The China-based threat actor known as Mustang Panda is suspected to have targeted Myanmar's Ministry of Defence and Foreign Affairs as part of twin campaigns designed to deploy backdoors and remote access trojans.
The findings come from CSIRT-CTI, which said the activities took place in November 2023 and January 2024 after artifacts in connection with the attacks were uploaded to the VirusTotal platform.
"The most prominent of these TTPs are the use of legitimate software including a binary developed by engineering firm Bernecker & Rainer (B&R) and a component of the Windows 10 upgrade assistant to sideload malicious dynamic-link libraries (DLLs)," CSIRT-CTI said.
Mustang Panda, active since at least 2012, is also recognized by the cybersecurity community under the names BASIN, Bronze President, Camaro Dragon, Earth Preta, HoneyMyte, RedDelta, Red Lich, Stately Taurus, and TEMP.Hex.
In recent months, the adversary has been attributed to attacks targeting an unnamed Southeast Asian government as well as the Philippines to deliver backdoors capable of harvesting sensitive information.
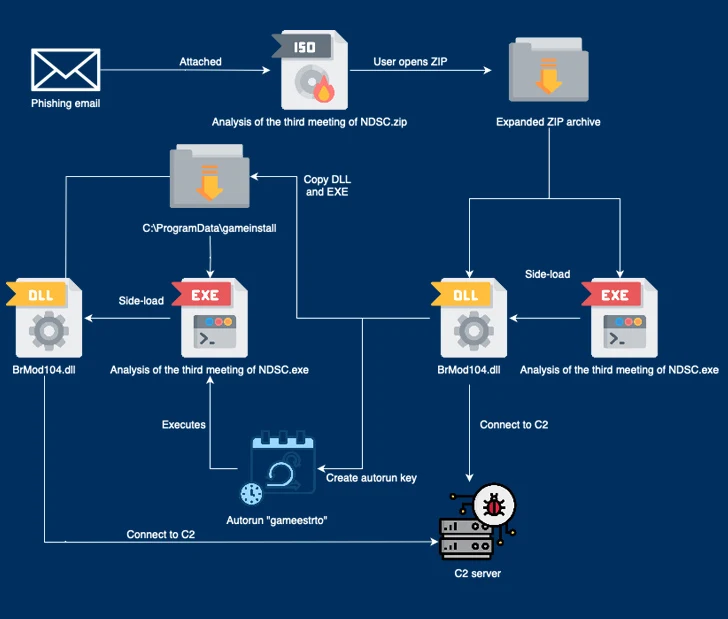
The November 2023 infection sequence starts with a phishing email bearing a booby-trapped ZIP archive attachment containing a legitimate executable ("Analysis of the third meeting of NDSC.exe") that's originally signed by B&R Industrial Automation GmbH and a DLL file ("BrMod104.dll").
The attack takes advantage of the fact that the binary is susceptible to DLL search order hijacking to side-load the rogue DLL and subsequently establish persistence and contact with a command-and-control (C2) server and retrieve a known backdoor called PUBLOAD, which, in turn, acts as a custom loader to drop the PlugX implant.
"The threat actors attempt to disguise the [C2] traffic as Microsoft update traffic by adding the 'Host: www.asia.microsoft.com' and 'User-Agent: Windows-Update-Agent' headers," CSIRT-CTI noted, mirror a May 2023 campaign disclosed by Lab52.
On the other hand, the second campaign observed earlier this month employs an optical disc image ("ASEAN Notes.iso") containing LNK shortcuts to trigger a multi-stage process that uses another bespoke loader called TONESHELL to likely deploy PlugX from a now-inaccessible C2 server.
It's worth noting that a similar attack chain attributed to Mustang Panda was previously unearthed by EclecticIQ in February 2023 in intrusions aimed at government and public sector organizations across Asia and Europe.
"Following the rebel attacks in northern Myanmar [in October 2023], China has expressed concern regarding its effect on trade routes and security around the Myanmar-China border," CSIRT-CTI said.
"Stately Taurus operations are known to align with geopolitical interests of the Chinese government, including multiple cyberespionage operations against Myanmar in the past."
Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post.