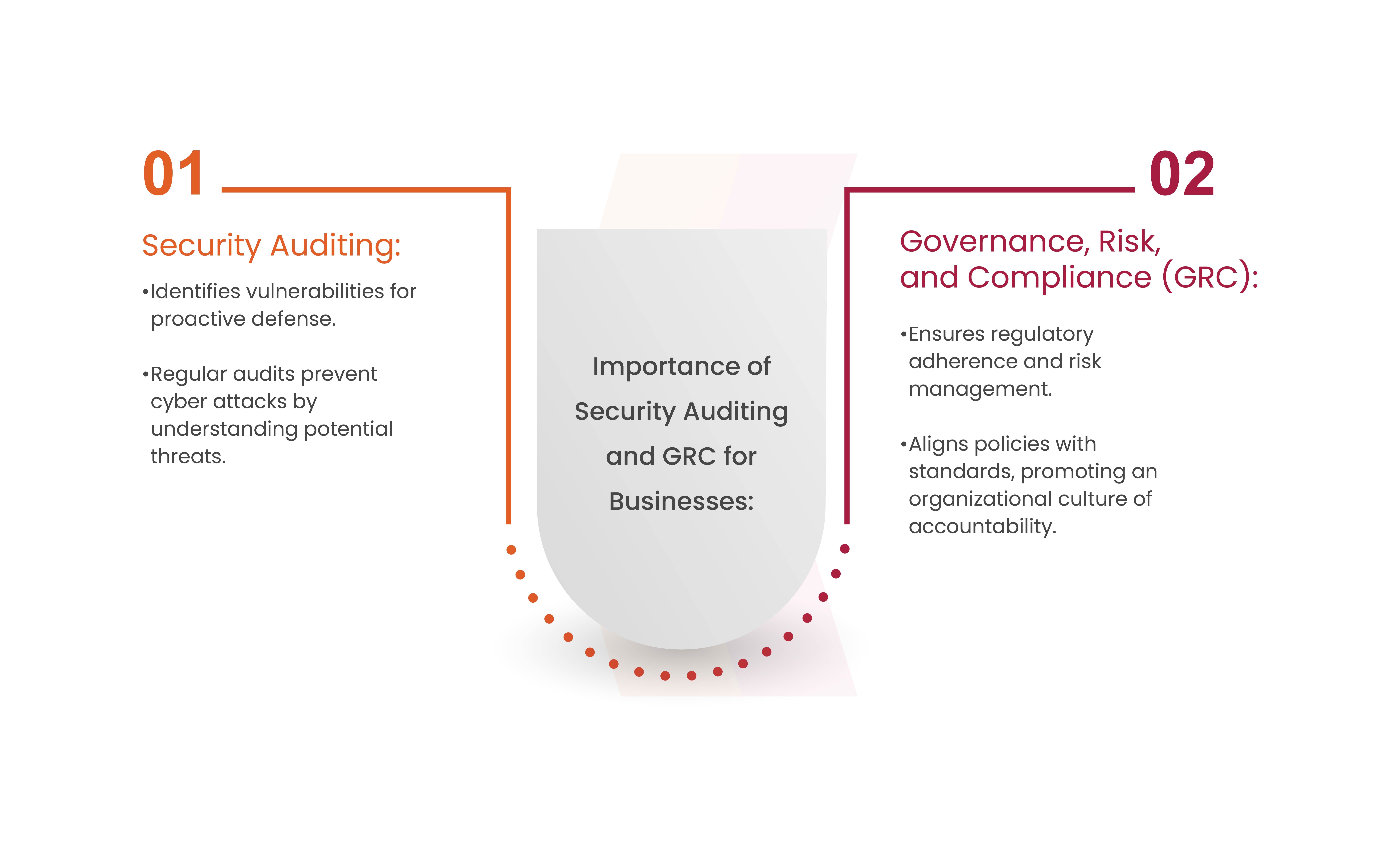
Security auditing thoroughly finds vulnerabilities in an organization’s digital infrastructure. This acts as an alert for businesses to secure their frameworks. Audits reveal hidden vulnerabilities in networks, apps, and procedures by use of methodical evaluations. This procedure offers a comprehensive assessment of the organization’s cybersecurity posture and goes above and beyond standard security measures. Organizations that undertake security audits regularly can prevent cyber risks before they materialize by acquiring a proactive understanding of potential threats.
The key components of an organization’s regulatory adherence and risk management approach are Governance, Risk, and Compliance (GRC). Maintaining compliance is essential in a time marked by strict industrial standards and data protection laws. Through the effective management of risks, the alignment of policies with industry standards, and the assurance of legal compliance, GRC frameworks help organizations optimize their operations. This promotes an organizational culture of accountability and transparency while protecting sensitive data.
Security auditing and GRC work together to produce an effective combination that enables organizations to successfully anticipate, avoid, and respond to cyber-attacks.
Conclusion
Businesses must take proactive and strategic steps to strengthen their cybersecurity defenses due to the problems they encounter. It is important for companies to understand that the recurring cyber attacks would stop with the right approach and under the correct guidance of cyber experts. As a CERT-In empanelled auditor, Kratikal leads this essential function. We offer organizations an unmatched level of knowledge and a strong defense against the constant threat of cyberattacks.
Our reputation as a premium security auditor promotes a robust cybersecurity posture. We help organizations detect and address risks associated with their digital assets in addition to ensuring compliance. Choosing Kratikal is a strategic alliance for companies looking to confidently navigate the complex field of cybersecurity and, not just a security investment.
The post 75% Organizations Struggle with Recurring Cyber Attacks appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Riddika Grover. Read the original post at: https://kratikal.com/blog/75-organizations-struggle-with-recurring-cyber-attacks/
如有侵权请联系:admin#unsafe.sh