2024-1-9 23:47:24 Author: www.horizon3.ai(查看原文) 阅读量:12 收藏
Since introducing NTLM coercion techniques such as PetitPotam into the NodeZero platform, we frequently have security practitioners request help understanding these techniques and what impact they have to their enterprise. There is a lack of concise resources to inform Blue Teams on how these techniques work, and clearly distinguishing them from other misconfigurations/vulnerabilities in the attack chain – particularly the NTLM Relay vulnerable Active Directory Certificate Services (ADCS) HTTP web endpoints.
The level of risk NTLM coercion opportunities provide in a network depends on the environment and mitigation of said risk can be done at several points in the attack chain – keep patched, prevent attackers from obtaining user credentials, and minimize the relay attack surface.
Back to Basics – NTLM Relay Attacks
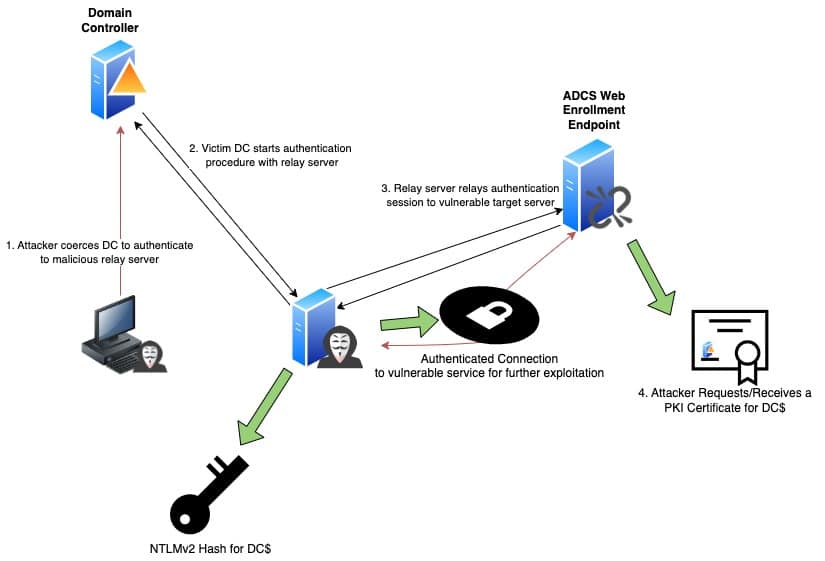
NTLM Relay Attack with Coercion and ADCS ESC8
The primary use case for PetitPotam and other NTLM coercion techniques is to source authentication material for an NTLM relay attack. NTLM relaying is a popular and useful man-in-the-middle tactic that takes advantage of the 20-year-old NTLMv1/2 challenge-response authentication protocol. An attacker, via “some mechanism”, is able to intercept authentication requests from a client and forward them to a vulnerable service configured to use NTLMv1/2 for authentication. The end result: the vulnerable service authenticates the attacker, believing they are the original client.
Historically, passive protocol poisoning techniques were the primary method for attackers to initiate an NTLM relay attack. These techniques rely on an enterprise using vulnerable broadcast protocols, such as LLMNR or mDNS, to reroute connection requests to a relay server. With the introduction of NTLM coercion attacks, researchers discovered a whole new world for getting a source client to initiate an authentication session with a relay server.
NTLM Coercion – Sourcing Privileged Machine Credentials for NTLM Relay Attacks
The beginning of the NTLM coercion hype started in 2018 when researcher Lee Christensen (@tifkin_) and others at SpectreOps reported an MS-RPRN abuse to Microsoft. The issue, to become widely known as “PrinterBug” in the community, was an authenticated method (i.e., an attacker needs to already have domain credentials) for getting a server running the Print Spooler service to initiate an NTLMv2 authentication session (using its Machine Account credentials) with a server of the attackers choosing. Microsoft considered this issue to be “by design”, and essentially a feature of the protocol.
In 2021, researcher Giles Lionel (@topotam) made an elephant sized splash by releasing his PetitPotam tool – utilizing a similar vulnerability in MS-EFSRPC. The difference? In addition to finding several authenticated methods in MS-EFSRPC for coercion, Giles discovered two methods (CVE-2021-36943 AND CVE-2022-26925) for unauthenticated coercion. This meant an attacker without any credentials could force a vulnerable server to connect to the relay server. To make matters worse, Domain Controllers were vulnerable to the unauthenticated attack by default.
Researchers inspired by the work of Christensen and Lionel continued to dig into additional RPC protocols and discover additional authenticated coercion opportunities but none have come close to the impact of unauthenticated PetitPotam.
| Technique Alias | Protocol | Researcher | Authenticated | Unauthenticated |
| PrinterBug | MS-RPRN | Lee Christensen, et al. | Yes | No |
| PetitPotam | MS-EFSRPC | Giles Lionel | Yes | CVE-2021-36942 |
| ShadowCoerce | MS-FSRVP | Giles Lionel And Charlie Bromberg(@_nwodtuhs) | CVE-2022-30154 | No |
| DFSCoerce | MS-DFSNM | Filip Dragović (@Wh04m1001) | Yes | No |
| CheeseOunce | MS-EVEN | @evilash | Yes | No |
Brace For Impact – The NTLM Relay Attack Surface
Once the targeted machine (likely a Domain Controller) connects to the attacker’s malicious server, the attacker can now relay the authentication session to a vulnerable service — allowing the attacker to masquerade as the machine to said service. Possible vulnerable services include:
- Active Directory Certificate Services (ADCS) Web Endpoint.
- LDAP with Signing Disabled
- Can be utilized to perform an RBCD attack.
- Domain Joined machines with Kerberos Unconstrained Delegation (KUD)
- Attackers could either dump LSASS on the machine with KUD or modify DNS records in order to perform a “kerberos relay” attack
- SMB with Signing Disabled
- NOT typically useful in an NTLM coercion attack – as machine accounts rarely have access to valuable SMB file shares.
- Other business services that accept NTLMv1/2 authentication – such as Outlook EWS.
ADCS – Why Everyone is Focused On It
When PetitPotam first hit the scene in 2021, most of the mitigations published were focused on killing the relay opportunity to ADCS – not on blocking the coercion technique itself. Although this created some confusion in the community (when a researcher says “PetitPotam” are they talking about just the coercion technique or the entire attack path to Domain Compromise via ADCS?), it was for a good reason.
In 2021, Will Schroder (@harmj0y) and Lee Christensen of SpectreOps published their white paper on various privilege escalations using Active Directory Certificate Services (ADCS) – Microsoft’s Active Directory integrated PKI solution. One of the key findings, known as ESC8, was the various HTTP enrollment endpoints that administrators could enable for ADCS were susceptible to NTLM relay attacks. If an attacker could relay a Domain Administrator or Domain Controllers session to one of these endpoints, they could potentially obtain a PKI certificate for the User/Machine. Attackers could then utilize these certificates to log in and compromise the domain. PKI certificates are highly valuable credentials – as they are very persistent, providing access even if a compromised user reset their domain password.
The combination of PetitPotam’s unauthenticated coercion attack with an ESC8 vulnerable ADCS server meant an attacker could easily obtain a PKI certificate for a Domain Controller – enabling them to fully compromise the domain by performing a DCSync or RBCD attack.
Real World Example
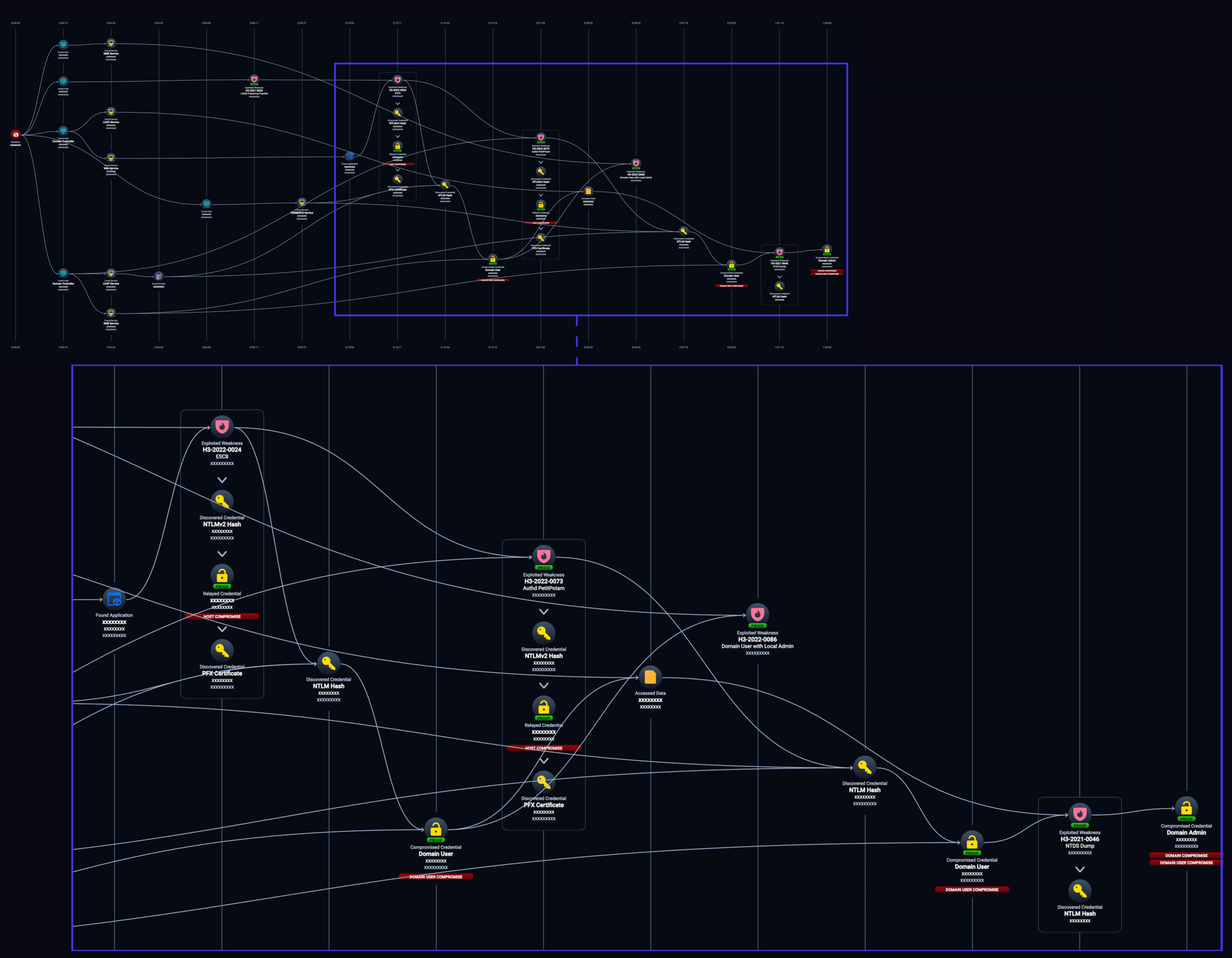
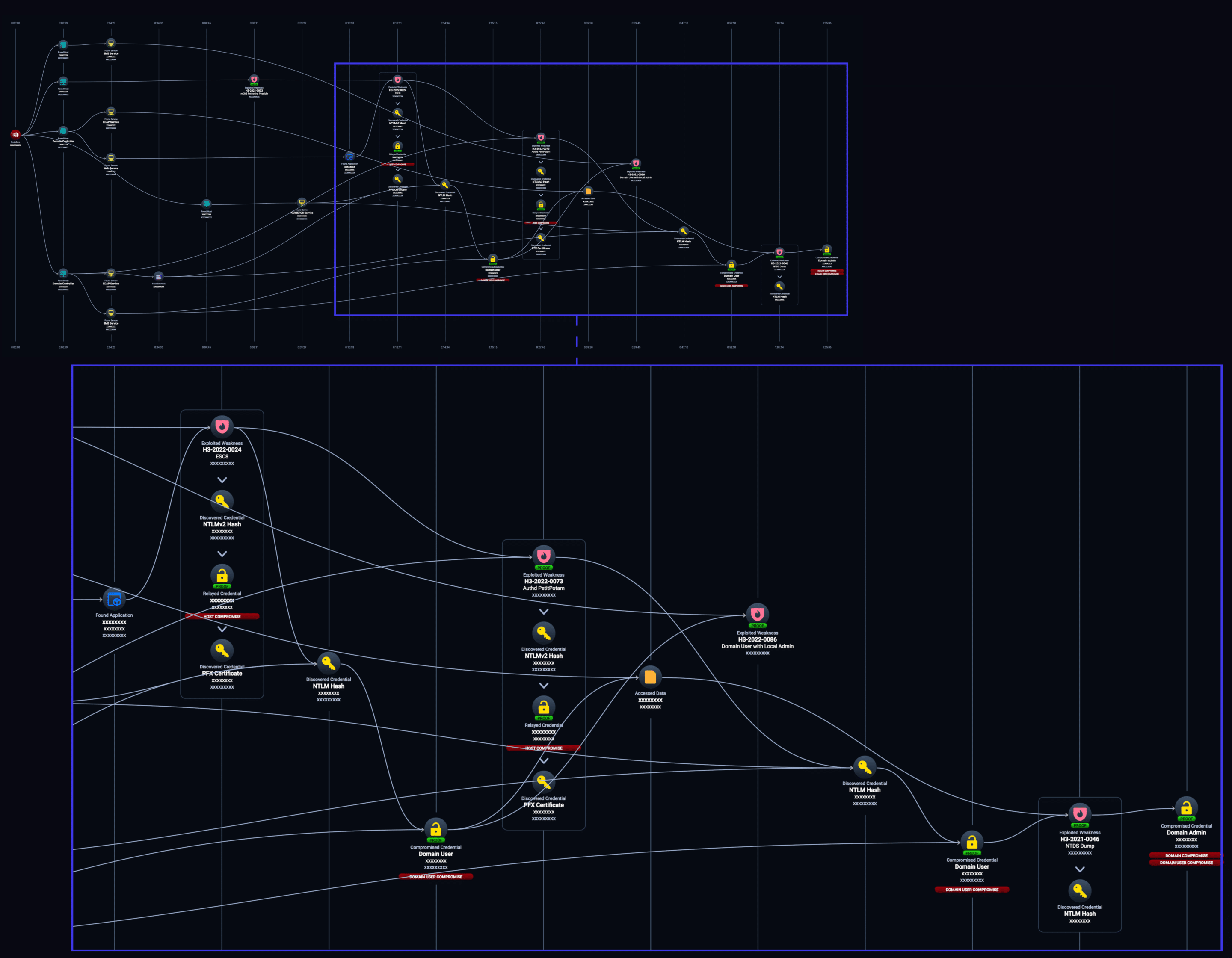
The above NodeZero attack graph is a great real-world example of the impact NTLM Coercion and ADCS ESC8 can have on an enterprise.
- NodeZero discovers a host is vulnerable to mDNS poisoning, a passive credential sourcing technique for an NTLM relay attack. NodeZero is able to poison said host, resulting in it starting an authentication session to its relay server with an unprivileged domain user credential.
- NodeZero is able to relay the user credential to ADCS and obtain a certificate for the user. NodeZero is then able to calculate the user’s NTLM hash from the certificate and utilize it to run an authenticated PetitPotam attack against the Domain Controller (DC).
- The DC connects to NodeZero’s relay server – which once again relays to ADCS to now obtain a certificate for the DC.
- NodeZero utilizes the PKI certificate for the DC to login and perform a DCSync attack – resulting in the discovery of a Domain Administrator’s credential.
- Domain Compromised.
Killing the Attack Chain
The severity of risk NTLM coercion techniques provide in an enterprise network depends on several key factors:
- Can an attacker obtain credentials?
- If not – are you patched against known unauthenticated attack methods?
- What services could an attacker perform a relay too? What value do they provide?
The questions above highlight several points where an attacker’s use of NTLM Coercion techniques can be minimized and mitigated in the attack chain. Here are a few recommendations:
- Patch! Keeping your high value servers up to date will ensure they remain safe against newly discovered unauthenticated attacks such as CVE-2021-36942 and CVE-2022-26925.
- Manage/minimize credential attack surface. All other coercion techniques require a domain user credential.
- This is easier said than done. H3 has highlighted just how typical it is for an attacker to obtain credentials, making this type of attack very difficult to defend against.
- Minimize the relay attack surface.
- Disabling ADCS’s vulnerable web endpoints
- Enable SMB Signing (Low Risk)
- Enable LDAP Signing
- Audit Machines with Kerberos Unconstrained Delegation
- Disable vulnerable services:
- PrinterBug – disable Print Spooler service if not required
- ShadowCoerce – disable File Server VSS Agent Service if not required.
- Filter vulnerable RPC protocols
- Disable NTLM authentication on vulnerable services or enable Extended Protection for Authentication (EPA).
- Some EDR solutions, such as Microsoft 365 Defender, provide identity security solutions that will block/identify coercion attacks.
Direct Mitigations
To mitigate unauthenticated NTLM coercion techniques, administrators should patch their vulnerable instances ASAP.
Some authenticated techniques can easily be disabled if not being utilized by the enterprise:
- MS-FSRVP (ShadowCoerce) – disable “File Server VSS Agent Service” on host
- MS-RPRN (PrinterBug) – disable the Print Spooler service on host
Others may require an RPC filter to block access to individual protocols if their use is not required. H3 has provided the RPC filters for the following:
- H3-2022-0073 – MS- EFSRPC (PetitPotam)
- H3-2023-0013 – MS-FSRVP (ShadowCoerce)
- H3-2023-0014 – MS-DFSNM (DFSCoerce)
- H3-2023-0015 – MS-EVEN (CheeseOunce)
- H3-2023-0016 – MS-RPRN (PrinterBug)
Key Takeaways
- NTLM coercion techniques (such as those utilized by the PetitPotam tool) focus on getting a high value source machine (e.g. a Domain Controller) to authenticate to an attacker-controlled relay server.
- The relay server can relay the authentication material to a myriad of vulnerable target services – providing the attacker access to said target service. Vulnerable Services include:
- ADCS Web Endpoint (ADCS ESC8)
- LDAP services with signing disabled
- Machines with Kerberos Unconstrained Delegation
- SMB services with signing disabled.
- PetitPotam != ADCS ESC8
- Defenders need to mitigate all possible paths that an attacker may utilize to gain additional access in a network if RPC filters are not feasible.
- SMB Signing Disabled is typically of LOW value for coerced credentials.
In our real-world example, NodeZero was able to compromise the domain in an hour and five minutes using a combination of Man-in-the-Middle techniques, to include using NTLM coercion to relay a Domain Controller’s credentials to an ADCS server. This example highlights the highest level of impact NTLM coercion can have in an environment, but it is only one of several different ways attackers can utilize the technique to gain their objectives.
Sign up for a free trial and quickly verify you’re not exploitable.
如有侵权请联系:admin#unsafe.sh