2024-1-3 23:15:43 Author: lab.wallarm.com(查看原文) 阅读量:10 收藏
Network Detection and Response (NDR): Demystifying the Basics

The Internet Security Tool known as Network Analysis and Immediate Action (NAIA) signifies a transformational step in cyber protection. This innovative framework fuses the power of artificial intelligence and the predictive prowess of machine learning, providing pre-emptive safeguarding against potential cyber invasions. Think of NAIA as the all-seeing warder of your digital dominion, bolstering network fortresses, broadening the comprehension of network links, identifying possible trespassers, and rapidly neutralizing risks.
Let's break down the three primary components of NAIA:
-
Relentless Network Supervision: This duty involves permanent tracking and investigation of network motions to identify anomalies. Sophisticated computational models intermingle with threat intelligence tactics to differentiate regular workflows from unusual incidents.
For instance, here's an illustrative tutorial on how to employ Scapy for network logging in Python.
<code class="language-python"># Network mapping with Python import scapy.all as scapy def network_sentry(ip): scapy.arping(ip) network_sentry("10.0.2.1/24")</code> -
Threat Neutralization: When a risk is detected, the system promptly mobilizes its resources. The correlated actions may entail segregating the infected subsystems, blacklisting questionable IP addresses, or instantly alerting the security personnel.
As an elemental safety measure, here's a method to halt traffic from an unreliable IP address using Python's iptables facility.
<code class="language-python"># Python sequence for risk isolation import os def threat_quarantine(ip): os.system(f"iptables -A INPUT -s {ip} -j DROP") threat_quarantine("192.168.1.10")</code> -
Management of All Network Frontiers: This segment covers the total virtual width of an organization. NAIA utilities tirelessly oversee all network paths, covering in-house, cloud-oriented, and integrated architectures.
When juxtaposing the superior proficiencies of NAIA against other safety mechanisms, we discover:
| Protection Technique | Network Scope | Danger Recognition | Swift Intervention | AI & ML Participation |
|---|---|---|---|---|
| Firewall | Restrained | Elementary | Manual | Nonexistent |
| Intrusion Awareness System (IAS) | Comprehensive | Commendable | Manual | Rare |
| Network Analysis and Immediate Action (NAIA) | Comprehensive | Commendable | Automated | Mandatory |
Unquestionably, NAIA takes centre stage featuring wide-ranging network scrutiny, advanced danger recognition facilities, and immediate automated responses, all underpinned by AI and ML.
To wrap up, NAIA surfaces a groundbreaking security procedure which exploits the might of AI and ML to detect and mitigate hazards that breach your network defenses. This model enhances network survey transparency and equips you to tackle threats before they provoke substantial harm.
Unfolding The Need for NDR: Ensuring Business Security
Exploring NDR's Capabilities: A Long-Term Shield for Your Business
The modern world, heavily driven by digital mechanisms, sees organizations often relying on innovative advancements in tech and virtual realms. In this setting, the need for strong network infrastructures is ever-increasing. Network Detection and Response (NDR) has brought about a remarkable revolution, transforming how businesses reinforce their network environment against cyber infiltrations. Let's examine NDR's role in strengthening corporate security.
Decoding NDR's Importance for Companies: A Detailed AnalysisDecoding NDR's Importance for Companies: A Detailed Analysis
The swift rise in complex cyber invasions underscores the vital importance of NDR. Cyber adversaries continuously innovate their tactics, making traditional security walls fall behind. Here, NDR stands as a guardian of network purity, identifying and incapacitating cyber threats before they cause chaos.
- Mitigating New Threats: Traditional protections often overlook unique dangers such as zero-day intrusions, Advanced Persistent Threats (APT), or insider perils. NDR utilizes avant-garde tech like machine learning and artificial intelligence for quick danger detection.
<code class="language-python"># This code exemplifies the application of machine learning in danger detection via NDR. from sklearn.ensemble import IsolationForest # Suppose 'data' is the network data clf = IsolationForest(contamination=0.01) clf.fit(data) # Forecast anomalies in the data pred = clf.predict(data) # -1 signifies anomalies anomalies = data[pred == -1]</code>
-
Accelerated Danger Identification: NDR delivers timely and precise threat detection, outdoing conventional security approaches that heavily bank on signature-based recognition. It consistently monitors network activities, signalling any abnormal patterns hinting at potential dangers.
-
Automated Quarantine: NDR doesn't just sound the hazard alerts; it ensures their speedy confinement, significantly narrowing the time between threat identification and consequent action, thus lessening prospective damage.
-
Thorough Surveillance and Control: NDR provides a bird's eye view of network interactions, granting corporations firm control over their security. It excels at spotting devices connected to the network, monitoring data exchange, and unmasking potential security vulnerabilities.
Contrasting Conventional Security Methods and NDR
| Characteristics | Conventional Security Methods | Network Detection and Response (NDR) |
|---|---|---|
| Threat Identification | Primarily Signature-based | Immediate and behaviour-centric |
| Threat Quarantine | Human intervention required | Quick automated quarantine |
| Protection Against Existing Threats | Limited | Wide-ranging |
| Network Comprehension | Limited | Thorough |
In conclusion, the immediate requirement for NDR in enhancing business security is undeniable. It offers an attentive, exhaustive, and automated formula for network protection, allowing companies to stand strong against the constantly evolving cyber menaces. As these threats continue to reshape and multiply, the pertinence of NDR will undoubtedly skyrocket.
`
`
Unveiling the Key Elements and Functions of Network Analysis and Reaction Mechanism
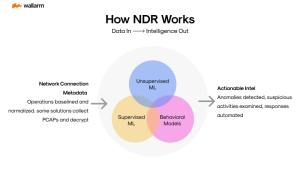
Network Analysis and Response Mechanism (NARM), due to its efficient performance, is rightly considered the cornerstone of modern-day protections against cyber-attacks. This chapter aims to delve into the essential aspects and workings of NARM and illuminate its contributions to the digital security landscape.
1. Prompt Danger Detection
At the heart of NARM lies the quick recognition of potential risks. NARM utilities continuously monitor network traffic, calling out any suspicious or unusual actions. The precision in threat recognition is attributable to advanced algorithms and artificial intelligence techniques which detect signs indicative of emerging risks.
<code class="language-python"># Exemplified Python code for prompt danger detection
def threat_detection(data_stream_live):
for data_entry in data_stream_live:
if data_entry['activity'] in suspect_operations:
raise_alert(data_entry)</code>
2. Automated Reactive Actions
Suitably, NARM utilities go beyond merely identifying threats, integrating automated responses to detected dangers. Options range from dispatching alerts to the security team to blocking suspicious IP addresses and even secluding compromised systems to prevent further intrusion.
<code class="language-python"># Exemplified Python code for automated reactive actions
def response_actions(threat_info):
if threat_info['risk_score'] > SET_THRESHOLD:
block_ip(threat_info['ip'])
else:
alert_security_unit(threat_info)</code>
3. Comprehensive Packet Analysis
Comprehensive Packet Analysis (CPA) is a prominent feature of NARM utilities that allows them to examine the data segment (rather than just the header) of a packet as it passes through a checkpoint. This strategy proves effective in identifying concealed threats like malware and application-layer attacks.
4. Behavioral Analysis
To understand the regular patterns of users, apps, and hardware within the network, NARM utilities employ behavioral analysis. Any variation from the perceived 'norm' is flagged as suspicious, proving particularly useful in detecting internal threats or compromised credentials.
5. Threat Information Alignment
NARM utilities, possessing the capability to align with threat information databases, can draw from the wealth of global threat data. This aids in detecting recognized malevolent IPs, URLs, and other signs of compromise, thus improving the threat detection capacity.
6. Total Visibility and Perception
NARM utilities provide total visibility into network traffic, exposing intricate details about user patterns, device use, software performance, and more. This is beneficial for proactive threat hunting, incident response strategies, and forensic investigations.
7. Scalability
Built to handle the vast data churned out by modern networks, NARM utilities demonstrate impressive scalability. They evolve along with the growth of the network, ensuring consistent output and threat detection capability.
8. Smooth Cohesion with Existing Security Architecture
NARM utilities are compatible with the existing security set-up, including firewalls, SIEM systems, and endpoint protection platforms. This attribute enables a unified and streamlined network security strategy.
Summing up, Network Analysis and Response Mechanism tools boast of a diverse range of features and functions that strengthen your cybersecurity stance. Equipped with prompt threat detection, automated reactive measures, comprehensive packet analysis, and behavioral analysis, among others, NARM tools markedly boost an organization's defense against cyber intrusions.
Unraveling the Complexities: A Journey into the Gears of Network Spotting and Managing (NSM)
Marvel at the deep-sea exploration of Network Spotting and Management (NSM), a pioneering intelligence defense tactic that leverages the superior capabilities of Advanced Informatics (AI) and Cognitive Learning (CL). The emphasis is on pinpointing, scrutinizing, and efficient countermeasures against electronic threats lurking in your infrastructure.
1. Fact Compilation (Information Aggregation):
The commencement phase of an NSM technique encompasses data synthesis. NSM mechanisms harness valuable information from numerous components within the network, such as traffic motion, chronicles, and other pertinent safety facts. This data storehouse is crucial for discerning customary network operations.
<code class="language-python"># Python script for the fact-gathering function.
def aggregate_information(network):
composite_data = []
for origin in network.origins:
composite_data.append(origin.derive_details())
return composite_data</code>
2. Analysis and Cognition (Information Dissection):
Following the accumulation phase, the NSM approach deploys cognitive learning utilities to navigate the amassed dataset. The purpose is to distinguish between habitual trends and disparities that could imply potential safety violations.
<code class="language-python"># Python script for the data inspection function.
def dissect_information(composite_data):
oddities = []
for factor in composite_data:
if identifies_disparity(factor):
oddities.append(factor)
return oddities</code>
3. Risk Calibration (Peril Estimation):
In the peril estimation step, probable dangers ascertained by the NSM configuration undergo thorough examination. This scrutiny includes juxtaposing disparities with existent peril indicators, estimating potential repercussions, and formulating an efficacious counteract strategy.
<code class="language-python"># Python script for the danger calibration function.
def estimate_perils(oddities):
risks = []
for oddity in oddities:
if presents_peril(oddity):
risks.append(oddity)
return risks</code>
4. Solution Implementation (Remedial Course):
In the wrapping up stage, upon the certainty of a threat, the NSM plan goes into action to tackle the danger. The responsive action could encompass mitigating the risk, alerting the intel-security team, or initiating mechanical safeguards.
<code class="language-python"># Python script for implementing solutions.
def instigate_solutions(risks):
for risk in risks:
if risk.requires_attention():
neutralize_risk(risk)
else:
notify_security_team(risk)</code>
| Stage | Summary |
|---|---|
| Fact Compilation | Aggregates information from different variables in the network |
| Analysis and Cognition | Uses cognitive learning tools to examine the collected data and spot potential violations |
| Risk Calibration | Assesses identified disparities to understand their implications |
| Solution Implementation | Responds to verified threats by executing countermeasures, notifying the intel-security team, or triggering corrective procedures |
In our summary, the NSM method is a succession of fact compilation, analysis and cognition, peril estimation, and solution implementation. All these stages form a holistic security barricade for your network, actively spotting and subduing threats.
Deciphering Threats with Network Intelligence: An In-Depth Exploration
Integral to cyber-security, Network Intelligence Response (NIR), is an advanced technique that significantly aids in pinpointing and addressing network threats. Let's take a detailed exploration into how NIR operates, offering an in-depth analysis into its intricate workings and functions.
1. Unearthing Threats: The DNA of NIR
At the heart of NIR is its essential function - laying bare threats within the network. Relying on an exhaustive examination of network communication and a unrelenting analysis for hints of harmful activity, NIR accomplishes this. This is made possible through a collaborative effort encompassing artificial intelligence algorithms, indicators of compromise (IOC) detection, and unconventional activity detection.
<code class="language-python">class NIR:
def __init__(self):
self.internet_traffic = []
self.irregularities = []
self.indicators = import_indicators()
def inspect_traffic(self, communication):
self.internet_traffic.append(communication)
self.unearth_threat(communication)
def unearth_threat(self, traffic):
if self.is_unusual(communication) or self.is_indicator_identified(communication):
self.andros_finest(communication)
def is_unusual(self, traffic):
# Unconventional detection algorithm here
pass
def is_indicator_identified(self, traffic):
# Indicator identifying algorithm here
pass
def andros_finest(self, traffic):
# Threat addressing algorithm here
pass</code>
This Python code sample offers a basic illustration of a NIR system's potential structure. It inspects network communication, unearths threats based on irregularities or indicator identification, and thoroughly addresses discovered threats.
2. Indicator of Compromise (IOC) Detection
IOC detection functions by leveraging observed patterns of detrimental behaviors to find threats. These patterns, coined 'IOCs', originate from threats that were previously spotted and studied. Extant network communication matching an established IOC makes the NIR system alert the potential threat.
| Mechansim | Explanation | Advantages | Drawbacks |
|---|---|---|---|
| IOC Detection | Detects threats by leveraging observed malicious patterns | Extremely efficient against pre-identified threats | Less successful with novel, uncharted threats |
3. Unconventional Activity Detection
Unlike IOC detection, unconventional activity detection functions by seeking variations from standard network activity. The NIR system establishes a benchmark for typical network communication patterns, then employs AI algorithms to identify discrepancies.
| Mechanism | Explanation | Advantages | Drawbacks |
|---|---|---|---|
| Unconventional Activity Detection | Discovers threats by pinpointing deviations from standard network conduct | Can unearth new, unidentified threats | Risk of false positives |
4. The Role of AI and Machine Learning in NIR
Both AI and machine learning play pivotal roles within NIR systems. They are predominantly employed in unconventional activity detection - helping to define the benchmark for network norms and identifying variations thereof. Machine learning algorithms can further enhance the system's threat-unearthing capabilities by adapting from past detections.
5. Addressing Discovered Threats
Upon detection of a threat, the NIR system must take proactive steps. This can range from isolating the affected network segment, disrupting the harmful communication, or even rolling out automatic patches. The specific action is dependent on the nature of the unearthed threat and the organization's cyber-security policies.
To conclude, NIR systems actively detect threats by relentlessly studying network communication, employing IOC and unconventional activity detection methodologies, and capitalizing on AI and machine learning. Once a threat is unearthed, the system addresses it in a way that neutralizes the threat and safeguards the network. This detailed look into NIR threat detection offers a deeper understanding of its functionalities, showcasing its paramount importance in modern cyber-security.
Leveraging Cyber Protection Mechanisms through Network Surveillance and Reaction (NSR): An Examination of Real-World Examples
The vast ocean of data security incorporates Network Surveillance and Reaction, frequently shortened to NSR. It is lauded for its integral participance in developing and strengthening the digital protective measures of numerous businesses. In this section, we'll dissect reliable real-world instances that underline how NSR is adept at discovering and handling online susceptibilities.
Example 1: Predominant Financial Institution
A formidable powerhouse in the financial industry was continuously bombarded by cyber invaders, leading to a noteworthy disruption in their seamless progression. Initially, the corporation relied on traditional protective structures, which were proven inferior in combating the rising tide of sophisticated online adversaries.
Recognizing the hurdles, the corporation decided on infusing NSR into their system architecture. The goal was to boost their digital protective prowess. The bedrock of NSR was established on the ceaseless oversight of the entirety of network interactions, identifying any inconsistencies, and immediate threat neutralization.
<code class="language-python"># A demonstrative code segment on how NSR evaluates network operations
def *study_traffic(nsR):
for data_flow in nsR.gather_packets():
if nsR.identifies_irregularity(data_flow):
nsR.quell_threat(data_flow)</code>
In the subsequent weeks, post the NSR integration, the company marked a distinct reduction in cyber invasion incidents. The NSR mechanism demonstrated its competency in identifying and eradicating threats that had previously slipped past the standard protective layers.
Example 2: An Enterprise in the Digital Trading Realm
An e-commerce entity was wrestling with a surplus amount of manipulative transactions. Despite an extensive security arrangement, the enterprise was unable to curb these unauthorized activities.
To rectify this predicament, the digital trading entity opted to integrate the NSR platform within their current system. The NSR mechanism was modeled to examine network interactions and pinpoint patterns echoing fraudulent transactions.
<code class="language-python"># A demonstrative code segment on how NSR detects dubious patterns
def *uncover_patterns(nsR):
for operation in nsR.compile_operations():
if nsR.detects_deception(operation):
nsR.void_threat(operation)</code>
Post the implementation of NSR, the company observed a precipitous decline in deceitful transactions. The NSR confirmed its worth by timely recognizing and neutralizing threats, thus mitigating potential losses.
Example 3: A Provider in the Medical Care Sector
A provider, operating in the healthcare services industry, found itself in the crosshairs of recurrent digital aggressions, leading to significant breaches in sensitive patient data. Initially, conventional security measures fell short in dealing with the complexities of the threats encountered.
In an effort to enhance their virtual fortifications, the provider decided to assimilate an NSR solution. The NSR was designed to ensure persistent surveillance of network operations, detect any deviation and promptly address any threats unearthed.
<code class="language-python"># A demonstrative sequence of how NSR secures patients' data
def *safeguard_information(nsR):
for record in nsR.extract_data():
if nsR.discovers_breach(record):
nsR.dilute_threat(record)</code>
Post integration of NSR, the healthcare center witnessed a considerable boost in its cyber defense standings. The NSR mechanism was found efficacious in identifying and eliminating threats that were previously ignored, preserving the integrity of patient data.
These real-life examples serve to authenticate the prowess of NSR in reinforcing digital security measures. By offering sustained surveillance of network operations, spotting unusual patterns, and swiftly rectifying threats, NSR can appreciably fortify a company's digital defense architecture.
Finally, NSR is a robust relic instrumental in amplifying cybersecurity tactics. It facilitates swift threat detection and reaction capabilities, thus thwarting significant data losses and guaranteeing the preservation of invaluable information.
`
`
Peering Into the Future: The Path of Network Detection and Response (NDR) in the Next Generation
Unraveling the future course of NDR, it is evident that this budding benchmark in cyber protection could significantly bolster our digital edifices. In this dialogue, we'll explore several groundbreaking developments that could shape the future course of NDR.
1. Increased Dependence on Artificial Intelligence and Machine Learning
At present, NDR frameworks rely on AI and ML to scrutinize behaviors and pinpoint inconsistencies. Amid rapid advancements in AI and ML industries, we're bound to witness an amplified tactical deployment within NDR operations.
These disciplines harbour enormous potential for scanning patterns within network traffic and spotting deviations that may hint towards cyber threats. Such openings could accelerate the process of threat pinpointing and handling, thus enriching digital security tactics.
<code class="language-python">class TrafficExaminer:
def __init__(self, input):
self.input = input
def examine(self):
# AI/ML driven assessment for identifying threats in
# network traffic
pass</code>
2. Shift towards Embracing Cloud-Based NDR
With corporations steering towards cloud environments, a corresponding rise in the acceptance of cloud-sourced NDR solutions is predictable. These security solutions boast advantages like scalability, cost efficiency, and comprehensive network traffic monitoring.
Yet, they also pose challenges like data safeguarding during transfer or storage. Anticipate the development of tailored security contracts and encryption techniques to counter these challenges.
3. Harmonious Union with a Variety of Cybersecurity Tools
Looking ahead, it's forecasted that NDR systems will blend seamlessly with a varied array of cybersecurity tools. Included will be preventative firewalls, intrusion detection mechanisms, endpoint security tactics, and Security Information and Event Management (SIEM) utilities.
Establishing such collaborations would empower businesses to construct a robust, fully-inclusive digital defense strategy.
<code class="language-python">class SecurityCoordinator:
def __init__(self, shield, irregularity_inspector):
self.shield = shield
self.irregularity_inspector = irregularity_inspector
def alert(self, concern):
# Trigger the defense mechanism and irregularity inspector if a
# threat is detected
self.shield.strengthen(concern)
self.irregularity_inspector.signal(concern)</code>
4. Boosted Focus on Threat Revelation
The active endeavor of unveiling concealed digital threats lurking behind security barriers, referred to as threat revelation, is on the rise. Leading-edge NDR entities powered by AI and ML will staunchly support this digital investigation.
5. Escalating Regulatory Analyses and Compliance Guidelines
As cyber threats transform, expect a surge in rigid regulatory actions and compliance mandates related to network safeguards. This may define the foundation for new cyber defense criteria for NDR deployments and heighten the examination of an organization's digital security procedures.
With these anticipated changes, the roadmap for NDR is filled with promise - progressive jumps in AI and ML, growing acceptance of cloud-centric strategies, deepening engagement with diverse cybersecurity gadgets, increased attention on threat revelation, and intensified regulatory examination. Businesses can wisely equip themselves for impending cybersecurity obstacles by staying updated with such transitions.
如有侵权请联系:admin#unsafe.sh