A Deep Dive into the Cosmic Universe of Information Safeguarding: An Exhaustive Examination of Distributed Data Security
As the virtual dominions continue to propagate at a phenomenal pace, the totality of data we generate daily scales new zeniths. We see ourselves increasingly relying on 'online hosted services' to govern this gigantic data deluge. This phrase, 'the geographically dispersed hosts', encompasses a wide spectrum of internet utilities such as data safeguarding, networking capabilities, software functionalities, and storage areas. As digital metamorphosis cuts across various sectors, there is an unmistakable requirement to sharpen our methods of fortifying our critical data within these vaporous online architectures.
To conceptualize 'the geographically dispersed hosts', picture a vast interconnected web of online hosts, fortified with cutting-edge applications that command network protocols in rolling out varied services. It is not just a storage setup; computing on geographically dispersed hosts offers an array of web-linked utilities.
<code class="language-python"># Python prototype code for interaction with online storage
import boto3
s3 = boto3.resource('s3')
for bucket in s3.buckets.all():
print(bucket.name)</code>
The mentioned piece illustrates the use of the Python boto3 library to forge a link with Amazon S3, a trailblazer in the realm of online storage. The primary function of this code is to fetch the identifiers of the storage compartments, better known as buckets, within Amazon S3.
In the context of Data Security on the geographically dispersed hosts, our goal is to augment the defenses of data handled by third-party online hosted service providers. While reducing the intricacies of conventional storage modalities, the geographically dispersed hosts do simplify processes, albeit exposing data to a host of susceptibilities such as data intrusions, unlawful access, and prospective data loss situations. Hence, the nucleus of our online data security strategy is to conceptualize and set in motion defensive measures that can abate these threats and guarantee the security of housed data.
Let's apprehend the discrepancies between the archaic localized data storage infrastructures and the nascent online storage methodologies:
| Traditional Locale-bound Storage | Innovative Network-bound Storage |
|---|---|
| Data is lodged in easily reachable hardware hosts. | Data resides in virtual hosts, granting access through web interactions. |
| Data control lies only with stakeholders. | Control exertion is shared with the network-bound service purveyors. |
| Safety hedges on physical and network security verifications. | Information protection is acquired via methods like ciphering, access control, and other preventative techniques. |
Equipped with an exhaustive comprehension of online data security, we encounter these pivotal elements:
-
Ciphering: A complex process of transmuting comprehensible data into ciphered figures to ward off unsanctioned access. This operation is employed on both stationary and transitioning data.
-
Access Control: A system that ensures confidential data is access-limited to those possessing the necessary clearance.
-
Replication and Restoration: The technique of cloning data to facilitate potential recuperation if the original data is tainted or misplaced.
-
Geo-Information Compliance: Adherence to legislations related to geographic placement and supervision of data, in sync with appropriate legal preconditions and norms.
To encapsulate, online data security is the elemental part of all tasks associated with computing on geographically dispersed hosts. It implies a mixture of varying methodologies and blueprints designed to preserve and defend the confidentiality and genuineness of the stored data. The swift strides made in the digital rebellion foreground the urgent need to put stringent online data security implementations in place.
Delving into the Cruciality of Enhancing Protective Measures for Information Preserved within Cloud Systems**
In the current era of digitization, information serves as the core fuel for business functions, forming the basis for insightful decisions and fostering consumer connections. As companies increasingly migrate towards virtual storage solutions, it becomes imperative to implement foolproof security strategies to ensure the integrity of data housed in cloud domains.
Securing a company's valuable digital holdings present in cloud formations necessitates the augmentation of data confidentiality, resilience, and recovery features. The strategic allocation of resources towards comprehensive and proactive security tactics can preempt unauthorized breaches, data anomalies, and accidental disclosure of vital details.
Allow me to delve deeper into the significance of steadfast security practices in handling data within cloud-focused platforms:
1. Enhancing Data Shielding:
The cardinal objective of security methods applied within cloud habitats is to ensure the safety of vital corporate information. Insufficient security provisions may expose critical data to malicious forces, triggering severe consequences such as financial losses, brand damage, and possible litigation.
For instance, here's a Python script demonstrating how encryption can be used to secure data storage:
<code class="language-python"> from cryptography.fernet import Fernet # Key Generation key = Fernet.generate_key() cipher_suite = Fernet(key) # Encrypting a confidential message cipher_text = cipher_suite.encrypt(b"Confidential information.") print(cipher_text)</code>
2. Adherence to Regulatory Standards:
Several sectors establish criteria mandating thorough monitoring of certain data types. Measures like HIPAA guide medical information, while PCI-DSS oversees finance sector data. Non-compliance with these rules can lead to hefty penalties. Reliable data shielding in cloud contexts enables companies to comply with these regulatory schemas.
3. Upholding Operational Flow:
Operational disruptions provoked by data anomalies can instigate chaos. Reliable data security practices in cloud infrastructures ensure prompt recovery and ensure smooth operational continuity despite potential threats. This steadfast continuity stems from meticulous data preservation and retrieval policies.
4. Maintaining Customer Confidence:
Customers entrust their significant data to businesses with the expectation of secure stewardship. Any breach of this faith can damage their trust and tarnish the company’s image. By deploying advanced data security methods in cloud storage, organizations can build and enhance user confidence.
We present a comparison highlighting the importance of thorough data protection in cloud landscapes:
| Consequences of Neglecting Cloud Data Security | Benefits of Rigorous Cloud Data Security |
|---|---|
| Heightened risk of data breaches | Increased assurance of data protection |
| Financial penalties due to non-compliance | Alignment with regulatory mandates |
| Disruptions in routine business operations | Swift recovery and operational continuity |
| Erosion of customer trust | Reinforcement of customer belief |
In conclusion, the responsibility of fortifying data within the cloud's domain has advanced from being a discretionary luxury to an indisputable necessity in the context of our data-focused universe. This reinforcement guarantees the protection of important business data, adherence to regulations, smooth operations, and safeguarding customer trust. Therefore, businesses must prioritize the comprehensive security of data in their cloud-centric arrangements for a more fortified future.
`
`
An Exhaustive Guide on Optimal Defence Tactics for Preserving Data Stored in the Cloud

Cocooning data within a cloud architecture calls for a meticulous, deliberate technique to neutralize plausible complications. These complexities may encompass curbing illegal access, curbing concealed data theft, or nullifying accidental data erasure. In this subsequent disquisition, we focus on vital facets of fortifying cloud data, supplying a pithy but far-reaching explanation of this critical element of combined cloud designs.
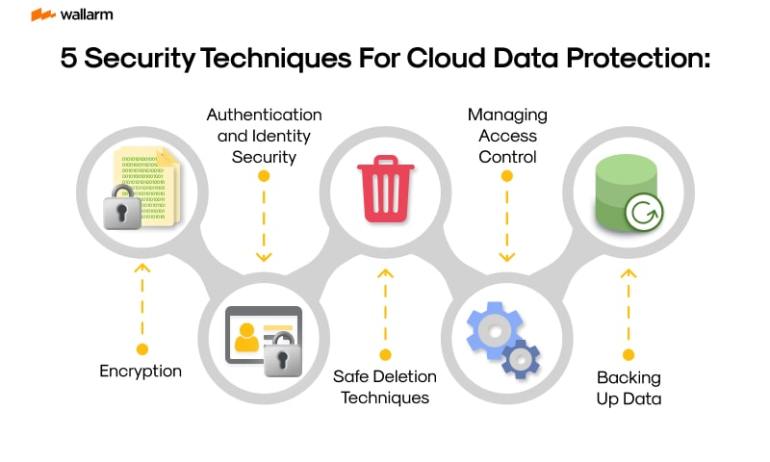
1. Ciphering - Data Cryptography: This essential component of data protection morphs simple text into a convoluted ciphered format to discourage unwelcome interference. Due to the inherent adaptability of cloud technology, you can apply encryption during data aggregation and during its transportation stage.
<code class="language-python">from cryptography.fernet import Fernet # Initiating Fernet tool and designing a cipher key key_crypto = Fernet.generate_key() cipher_collection = Fernet(key_crypto) # Translation of data data_in_simple = "confidential_data".encode() encrypted_data = cipher_collection.encrypt(data_in_simple)</code>
The Python code example above illustrates data conversion, utilizing the Fernet function within the cryptography module.
2. User Access Control: Frequently referred to as user permissions governance, it details the accessibility of data to each user and the extent of their authorized affiliations.
3. Data Replication and Recuperation: Regular replication of data offers a safety net against unforeseen injury or loss. The cloud provides a variable range of backup options, from local to global and intermingled solutions. It is crucial to formulate a speedy data recuperation strategy.
4. Geographical Data Reduplication: Familiar as Data Mirroring, it promotes the conservation of identical data sets in varied geographical points to assure maintained accessibility during network interruptions.
5. Cyber Defences: These digital fortifications, also known as cyber barriers, construct a division that segregates your custom cloud network from the shared one (for example, the Internet), regulating and scrutinizing all incoming and outgoing traffic as per set security codes.
6. Anomaly Recognition and Mitigation Plan (ARMP): ARMP main agenda is to keep track of network patterns for discrepancies and initiate alerts when these deviations are noticed. Advanced systems may also have the capacity to reconcile these disruptions.
7. Digital Protection Monitoring and Incident Response (DPMIR): As an upgraded version of SIEM, DPMIR solutions aggregate and examine security-oriented data coursing through the cloud structure to detect looming threats and neutralize them promptly and proficiently.
8. Verification of Legal Adherence: Within the sphere of cloud data safeguarding, adherence to data security norms and rules such as GDPR, HIPAA, and PCI DSS becomes crucial. It requires deep comprehension of, and concurrence with a variety of legally imposed requirements.
| Component | Description |
|---|---|
| Ciphering - Data Cryptography | Transmutes data into a code to restrain unauthorized acquisition |
| User Access Control | Orchestrates each user's precise authorization degrees |
| Data Replication and Recuperation | Enables regular data duplication and swift recovery methodologies |
| Geographical Data Reduplication | Guarantees identical data duplication across different geographical regions |
| Cyber Defences | Supervises network movements based on predetermined security standards |
| Anomaly Recognition and Mitigation Plan | Watches over network irregularities and triggers relevant corrective measures |
| Digital Protection Monitoring and Incident Response | Accumulates and evaluates data to recognize and tackle impending cyber menaces |
| Verification of Legal Adherence | Demands compliance with diverse data securement norms and policies |
Comprehending these components is critical in shaping a staunch strategy for data protection nested within the architecture of cloud systems. Each part plays a vital role in proliferating data security measures, resulting in an overarching security blueprint in conjunction with data lodged in cloud-based structures.
Charting Diverse Approaches for Enhanced Data Safeguarding in Cloud Systems
The sphere of guarding sensitive data stored on the cloud is a vast and dynamic landscape, teeming with innovative tactics tailored to bolster the defense of your confidential resources. This discourse focuses on a range of methodologies contrived for escalating the safety factor of data housed on cloud settings, diving into their multifaceted nature, and dissecting their unique merits and demerits.
1. Data Distortion
An essential approach in safeguarding data placed on the cloud is data distortion, a maneuver that transforms data into an unreadable format to thwart unwanted access. Only those possessing the right decryption cipher can decode the distorted data.
<code class="language-python">from cryptography.fernet import Fernet # Develop a Key and Activate a Fernet Model key = Fernet.generate_key() codex = Fernet(key) # Encrypt a classified text encrypted_text = codex.encrypt(b"Classified text. Illicit access is prohibited.") # Decrypt the concealed text to its original essence actual_format = codex.decrypt(encrypted_text)</code>
The Python code snapshot shown above illustrates the fundamental process of data distortion and reversal using the Fernet component of the cryptography package.
2. Data Duplication & Restoration
The tactic of duplicating and restoring data serves as a crucial protective layer in advancing cloud-based data security. Essentially, it involves creating replicas of your data for safe storage, thereby enabling quick retrieval in distressing scenarios like data loss or degradation.
3. Data Multiplicity
The concept of data multiplicity, creating manifold identical sets of data, involves generating several copies of your data dispersed across various locations. This approach guarantees the continuous availability of your data, even in the event of an outage in one of your chosen data centers.
4. Token Deployment
Tokenization, a practice which substitutes sensitive data with harmless stand-ins or tokens, ensures the safe confinement of actual data while routine operations interact only with tokens.
Data camouflaging, also known as data concealment, focuses on obscuring particular portions of data within a database. This technique safeguards critical data while permitting its use during testing and development stages.
6. Firewall Defence
Firewalls perform the role of a barrier between your data and potential threats. These digital protectors supervise and orchestrate network data transmission according to established security guidelines.

In summary, to assure a fallback for data residing in cloud systems, it's essential to employ a variety of techniques intended to maintain the confidentiality and integrity of your data. The choice of a suitable strategy should harmonize with your distinct needs and the nature of your data. Thus, gaining insights into the robustness and drawbacks of each tactic is vital for a well-informed decision regarding your cloud data defense blueprint.
Curtailing Mistakes in Cloud Data Safeguarding
Securing data in the cloud forms a pivotal part of an organization's strategy for managing information. There are, however, prevalent mistakes that might compromise your strategies to safeguard data in the cloud. Familiarizing with these flaws can guide you to circumvent them, guaranteeing your data remains risk-free and at your disposal when requisite.
1. Absence of an All-inclusive Strategy for Data Safety
A frequent mistake in protecting cloud data is the absence of an encompassing strategy for data safety. Several establishments merely shift their information to the cloud without giving thought to the discrete challenges posed by securing data in a cloud set-up.
<code class="language-python"># Instance of a misguided approach info = garner_data_from_local_storage() migrate_to_cloud(info)</code>
Reflecting on the precedent scenario, information is simply transitioned from local sources to cloud with utterly no regard for security or data safety, a commonplace error that could induce data violations and data loss incidents.
A comprehensive strategy for data protection ideally includes facets such as data coding, privileges management, data duplication and restoration, continuously scheduled safety checks and reviews.
2. Undervaluing the Significance of Encryption
Encrypting data holds crucial importance in the defense of data within the cloud. Yet, numerous firms neglect this imperative security control.
<code class="language-python"># Instance of a misguided approach info = garner_data_from_local_storage() migrate_to_cloud(info)</code>
In the precedent scenario, the data is shifted to the cloud devoid of any encoding or encryption. Consequently, if the data transfer is breached, the data's contents are readily comprehensible and can be inappropriately exploited by those without authorization.
Maintain that your data is encrypted both during data transfer (in transit) and when stored (at rest).
3. Lack of Interest in Managing Access
Managing who can access your data, or access control, proves significant in cloud data safety. Yet, numerous companies fail to institute robust access control mechanisms, making sensitive data accessible to unauthorized individuals.
<code class="language-python"># Instance of a misguided approach info = garner_data_from_local_storage() migrate_to_cloud(info, entrance='public')</code>
Examining the precedent case, data is migrated to the cloud with public admitted access, implying it's accessible to everyone. Such an exposure poses a grave security threat and is advised to be avoided.
Ascertain that only accredited individuals can access your cloud-held data.
4. Overlooking the Value of Data Replication and Recovery
Replicating data and ensuring its recovery constitutes an essential element of any data safety strategy. Nevertheless, several organizations disregard this element of cloud data defense, leaving them exposed to data loss.
<code class="language-python"># Instance of a misguided approach info = garner_data_from_local_storage() migrate_to_cloud(info)</code>
Reflecting on the precedent case, there's no provision for data redundancy or recovery. Should the data get corrupted or misplaced, the chances of recovery are nil.
Guarantee that there's a sound, robust strategy for data replication and restoration in place.
5. Disregarding the Need for Routine Safety Reviews
Consistent safety check-ups are instrumental in unearthing any potential vulnerabilities and validating the efficacy of your cloud data protection strategy. Nevertheless, numerous firms fall short in carrying out these reviews, making themselves susceptible to security violations.
<code class="language-python"># Instance of a misguided approach info = garner_data_from_local_storage() migrate_to_cloud(info)</code>
Reflecting on the precedent instance, there's no arrangement for routine safety audits. This could result in potential security loopholes being overlooked, grow the risk of a data violation.
Be certain to regularly conduct safety audits to pinpoint and tackle any lurking vulnerabilities.
Concluding, circumventing these prevalent flaws can substantially boost your efforts in providing protection to your cloud-stored data. Make sure you always have an all-embracing data safety strategy in order, accounting for elements such as encryption, access control, data replication, restoration as well as consistent safety audits.
Trailblazing Innovations Reshaping the World of Securing Cloud Data
We are all being part of the accelerating digital age, where the contours of cloud data safety are persistently redesigned, morphed and updated. This installment is aimed to highlight the landmark innovations that are currently redefining the landscape of securing cloud data. These progressive changes not only influence the way organizations safeguard their data but also reshape professional guidelines and practises.
1. Increasing Preference for Diverse Cloud Strategies:
The concept of a diverse cloud strategy involves utilizing numerous cloud computing services from a variety of providers. This concept is currently gaining traction as it offers businesses the advantage to evade the dominance of a single service provider, enhance adaptability and manage expenses effectively.
<code class="language-python"># Python code showcasing diverse cloud strategy utilizing AWS and Google Cloud
import boto3
from google.cloud import storage
# AWS S3
s3 = boto3.resource('s3')
for bucket in s3.buckets.all():
print(bucket.name)
# Google Cloud Storage
storage_client = storage.Client()
buckets = list(storage_client.list_buckets())
print(buckets)</code>
2. Expanding Role of AI and Machine Learning:
The influence of Artificial Intelligence (AI) and Machine Learning (ML) in securing cloud data is extending. Adopting these technologies results in detecting inconsistencies and possible threats, thereby endorsing pro-active safety initiatives.
<code class="language-python"># Implementation of Scikit-learn library in Python for anomaly detection from sklearn.ensemble import IsolationForest clf = IsolationForest(contamination=0.01) clf.fit(data) pred = clf.predict(data) anomalies = data[pred == -1]</code>
3. Broad Utilization of Cryptographic Methods and Tokenization:
In the domain of securing cloud data, we observe an increased usage of cryptographic methods and tokenization. By an encrypted transformation of data, these methods significantly contribute towards enhancing the safeguard of valuable data.
| Method | Function |
|---|---|
| Cryptography | Converts data into a code, readable only with a specific key. |
| Tokenization | Substitutes sensitive data with unhazardous counterparts, termed as tokens. |
4. Emphasis on No Trust Safety:
The no trust safety model is built on the "authenticate first, trust later" philosophy. This model is receiving attention for it significantly lowers the chances of data infringements.
<code class="language-python"># Illustrating No Trust Safety using JWT Tokens in Python
import jwt
token = jwt.encode({"user": "test", "role": "admin"}, "secret", algorithm="HS256")
decoded = jwt.decode(token, "secret", algorithms="HS256")
print(decoded)</code>
5. Growth in Privacy Laws:
The advent of laws like GDPR and CCPA pushes organizations to reinforce their data safety measures. This trend stimulates a growing demand for innovative solutions in the realm of securing cloud data.
6. Progressing Towards Server-less Structures:
The focus is shifting towards server-less structures as they free developers from the responsibility of server management and empower them to concentrate on application semantics. This shift impacts the methods used to secure data in the cloud.
<code class="language-python"># An example of AWS Lambda server-less function in Python
import json
def lambda_handler(event, context):
# TODO implement
return {
'statusCode': 200,
'body': json.dumps('Hello from Lambda!')
}</code>
7. Emergence of Quantum Computation:
Quantum Computation poses a dual nature with respect to securing cloud data by presenting both probable hazards and prospects. While it could potentially threaten conventional encryption methods, it also offers a route to novel and more reliable algorithms.
To sum up, the world of securing cloud data is dynamic and constantly evolving. By keeping pace with the changing tides, organizations can guarantee that their tactics for securing cloud data are robust, proficient, and equipped for future advancements.
`
`
Comprehensive Survey of Mechanisms to Secure Cloud-Stored Data: An Innovative Approach
Establishing a secure data governance framework is crucial, especially when data is being stored in a cloud environment. This chapter offers an explorative study of select participants who have effectively increased their cloud data defense mechanisms.
Case Study One: Safeguarding Techniques Implemented by Dropbox
Dropbox, a popular name in cloud storage, intrinsically combines a variety of secure practices to defend against data breaches. Instead of leaving unattended data unprotected, Dropbox employs algorithms like the AES-256. Moreover, moving data or data being exchanged is enveloped with cryptographic shields, like SSL/TLS.
<code class="language-python"># Illustrative example of AES-256 encryption code from Crypto.Cipher import AES key = b'Sixteen byte key' encryption_tool = AES.new(key, AES.MODE_ECB) encrypted_message = encryption_tool.encrypt(b'Just a Test.') print(encrypted_message)</code>
Dropbox fortifies its security measures by incorporating biometric validation as well. Consequently, even if a scheming actor manages to decipher a user's password, the intruder would also need access to the user's mobile device to breach their Dropbox account.
Case Study Two: Data Security Approaches in Amazon Web Services (AWS)
Being a front-runner in cloud-based solutions, AWS offers a myriad of services focusing on data security. This includes structural facets like Amazon S3 for data housing, AWS Key Management Service for encryption keys administration, and AWS Identity and Access Management to manage who has access.
To maintain the sanctity of idle data, AWS has ingrained preservation procedures that include server-governed encryption with S3-prescribed keys (SSE-S3), AWS Key Management Service (SSE-KMS), and user-generated keys (SSE-C). For data in-transit, AWS employs SSL/TLS.
<code class="language-python"># Possible example showing server-concentrated encryption in AWS S3. import boto3 s3 = boto3.client('s3') s3.put_object(Bucket='original_bucket', Key='new_key', Body='dummy_text', ServerSideEncryption='AES256')</code>
Case Study Three: Strengthening Data Security in Google Cloud Platform (GCP)
GCP implements a variety of mechanisms to secure user data. This involves protecting both stationary and moving data with encryption, deploying impervious network defenses, and conducting thorough examination for imminent security risks.
By default, GCP shields user's inactive data using individual or multiple encryption keys. The practice for securing data in transit involves GCP utilizing SSL/TLS.
<code class="language-python"># Hypothetical code snippet to enable automatic encryption for GCP storage bucket. from google.cloud import storage cloud_client = storage.Client() bucket = cloud_client.get_bucket('distinct_bucket') bucket.default_kms_key_name = 'projects/example_project/locations/project_place/keyRings/unique_keyring/cryptoKeys/example_key' bucket.patch()</code>
Comparative Analysis: Security Procedures among Dropbox, AWS, and GCP
| Cloud Provider | Dormant Data Encryption | Moving Data Encryption | Access Control Monitoring |
|---|---|---|---|
| Dropbox | AES-256 | SSL/TLS | Biometric validation |
| AWS | SSE-S3, SSE-KMS, SSE-C | SSL/TLS | AWS IAM |
| GCP | Automatic Encryption | SSL/TLS | GCP IAM |
The case studies underscore that a robust fortress for cloud-stored data should involve a blend of encryption mechanisms, tight control over accessibility, and continuous inspections for impending threats. Although each cloud service provider employs a distinct blend, the fundamental notion remains the same: ensure protection for both dormant and moving data, control access rights, and proactively scan for potential security breaches.
如有侵权请联系:admin#unsafe.sh