2024-1-30 13:40:35 Author: securityboulevard.com(查看原文) 阅读量:9 收藏
A new concern has surfaced for Outlook users! Accepting calendar invitations within the platform may now pose a serious risk to the security of user passwords. A recent Outlook vulnerability, patched in December 2023 is still hiding for unpatched users, could expose your password with just a single click. This isn’t your typical phishing scam – malicious actors can craft seemingly harmless calendar invites that, when accepted, leak your password hash in just one click.
Varonis Threat Labs recently identified a fresh Outlook vulnerability (CVE-2023-35636) as part of three new methods for obtaining NTLM v2 hashed passwords through exploits in Outlook, Windows Performance Analyzer (WPA), and Windows File Explorer. These vulnerabilities enable attackers to launch offline brute-force or relay attacks, risking unauthorized access and compromising accounts. This blog tells about a recently discovered vulnerability, shedding light on how cyber attackers could exploit this flaw to gain unauthorized access.
What is NTLM v2 (Windows New Technology LAN Manager)
Microsoft Windows uses a cryptographic protocol for secure user authentication to remote servers, enhancing security compared to NTLM. However, it still exhibits susceptibility to offline brute-force and authentication relay attacks. In NTLM, passwords securely transmit as hashes, converted into concise alphanumeric strings using encryption algorithms. The absence of salting, a practice that adds a random value to passwords to hamper pre-computed hash table attacks, renders these hashes password equivalent. Consequently, attackers obtaining the hash value can authenticate without knowledge of the actual password.
How Attackers Use NTLM v2 Hashes?
These are commonly exploited by attackers in two main types of attacks: offline brute-force attacks and authentication relays.
Offline Brute Force
An offline brute-force attack involves a threat actor having access to the hash of a user’s password. Using a computer, the attacker systematically generates all possible passwords, attempting each one against the hash until a match is found. This method is conducted solely on the attacker’s machine, leaving no trace on the network and making detection difficult. The technique’s prevalence is evident with ntlm.pw, a free web tool emphasizing risks linked to crackable passwords and hash vulnerability.
Authentication Relay
An authentication relay attack involves a threat actor intercepting an NTLM v2 authentication request and redirecting it to another server. Subsequently, the victim’s machine transmits the authentication response to the attacker’s server. The attacker can leverage this information to authenticate themselves on the server originally intended by the victim.
MS Outlook Vulnerability Leaks Passwords
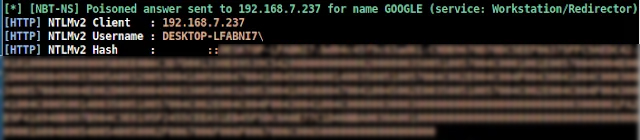
The identified Outlook vulnerability, CVE-2023-35636, has raised significant concerns as it introduces a novel attack vector that allows threat actors to leak the hashed passwords during the process of sharing calendar invites. The exploitation of this security flaw involves the manipulation of email headers by attackers, prompting Outlook to make authentication requests to the attacker’s system. Specifically, two headers – one indicating “content-class” as “sharing” and the other directing to an “x-sharing-config-url” – are employed. When an Outlook user opens a calendar invite link, the hashed password becomes exposed as Outlook attempts to authenticate on the attacker’s system to retrieve the associated .ics file.
What makes this exploit particularly noteworthy is its one-click weaponization, as highlighted by Dvir Sason from Varonis. Sason highlights the difference between a CVE-patched vulnerability and a functional abuse in Microsoft’s decision. The simplicity and effectiveness of the one-click action, where the victim unwittingly leaks their password by accepting a calendar invite, sets CVE-2023-35636 apart from other reported issues.
Microsoft responded promptly by including a patch for CVE-2023-35636 in the updates released on December 12. The medium-severity CVSS score of 6.5 underscores the urgency of this patch. While the exact remediation rate is unknown, historical data from a 2023 report by Edgescan suggests that vulnerabilities of critical severity typically took an average of 65 days to be addressed.
Book a Free Consultation with our Cyber Security Experts

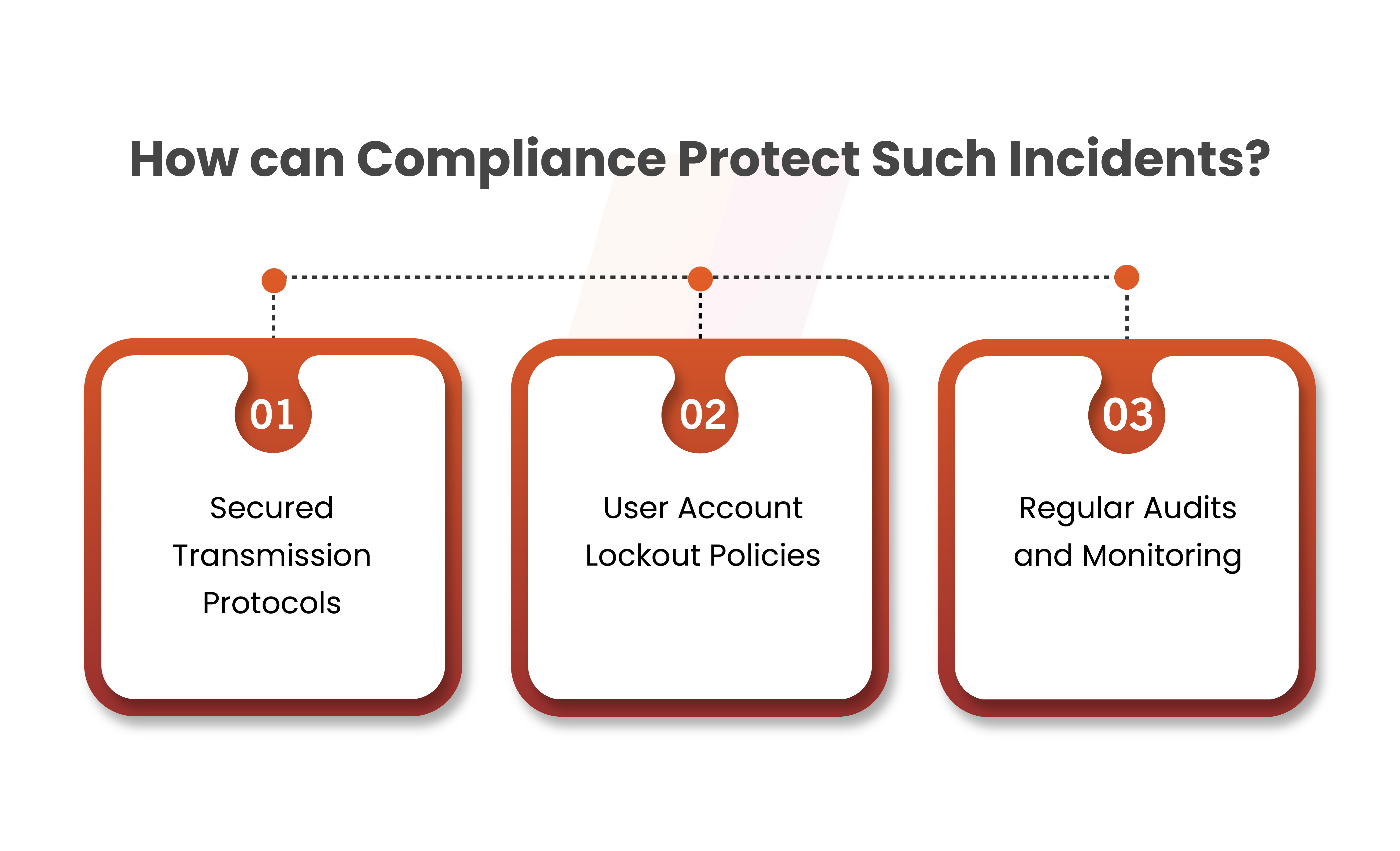
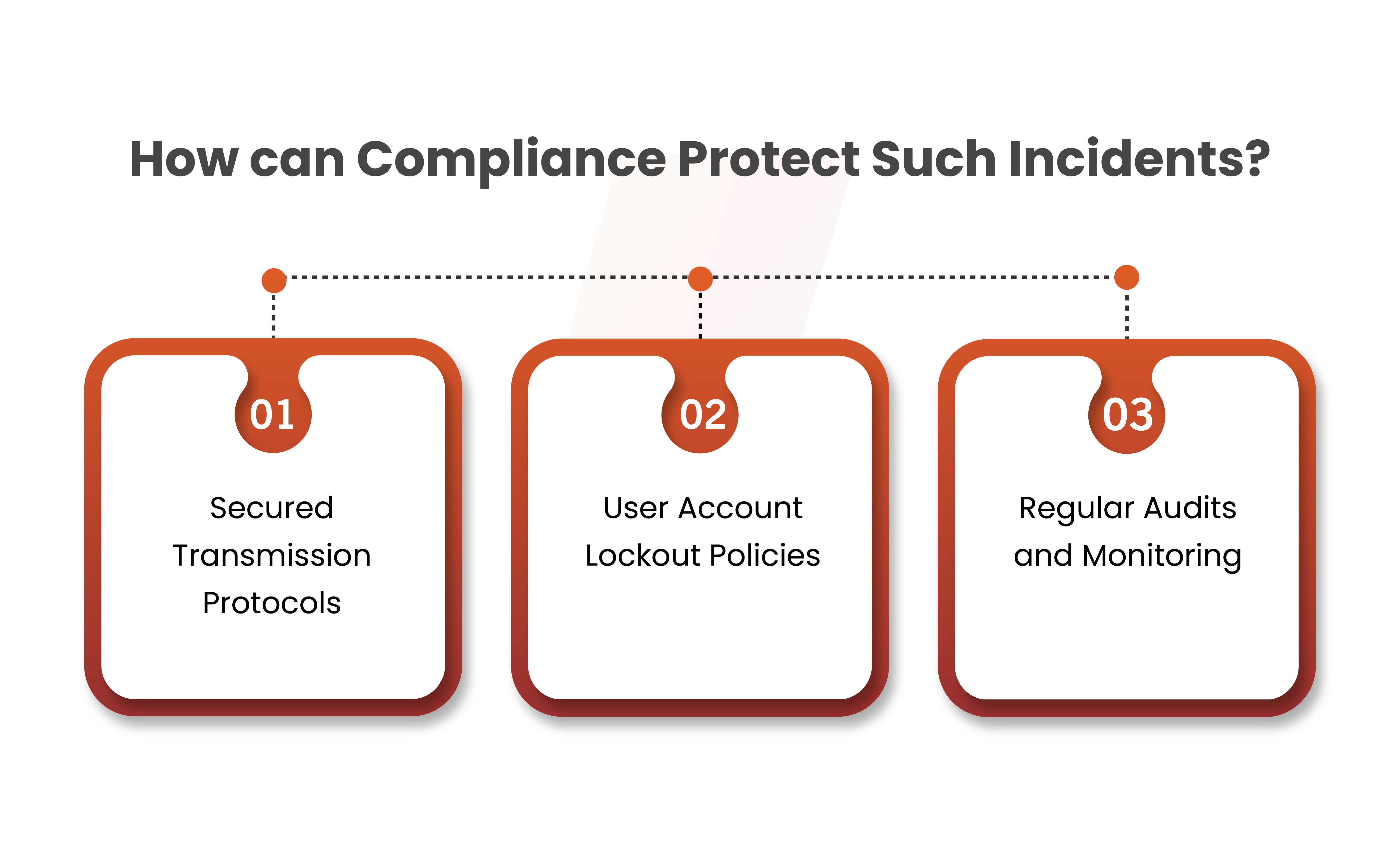
How can Compliance Protect Such Incidents from Happening?
Compliance plays a crucial role in protecting against password leaks by establishing and enforcing security standards. Here are some ways of how compliance can help mitigate the risk of password leaks:
Secured Transmission Protocols
Compliance frameworks may also mandate the use of robust transmission protocols—such as HTTPS—when sending passwords and other sensitive data across networks. This protects against the transmission of statistics through man-in-the-middle attacks.
User Account Lockout Policies
Frequently, compliance recommends or mandates setting personal account lockout policies. By locking out a user account after a predetermined number of unsuccessful login attempts, these rules help defend against brute-force attacks by prohibiting unwanted access.
Regular Audits and Monitoring
Compliance frameworks often necessitate regular audits and monitoring of systems to identify and respond to potential security incidents. This helps in detecting unauthorized access or suspicious activities related to password handling.
Conclusion
The Outlook vulnerability CVE-2023-35636 poses a serious one-click threat, exposing NTLM v2 hashed passwords through calendar invites. Microsoft promptly addressed the issue with a patch emphasizing the urgency with a medium-severity CVSS score. Compliance services including security assessments, lockout policies, and audits, are vital in preventing such incidents. These practices defend against unauthorized access and password leaks, reinforcing cybersecurity amid evolving threats.
Kratikal, recognized as a CERT-In empanelled auditor, plays a pivotal role in providing premium security. Drawing upon our extensive experience, we provide in-depth analysis and strong defense mechanisms against the ongoing threat of cyber attacks. Collaborating with Kratikal facilitates early detection and resolution of security flaws, effectively preventing malicious hackers from capitalizing on vulnerabilities.
Ref: https://www.scmagazine.com/news/accepting-a-calendar-invite-in-outlook-could-leak-your-password
The post Can MS Outlook Calendar Leak Your Password? appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Shikha Dhingra. Read the original post at: https://kratikal.com/blog/can-ms-outlook-calendar-leak-your-password/
如有侵权请联系:admin#unsafe.sh