2024-1-30 23:1:16 Author: cyble.com(查看原文) 阅读量:47 收藏
Introduction
Atlassian revealed a Remote Code Execution (RCE) vulnerability on January 16, 2024, identified as CVE-2023-22527, impacting outdated versions of both Confluence Data Center and Confluence Server.
CVE-2023-22527 has been labeled as a critical vulnerability involving Object-Graph Navigation Language (OGNL) injection, with a substantial CVSS score of 10 (with the following vector CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H) as per Atlassian.
OGNL, a Java-based expression language, is employed in applications like Atlassian Confluence. When these applications fail to appropriately validate and sanitize user input before incorporating it into OGNL expressions, it can result in a security vulnerability known as OGNL injection.
This enables a Threat Actor (TA) to input specifically crafted strings that include OGNL expressions within user interfaces or input fields, thereby facilitating remote code execution on the affected system.
Cyble Global Sensor Intelligence (CGSI)
The Cyble Global Sensor Intelligence (CGSI) network identified exploitation attempts of CVE-2023-22527 on January 26, 2024. Analysis of the attack patterns observed by CGSI indicates that the attackers aimed to target vulnerable Atlassian Confluence applications in the following countries:
- China
- Singapore
- Brazil
- United States
- Russia
- Vietnam
- India
- Germany
- United Kingdom
- Romania
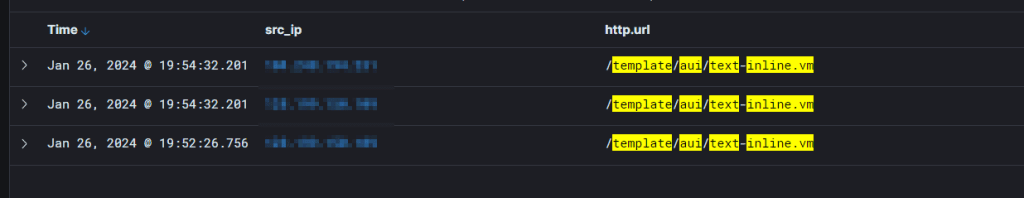
The figure illustrates an exploitation attempt captured by the CGSI network where attackers are initiating POST requests.

Figure 1 – Confluence Scanning Attempts Captured By CGSI
Atlassian Confluence Exposure Instances
According to Cyble ODIN’s scanners, there have been over 4,000 internet-exposed instances of Confluence in the last three months, with the majority of these instances located in the United States, Germany, China, and Russia, as illustrated in the figure below.

Figure 2 – Publicly exposed Confluence instances (Last three months)
Vulnerability Details
RCE (Remote Code Execution) Vulnerability in Confluence Data Center and Confluence Server
CVSS:3.1: 9.8
Severity: Critical
Vulnerable Versions:
Confluence Data Center and Confluence Server endpoints, versions 8.0.x, 8.1.x, 8.2.x, 8.3.x, 8.4.x, and 8.5.0 to 8.5.3
Description:
A template injection vulnerability on out-of-date versions of Confluence Data Center and Server allows an unauthenticated attacker to achieve RCE on an affected version.
Technical Details
The vulnerability arises from the text-inline.vm velocity template, which permits the passing of the label parameter to an OGNL-sink.
By utilizing the expression below:
- #request[‘.KEY_velocity.struts2.context’].internalGet(‘ognl’),
Security researchers from ProjectDiscovery successfully accessed the org.apache.struts2.views.jsp.ui.OgnlTool class and executed the Ognl.findValue(String, Object) method.
It’s important to emphasize that this class is linked to the OGNL library and is not part of Struts. As a result, the “findValue” invocation takes place outside the confined restrictions of Struts’ sandbox environment. This approach allows an attacker to evade the constraints imposed by the sandbox enforced by Struts.
According to ProjectDiscovery’s findings, there is a limitation on the length of OGNL expressions that can be evaluated, specifically a 200-character limit.
In the image below, the upper panel illustrates the HTTP request with the character limit of P1, emphasizing the restrictions imposed by the 200-character limit. The lower panel indicates that an additional parameter can be referenced to bypass this restriction, effectively eliminating the 200-character limit and executing system commands.

Figure 3 – Contrasting HTTP requests: Overcoming the 200-character limit using an additional parameter (Source: Attackerdb)
Conclusion
The increasing trend of TAs exploiting susceptible Internet-exposed assets emphasizes the vital importance of comprehending and consistently securing your attack surface. Attack Surface typically comprises various entry points and interfaces susceptible to exploitation by TAs.
In the instance of this vulnerability found in Confluence Data Center and Server versions, unauthenticated attackers have the potential to exploit a template injection flaw, giving them the capability to execute arbitrary code on compromised systems.
Users with outdated versions are strongly recommended to scrutinize for potential indicators of compromise, conduct a comprehensive cleanup, and upgrade to a secure version.
Our Recommendations
Here are our recommended measures for readers to secure themselves against such attacks:
-
- Enhance your organization’s cybersecurity infrastructure by applying patches as advised by vendors. Atlassian strongly suggests updating each affected installation to the latest available version for Confluence Data Center and Server:
- Confluence Data Center and Server 8.5.5 (LTS)
- Confluence Data Center 8.7.2 (Data Center Only)
- Enhance your organization’s cybersecurity infrastructure by applying patches as advised by vendors. Atlassian strongly suggests updating each affected installation to the latest available version for Confluence Data Center and Server:
-
- Conduct regular security audits and penetration testing to identify and address vulnerabilities, including template injection issues.
-
- Implement proper network segmentation to prevent attackers from performing lateral movement and minimize exposure of critical assets over the internet.
-
- Establish a well-organized patch management process incorporating a clearly defined schedule for regular updates and patches. Prioritize the deployment of critical security patches.
Indicators of Compromise (IoCs)
| Indicators | Indicator Type | Description |
| 128[.]199[.]150[.]109 | IP | Confluence Scanning attempt |
| 14[.]225[.]53[.]68 | IP | Confluence Scanning attempt |
| 179[.]0[.]190[.]32 | IP | Confluence Scanning attempt |
| 103[.]228[.]162[.]76 | IP | Confluence Scanning attempt |
| 125[.]76[.]87[.]134 | IP | Confluence Scanning attempt |
| 202[.]142[.]95[.]131 | IP | Confluence Scanning attempt |
| 193[.]8[.]172[.]178 | IP | Confluence Scanning attempt |
| 194[.]113[.]236[.]177 | IP | Confluence Scanning attempt |
| 60[.]235[.]233[.]170 | IP | Confluence Scanning attempt |
| 47[.]236[.]124[.]26 | IP | Confluence Scanning attempt |
| 222[.]217[.]86[.]135 | IP | Confluence Scanning attempt |
| 177[.]185[.]117[.]136 | IP | Confluence Scanning attempt |
| 64[.]190[.]113[.]197 | IP | Confluence Scanning attempt |
| 161[.]97[.]172[.]232 | IP | Confluence Scanning attempt |
| 14[.]225[.]53[.]21 | IP | Confluence Scanning attempt |
| 217[.]112[.]83[.]246 | IP | Confluence Scanning attempt |
| 120[.]237[.]168[.]25 | IP | Confluence Scanning attempt |
| 49[.]232[.]119[.]187 | IP | Confluence Scanning attempt |
| 219[.]139[.]101[.]136 | IP | Confluence Scanning attempt |
| 111[.]26[.]72[.]177 | IP | Confluence Scanning attempt |
| 47[.]93[.]204[.]111 | IP | Confluence Scanning attempt |
| 193[.]29[.]12[.]182 | IP | Confluence Scanning attempt |
| 183[.]57[.]45[.]194 | IP | Confluence Scanning attempt |
| 222[.]216[.]206[.]99 | IP | Confluence Scanning attempt |
| 183[.]196[.]214[.]38 | IP | Confluence Scanning attempt |
| 39[.]98[.]218[.]14 | IP | Confluence Scanning attempt |
| 14[.]225[.]53[.]158 | IP | Confluence Scanning attempt |
| 114[.]242[.]99[.]122 | IP | Confluence Scanning attempt |
| 39[.]103[.]211[.]146 | IP | Confluence Scanning attempt |
| 5[.]157[.]38[.]50 | IP | Confluence Scanning attempt |
| 47[.]120[.]10[.]39 | IP | Confluence Scanning attempt |
| 122[.]224[.]83[.]80 | IP | Confluence Scanning attempt |
| 120[.]79[.]250[.]151 | IP | Confluence Scanning attempt |
| 39[.]96[.]220[.]196 | IP | Confluence Scanning attempt |
References
https://confluence.atlassian.com/security/cve-2023-22527-rce-remote-code-execution-vulnerability-in-confluence-data-center-and-confluence-server-1333990257.html https://www.picussecurity.com/resource/blog/cve-2023-22527-another-ognl-injection-leads-to-rce-in-atlassian-confluence https://attackerkb.com/topics/wONJMCgCgl/cve-2023-22527 https://blog.projectdiscovery.io/atlassian-confluence-ssti-remote-code-execution/
Related
如有侵权请联系:admin#unsafe.sh