2024-1-9 06:24:13 Author: www.forcepoint.com(查看原文) 阅读量:17 收藏
The attack starts off with a seemingly inconspicuous email regarding voting in the upcoming general election, as follows:
“What not to do on voting day? If you commit a crime, you will be fined NT$2 million and jailed for two years.”
The email goes on, listing some of the things that a voter should not be doing on the election day:
“Voting steps:
1. Bring your ID card, seal, and voting notice to the voting station.
2. Show your ID to the on-site staff for identity verification.
3. Sign or stamp the ballot to receive it.
4. Go to the ballot box to vote and use the Election Committee’s stamping tool to circle your ballot.
5. Insert the ballot into the corresponding slot.
6. Complete your vote.”
Interestingly, the email never explicitly entices the user to click on any attachments, but the document attached is called the following:
Voting Instructions.docx
Our investigations have revealed that multiple versions of the same document (hashes listed below) have been sent to prominent business leaders. It is currently not clear what the attackers are looking to gain, but it could be to monitor the sentiments of voters.
So, next up is the Word document itself. It is a completely blank and empty word document, but investigating the document.xml properties, it shows a link to an OleObject:
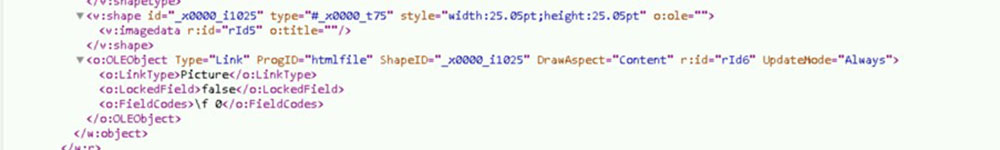
This is similar to the Follina exploits of 2023 but with one key difference, the link type is now represented as a picture and UpdateMode is set to Always rather than “OnCall.” This means that the script auto executes on document open. We believe that there is a second stage dropper, exploiting a new vulnerability in Windows, similar to the Microsoft diagnostic tool exploit seen within the Follina attack chain.

Within document.xml.rels, there is a reference to an external OleObject which has a target of the stage 2 dropper. This URL has been redacted due to the link still being active and working. Forcepoint is working with the relevant authorities to ensure the link is shut down and made inactive.
We have been unable to execute the second stage of the attack, due to the extremely targeted nature of the attack. It is likely that the web server hosting the second stage is configured to deploy the second stage to specific IP addresses.
In lieu of this, we deployed the second stage of the Follina attack to demonstrate that the embedded OleObject is a new, novel way of being able to launch an MSHTML file to deploy the malware payload itself.
At this moment in time, it is not clear that there is any ability to change the configuration of Microsoft Office to prevent this exploit.
Zero Trust CDR Protects Against This Attack
Anti-malware detection is not working – the example document is not currently being reported as malicious by any of the prominent vendors on VirusTotal – probably because targeted attacks like this don’t have the consistency of patterns to form accurate signatures.
What’s needed is a way of stopping the initial malware reaching its target, and that’s what Forcepoint’s Zero Trust CDR achieves. It doesn’t deliver the original file. It builds a new file that looks and feels the same, but without the malicious content. In this case, the OleObject reference is external, so we simply do not build the new file with reference.
Forcepoint’s Zero Trust CDR is the only solution that can viably remove zero day and advanced undetectable threats without ever needing to rely on detection.
Indicators of Compromise:
173c918e70f989ce7b5730cab2458bae7591db6d30400988803c9ecbc63cf68a
如有侵权请联系:admin#unsafe.sh