2024-1-23 20:21:12 Author: lab.wallarm.com(查看原文) 阅读量:21 收藏
Diving into the Enigma of TCP Resets Executed by Client and Server
The Base Communication Protocol (BCP), understoond as the Transmission Control Protocol (TCP) equivalent, plays a key role in the protocol unit of the internet. Its primary task entails laying a groundwork for communication between two digital entities over the internet, and ensuring the sequenced and error-free delivery of data packages. However, unforeseen circumstances might necessitate the abrupt cessation of a BCP connection. This is precisely where BCP Resets, also known as BCP-RST-FROM-Client, gain significance.
BCP Resets, in simpler terms, are a procedural function designed to fetch a sudden end to a BCP connection. They are initiated by a client or server when they wish to conclude the connection without following the conventional termination protocol. This could occur due to multitude of reasons, like the arrival of a package that doesn't relate to an existing connection, or the receipt of a package with an erroneous sequence value.
The intricacy of BCP Resets comes from the fact that both the client and server can execute them. Hence, to thoroughly comprehend BCP Resets, it is needed to delve deep into both facets - client-side and server-side - of a BCP connection.
Let's delve into a basic instance of a interaction between a client and a server to get a clearer picture. In a regular interaction, the client forwards a request to server which is processed and answered by the server. Say a situation arises where the server is unable to process a received package, it may then initiate a BCP Reset to the client. Likewise, the client might send a BCP Reset to the server should it receive a package it is unable to process.
<code class="language-python"># Client-end code
import socket
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect(("localhost", 12345))
# Forward request
s.sendall(b"Greetings, Server!")
# Await result
info = s.recv(1024)
# If result not as expected, trigger BCP Reset
if info != b"Greetings, Client!":
s.sendall(b"RST")
s.close()</code>
<code class="language-python"># Server-end code
import socket
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.bind(("localhost", 12345))
s.listen(1)
conn, addr = s.accept()
# Await request
info = conn.recv(1024)
# If result not as expected, trigger BCP Reset
if info != b"Greetings, Server!":
conn.sendall(b"RST")
# If not, respond
else:
conn.sendall(b"Greetings, Client!")
conn.close()</code>
In the above display of codes, a BCP Reset is initiated by both, client and server, if the received data doesn't match the expected data. Though this is a simplified scenario, it does shed light on the fundamental concept of BCP Resets.
What further adds to the intricacy of BCP Resets is the differential consequence based on their initiation source, be it a client or a server. For example, a BCP Reset activated by a client may result in loss of pending data on the server while the reverse may cause the client to lose data that is yet to be acknowledged.
| Reset Origin | Consequence |
|---|---|
| Client | Server potentially loses pending data |
| Server | Client may lose data yet to be acknowledged |
Additionally, BCP Resets can be provoked by a host of factors ranging from network traffic overload, defective network devices, and even spiteful attacks. Therefore, mastering and administrating BCP Resets entails a comprehensive insight into both the technicalities of BCP connections and the broader aspects of network surroundings.
In summation, BCP Resets supervised by Client and Server, or BCP-RST-FROM-Client, serve as a complex yet pivotal element of BCP connections. They function as a mechanism for bluntly ending a connection. The complexity arises from their dual-source, differential impacts based on origin, and vulnerability to a host of factors. Grasping this complexity is a stepping stone to effectively handling and troubleshooting BCP connections.
Unraveling the Enigma of TCP-RST-FROM-Client: An In-Depth Dissection
As we traverse the challenging landscape of computer networking, we often encounter perplexing concepts begging for interpretation. One such puzzle is the TCP Resets initiated by the Client, formally denoted as TCP-RST-FROM-Client. This chapter seeks to demystify this tangled topic, clarifying its practical applications.
Working within the confinements of the Transmission Control Protocol (TCP), TCP-RST-FROM-Client is a mechanism typically employed to expedite closing of connections. Simply put, it represents a signal fired from the client towards the server, distinctly conveying client's ambition to abruptly cease the current connection, bypassing the usual shutdown procedures.
Pouring some light on this subject, let's take an up-close look at the foundation of the TCP Reset packet. Essentially, a TCP Reset packet is a petite data unit carrying an exceptional flag known as the RST (Reset) flag. This flag is set at '1' in a TCP Reset packet. Below is a vivid exemplification of a TCP Reset packet:
<code>TCP Header: Source Port: 80 Destination Port: 12345 Sequence Number: 123456 Acknowledgment Number: 0 Data Offset: 5 Reserved: 000 Flags: RST (1) Window: 0 Checksum: 1234 Urgent Pointer: 0</code>
In this packet, the 'Flags' segment houses the RST flag, marked as '1', denoting it as a TCP Reset packet. 'Source Port' and 'Destination Port' entries designate the connection's terminus points, and the 'Sequence Number' component plays a pivotal role in the tactical placement of the packets.
Let's contrast a regular TCP packet with a TCP Reset packet:
| Typical TCP Packet | TCP Reset Packet |
|---|---|
| Flags: ACK (1) | Flags: RST (1) |
| Window: >0 | Window: 0 |
| Acknowledgment Number: >0 | Acknowledgment Number: 0 |
The table highlights the significant differences in 'Flags', 'Window', and 'Acknowledgment Number' sections. In a TCP Reset packet, the RST flag is active, the Window is empty, and the Acknowledgment Number is zero.
The TCP-RST-FROM-Client approach offers impressive effectiveness when it comes to preserving the reliability and swiftness of a network. It permits a client to swiftly discontinue an obsolete connection, thus paving the way for potential networking sessions. However, reckless usage can provoke unpredictability in connections and data loss.
Here are some situations where a client may issue a TCP Reset:
- The client obtains a data packet meant for a connection that already been terminated.
- The client spots a packet with an erroneous sequence number.
- The client feels compelled to forcefully terminate a connection due to glitches or latencies.
In summing up, the TCP-RST-FROM-Client acts as a potent instrument within the TCP protocol, facilitating prompt and smooth cessation of connections. Nevertheless, it is vital to handle it with care to sidestep potential predicaments. In the forthcoming chapter, we’ll explore the journey of TCP Resets from the client to the server.
`
`
Unraveling TCP Resets: A Journey from User to Mainframe

The Internet protocol suite fundamentally contains the Transmission Control Protocol (TCP). With its key role, it ensures accurate, sequential, and scrutinized transmission of byte sequences among apps activated on devices interacting over an IP network. Part of this crucial protocol is the TCP Resets, otherwise known as TCP-RST-FROM-User.
This chapter aims to provide a detailed explanation of the functioning of TCP Resets, from the user to the mainframe, enriched with case examples, illustrative tables, and itemized data.
1. Digging into TCP Resets
TCP Resets are engineered to abruptly wind up an active TCP link. They usually come into play when an unexpected packet arrives or in reaction to distinct error scenarios.
A TCP Reset packet is essentially one where the RST bit is enabled in the TCP header. On detecting this, the target end of the TCP link should activate closure of the connection promptly, disregarding any inbound data undelivered to the app, if any.
2. Tracing TCP Reset: User to Mainframe
Consider a general scenario where a user shoots a TCP Reset towards a mainframe.
a. The user kick-starts a TCP link with the mainframe.
b. The mainframe gives a nod to the link.
c. Data transmission is initiated from the user towards the mainframe.
d. The mainframe confirms the receipt of data.
e. The user stumbles upon an error or an unforeseen packet, prompting termination of the connection.
f. The user dispatches a TCP Reset towards the mainframe.
g. On receipt of the TCP Reset, the mainframe breaks the link instantaneously, discarding any residual undelivered data.
3. Sample Code: Executing a TCP Reset
Here's an elementary Python script illustrating a user transmitting a TCP Reset to a mainframe:
<code class="language-python">import socket
# Initiate a TCP/IP socket
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
# Secure the socket to the mainframe's port
mainframe_address = ('localhost', 10000)
sock.connect(mainframe_address)
try:
# Transfer data
info = 'This is the info.'
sock.sendall(info.encode('utf-8'))
# Transmit TCP Reset
sock.setsockopt(socket.SOL_SOCKET, socket.SO_LINGER, struct.pack('ii', 1, 0))
finally:
sock.close()</code>
Here, the SO_LINGER option regulates the steps taken when close() is executed on a socket with unsent data in queue. When the linger structure's l_onoff member is set to non-zero, it establishes a holdover period (seconds) for the socket in the close() call to facilitate transmission of queued data. Setting it to zero commands a TCP Reset dispatch.
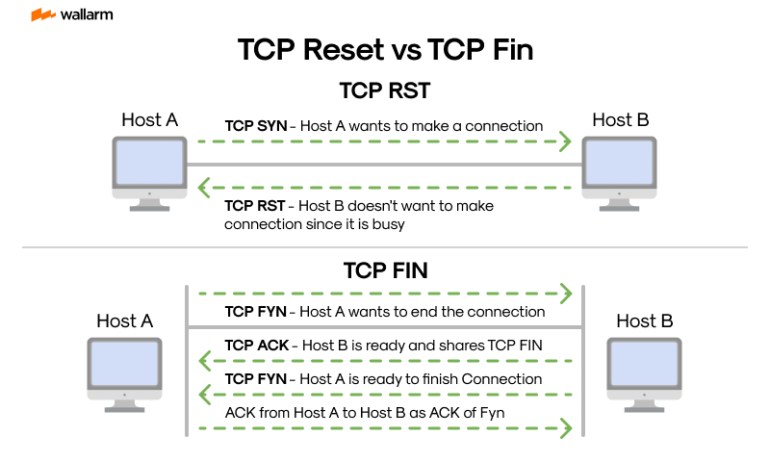
4. Tabulated Differences: TCP Reset vs. TCP Fin

| TCP Reset | TCP Fin |
|---|---|
| Abolishes a TCP link suddenly | Shutters a TCP link smoothly |
| Dismisses unsent data | Ensures complete data delivery before closure |
| Dispatchable at any moment | Only dispatched with no more data to transmit |
| Prompt closure of the link | Two-way handshake permitted before termination |
5. Enumeration: Instances Triggering a TCP Reset
Here's why a user may need to route a TCP Reset to a mainframe:
- Unexpected packet receipt.
- Application encounters an anomaly.
- The need for a forceful termination of the connection.
- Receipt of a packet over a perceived closed link.
To sum up, comprehension of user-to-mainframe TCP Reset operations is essential for network administrators, developers, and all those involved in TCP/IP networking. By grasping the mechanism of a TCP Reset, you can effectively solve network issues and ensure seamless functioning of your apps.
Practical Tips to Manage TCP Resets between Client and Server
Managing TCP Resets between a client and a server can be a daunting task, especially if you're not familiar with the intricacies of the TCP/IP protocol. However, with a few practical tips and a bit of patience, you can effectively manage these resets and ensure a smooth communication process.
1. Understanding TCP Resets
Before you can manage TCP Resets, you need to understand what they are and why they occur. A TCP Reset (RST) is a type of TCP/IP packet that is sent from one device to another to terminate an existing connection. It's essentially a way for a device to say, "I'm not communicating with you anymore."
TCP Resets can occur for a variety of reasons, such as when a device is overloaded with traffic, when there's a problem with the network connection, or when a device is shutting down.
2. Monitoring Network Traffic
One of the best ways to manage TCP Resets is to monitor your network traffic. This can be done using various network monitoring tools, such as Wireshark or tcpdump. These tools can help you identify any unusual patterns or spikes in TCP Resets, which could indicate a problem.
Here's a simple command you can use with tcpdump to monitor TCP Resets:
<code class="language-bash">tcpdump 'tcp[tcpflags] & tcp-rst != 0'</code>
This command will display all TCP packets with the RST flag set.
3. Analyzing TCP Resets
Once you've identified a spike in TCP Resets, the next step is to analyze them. This involves looking at the source and destination IP addresses, the TCP port numbers, and the sequence and acknowledgment numbers.
For example, if you notice that a large number of TCP Resets are coming from a specific IP address, this could indicate that the device at that address is experiencing problems.
4. Addressing the Cause of TCP Resets
After analyzing the TCP Resets, you should have a better idea of what's causing them. The next step is to address this cause.
For example, if the Resets are due to network congestion, you might need to increase your bandwidth or implement quality of service (QoS) measures. If the Resets are due to a specific device, you might need to troubleshoot that device or replace it.
5. Preventing Future TCP Resets
Finally, it's important to take steps to prevent future TCP Resets. This could involve regularly monitoring your network traffic, keeping your network devices up to date, and implementing robust security measures.
In conclusion, managing TCP Resets between a client and a server involves understanding what they are, monitoring your network traffic, analyzing the Resets, addressing their cause, and taking steps to prevent future Resets. With these practical tips, you can ensure a smooth and efficient communication process.
Dissecting the Influence of TCP Resets Originating from the Client and Server
An essential tool in the Internet Protocol Suite is the Transmission Control Protocol (TCP). Its functionalities include forming dependable connections among network devices, promising data packets are sent in the correct sequence, and controlling network congestion. A primary procedure that TCP mobilizes to control these communications is the TCP reset (RST) instruction. It's a command that is utilized to promptly cease a TCP connection and can be dispatched from the client or the server. In this discourse, we will understand the influence of TCP Resets from both the client and server, often referred to as TCP-RST-FROM-Client.
Grasping the Influence of TCP Resets
TCP resets can markedly affect the efficiency and dependability of a network. On transmitting a TCP reset, it promptly terminates the TCP link, leading to lost in-transit data. This can cause an array of problems, such as:
1. Data Depletion: One of the main consequences of a TCP reset is data depletion. This is specifically destructive to applications that depend on a constant data flow, like online gaming or video streaming.
2. Connection Unpredictability: TCP resets can trigger connection unpredictability too. If TCP resets are dispatched frequently, it can result in continuous connection interruptions, resulting in a substandard user experience.
3. Surged Network Load: Whenever a TCP reset is dispatched, it mandates the client and server to restore the TCP connection. This raises network load, possibly leading to congestion and reduced functionality.
Scrutinizing TCP Resets Originating from the Client
TCP resets that initiate from the client are generally due to a problem with the client device. Causes could be a software glitch, hardware malfunction, or even a malicious attack. For instance, a client device might transmit a TCP reset if it obtains an unexpected packet, or if it spots an irregularity in the TCP sequence numbers.
Let's examine a code snippet that demonstrates how a client might transmit a TCP reset:
<code class="language-python">import socket # Construct a TCP/IP socket sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM) # Connecting the socket to the server server_address = ('localhost', 10000) sock.connect(server_address) # Data transmission message = 'This is the message.' sock.sendall(message) # Dispatching a TCP reset sock.setsockopt(socket.SOL_SOCKET, socket.SO_LINGER, struct.pack('ii', 1, 0)) sock.close()</code>
In this scenario, the client constructs a TCP link with the server, transmits data, and abruptly ceases the connection by sending a TCP reset.
Scrutinizing TCP Resets Originating from the Server
The server originating TCP resets can significantly impact network functionality too. If the server dispatches a TCP reset, it usually occurs as it cannot handle the current load or has identified an error in the TCP link.
Here's a basic code snippet indicating how a server might dispatch a TCP reset:
<code class="language-python">import socket
# Setting up a TCP/IP socket
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
# Bind the socket to a specific port
server_address = ('localhost', 10000)
sock.bind(server_address)
# Listening for incoming links
sock.listen(1)
while True:
# Waiting for a connection
connection, client_address = sock.accept()
# Receiving data
data = connection.recv(16)
# If received data doesn't match expected data, dispatch a TCP reset
if data != 'Expected data':
connection.setsockopt(socket.SOL_SOCKET, socket.SO_LINGER, struct.pack('ii', 1, 0))
connection.close()</code>
In this scenario, the server waits for incoming TCP links, retrieves data from the client, and if the data mismatches its expectations, it dispatches a TCP reset to instantly terminate the connection.
In summation, both client and server-originating TCP resets can remarkably impact network functionality and dependability. Grasping the roots of these resets and dealing with them is essential for sustaining a secure and productive network.
`
`
Addressing TCP Resets between Client and Server: A Comprehensive Problem-Solving Guide
TCP Resets, an intricate issue often denoted as TCP-RST-FROM-Client, can pose quite a formidable challenge. Nevertheless, equipped with an in-depth cognition of the procedure along with a methodical troubleshooting pathway, managing this intricate issue becomes plausible. The ensuing portion of this guide delineates a sequential approach to discerning and resolving TCP Resets between Client and Server.
1. Pinpointing the Predicament
The initial stride in problem-solving involves pinpointing the predicament. For TCP Resets, symptoms might include an abrupt disconnection or a failure to set up a link. Utilize diagnostic network applications to confirm if TCP Resets are the culprit. Software such as Wireshark can enable you to trail and dissect network activity to detect TCP Resets.
<code class="language-bash"># Invoke Wireshark to trail network activity sudo wireshark</code>
2. Tracing the Origin
On confirming that TCP Resets are responsible, the subsequent stride entails tracing the origin. This could be either the client or the server. Examine network activity meticulously to ascertain which entity is transmitting the TCP Reset packets.
<code class="language-bash"># Scope out TCP Reset packets in Wireshark tcp.flags.reset == 1</code>
3. Comprehending the Root Cause
The root cause of TCP Resets varies, from erroneous TCP sequence numbers, closed ports, or firewall configurations. Assess network activity and machine logs to grasp the underlying reasons for the TCP Resets.
<code class="language-bash"># Scrutinize system logs for glitches cat /var/log/syslog | grep -i "error"</code>
4. Executing a Remedy
Post confirming the root cause, you can then execute an appropriate remedy. This may encompass adjusting firewall configurations, unlatching closed ports, or rectifying TCP sequence numbers.
<code class="language-bash"># Unlatch a closed port sudo iptables -A INPUT -p tcp --dport 80 -j ACCEPT</code>
5. Verifying the Resolution
After executing the remedy, proceed to verify if the issue has been amicably resolved. Inspect network activity vigilantly for any additional TCP Resets.
<code class="language-bash"># Watch network activity for TCP Resets tcpdump -i eth0 'tcp[tcpflags] & (tcp-rst) != 0'</code>
6. Keeping a Record of the Resolution Process
The final step is to keep a concise record of the entire resolution process. This could lend a hand in future problem-solving or as a valuable resource for training purposes.
Always remember, problem-solving symbolizes a process of elimination. It might necessitate several endeavours to pinpoint and address the problem. Diligence and a methodical approach are integral here.
In summary, peeling the layers of TCP Resets between Client and Server can be arduously complex. Nevertheless, with unambiguous insights into the process, coupled with a methodical troubleshooting procedure, effective management of these tasks becomes achievable. This guide has incorporated a coherent, sequential approach towards resolving TCP Resets, extending from pinpointing the predicament to the execution and verification of a remedy.
Common Inquiries Surrounding TCP Resets Involving Client and Server
TCP-related Resets from the vantage point of client and server, colloquially known as TCP-RST-FROM-Client, invokes a myriad of questions for discussion. This chapter aims to deepen your understanding by addressing some of the most common inquiries related to TCP Resets in the context of client and server.
1. What does TCP-RST-FROM-Client indicate?
In the realms of Transmission Control Protocol (TCP), TCP-RST-FROM-Client, often referred to as TCP Reset, is an procedure to end a connection abruptly. This can occur when either the client or the server decides to disengage with its counterpart, signaling for an immediate termination of the ongoing TCP connection.
2. Unraveling the workings of a TCP Reset
Executing a TCP Reset involves the dispatch of a packet with the RST flag activated. Either the client or the server can initiate this action. Upon receiving this packet, the other party terminates the connection promptly.
<code class="language-python">def initiate_tcp_reset():
# Develop a TCP/IP socket
connection = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
# Activate the RST flag
connection.setsockopt(socket.SOL_SOCKET, socket.SO_LINGER, struct.pack('ii', 1, 0))
# Establish the socket to the server
server_coordinates = ('localhost', 10000)
connection.connect(server_coordinates)
# Dispatch data to initiate the RST
memo = 'Here's a TCP Reset'
connection.sendall(memo.encode())
# Disconnect the socket, this triggers the RST
connection.disconnect()</code>
3. Can you pinpoint when a TCP Reset is sent?
A TCP Reset is generally dispatched when the system encounters an unanticipated packet, for instance, a packet related to a previously closed connection or one with an incorrect sequence number. Other situations may include when a service is unresponsive or if a security scare necessitates a swift disconnection.
4. How does a TCP Reset affect network communication?
The ripple effect of a TCP Reset on network communication can be profound. It can abruptly terminate a connection, leading to potential loss of data. Moreover, if exploited with malicious intent, it can provoke a denial of service.
5. How can I regulate TCP Resets in a Client-Server interaction?
The regulation of TCP Resets revolves around vigilant monitoring of network traffic and appropriate configuration of firewall guidelines. Other measures may entail calibration of TCP settings on the client and server ends to minimize unexpected resets.
6. What measures can aid in troubleshooting TCP Resets?
The analysis of network traffic using tools like Wireshark frequently underpins the troubleshooting of TCP Resets, as it can identify the genesis of the resets. Other useful measures may include an examination of system logs and firewall configurations.
7. Are TCP Resets a matter of security concern?
Indeed, TCP Resets can potentially pose a security threat. They can be weaponized in denial-of-service attacks to disrupt network communication. Nevertheless, proper usage can morph them into an effective security instrument, particularly while promptly terminating an under attack connection.
8. Is there any way to bypass TCP Resets?
Complete bypassing of TCP Resets is typically neither possible nor recommended, considering their role in TCP's error management. However, unnecessary resets can be curtailed by ensuring optimal network configuration and correct handling of TCP connections by your applications.
In the final analysis, a thorough understanding of TCP Resets in a client to server context is of prime importance for securing and maintaining robust network communication. Being familiar with their operation and management, you can fortify your network's resilience and security.
如有侵权请联系:admin#unsafe.sh