2024-2-5 22:21:21 Author: www.sentinelone.com(查看原文) 阅读量:5 收藏
Today is an exciting day. We announced that our acquisition of PingSafe is now complete. PingSafe represents an important part of SentinelOne’s cloud security future, and I wanted to take this opportunity to outline our journey ahead. More broadly, I will address how and why cloud security often represents the most challenging aspect of enterprise security and is in dire need of an upgrade. 
Cloud As Change
The power of cloud computing and containers is that they can drive business transformation and innovation by enabling greater scale, speed, and reliability in the development and deployment of applications and data pipelines.
However, usage of new technologies can also result in security concerns and an expanded attack surface. There is a tension that exists between security and innovation, and currently, for many companies, security is not balancing out.
One of the most interesting trends of cyber attacks in 2023 was a pivot made by many threat actors to the cloud. This pivot is partly due to an inability of many of their targets to prevent and detect threat activity in their cloud environments.
Some of the high-profile breaches of last year included customized cloud attack techniques to enable ransomware deployments. Notably, Roasted 0ktapus (also known as Scattered Spider), performed sophisticated discovery, lateral movement, persistence, and defense evasion across cloud environments within their attacks.
Beyond targeting cloud infrastructure, threat actors are modifying and disabling cloud services and identities as a part of their attacks.
Additionally, the level of automation within cloud breaches is rising, contributing to increased compromise speeds. Even within readily available open-source toolsets like AlienFox (which SentinelOne Labs reported on here) and Androxgh0st (which the FBI and CISA recently released a TLP:Clear Advisory for), we have seen the inclusion of automated scripts. In these two instances: for persistence and privilege escalation within cloud identity, as well as the manipulation of cloud service provider email services.
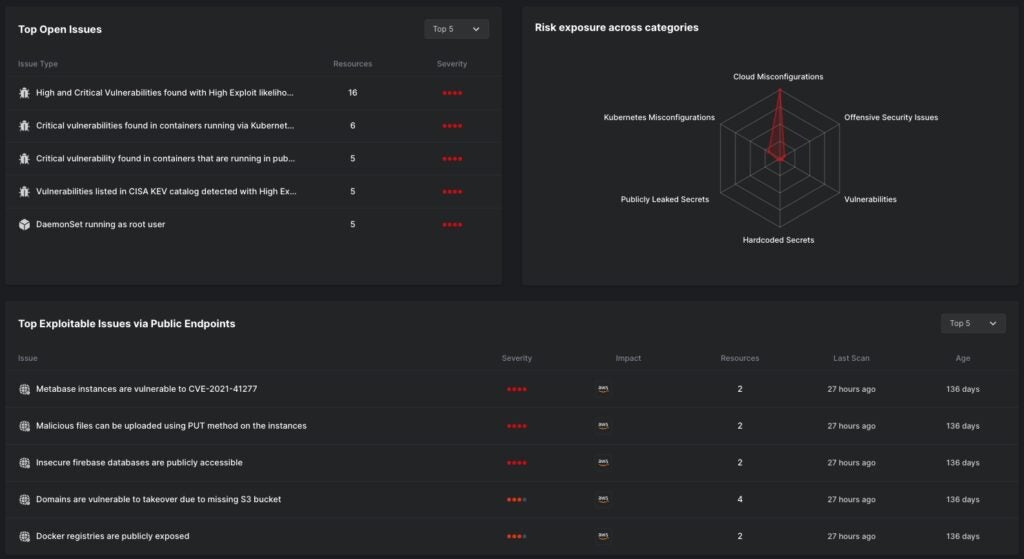
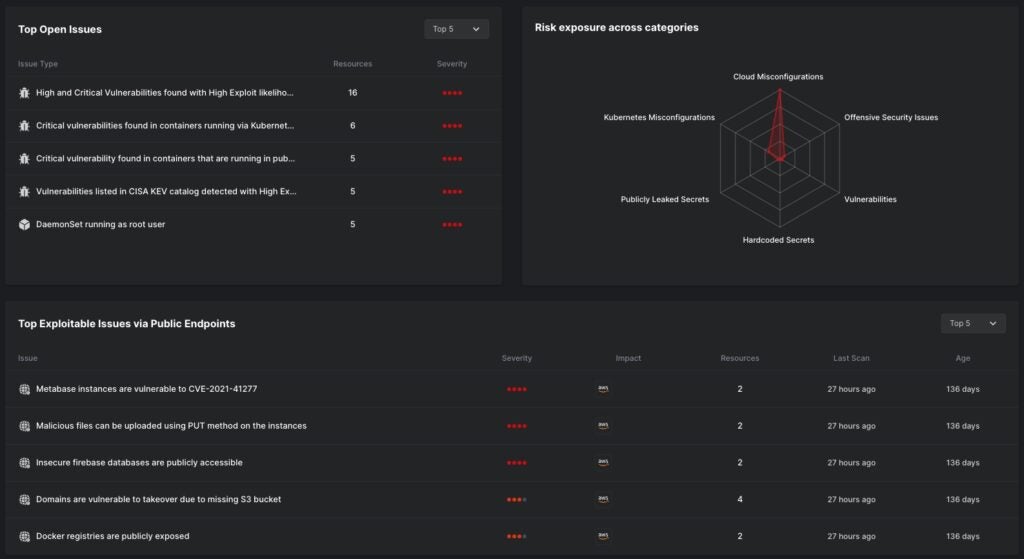
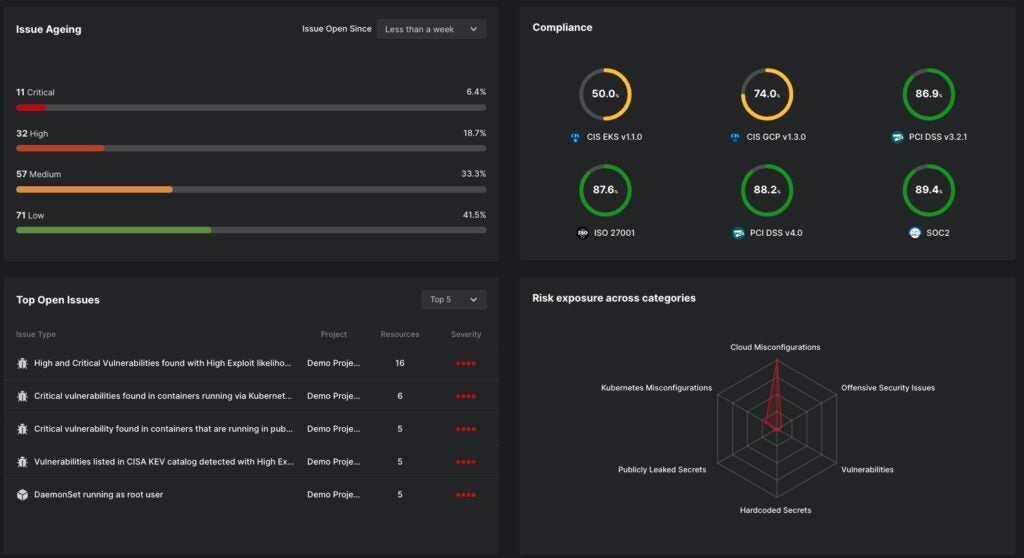
These developments in how threat actors approach cloud environments necessitate a mindshift towards cloud security. For example cloud misconfigurations. With Gartner’s warning in mind that by 2025, 99% of cloud breaches will be due to preventable human error, there has been a rightful focus on identifying, assessing and remediating cloud misconfigurations.
Cloud Security Posture Management (CSPM) capabilities have been key for cloud security practitioners, and Well Architected Frameworks from cloud service providers have been invaluable, the work of comparing ever-changing deployment realities to compliance standards remains a noisy affair with little prioritization.
With threat actors now seen causing misconfigurations themselves, alerts like excessive and changing permissions in Azure AD or AWS IAM may now be compromise artifacts within a greater attack chain. Misconfigurations as a result of threat actor actions can now be indicative of malicious activity already performed, leading to a need to include misconfigurations as compromise artifacts.
Security operations center analysts may now have to work alongside cloud security and infrastructure teams to identify when misconfigurations may represent malicious activity.We should also not forget that before cloud environments are deployed into production, there are increasing threats of supply chain risk within the build pipeline from the use of open-source components. Our colleagues at ReversingLabs recently compiled some excellent reporting on trends specific to this space.
When taken all together, it’s clear that current cloud security tooling can be improved to assist infrastructure and development teams tasked with keeping the cloud safe.
Three Realities of Cloud Security for Today and Tomorrow
As we look at what customers need today and will require tomorrow, three realities quickly emerge. The first reality is that organizations require security and visibility controls across the breadth of their environments, from build pipelines, deployment services, identity and endpoints to cloud infrastructure.
Ideally, these capabilities are provided by a single platform, not only for ease of use and the benefits of using fewer vendors but also because the crucial correlation of security data among these environments is what is needed to drive security innovation to where it needs to be.
The second reality is that while visibility is paramount to security, it cannot be its sole component. Effective cloud security must go further and include the power to block at machine speed and respond. By nature, this necessitates a protection solution that combines the stopping and forensics power of an agent with the speed and breadth of agentless security.
And thirdly, the most important reality is that security must be sustainably achieved and maintained. Nobody needs or has time for noise! With limited resources and constant time pressures, cloud security insights must be prioritized, actionable and false-positive free, and security practitioners require AI assistance to help speed their workflows. Our focus in building a modern, comprehensive approach to cloud security is to deliver a single platform, purpose-built to empower users and deliver visibility, protection, response and remediation capabilities through the cloud lifecycle in real time.
We are approaching this by bringing together our existing agent-based Cloud Workload Security (aka Cloud Workload Protection Platform or CWPP) and Cloud Data Security threat protection products along with our new capabilities from our PingSafe acquisition, which from here on shall be referred to as Cloud Native Security.
Combined they form our comprehensive CNAPP.
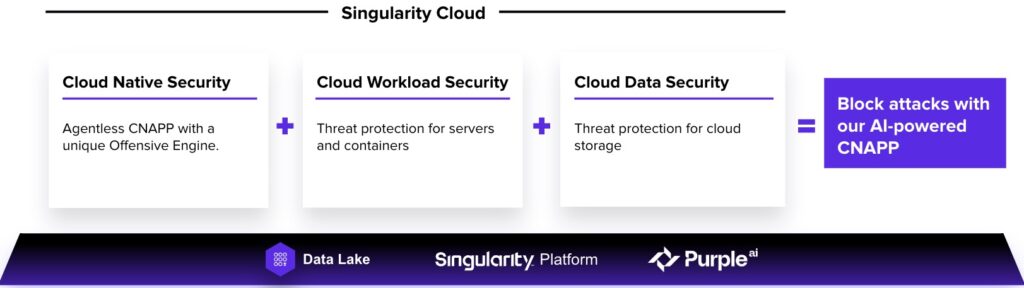
For the mandatory definition after a potentially new acronym, we’ll rely on Gartner:
“.. a unified and tightly integrated set of security and compliance capabilities designed to secure and protect cloud-native applications across development and production”
To understand the outcomes of our comprehensive CNAPP, it is worthwhile using a framework of the four guiding principles it revolves around:
- Visibility across the entire environment
- Action what matters by defending with an attacker’s perspective
- Moving beyond detection to protection
- Being AI-driven
Visibility Across the Entire Environment
Before anything can be achieved, you need visibility. As the saying goes: “you can’t protect what you can’t see”. SentinelOne ensures security teams can manage cloud sprawl with agentless visibility, easily deployed within minutes, combined with integrated endpoint and identity founded on a single platform.
Many attacks start on the endpoint, escalate privileges via identity related attacks, and then move into the cloud. Our customers instantly gain centralized visibility and discovery across multi-cloud, with an asset inventory including mapped relationships between resources.
With views into areas typically reserved for development and infrastructure teams, security is now able to overview the health of container images, Infrastructure as Code (IaC) templates, Kubernetes clusters, and diverse cloud services. This enables security teams to be able to identify and report on misconfigurations, secrets, and malware, and will be able to hunt down unmanaged instances.
The importance of visibility through the cloud lifecycle is to ensure security can be embedded into the build process, in a shift-left style, as well as across crucial production environments.
However, SentinelOne’s comprehensive CNAPP goes a step further, and enables customers to not just shift left, but Respond Left using IaC template scanning and via our partnership with Snyk. This is the ability for a security team to work alongside development and infrastructure teams to apply insights post-incident.
Remediation and response should include pivoting back to the build pipeline to ensure the possibility of re-infection is thoroughly reduced, at the root cause.
Action What Matters by Defending with an Attacker’s Perspective
An unfortunate reality is that noise is now a defining feature of cloud security tooling. A focus on compliance and best practices, while important, leads many security teams unable to differentiate between what is misconfigured or vulnerable according to best practices versus which weaknesses represent likely exploit potential.
SentinelOne’s CNAPP has a revolutionary approach to cutting through this noise – the incorporation of an automated attacker’s perspective. Our Offensive Security Engine simulates attacker methods safely, and validates where your cloud environment is actually exploitable.
This is false-positive free, evidence-based reporting of Exploit Paths that instantly identifies the most crucial risks that require immediate attention. This is the differentiation between a theoretical CVE list of “Where do I start with all these areas I need to fix?” and “What needs to be fixed now?”, and a world of difference in risk management.
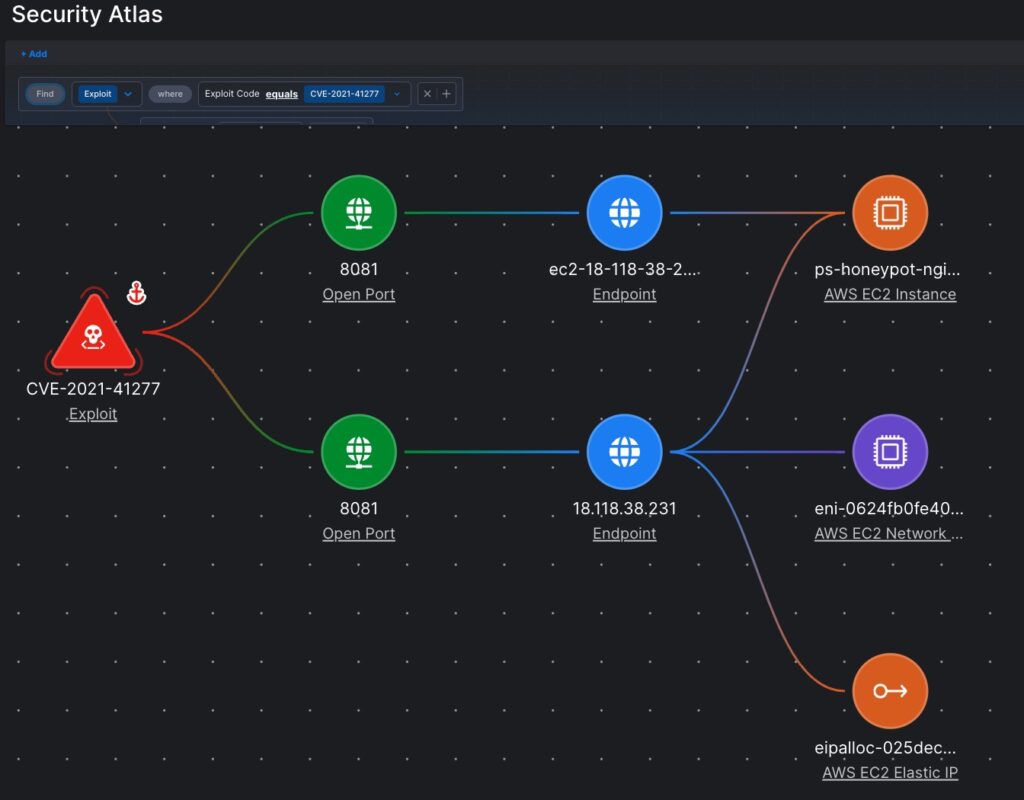
Moving Beyond Detection to Protection
In a world of advanced threats and shortened time frames to breach, visibility alone quite clearly is insufficient. By combining agent and agentless capabilities, SentinelOne is able to pair our in-depth understanding of cloud threats with robust runtime protection. This enables advanced cloud detection and response that includes protection, by blocking threats at machine speed.
For response, rather than relying on time-costly human intervention or self-created automated workflows with limited scope, SentinelOne identifies and kills malicious processes and quarantines files as they run.
This allows security teams to more quickly and efficiently move into the remediation phase of an incident, and perform remedial actions via SentinelOne.
Being AI-driven
AI is everywhere today, but not all AI is equivalent. Layering AI over the top of legacy, siloed tooling will bring some value, but infusing AI and automation into a cohesive platform will yield faster, better results. No one wants 68 agents, 14 consoles showing alert queues, or 3 query languages.
We’ve built the Singularity Platform as the AI-infused foundation that underpins and brings together all of our security solutions, so when we say ONE agent and ONE platform, we mean it. Many vendors will offer you a portfolio, we will deliver the platform.
Our cloud security solutions are built on this single platform, meaning across identity, endpoint, and cloud we can correlate activities in the Singularity Data Lake and use our AI security analyst Purple AI to spot and stop nefarious activities.
What Happens Now?
Now that we have closed the PingSafe acquisition we are rapidly moving to integrate the capabilities into our platform to offer the following capabilities:
- Cloud Security Posture Management (CSPM): Automatically identify misconfigurations, ensuring compliance with industry benchmarks such as NIST, MITRE, CIS, PCI-DSS, and more.
- Agentless Vulnerability Scanning: Discover vulnerabilities across your entire cloud infrastructure without installing any agent.
- Infrastructure as Code (IaC) Scanning: Shift left to identify pre-production issues in IaC templates and container configuration files.
- Kubernetes Security Posture Management (KSPM): Secure containers from code to runtime.
- Secrets Scanning: Detect and prevent cloud credential leakage in public repositories.
- Offensive Security Engine: Use an attacker’s mindset to simulate attacks, verify actual exploit paths and prioritize those issues with breach potential assessments.
We expect to launch Cloud Native Security in mid 2024 as we begin the global rollout phases and will immediately offer customers the ability to run the existing PingSafe solution.
If you would like to see how Cloud Native Security provides rapid visibility and prioritized false-positive free, evidence-based reporting and actionable insights, or if you would like to ensure your critical cloud workloads are secured with machine speed protection with our Cloud Workload Security, contact us or request a free demo.
如有侵权请联系:admin#unsafe.sh