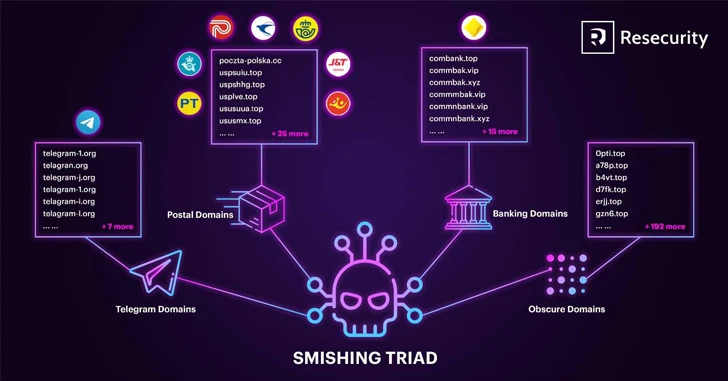
The Chinese-speaking threat actors behind Smishing Triad have been observed masquerading as the United Arab Emirates Federal Authority for Identity and Citizenship to send malicious SMS messages with the ultimate goal of gathering sensitive information from residents and foreigners in the country.
"These criminals send malicious links to their victims' mobile devices through SMS or iMessage and use URL-shortening services like Bit.ly to randomize the links they send," Resecurity said in a report published this week. "This helps them protect the fake website's domain and hosting location."
Smishing Triad was first documented by the cybersecurity company in September 2023, highlighting the group's use of compromised Apple iCloud accounts to send smishing messages for carrying out identity theft and financial fraud.
Beat AI-Powered Threats with Zero Trust - Webinar for Security Professionals
Traditional security measures won't cut it in today's world. It's time for Zero Trust Security. Secure your data like never before.
Join NowThe threat actor is also known to offer ready-to-use smishing kits for sale to other cybercriminals for $200 a month, alongside engaging in Magecart-style attacks on e-commerce platforms to inject malicious code and pilfer customer data.
"This fraud-as-a-service (FaaS) model enables 'Smishing Triad' to scale their operations by empowering other cybercriminals to leverage their tooling and launch independent attacks," Resecurity noted.
The latest attack wave is designed to target individuals who have recently updated their residence visas with harmful messages. The smishing campaign applies to both Android and iOS devices, with the operators likely using SMS spoofing or spam services to perpetrate the scheme.
Recipients who click on the embedded link the message are taken to a bogus, lookalike website ("rpjpapc[.]top") impersonating the UAE Federal Authority for Identity, Citizenship, Customs and Port Security (ICP), which prompts them to enter their personal information such as names, passport numbers, mobile numbers, addresses, and card information.
What makes the campaign noteworthy is the use of a geofencing mechanism to load the phishing form only when visited from UAE-based IP addresses and mobile devices.
"The perpetrators of this act may have access to a private channel where they obtained information about UAE residents and foreigners living in or visiting the country," Resecurity said.
"This could be achieved through third-party data breaches, business email compromises, databases purchased on the dark web, or other sources."
Smishing Triad's latest campaign coincides with the launch of a new underground market known as OLVX Marketplace ("olvx[.]cc") that operates on the clear web and claims to sell tools to carry out online fraud, such as phish kits, web shells, and compromised credentials.
"While the OLVX marketplace offers thousands of individual products across numerous categories, its site administrators maintain relationships with various cybercriminals who create custom toolkits and can obtain specialized files, thereby furthering OLVX's ability to maintain and attract customers to the platform," ZeroFox said.
Cyber Criminals Misuse Predator Bot Detection Tool for Phishing Attacks
The disclosure comes as Trellix revealed how threat actors are leveraging Predator, an open-tool designed to combat fraud and identify requests originating from automated systems, bots, or web crawlers, as part of various phishing campaigns.
The starting point of the attack is a phishing email sent from a previously compromised account and containing a malicious link, which, when clicked, checks if the incoming request is coming from a bot or a crawler, before redirecting to the phishing page.
The cybersecurity firm said it identified various artifacts where the threat actors repurposed the original tool by providing a list of hard-coded links as opposed to generating random links dynamically upon detecting a visitor is a bot.
"Cyber criminals are always looking for new ways to evade detection from organizations' security products," security researcher Vihar Shah and Rohan Shah said. "Open-source tools such as these make their task easier, as they can readily use these tools to avoid detection and more easily achieve their malicious goals."
Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post.