2024-1-23 13:57:19 Author: securityboulevard.com(查看原文) 阅读量:7 收藏
Data breach incidents have increased since post covid. The increase in work-from-home for employees has led to multiple cyber attacks, data breaches, and financial fraud. Information confidentiality is compromised by security incidents. A significant breach is observed in consumer data encryption during a ransomware attack. Another obvious sign of a security breach is the theft of hard drives, thumb drives, or even paper documents that physically contain important information. The illegal access, disclosure, or compromise of personal data is the fundamental component of a records breach.
This blog is about a recent data breach on a famous Internet Service Provider and how millions of customer’s data got leaked. We’ll also discuss our internal research on data breaches, providing insights that any industry can leverage to assess its security measures.
What Happened in Hathway?
In December 2023 multiple sources revealed that Hathway, an Indian Internet Service Provider (ISP) had a vulnerability in their PHP Laravel application that exposed their customer’s Personal Identity Information. According to a threat actor, the vulnerability enabled attackers to retrieve any customer’s personal information, resulting in extensive breaches.
How Did the Incident Happen?
According to the threat actor, there was a vulnerability on the target Laravel application that allowed a malicious actor to access server-internal data. The threat actor did not reveal what was exactly vulnerable on that application. By searching on exploit-db we found there was some vulnerability allowing remote code execution.
What Data was Compromised?
The leaked data comprises Aadhaar cards, phone numbers, passports, and other critical details, all exposed in the recent cyberattack. Attacker created a Tor site for individuals to access leaked data by entering their email or phone number. However, Hathway has not confirmed nor denied these allegations.
How These Leaked Data Can Be Used
Hathway’s data breach exposed personal information (PII) including Aadhar, Passport, phone numbers, and home addresses. Aadhaar cards enable online account registration, enabling fraudsters to impersonate and conduct scams as the account holder. Cyber attackers exploited a police ID to impersonate a Mumbai City official, falsely alleging an FIR and coercing people for money.
Source:mid-day.com
Could This Attack Be Prevented?
Yes, the prevention of attack was possible. Data breaches often occur when organizations neglect guidelines, disregard compliance, and fail to conduct regular security audits. We at Kratikal have shared many guidelines, resources, and best approaches to preventing these attacks.
How Can Cyber Attacks Be Prevented?
We have created an in-depth post on how data breaches happen. Explore the topic where we have covered all potential attack surfaces for unauthorized access to your organization. We have discussed all about initial access techniques used by malicious actors to breach your network.
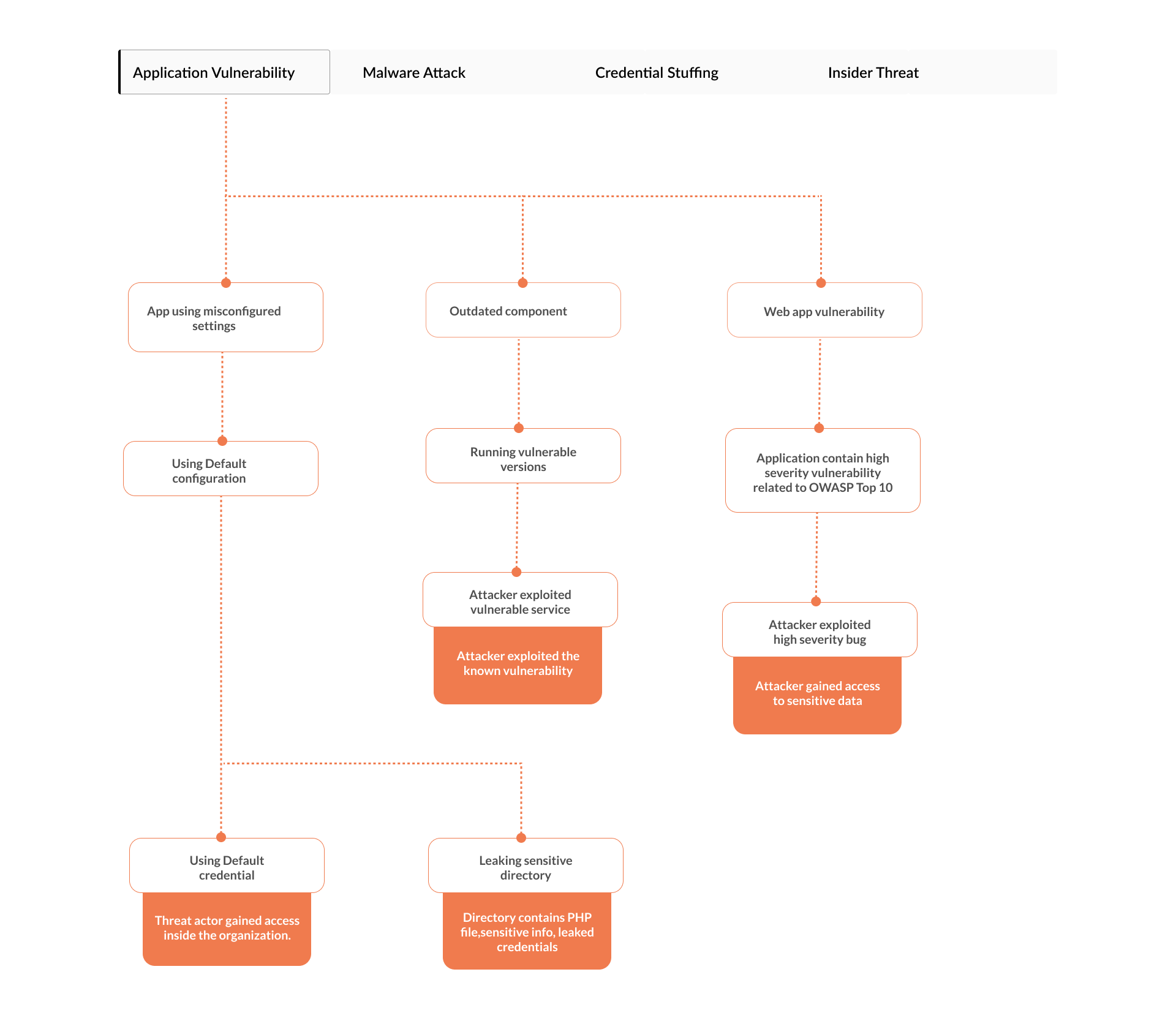
To check your organization’s cybersecurity maturity we have also created a mind map.
The mind map is a flow chart that you can use to track types of cyber attacks and how they could happen to any organization.
Future of Cyber Attacks
Recent breaches have shown a rapid increase in attacks, whether it is on target application vulnerabilities, sensitive data leaks, or misconfiguration. The increase in AI tools makes it easier for attackers to gain unauthorized access, exploit security loopholes, and breach assets.
The screenshot reveals an attacker effortlessly scanning the LLM chatbot, obtaining instant results without the need for setting up, downloading, or running tools on their own system. Cloud-based operations ensure improved speed and accuracy. Organizations adapt to smarter attackers with robust compliance and regular security audits on networks and infrastructure.
Conclusion
Hathway’s PHP Laravel app vulnerability emphasizes the need for regular security audits and compliance. The severity of the compromise, with leaked Aadhaar cards and personal information, emphasizes the potential risks for online impersonations. To defend against violations, focus on preventive measures like maintaining compliance and conducting routine safety audits. In combatting AI-driven cyber threats, organizations need a proactive and adaptable cybersecurity strategy to stay ahead of future trends. To counter emerging threats, organizations must consistently improve cybersecurity maturity with strong compliance models and extensive network audits.
Kratikal, an auditor empanelled by CERT-In, plays a crucial role in elevating security standards. We have prevented such breaches in the past. Leveraging unparalleled expertise, we offer comprehensive analysis and strong defense mechanisms to counter the persistent threat of cyberattacks. Partnering with Kratikal enables proactive identification and resolution of security vulnerabilities, hamper the efforts of malicious hackers seeking to exploit such flaws.
Ref: https://www.hackread.com/indian-isp-hathway-data-breach-user-data-kyc-leak/
The post Data Breach Strikes Hathway: 41.5M Data Exposed appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Shikha Dhingra. Read the original post at: https://kratikal.com/blog/data-breach-strikes-hathway-41-5m-data-exposed/
如有侵权请联系:admin#unsafe.sh