2024-1-24 18:38:40 Author: lab.wallarm.com(查看原文) 阅读量:15 收藏
Opening Note: Understanding the Core Concepts of Security Analysis
Continual developments in technology have elevated the significance of security analysis, a critical phase in software design. You can think of it as a vital diagram within the process of coding, engineered to identify and resolve any concealed abnormalities within a platform, application, or network. Essentially, it serves as the bulwark against impending virtual perils.
Instead, envision security analysis as a comprehensive blueprint for a complex cyber mechanism. Similar to how a diagram illuminates the functionality of a machine, security analysis provides a defense mechanism against the invasion of pesky cyber delinquents.
Next, delving deeper into the bedrock notions supporting security analysis, here are the main concepts:
1. Identifying Security Norms: The launch point of the cybersecurity exploration involves recognizing the mandatory security principles of a platform, often labelled as Defense Principles. They are typically formulated depending on the operational aspects of the system, the kind of information it handles, and the potential cyber risks it may face. For instance, a software handling financial transactions would necessitate foolproof data handling and stringent validation procedures.
<code class="language-python"># Illustration of a defense principle
class ProtectivePrinciple:
def __init__(self, principle_name, principle_description):
self.principle_name = principle_name
self.principle_description = principle_description
principle1 = ProtectivePrinciple("Information Preservation", "Adhere to strict data control using AES-256.")</code>
2. Tracing Probable Threats: After shaping security norms, a navigational plan is drafted that considers possible threats, also known as Risk Evaluation. It involves locating potential attack entrances and devising preventive tactics to protect the system.
<code class="language-python"># Representation of a risk evaluation
class ThreatAssessment:
def __init__(self, threat_title, threat_examination, safeguard_proposal):
self.threat_title = threat_title
self.threat_examination = threat_examination
self.safeguard_proposal = safeguard_proposal
threat1 = ThreatAssessment("Invasive SQL Attack", "Likely malicious SQL code infiltration.", "Employ parameterized queries to avert SQL incursions.")</code>
3. Forming the Testing Model: Based on the delineated defense principles and detected threats, a procedural checking plan is put into action. This involves the necessary tools, anticipated outcomes, and the overall techniques for executing the tests.
<code class="language-python"># Display of a checking layout
class ScrutinyScheme:
def __init__(self, check_title, check_method, check_tools, expected_results):
self.check_title = check_title
self.check_method = check_method
self.check_tools = check_tools
self.expected_results = expected_results
checking_sketch1 = ScrutinyScheme("Guarding Against SQL Attacks", "Employ software automation to mimic SQL attack trials.", ["SFML", "Havij"], "Forecasting successful deterrence of SQL infiltrations.")</code>
4. Initiating the Testing Model: The scrutiny scheme is then put into action, combing the system thoroughly for any likely flaws.
5. Appraising the Results: The findings of the tests are then assessed to uncover any security weak points or errors.
6. Strengthening the System: Upon locating any potential weaknesses, appropriate corrective actions are taken, and rechecks are conducted to confirm the weaknesses have been duly addressed and resolved.
Here's an overview of the building blocks that constitute the foundational framework of security analysis:
| Component | Description |
|---|---|
| Identifying Security Norms | Outlining the platform's defense principles |
| Tracing Probable Threats | Highlight assumed threats and reactive stratagems |
| Forming the Testing Model | Outlining the investigation layout and forecasting possible results |
| Initiating the Testing Model | Carrying out checks to discover system vulnerabilities |
| Appraising the Results | Reviewing test findings to identify weak points |
| Strengthening the System | Repair identified problems and validate solutions via re-inspections |
To conclude, the procedure of security analysis is granular and thorough, starting with defining security requisites, leading on to threat detection, sketching check layouts, executing checks, appraisal, and finally, bolstering the platform. Grasping these elementary concepts of security analysis is crucial for creating robust, near-invincible platforms.
Traversing the Diverse Techniques of Security Analysis

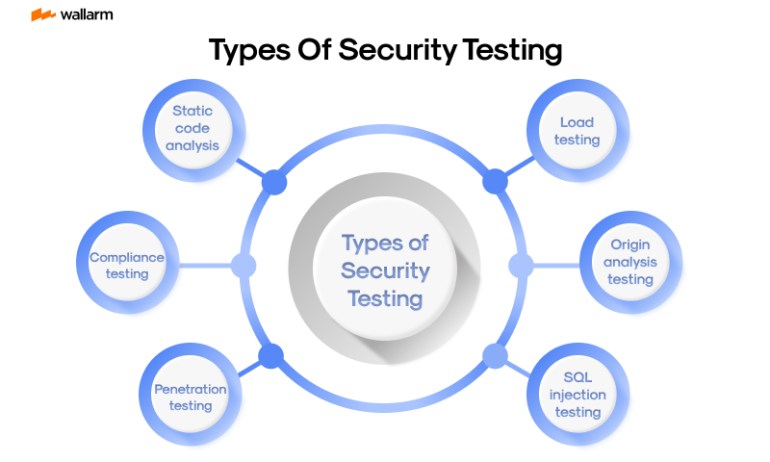
Delving into the terrific terrain of software evaluation, security analysis emerges as an unassailable foundation. Its quintessence lies within revealing concealed vulnerabilities, targeting threats, and discerning hidden risks intertwined within any software application, ultimately fortifying the bulwark against sinister interlopers. To fully fathom multiple aspects of security testing, we must delve into their assorted manifestations. Each variant of testing delivers unique merits and plays a pivotal function in fortifying software's defense mechanisms.
1. Delving into Source Code Examination (DSCE)
The 'white box testing', better known as DSCE, takes a meticulous approach towards dissecting an application's source code. This scrutiny is frequently conducted during the rudimentary phase of developmental cycle, often prior to code compilation.
<code class="language-python"># An example from DSCE- Python Code Snippet
def improper_deserialization(user_input):
pickle.loads(user_input)</code>
Looking at the Python code snippet above, the function 'improper_deserialization' is susceptible to potential attacks since it involves unsanctioned deserialization of user inputs. DSCE tools would label such a function as a potential security hazard.
2. Live State Application Examination Test (LSAET)
Also labelled as 'black box testing,' LSAET initiates post-activation of the software. It identifies vulnerabilities by crafting attacks and monitoring the application's response.
<code class="language-html"><!-- An LSAET HTML code snippet example --> <form action="/entry" method="post"> <input type="text" name="user_id"> <input type="password" name="secret_code"> <input type="submit" value="Submit"> </form></code>
In the HTML form above, an LSAET instrument may devise SQL provocations or Cross-Site Script attacks to examine the integrity of the form's security.
3. Comprehensive Security Validation Test (CSVT)
CSVT combines the merits of DSCE and LSAET, employing a blend of dynamic analysis and immediate verification to expose security deficiencies, thus presenting a complete outlook on the application's overall defense status.
4. Crafted Virtual Cyber Onslaught (CVCO)
Known as penetration testing, CVCO executes a thoughtfully designed cyber-assault targeting a system with the intention to unveil dormant vulnerabilities. It marries automated and manual strategies to penetrate software's security protection.
5. Security Compliance Verification Procedure (SCVP)
SCVP is a comprehensive review of software programs and operating systems with a goal of exposing security flaws. In addition, an SCVP validates the firm's compliance with prescribed security protocols and lawful norms.
6. Protective Armor Analysis
This technique aims to locate frailties in diverse systems and networks while defining strategies to mitigate the associated risks. Protective Armor analysis can be executed manually, automatically, or via a blended approach.
7. Hazard Appraisal
This method facilitates the ranking of security hazards in an organization. Threats are categorized into Low, Moderate, or Severe levels. This strategem empowers organizations to effectively prioritize their defensive countermeasures.
8. Automated System Threat Scan (ASTS)
ASTS is an automated review of systems, formulated to pinpoint proven vulnerabilities. The insights are typically archived in the vulnerability scanner's database for future perusal.
9. Organizational Protection Evaluation
This approach includes a thorough study of an organization's security equilibrium, reviewing its safety regulations, strategies, and safeguards in place.
10. Authorized Digital Intrusion
Contrary to their malevolent counterparts, sanctioned digital intruders use their skills to bolster an organization's defenses. They detect frailties and perils within the system that a malicious hacker might exploit.
| Evaluation Method | Brief Overview |
|---|---|
| DSCE | Scans application's source code |
| LSAET | Engages provocations to uncover weak spots |
| CSVT | Merges DSCE and LSAET |
| CVCO | Employs a cyber-attack on a system |
| SCVP | Undertakes a systematic scan of applications and OS |
| Protective Armor Analysis | Identifies system/network vulnerabilities |
| Hazard Appraisal | Organizational hazard profiling |
| ASTS | Automated scrutiny of systems for visible flaws |
| Organizational Protection Evaluation | Appraises organization-wide security preparedness |
| Authorized Digital Intrusion | Discovers potential threats in the system |
From a wider perspective, each style of security evaluation amplifies the sturdiness of a software's defenses. By comprehending these varieties, organizations can effectively fortify their systems and protect their information from looming dangers.
`
`
Leveraging Superior Security Evaluation Tools for Enhanced Defense

Navigating the ever-changing realm of cybersecurity necessitates the ability to anticipate and respond to threats. A practical method for doing this is by employing leading-edge security assessment tools. These resources offer an all-encompassing strategy to unveil potential weak spots, fortifying your system against breaches. In this section, we'll explore several top-notch security evaluation tools in today's market, highlighting their role in boosting your defense mechanism.
1. OWASP ZAP
The Open Web Application Security Project's Zed Attack Proxy (ZAP) is an unrestricted, community-driven web application safety probe. Its design is to instigate the detection of security loopholes within your web applications during their creation and probe stages.
<code class="language-python"># Example of utilizing OWASP ZAP Python API from zapv2 import ZAPv2 zap = ZAPv2(apikey='your-api-key') print('Accessing target %s' % target) zap.urlopen(target) print('Initiating spidering target %s' % target) zap.spider.scan(target)</code>
2. Nessus
Nessus is an exclusive vulnerability inspection tool from the house of Tenable Network Security. It enjoys great popularity among security evaluation tools due to its intricate vulnerability repository and intuitive interface.
3. Wireshark
Wireshark is a complimentary, community-driven traffic analyser. It desciphers your network activity at a granular level, making it a preferred choice across numerous commercial and non-profit entities.
<code class="language-bash"># How to use Wireshark wireshark -k -i <interface></code>
4. Burp Suite
Burp Suite offers a robust and functional platform for executing security probes of web applications. It enables comprehensive control, merging proficient manual approaches with cutting-edge automation techniques.
5. SQLMap
SQLMap is a community-supported penetration probe tool that mechanizes the task of discovering and exploiting SQL injection deficiencies, leading to the control of database servers.
<code class="language-bash"># Demonstrating the use of SQLMap sqlmap -u "http://www.target.com/page.php?id=1" --dbs</code>
Comparative Schema of Security Evaluation Tools
| Tool | Open Source | Vulnerability Disclosure | Network Dissection | Web Application Defense |
|---|---|---|---|---|
| OWASP ZAP | Yes | Yes | No | Yes |
| Nessus | No | Yes | Yes | Yes |
| Wireshark | Yes | No | Yes | No |
| Burp Suite | No | Yes | No | Yes |
| SQLMap | Yes | Yes (SQLi) | No | Yes |
By familiarizing yourself with the strengths and weaknesses of every tool, you can opt for one that aligns perfectly with your requirements. Remember, relying on a single tool for absolute security is a myth. Simultaneous usage of multiple tools is always recommended for an encompassing defense.
In the next chapter, we'll dissect the industry-standard practices for security testing, ensuring you maximize the benefits offered by these tools.
Understanding Jargon: Efficient Tactics for Safeguarding Evaluations
Examining the safeguarding aspects of software creation is crucial. These types of inquiries ensure that the software doesn't contain potential flaws that could disrupt its functionality or the correctness of the data it handles. Importantly, the authenticity of these outcomes heavily relies on operating specific finest practices during the safeguarding evaluation stage. The intention of this chapter is to illuminate these tactics, to aid you in acquiring a comprehensive understanding of effectual methods in security testing.
1. Initiate Early, Review Consistently
A renowned principle in safeguarding testing is to start early, integrating such an examination into the initial phases of the software creation process. This pre-emptive strategy facilitates the identification and rectification of potential risks before they transform into significant concerns.
<code class="language-python"># Pictorial demonstration of initial security review in Python
import unittest
from myapp import MyApp
class SecurityCheck(unittest.TestCase):
def setUp(self):
self.app = MyApp()
def test_code_interference(self):
# Performance of a SQL intrusion vulnerability test
response = self.app.query("DROP TABLE users;")
self.assertNotEqual(response.status_code, 200)</code>
2. Embrace a Threat-Oriented Approach
Not all security dangers can be viewed with the same risk severity. Therefore, it's advantageous to order your examination efforts based on the hypothetical consequences of a security breach. This threat-focused method helps in directing your resources towards the most vital segments, guaranteeing maximum protection.
3. Employ Varied Evaluation Techniques
Safeguarding evaluation doesn't stick to a single procedure. Various testing methods are available to expose specific vulnerability types. For instance, a penetration test can establish deficiencies that an nefarious actor might exploit, while static code review can pinpoint concealed problems in your software.
<code class="language-java">// Illustrative representation of static code review in Java
public class SecurityUtilities {
public boolean passwordAuthentication(String password) {
if (password.length() < 8) {
return false;
}
return true;
}
}</code>
4. Remain Informed About New Dangers
The sector of cyberspace safety is persistently evolving, with fresh threats emerging continually. Stay updated about the newest security risks and susceptibilities to ensure the applicability of your evaluation procedures.
5. Boost Automation
Amping up automation can dramatically accelerate the safeguarding evaluation process while offering constancy. Nevertheless, automation shouldn't entirely replace manual scrutiny. The most efficacious outcomes are accomplished with a combination of both.
<code class="language-javascript">// Illustration of automated security evaluation in JavaScript
const zaproxy = require('zaproxy');
const zap = new zaproxy('http://localhost:8080');
zap.spider.scanAsUser(contextId, userId, targetUrl, maxChildren, recurse, subtreeonly, (err, resp) => {
// Managing output
});</code>
6. Guarantee All-Embracing Evaluation Range
Ensure that your safeguarding evaluation encompasses all facets of your software solution, including its code, database, networking, and user interface. Full-scale coverage guarantees that no part is susceptible to possible assaults.
7. Regular Reassessment and Upgradation of Policies
Safeguarding evaluation isn't a one-off task. Systematic reassessments and enhancements to evaluation policies are requisite to keep them potent against the newest dangers.
8. Enrichment of Team Awareness
Ensure that your crew is adept in a multitude of safeguarding evaluation techniques and finest practices. A knowledgeable team is the best quarantine against cyberspace safety threats.
In conclusion, safeguarding examination is a pivotal component in the domain of software creation. By adhering to the finest practices detailed, it elevates the security, trustworthiness, and dependability of your software. The upcoming chapter will contrast diverse safeguarding evaluation instruments to aid in selecting the most suitable one for your requirements.
A Reflective Analysis: Clash of Security Testing Instruments
Navigating the prolific realm of security testing leads you to encounter a multitude of tools. Each one, while having its distinctive merits and demerits, is tailored to executing specific kinds of security tests. Through this chapter, we intend to juxtapose some of the widely acclaimed security testing tools to simplify your choice of the perfect instrument.
1. Dissection: Zed Attack Proxy (ZAP) from OWASP vs. Tenable's Nessus
OWASP brings to the table a complementary, open-source web app security testing tool called ZAP (Zed Attack Proxy). Its charm lies in uncovering potential security loopholes in your web applications during their development and testing phases.
<code class="language-python"># A brief code snippet to initialize a new ZAP session from zapv2 import ZAPv2 zap = ZAPv2() zap.urlopen('http://target.com')</code>
Contrarily, Nessus is a paid, proprietary tool from the house of Tenable Network Security. Nessus outshines its competitors with a broad vulnerability coverage, powered by over 45,000 plugins.
| Attributes | Zed Attack Proxy (ZAP) | Nessus |
|---|---|---|
| Investment | None | Required |
| Open Source | True | False |
| Coverage of Vulnerabilities | Satisfactory | Comprehensive |
| User Interface | GUI, CLI | GUI, CLI |
| Capacity for Customization | Superior | Adequate |
2. Delving into Network Protocols: Wireshark vs. tcpdump
Wireshark, an open-source, full-featured network traffic analyzer, provides an in-depth insight into your network's activities. Expert professionals often rely on its ability to troubleshoot network issues, conduct analysis, create applications, and develop communication protocols.
<code class="language-bash"># A quick command to seize packets using Wireshark wireshark -i eth0 -k -Y 'http'</code>
Alternatively, tcpdump is a substantial, command-line utility for packet analysis. Tcpdump empowers users to witness TCP/IP and other network protocols in transit across any linked network.
| Attributes | Wireshark | tcpdump |
|---|---|---|
| Investment | None | None |
| Open Source | True | True |
| User Interface | GUI, CLI | CLI |
| Scope for Customization | Superior | Superior |
| Protocol Support | Comprehensive | Intermediate |
3. Fighting Web Threats: Burp Suite vs. SQLmap
Burp Suite emerges as a prominent player in the league of web security testing. Its comprehensive suite of features includes a proxy server, a web spider, scanner, intruder, repeater, sequencer, decoder, and comparer.
<code class="language-java">// A brief code snippet to dispatch a request with Burp Suite IBurpExtenderCallbacks callbacks = BurpExtender.getCallbacks(); IHttpRequestResponse messageInfo = callbacks.makeHttpRequest(httpService, request);</code>
In comparison, SQLmap is a free, open-source tool that streamlines penetration testing by identifying SQL injection vulnerabilities leading to potential database takeovers.
| Attributes | Burp Suite | SQLmap |
|---|---|---|
| Cost | Basic and Premium options | None |
| Open Source | False | True |
| User Interface | GUI, CLI | CLI |
| Degree of Customizability | Superior | Satisfactory |
| Primary Purpose | Web Security | Averting SQL Injection |
In summary, selecting an appropriate security testing tool revolves around your specific requirements, the available budget, and the kinds of vulnerabilities you're charting to detect. To optimize your coverage against looming security threats, it is better to employ a blend of multiple tools.
Crafted Suggestions for Top-Tier Returns from Security Assessments
The sphere of software development flourishes when firmly rooted in thorough security analyses. This vital step encases applications with a protective shield, ensuring ongoing performance and dependability. Such scrutiny involves exacting attention to minute elements, deep knowledge of potential risks, and proficient use of appropriate tools to uncover and disarm potential threats. This chapter offers astute advice for maximizing benefits from your security appraisal ventures.
1. Decode Your Software
Possessing extensive knowledge of your software is the cornerstone of efficient risk vulnerability investigations. Understanding its underlying blueprint, the driving technology, the flow of data, and the services it provides will help you identify potential weaknesses that could be exploited by digital trespassers.
<code class="language-python"># Example of understanding data movement in a Python software
def process_input(input_param):
# Experiment with the input data
examined_data = specific_processing_function(input_data)
return examined_data
def fundamental_func():
# Retrieve the input data
input_param = acquire_input_data()
# Process the input data
examined_data = process_input(input_param)
# Implement the processed data
execute_examined_data(examined_data)
if __name__ == "__main__":
fundamental_func()</code>
In the demonstrated Python script, data traverses from acquire_input_data function, through process_input function, to execute_examined_data function. Understanding this journey can indicate appropriate places for data verification and cleaning to secure against vulnerabilities.
2. Design Your Examination
Various security assessments have differing levels of importance based on the software's purpose and the data it handles. Construct your examination design on the expected impact of a security breach. For instance, tests for data ciphering and user validation should take precedence if your software deals with confidential user data.
| Significance | Security Investigation | Basis |
|---|---|---|
| Essential | Data Ciphering | Protects private data from theft |
| Essential | User Verification | Limits software access to authorized individuals |
| Medium | Input Verification | Prevents malicious data from entering the software |
| Low | Error Handling | Avoids exposing sensitive details through error messages |
3. Deploy Both Automated and Manual Investigations
Automated and manual checks each serve a distinct purpose in the realm of security examinations. Automated tools quickly highlight common vulnerabilities while manual checks offer deep exploration of potential security chinks. Utilize a combination of both for a comprehensive security review approach.
<code class="language-bash"># Sample of using an automated security investigation tool $ owasp-zap -rapidresult zap_output.xml -rapidsite https://www.previewWebsite.com</code>
In the given command line, the OWASP ZAP tool performs a speedy automated security scan on the preview website at "https://www.previewWebsite.com", recording the results in "zap_output.xml".
4. Perpetual Learning
The realm of security is ever-evolving, hence, your safeguarding protocols should follow suit. Commit to keeping abreast of the newest security vulnerabilities and investigation methods. This could include listening to podcast updates on security, active participation in security-centered forums, and regular reviews of security bulletins from trusted sources.
5. Learn from Missteps
In the unfortunate circumstance of a security breach, take it as an opportunity for improvement. Investigate the cause of the breach, the exploited gaps, and how it could have been prevented. Subsequently, enhance your security investigation techniques to prevent similar incidents moving forward.
In conclusion, maximizing the efficacy of your security assessments requires in-depth knowledge of your software, thoughtful planning, employing both automated and manual testing techniques, maintaining up-to-date knowledge of emerging security hazards, and learning from mistakes. Strict compliance with these expert tips will result in superior security for your software applications.
`
`
Proposing Upcoming Templates: Catalysts Shaping Cybersecure Evaluation
As we traverse an ever-expanding digital landscape, the importance of cybersecure evaluation continues to take center stage. A collection of burgeoning methodologies and innovative technological leaps are sketching the future outline of cybersecure evaluation. This chapter delves into these approaching realities, providing a comprehensive analysis of the advancements in cybersecure evaluation.
1. Synthetic Consciousness and Cognitive Approaches
Synthetic Consciousness (SC) and Cognitive Approaches (CA) are stirring a transformative shift in cybersecure evaluation. The SC and CA methodologies can analyze monumental volumes of data, excavate anomalies, and predict potential threats of security. This prognosticating capability builds a foundation for preemptive security strategies, drastically reducing the odds of security infractions.
<code class="language-python"># A snapshot of a code block showcasing the use of CA in cybersecure evaluation from sklearn.ensemble import RandomForestClassifier from sklearn.model_selection import train_test_split # Dividing data into learning and testing groups X_train, X_test, y_train, y_test = train_test_split(X, y, test_size=0.3, random_state=0) # Setting up a random forest Classifier clf = RandomForestClassifier(n_estimators=100) # Training the Classifier clf.fit(X_train, y_train) # Forecast the outcome for testing dataset y_pred = clf.predict(X_test)</code>
2. Automated Techniques in Security Evaluation
Automation is another driving force significantly sculpting cybersecure evaluation. Self-regulated evaluation tools can execute repetitive tasks, granting examiners the bandwidth to focus on complex challenges. Automation also improves accuracy and consistency of evaluation.
| Human Trials | Automated Trials |
|---|---|
| Labor-intensive | Agile |
| Prone to human errors | Highly accurate |
| Limited in scope | Can manage a wide range of trials |
3. Integration of Cybersecure Evaluation in DevOps
Integrating cybersecure evaluation within DevOps - denoted as DevSecOps, is a fast-growing trend. This method ensures an emphasis on security at each stage of the software development cycle, resulting in hardy applications.
4. Rise in Adoption of Open Source Tools
The use of open-source tools in cybersecure evaluation is on the upswing. These tools provide cost efficiency and regular updates from a community of developers, ensuring current security threats are addressed.
5. Shift-Left Approach
The shift-left approach means introducing cybersecure evaluation during the earlier phases of software development. This preparatory approach can identify and address potential issues before they intensify.
6. Cybersecure Evaluation in the Cloud
With the broad acceptance of cloud technologies, cloud-based cybersecure evaluation is taking the front seat. This method offers flexibility, scalability, and affordability.
7. Increased focus on Privacy Evaluation
With the introduction of laws like GDPR, the significance of privacy evaluation has increased. It involves appraising applications for adherence to data privacy laws.
In summary, the path of cybersecure evaluation is both ascendant and dynamic. By staying abreast with these transformative methodologies, organizations can ensure they are poised to face future cybersecurity challenges.
如有侵权请联系:admin#unsafe.sh