
2024-1-17 07:30:18 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:42 收藏

Executive Summary
On Jan. 10, 2024, Ivanti disclosed two new vulnerabilities in their Ivanti Connect Secure (ICS) and Ivanti Policy Secure gateways: CVE-2023-46805 and CVE-2024-21887. The first CVE is a High severity authentication bypass vulnerability, and the second CVE is a Critical severity command injection vulnerability. These vulnerabilities impact all supported versions of the gateways.
When chained together, exploiting these vulnerabilities allows attackers to run commands on the compromised system without the need for authentication.
We are sharing our observations of device exposure and possible related threat activity to aid in developing security measures as threat actors are actively exploiting these vulnerabilities.
Use of these two Ivanti products is widespread. Unit 42 observed 30,089 exposed instances of Connect Secure in 141 countries as of Jan. 9, 2024. We are also engaged in several incident response cases that are suspected to involve these vulnerabilities.
Ivanti plans to begin releasing patches addressing these vulnerabilities the week of Jan. 22, 2024. They plan to release patches in a staggered schedule, with the final patch being available during the week of Feb. 19, 2024. Until patches are available, Ivanti has provided a workaround.
We assess with moderate to high confidence that threat actors, likely at the nation-state level, will continue to target and exploit devices impacted by these vulnerabilities as initial access vectors into target environments for espionage purposes. We assess with moderate confidence that financially motivated, advanced and well-resourced cybercriminals will also attempt to compromise organizations through this vector.
Palo Alto Networks customers receive protections from and mitigations for CVE-2023-46805 and CVE-2024-21887 in the following ways:
- Cortex Xpanse customers can identify external-facing instances of impacted applications through the “Ivanti Connect Secure” and “Ivanti Policy Secure” attack surface rules.
- Next-Generation Firewall with the Advanced Threat Prevention security subscription can help block the associated web shell.
- Advanced URL Filtering and DNS Security categorize as malicious known domains associated with this activity.
- Cortex XDR and XSIAM help protect against post-exploitation activities using the multi-layer protection approach.
Ivanti also recommends customers perform a workaround until patches are made available.
The Unit 42 Incident Response team can also be engaged to help with a compromise or to provide a proactive assessment to lower your risk.
| Vulnerabilities Discussed | CVE-2023-46805, CVE-2024-21887 |
Table of Contents
Details of the Vulnerability
Current Scope of the Attack
Interim Guidance
Conclusion
Palo Alto Networks Product Protections for CVE-2023-46805 and CVE-2024-21887
Next-Generation Firewalls and Prisma Access With Advanced Threat Prevention
Cloud-Delivered Security Services for the Next-Generation Firewall
Cortex XDR and XSIAM
Prisma Cloud
Cortex Xpanse
Details of the Vulnerability
The first vulnerability (CVE-2023-46805) is an authentication bypass vulnerability in the web component of all supported versions of Ivanti Connect Secure and Ivanti Policy Secure (versions 9.x and 22.x). This vulnerability allows a remote attacker to access restricted resources by bypassing control checks.
The second vulnerability (CVE-2024-21887) is a command injection vulnerability in the web components of Ivanti Connect Secure and Ivanti Policy Secure (versions 9.x and 22.x). This vulnerability allows an authenticated administrator to send specially crafted requests and to execute arbitrary commands on the appliance.
Current Scope of the Attack
According to Ivanti, their products are used by over 40,000 companies around the world.
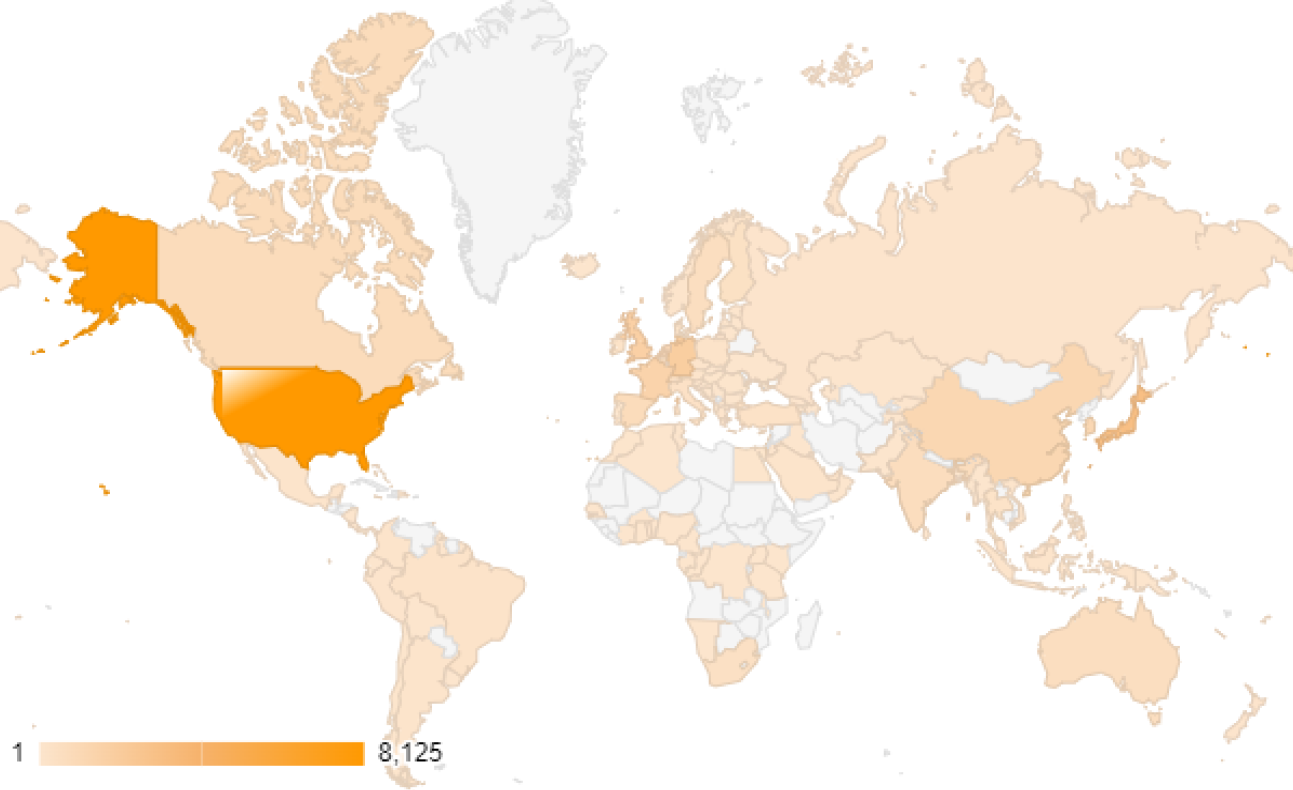
Unit 42 observed 30,089 exposed instances of Connect Secure in 141 countries as of Jan. 9, 2024. Figure 1 shows that the top 10 exposed countries account for nearly 70% of global exposure, per the observations of Connect Secure devices.
Volexity has reported that the attacker was able to use credentials they had dumped from the memory of the LSASS process to log into workstations and servers in the affected environment. Attackers were then observed exfiltrating the output of this activity.
Volexity also noted that the attacker was observed attempting to create a compressed archive of the system’s Active Directory database NTDS.dit file. Attackers have also been observed wiping log files on the affected devices.
Unit 42 is engaged in incident response cases that are suspected to be related to exploitation of these vulnerabilities. In these cases, we have observed the behavior Volexity has described.
Volexity and Mandiant have both highlighted compromised, out-of-support Cyberoam VPN appliances being used for command and control. Cortex Xpanse has a device fingerprinting rule in place to identify these out-of-support devices, and it has captured over 18,000 total distinct IPs associated with Cyberoam.
Interim Guidance
Ivanti has provided a workaround to be applied until they release patches. They have stated that they have seen evidence of attackers attempting to manipulate Ivanti’s internal integrity checker. As such, they are recommending that all customers run Ivanti’s external integrity checker, which has been updated with additional functionality to address this issue.
Conclusion
As there is no patch currently available, it’s important to follow the mitigation steps Ivanti recommends as the two new vulnerabilities are actively being exploited. We will keep this post updated as more information comes to light.
Palo Alto Networks has shared our findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Palo Alto Networks customers are better protected by our products, as listed below. We will update this threat brief as more relevant information becomes available.
Palo Alto Networks Product Protections for CVE-2023-46805 and CVE-2024-21887
Palo Alto Networks customers can leverage a variety of product protections and updates to identify and defend against this threat.
If you think you might have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Next-Generation Firewalls and Prisma Access With Advanced Threat Prevention
Next-Generation Firewall with the Advanced Threat Prevention security subscription can help block the associated webshell via the following Threat Prevention signature: 81872
Cloud-Delivered Security Services for the Next-Generation Firewall
Known domains associated with this malicious activity are categorized as malicious by Advanced URL Filtering and DNS Security.
Cortex XDR and XSIAM
Cortex XDR and XSIAM help protect against post-exploitation activities using the multi-layer protection approach.
Prisma Cloud
Prisma Cloud monitors Ivanti Cloud Secure products, which are not known to be vulnerable to either of these vulnerabilities at this time. Prisma Cloud's security research team will continue to monitor the situation and update Prisma Cloud detections should Ivanti Cloud Connect be found vulnerable to these threats.
Cortex Xpanse
Cortex Xpanse customers can identify external-facing instances of impacted applications through the “Ivanti Connect Secure” and “Ivanti Policy Secure” attack surface rules. Insecure detections of Ivanti Connect Secure are default enabled for all customers.
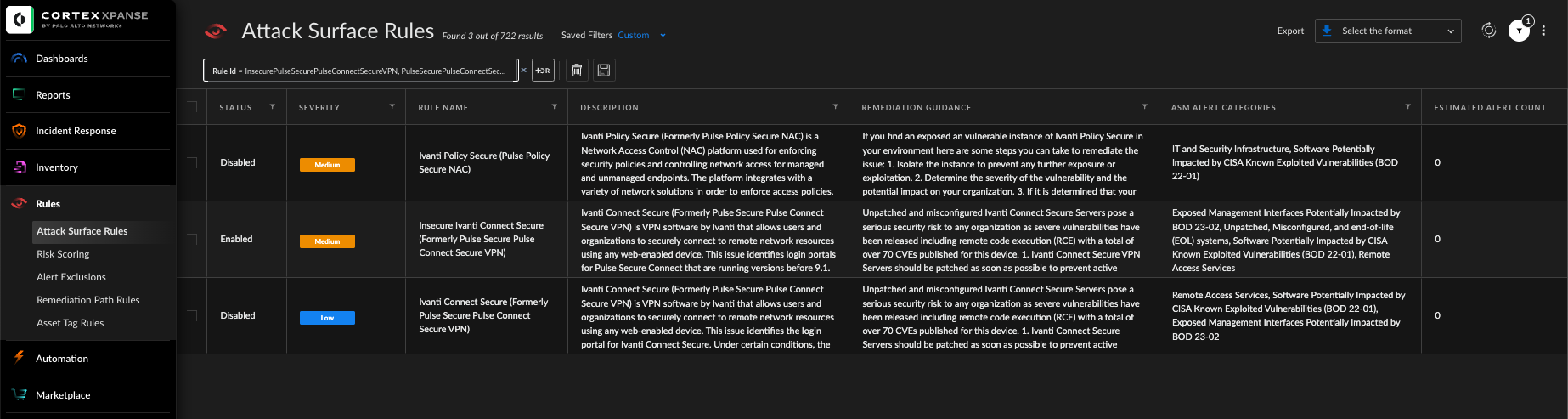
Within the Cortex Xpanse Threat Response Center, organizations can also find curated threat intel summaries, exploit consequences, previous exploit activity and links to other sources for additional information. This allows you to see how risk is distributed across your organization and build a remediation plan based on the guidance provided. Cortex Xpanse identifies service owners automatically, so organizations can easily assign a ticket to the right person.
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh