
2024-1-9 01:2:28 Author: securityboulevard.com(查看原文) 阅读量:7 收藏

The Network Information Systems Directive (NIS) was published in 2016 and required EU critical infrastructure sectors to meet basic cybersecurity compliance requirements. In October 2024 the second iteration of the Network Information Systems Directive (NIS2) will be going into effect, which will both substantially expand the number of entities required to be compliant in addition to creating additional penalties for non-compliance.
It’s important to note that EU regulation works by mandating that member states enshrine requirements into their own laws. NIS2 is a regulation propagated by the EU parliament requiring that member states use the fundamental requirements contained to create and maintain their own law codes which will be based on, and incorporate all requirements found in NIS2.
We will start by covering NIS before moving onto updated requirements in NIS2.
Key Goals of NIS2
Under NIS2 covered EU organizations will be required to meet specific operational security requirements, report incidents to their national CSIRT teams, and create continuous improvement in security procedures. NIS2 introduces personal liability for the “management bodies” of companies that fail to comply and involves fines the greater of €7,000,000 or 10% of gross turnover.
What is NIS?
NIS stands for the Network Information Systems Directive and was an EU compliance law published in 2016 and went into effect on 10 May 2018. NIS mandated that covered entities create basic cybersecurity hygiene processes and practices. NIS was originally intended to apply to critical infrastructure (labeled “essential services”), and was focused on creating reporting requirements as well as basic system hardening. Under NIS organizations are categorized as either “essential” or as “digital services providers” or “not covered” with specific requirements for each.
The directive mandates that organizations EU member states publish regulations meeting the following standard for essential services:
Member States shall ensure that operators of essential services take appropriate and proportionate technical and or organizational measures to manage the risks posed to the security of network and information systems which they use in their operations. Having regard to the state of the art, those measures shall ensure a level of security of network and information systems appropriate to the risk posed.
EU nations were instructed to create additional legal requirements for “Digital Services Providers” in which they were required to have the following:
(a) the security of systems and facilities;
(b) incident handling;
(c) business continuity management;
(d) monitoring, auditing and testing;
(e) compliance with international standards.
Additionally member states had to require that entities covered by the regulation proactively report incidents to their nations CSIRT team which would provide guidance based on the severity and impact of the incident.
NIS2: Expanded Scope & Mandate
Directive (EU) 2022/2555 (NIS2) is the successor directive to NIS and dramatically expands both the entities covered under the regulation and the specific requirements that organizations need to operate under. Like the original NIS directive, NIS2 is broad and will require all EU member states to implement their own version of the regulation. However, NIS2 is quite specific that EU Member states will need to:
Ensure that essential and important entities take appropriate and proportionate technical, operational and organizational measures to manage the risks posed to the security of network and information systems which those entities use for their operations or for the provision of their services, and to prevent or minimize the impact of incidents on recipients of their services and on other services.
NIS2 then lays out specific requirements that member states will need to require from covered organizations including:
The measures referred to in paragraph 1 shall be based on an all-hazards approach that aims to protect network and information systems and the physical environment of those systems from incidents, and shall include at least the following:
(a) policies on risk analysis and information system security;
(b) incident handling;
(c) business continuity, such as backup management and disaster recovery, and crisis management;
(d) supply chain security, including security-related aspects concerning the relationships between each entity and its direct suppliers or service providers;
(e) security in network and information systems acquisition, development and maintenance, including vulnerability handling and disclosure;
(f) policies and procedures to assess the effectiveness of cybersecurity risk-management measures;
(g) basic cyber hygiene practices and cybersecurity training;
(h) policies and procedures regarding the use of cryptography and, where appropriate, encryption;
(i) human resources security, access control policies and asset management;
(j) the use of multi-factor authentication or continuous authentication solutions, secured voice, video and text communications and secured emergency communication systems within the entity, where appropriate.
Notice how specific the requirements have become in NIS2 compared to the original NIS, with specific operational level details being spelled out in the regulation. Additional requirements for “Digital services providers” will be explored and incorporated later.
NIS vs NIS2: What is Covered?
Under NIS the two primary categories of covered entities were operators of essential services (OES) and relevant digital services providers (RDSPs). RDSPs had additional requirements compared to OESs. NIS Lays out a framework for member states to identify RDSPs and OESs. Annex II provides a specific list of covered entities to include:
- Electricity Companies
- Oil Companies
- Gas Companies
- Air Transport
- Rail Transport
- Road Transport
- Healthcare
- Banking
- Financial Markets
- Drinking and Water Supply
- Digital Infrastructure
NIS2 dramatically expands the scope of companies that are covered by the law by adding a category for “Important Entities” which are required to also meet key requirements. Newly added sectors include:
- Waste management
- Manufacturing
- IT & Security Services Providers
- Postal & Courier sServices
- Chemicals Companies
- Food Processing
- Research Organizations
- Social Networks and Digital Providers
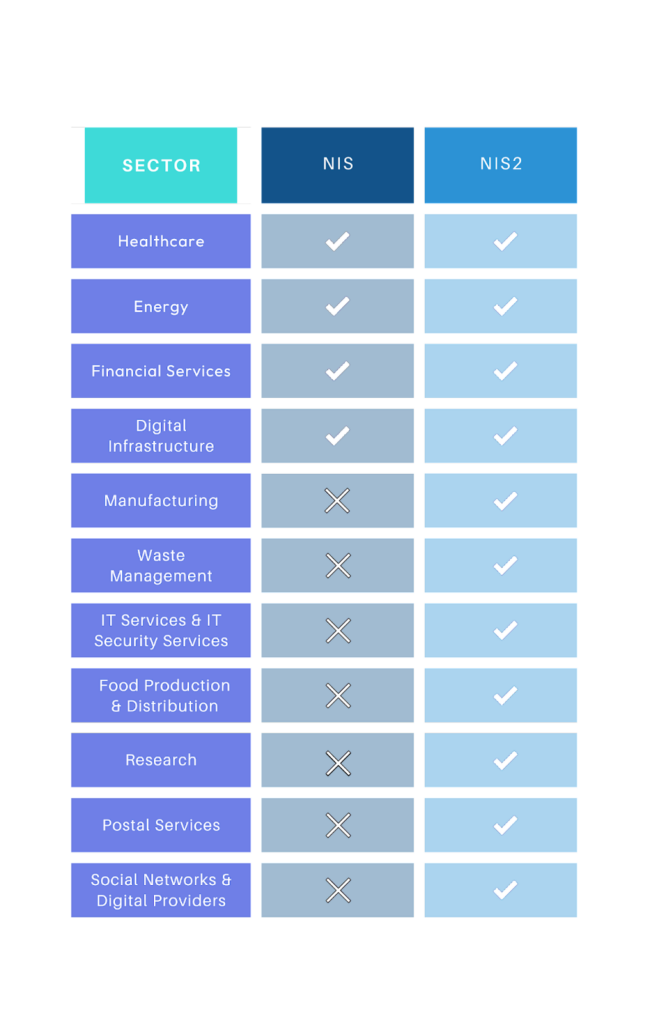
Industries that NIS vs NIS2 cover
NIS2 and Supply Chain Risk Management
Supply chain risk management is a critical component of NIS2. Notably NIS2 goes substantially further than other cybersecurity regulations by mandating companies evaluate their extended supply chain and additionally that organizations identify specific vulnerabilities related to third-party suppliers.
Member States shall ensure that, when considering which measures referred to in paragraph 2, point (d), of this Article are appropriate, entities take into account the vulnerabilities specific to each direct supplier and service provider and the overall quality of products and cybersecurity practices of their suppliers and service providers, including their secure development procedures. Member States shall also ensure that, when considering which measures referred to in that point are appropriate, entities are required to take into account the results of the coordinated security risk assessments of critical supply chains carried out in accordance with Article
In addition organizations are mandated to consider risks related to their downstream supply chain, although without the requirement to identify specific vulnerabilities.
Penalties for Non Compliance with NIST2
NIS2 requires EU member states to impose steep penalties for non-compliance. Member states are required to impose a fine of €10,000,000 Euros of 2% of global annual turnover for entities defined as “critical” and € 7,000,000 or 1.4% of global turnover for entities defined as important.
Corporate Management Liability
An approach to cybersecurity that directly involves the “management bodies” of organizations is a key element of NIS2. The EU is clearly attempting to create a legal and business practice that requires CEOs, boards of directors, and senior management to take a direct part in the organization’s cyber risk management plan. NIS2 states
Member States shall ensure that the management bodies of essential and important entities approve the cybersecurity risk-management measures taken by those entities in order to comply with Article 21, oversee its implementation and can be held liable for infringements by the entities of that Article.
The inclusion of personal liability for management is a stark departure from U.S. cybersecurity regulations and previous EU regulations.
What Else is Included in NIS2?
NIS2 is not just focused on business but also on ensuring that EU member states improve their national cybersecurity postures. As a result NIS2 incorporates several requirements that apply to EU member states and are focused on creating a more collective defense.
NIS2 and Incident Reporting Requirements
Expanded incident reporting is a critical aspect of NIS2. Under the regulation organizations will be required to report incidents within 24 hours, and provide a more complete report by the end of the third day of the incident.
Mandates for CSIRT Teams
CSIRT teams take center stage in NIS2. EU Nation CSIRT teams are tasked with acting as a central repository for covered entity incident reporting. In addition CSIRT teams are instructed to provide incident guidance for covered entities that report an incident to them.
EU Vulnerability Database
NIS2 is focused not only on improving the cybersecurity of individual companies but also on creating better EU cyber readiness. To this end NIS2 mandates that the EU create a vulnerability database where information to catalog vulnerability data and enable seamless sharing between various national governments.
The Bottom Line: NIS2 & Corporate Cybersecurity
NIS2 is going to remake much of the EU cybersecurity landscape. The EU is pushing organizations and national governments to prioritize information security as a core element of national security. NIS2 represents a break from previous EU-wide cybersecurity regulations by mandating personal liability for corporate executives, specific requirements that covered entities must follow, and by requiring unprecedented coordination between national governments.
The supply chain requirements in NIS2 are also fairly unique. Requiring organizations to identify specific vulnerabilities related to third-party suppliers represents a substantial break from previous supply chain risk management practices which typically just required evaluating potential suppliers for adequate cybersecurity.
NIS2 represents a significant enhancement of existing EU and global cybersecurity regulation which will likely be further enhanced in coming years – particularly for organizations classified as digital services providers. Organizations would do well to adopt robust, defensible, and aggressive cybersecurity regimes that allow them to demonstrate proactive compliance that not only meets, but exceeds auditor expectations.
Please note that this blog is not intended to educate on basic requirements in NIS2 and is not a substitute for legal advice. If you are concerned with NIS2 or believe that it might apply to your organization we encourage you to contact a qualified attorney.
Corporate Cybersecurity with Flare
Flare is a Threat Exposure Management (TEM) solution that automatically detects threats across the clear & dark web and illicit Telegram channels that cause organizations to suffer data breaches.
Our platform automatically monitors your and third-party organizations so you can act quickly on remediation based on our prioritized alerts.
The post NIS2 Compliance: Updated for 2024, Complete Guide appeared first on Flare | Cyber Threat Intel | Digital Risk Protection.
*** This is a Security Bloggers Network syndicated blog from Flare | Cyber Threat Intel | Digital Risk Protection authored by Flare. Read the original post at: https://flare.io/learn/resources/blog/nis2-compliance/
如有侵权请联系:admin#unsafe.sh