A new collection of eight process injection techniques, collectively dubbed PoolParty, could be exploited to achieve code execution in Windows systems while evading endpoint detection and response (EDR) systems.
SafeBreach researcher Alon Leviev said the methods are "capable of working across all processes without any limitations, making them more flexible than existing process injection techniques."
The findings were first presented at the Black Hat Europe 2023 conference last week.
Cracking the Code: Learn How Cyber Attackers Exploit Human Psychology
Ever wondered why social engineering is so effective? Dive deep into the psychology of cyber attackers in our upcoming webinar.
Join NowProcess injection refers to an evasion technique used to run arbitrary code in a target process. A wide range of process injection techniques exists, such as dynamic link library (DLL) injection, portable executable injection, thread execution hijacking, process hollowing, and process doppelgänging.
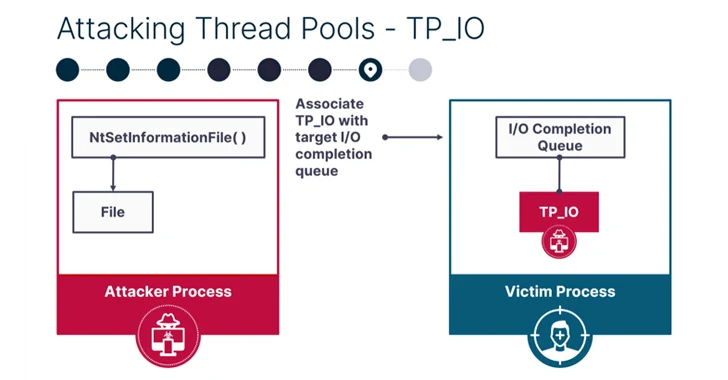
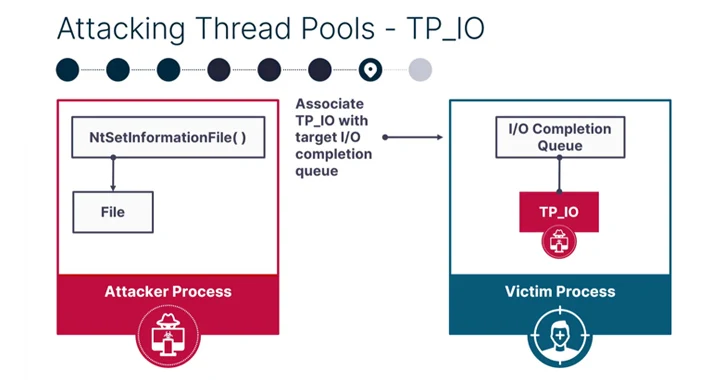
PoolParty is so named because it's rooted in a component called Windows user-mode thread pool, leveraging it to insert any type of work item into a target process on the system.
It works by targeting worker factories – which refer to Windows objects that are responsible for managing thread pool worker threads – and overwriting the start routine with malicious shellcode for subsequent execution by the worker threads.
"Other than the queues, the worker factory that serves as the worker threads manager may be used to take over the worker threads," Leviev noted.
SafeBreach said it was able to devise seven other process injection techniques using the task queue (regular work items), I/O completion queue (asynchronous work items), and the timer queue (timer work items) based on the supported work items.
PoolParty has been found to achieve 100% success rate against popular EDR solutions, including those from CrowdStrike, Cybereason, Microsoft, Palo Alto Networks, and SentinelOne.
The disclosure arrives nearly six months after Security Joes disclosed another process injection technique dubbed Mockingjay could be exploited by threat actors to bypass security solutions to execute malicious code on compromised systems.
"Though modern EDRs have evolved to detect known process injection techniques, our research has proven that it is still possible to develop novel techniques that are undetectable and have the potential to make a devastating impact," Leviev concluded.
"Sophisticated threat actors will continue to explore new and innovative methods for process injection, and security tool vendors and practitioners must be proactive in their defense against them."
Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post.