Over the past few years, SaaS has developed into the backbone of corporate IT. Service businesses, such as medical practices, law firms, and financial services firms, are almost entirely SaaS based. Non-service businesses, including manufacturers and retailers, have about 70% of their software in the cloud.
These applications contain a wealth of data, from minimally sensitive general corporate information to highly sensitive intellectual property, customer records, and employee data. Threat actors have noted this shift, and are actively working to breach apps to access the data.
Here are the top trends influencing the state of SaaS Security for 2024 — and what you can do about it.
Democratization of SaaS
SaaS apps have transformed the way organizations purchase and use software. Business units purchase and onboard the SaaS tools that best fit their needs. While this is empowering for business units that have long been frustrated by delays in procuring and onboarding software, it does require organizations to rethink the way they secure data.
Security teams are being forced to develop new ways to secure company data. Lacking access and visibility into an application, they are placed in the role of advising a business unit that is using SaaS applications. To further complicate matters, every SaaS application has different settings and uses different terminology to describe security features. Security teams can't create a one-size-fits-all guidance document because of the differences between the apps.
Security teams must find new ways to collaborate with business units. They need a tool that offers visibility and guidance for each application setting so that they – and the business unit – understand the risks and ramifications involved in the configuration choices that they make.
ITDR Forms a Critical Safety Net
If a threat actor gains access to a high-privilege account, they gain unfettered access within the application. Organizations are now understanding that identity is the de facto perimeter for their SaaS applications.
When threat actors take over an authorized user account, they typically follow common tactics, techniques and procedures (TTP) as they work their way through the app toward the data they want. They leave behind indicators of compromise (IoC), which might be based on actions taken within the app or logs.
As we move into the new year, we are going to see more organizations adopting an Identity Threat Detection & Response (ITDR) approach. ITDR mitigates that concern. As a key component in Identity Security Posture Management, ITDR capabilities can detect TTPs and IoCs, and then send an alert to the incident response team. Through ITDR, threat actors who have managed to breach the identity perimeter can still be stopped before they steal critical data or insert ransomware into the application.
Learn about how ITDR can help you handle these SaaS Security trends today
Cross-Border Compliance Means More Tenants to Secure
Global companies are increasingly facing different regulatory requirements from one country to the next. As a result, 2024 will see an increase in the number of geo-specific tenants as part of the effort to keep data segmented in accordance with the different regulations.
This change will have a limited impact on software costs as most SaaS app pricing is based on subscribers rather than tenants. However, it will have a significant impact on security. Each tenant will need to be configured independently, and just because one instance of the application is secure doesn't mean that all tenants are secure.
To secure all these tenants, security teams should look for a security solution that allows them to set app benchmarks, compare tenants, and display security settings side-by-side without charging extra for each additional tenant. By applying best practices throughout the organization, companies can keep all their tenants secure.
 |
| Figure 1: Adaptive Shield's platform monitoring and presenting all Salesforce tenants |
Misconfigured Settings Are Leading to New Exploits
A default misconfiguration in ServiceNow triggered widespread panic in October. The setting, which was part of the application's Access Control Lists, allowed unauthorized users to extract data from records. The misconfiguration impacted thousands of companies. A similar misconfiguration in Salesforce Community back in May also impacted a significant number of companies and led to data breaches.
Misconfigurations like these have the potential to cause major damage to companies. They lead to data leaks that break the trust between companies and their stakeholders, and have the potential to turn into onerous fines, depending on the nature of the data that leaked.
Securing misconfigurations is an organization's best chance at preventing these exploits from impacting their operations and hurting their bottom lines.
See how to automate SaaS misconfigurations and regain control of your SaaS stack
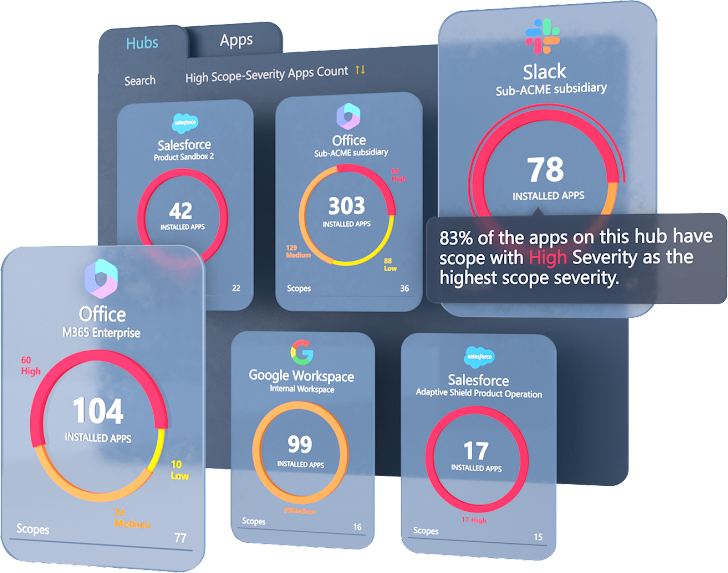
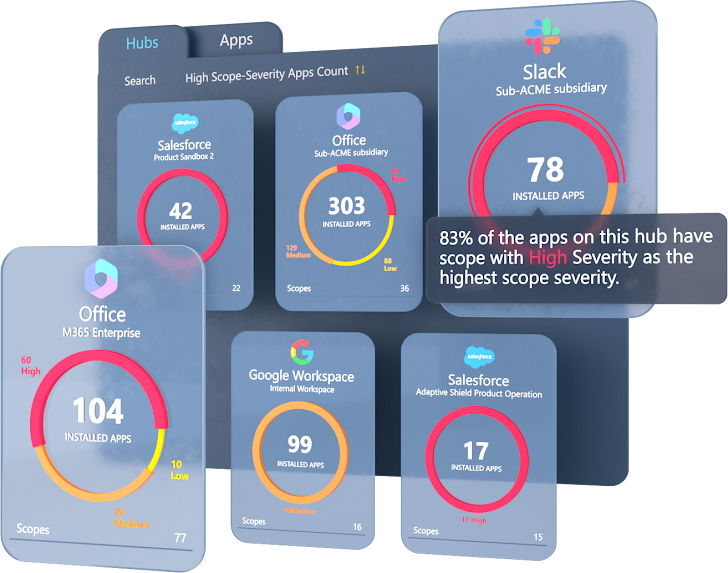
Increased Reliance on Third-Party Applications Adds to SaaS Risk
Third-party applications add real value for end users. They improve processes, extend functionality, and connect data between multiple applications. Users connect these SaaS apps with the click of button, and instantly begin improving their workflows.
In March 2023, Adaptive Shield released a report showing that organizations using Google Workplace with 10,000-20,000 users averaged 13,913 third-party apps connected to Google Workplace alone. An astonishing 89% of these requested either high- or medium-risk permissions. Many of these high-risk apps are used once and forgotten about, or used by a small number of employees. However, even these dormant or lightly used applications have significant permissions and can be used to compromise or breach a SaaS application.
The use of third-party applications is only increasing, as more apps are developed and employees use their own judgment – rather than checking with their security team – when integrating third-party applications into their stack. Security teams must develop visibility into all their integrated apps, and gain insights into the permissions requested, the value the app contributes to the organization, and the risk it poses.
 |
| Figure 2: Adaptive Shield's platform shows integrated third-party apps, their risk score, and the scopes granted |
Multiple Devices to Secure as Working from Home Isn't Going Anywhere
In 2023, nearly 40% of all employees worked from home at least part of the time. According to WFHResearch, approximately 12% of employees work exclusively in their homes, while another 28% have hybrid roles.
These figures should give pause to security personnel concerned about users logging in to their work accounts from personal devices. One of the biggest concerns security teams have is when high-privileged users log into their accounts using an unmanaged or unsecured device. These devices may have critical vulnerabilities, and create a new attack vector. For many teams, there is almost no way to tell which devices are used to access the SaaS app or see whether those devices are secure.
Organizations Are Turning to SSPM to Secure SaaS
While all these trends point to legitimate SaaS security concerns, SaaS Security Posture Management (SSPM) tools coupled with ITDR capabilities, like Adaptive Shield, can fully secure the SaaS stack. SSPMs are designed to automatically monitor configurations, looking for configuration drifts that weaken an app's posture. In SaaS Security Survey, 2024 Plans & Priorities by Cloud Security Association and Adaptive Shield, 71% of respondents said their company had increased their investment into SaaS security tools over the past year, and 80% were either already suing SSPM or planned to invest in one within the next 18 months.
SSPMs can provide baselining tools for multiple tenants of the same app, and enable users to establish best practices, compare settings from different instances, and improve the overall posture of the SaaS stack.
SSPMs also detect and monitor third-party applications, alerting users if their integrated apps are requesting too much access and updating the security team when integrated apps are dormant. It tracks users, and monitors the devices being used to access applications to prevent the use of unmanaged or unsecured devices on corporate SaaS apps. Furthermore, their built-in communication tools make it easy for business units to collaborate with security personnel in securing their applications.
SaaS apps have grown in popularity for good reason. They allow organizations to scale as needed, subscribe to the apps they need at the moment, and limit investment in some IT. With SSPM, these applications can be secured as well.
See live in a ten-minute demo how you can start securing your SaaS stack
Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post.