Apache Struts is a popular open-source web application framework used to develop MVC-based web applications. The widespread adoption of the Apache Struts framework has resulted in the related applications being targeted by malicious actors over the years. The popularity of the framework results in a major concern across organizations for any related vulnerability.
About CVE-2023-50164
CVE-2023-50164 was published on December 7th, 2023 to create awareness of a critical vulnerability in Apache Struts 2. A CVSS score of 9.8 has been assigned to the vulnerability.
Specific versions of Apache Struts2 allow for a malicious file to be uploaded.
The file upload functionality implementation in Apache Struts 2 leads to a Remote Code Execution.
Based on the advisory, the following versions are vulnerable:
Apache Struts 2.0.0 – 2.3.37
Apache Struts 2.5.0 – 2.5.32
Apache Struts 6.0.0 – 6.3.0
The vulnerability has been addressed with versions 2.5.33, 6.3.0.2, and above.
Detecting the Vulnerability with Qualys WAS
Qualys has released QID 150774: Apache Struts2 Remote Code Execution Vulnerability to detect vulnerable applications.
The new detection released to production is intrusive. As part of the security testing of the application when the Qualys WAS scan is launched, an attempt is made to upload a couple of non-malicious files – ‘Qualyswas.txt’ and ‘Qualyswas.jsp’. Vulnerable applications will successfully upload the file(s). When the QID is reported in your scan against your Struts application, the vulnerable server should be reviewed. Please search the server directory for the presence of uploaded files and remove the file(s).
Detection will be flagged as “Broken Access Control” of OWASP Top 10 2023 and categorized under “Information Disclosure” vulnerabilities.

The number of detections will increase in their dashboard under a Severity of ‘5’.
Please refer to the knowledge base on your Qualys Portal to get details on the vulnerability.

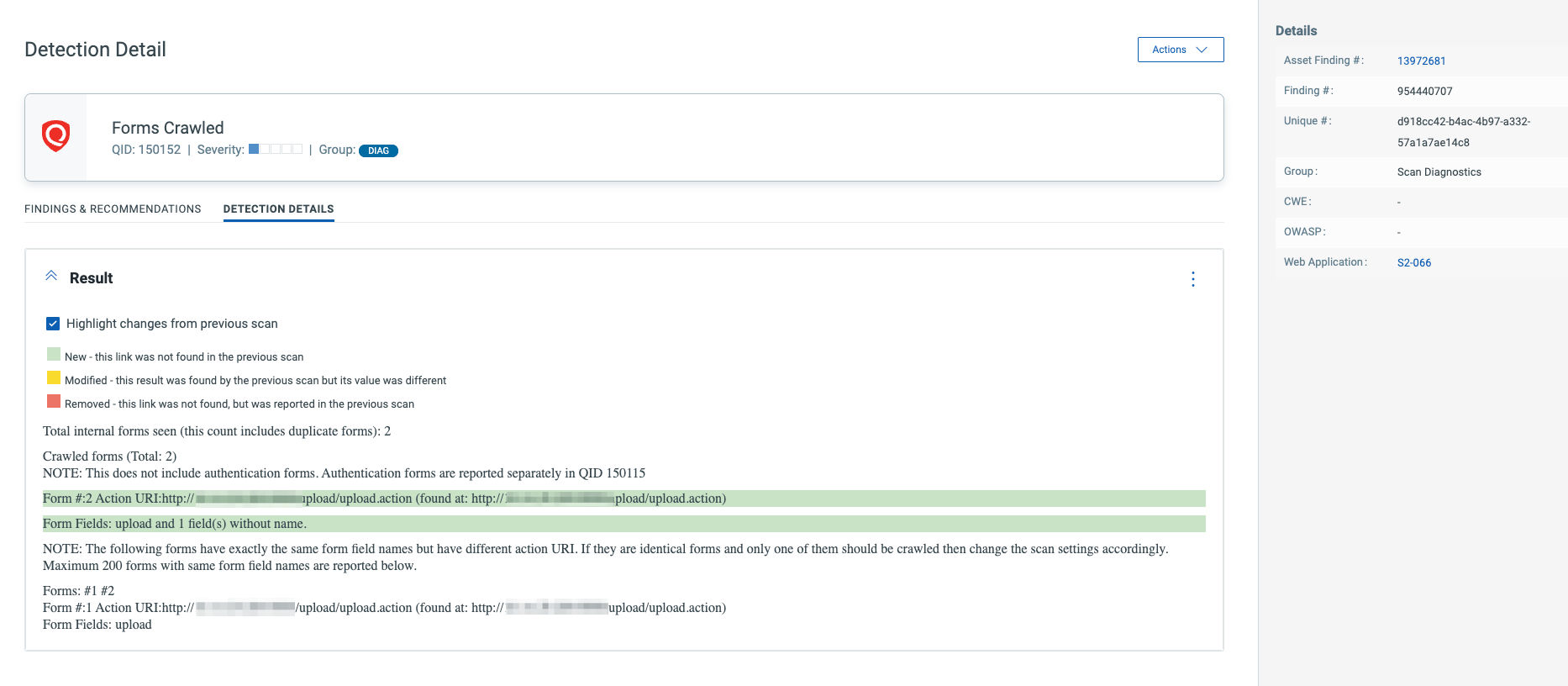
In addition to this QID, please review 150125 IG QID that identifies a file upload form in a Qualys WAS scan.


The upload form will also be listed in your scan report under the list of forms identified in IG QID 150152

If the QID is detected but files are not present on the server, please log a ticket with Qualys support to analyze the detection further.
Solution
Customers are advised to upgrade to Struts versions 2.5.33, 6.3.0.2, or later to patch the vulnerability.
Once your server has been upgraded to the patched version, use the “Retest” option to confirm the mitigation of the vulnerability on your server.
Protection with WAF
You can take advantage of your WAF to avoid being exploited.
Credits
- https://cwiki.apache.org/confluence/display/WW/S2-066
- https://lists.apache.org/thread/yh09b3fkf6vz5d6jdgrlvmg60lfwtqhj
- https://nvd.nist.gov/vuln/detail/CVE-2023-50164
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-50164
Additional Contributors
Mayank Deshmukh, Senior Web Application Signatures Engineer