2023-12-22 23:43:20 Author: www.sentinelone.com(查看原文) 阅读量:13 收藏
The Good | Latest Global Crackdown Hailed a Success With 3500 Cybercriminals Arrested and $300 Million Funds Seized
3,500 suspected cybercriminals of all levels found themselves nabbed this week by a major international law enforcement initiative dubbed Operation HAECHI IV. The arrests were accompanied by the confiscation of a staggering $300 million in illegal gains. The half-year long operation, spearheaded by South Korean authorities, saw collaboration with agencies from 34 nations, including major players such as the United States, the United Kingdom, Japan, and India.
👮👮♀️Operation Haechi IV makes online world safer for all by attacking AI-driven scams and e-frauds: 🚔3000 arrests, 82,000 suspicious accounts blocked & USD 300 million seized & networks disrupted #CyberSecurity https://t.co/tlHuam6xYx
— INTERPOL (@INTERPOL_HQ) December 19, 2023
This expansive operation unfolded between July and December 2023, with a primary focus on combating threat actors engaged in a spectrum of cybercrimes that ranged from e-commerce and investment fraud, business email compromise (BEC), voice phishing, online sextortion, and illicit online gambling. Additionally, Interpol identified and froze a substantial 82,112 bank accounts across 34 countries linked to various cybercrimes and fraudulent activities.
The operation revealed two key threat trends that continue to gain traction in the current cybercrime world. The first focuses on digital investment frauds and NFT investment platforms that operate briefly before a final “rug pull”, where the scammers abscond with all invested funds and erase all traces of their existence. The second adds to existing concerns about the use of artificial intelligence (AI) by threat actors. HAECHI found that the fraudsters leveraged AI and deepfake tools to mimic real individuals’ voices to further their impersonation scams.
Interpol has emphasized the gravity of the $300 million seizure, describing it as a clear driving force behind the rising nature of transnational organized crime. Global involvement in major operations like HAECHI continue to underscore the need for disrupting underground financial infractures that fund and support hierarchies of cyber threat actors and groups.
The Bad | Chameleon Banking Trojan Gets a Feature Upgrade Allowing Hackers to Steal Android Device PINs
Android users were put on high alert this week with news of a novel version of Chameleon banking trojan enabling hackers to steal device PINs. Security researchers reporting on the latest iteration noted that targets have spread to include users in the UK and Italy.
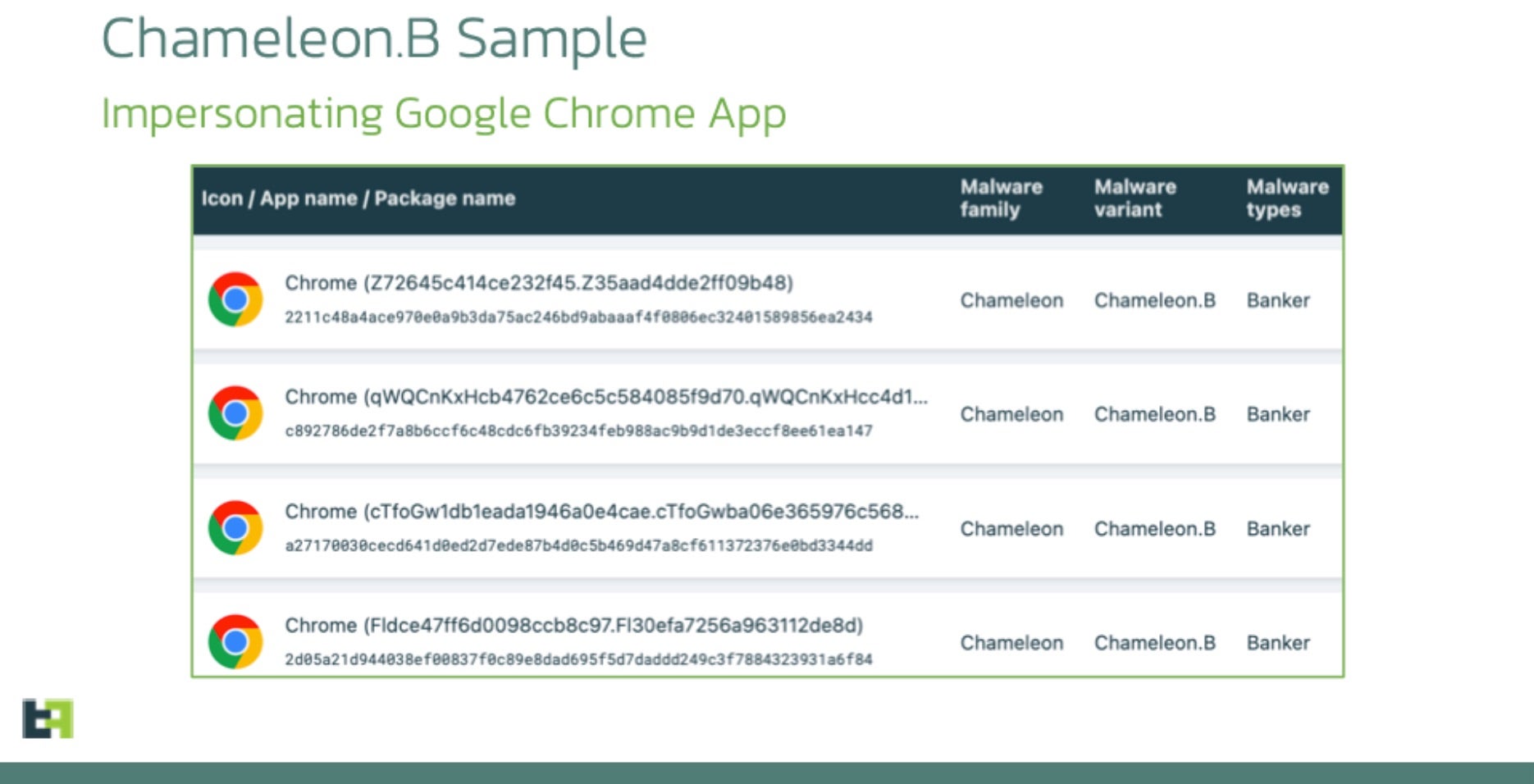
Analysis of the resurgence indicates that Chameleon is now distributed through an off-the-shelf Dropper-as-a-Service (DaaS) called Zombinder, allowing the trojan to masquerade as a Google Chrome web browser. Zombinder attaches malware to legitimate Android apps, tricking victims to unknowingly use the intended app while dangerous code runs in the background.
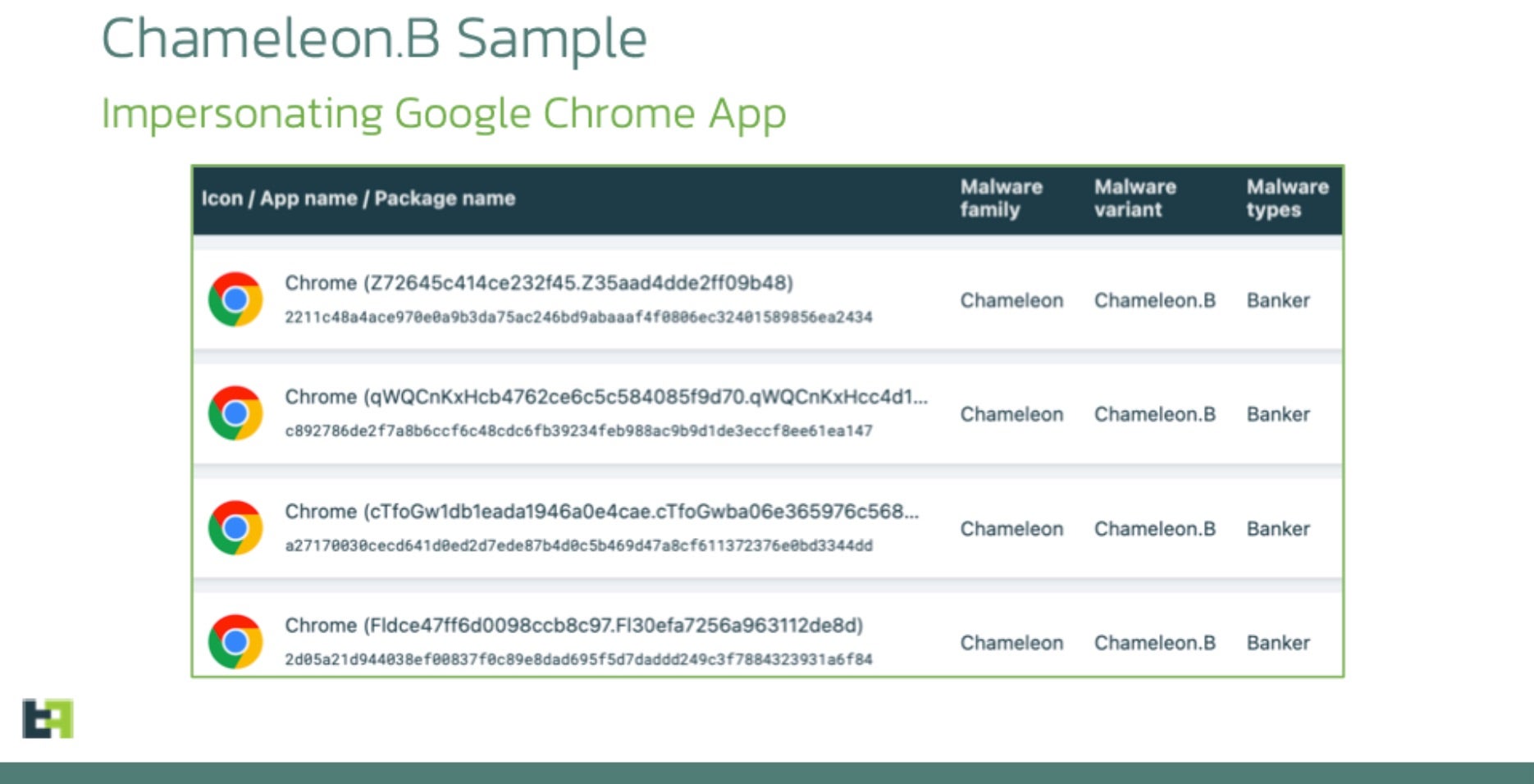
The latest Chameleon variant introduces two notable features. Firstly, it displays an HTML page on devices running Android 13 and later, prompting victims to grant permission for the app to use the Accessibility service. By detecting Android 13 or 14, the malware bypasses the “Restricted Setting” security feature, enabling it to guide users through a manual process to activate Accessibility and overcome system protections. Secondly, Chameleon disrupts biometric operations like fingerprint and face unlock, forcing a fallback to PIN or password authentication using the Accessibility service. The trojan captures entered PINs and passwords, allowing it to unlock the device at will for malicious activities concealed from the user.
These feature enhancements speak to the adaptability of the new Chameleon variant, positioning it as a more potent threat in the mobile banking landscape. To mitigate the threat, users are advised to avoid downloading Android package files (APKs) from unofficial sources, as this is the primary distribution method for the Zombinder service. Users should also ensure that Play Protect is enabled and conduct regular device scans for malware and adware.
The Ugly | Millions Impacted In Data Breach of Major Electronic Health Record Software Company
ESO Solutions informed their customers this week of a ransomware attack on their systems, which compromised the personal data of 2.7 million patients. The company is a major supplier of electronic health record (EHR) products for various healthcare organizations and fire departments across the U.S. As of this writing, no ransomware group has claimed responsibility for the ESO attack.

According to their notice, the initial attack occurred in late September and involved data exfiltration before the attackers encrypted several company systems. This tactic points to double extortion where victims are threatened in a two-pronged approach: first, the victim is threatened to decrypt their files via ransom payment, and then they face the risk of having the stolen files and data leaked or sold online. This strategy amplifies the impact of ransomware attacks, putting the victim in a very dangerous dilemma. Paying the ransom fuels the attackers to continue future threat campaigns, and refusing to pay means losing sensitive information.
In the attack on ESO, the attackers were able to access a machine containing sensitive personal data of several ESO clients, including full names, dates of birth, phone numbers, patient account/medical record numbers, injury type and date, diagnosis information, treatment type and date, procedure details, and Social Security Numbers (SSNs).
ESO Solutions has confirmed that other than notifying the FBI and state authorities, they took affected systems offline immediately and successfully restored operations through viable backups. The company also clarified that currently, no evidence has been found that the compromised data has been misused. To mitigate the short and long-term risks post-breach, ESO has offered 12 months of identity monitoring service coverage to affected individuals.
如有侵权请联系:admin#unsafe.sh