
2024-2-6 13:0:0 Author: checkmarx.com(查看原文) 阅读量:22 收藏
In the evolving landscape of cybersecurity, a new threat has emerged, targeting the core of software development processes. Recently, an alarming incident has brought to light a significant vulnerability in Jenkins CI/CD servers. Approximately 45,000 Jenkins servers have been left exposed to remote code execution (RCE) attacks, leveraging multiple exploit public POCs https://github.com/h4x0r-dz/CVE-2024-23897 https://github.com/binganao/CVE-2024-23897. This breach is not just a standalone event but a symptom of a growing trend of attacks on Continuous Integration/Continuous Deployment (CI/CD) software supply chains.
The significance of this vulnerability
Exploiting this widespread vulnerability can do more than just initial access gleaned by exploiting the Jenkins CVE, it can also put the software consumers of this company affected, at immediate risk.
Software developers use Build servers’ software to manage and automate software compilation, building, testing, and releasing. If compromised, access to a build server would provide malicious actors with access to that software developer’s source code, signing certificates, and the ability to subvert software compilation and deployment processes—access a malicious actor could further use to conduct supply chain operations.
The attraction of software supply chain attacks for attackers lies in their high reward potential and the extensive reach these attacks can have. By infiltrating a single, often well-trusted component of the software supply chain, attackers can gain access to a broad network of systems and data, making these attacks increasingly favored due to their far-reaching and often catastrophic ripple effects.
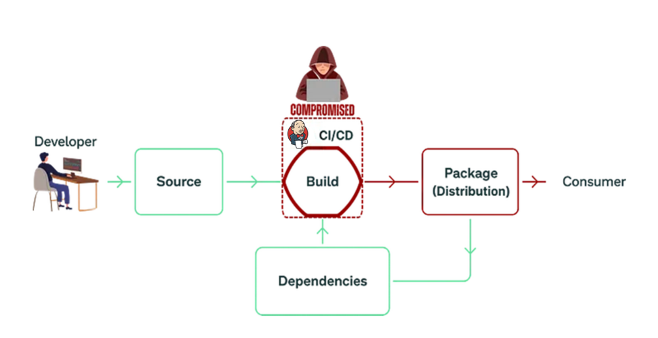
The growing trend of attacks on Continuous Integration/Continuous Deployment (CI/CD) software supply chains
This attack comes after a highly publicized attack on another CI/CD server TeamCity software https://nvd.nist.gov/vuln/detail/cve-2023-42793 this attack was attributed by CISA to Russian Foreign Intelligence Service (SVR) https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-347a and also to multiple North Korean threat actors https://www.microsoft.com/en-us/security/blog/2023/10/18/multiple-north-korean-threat-actors-exploiting-the-teamcity-cve-2023-42793-vulnerability/. We believe that this public vulnerability will also be used by Nation-state actors to strengthen their control on sensitive software supply chain.
Beyond traditional security measures
In the wake of sophisticated cyber-attacks like those attack, the limitations of traditional security tools such as antivirus software and intrusion detection systems become apparent. These tools, foundational for baseline security, are tailored to address known threats and vulnerabilities. However, their capacity to handle advanced cyber-attacks targeting software distribution mechanisms is limited. Such attacks often bypass perimeter defenses and exploit subtleties in software delivery systems, highlighting gaps in conventional security measures.
The shortcomings of traditional approaches are further exemplified by tools like the Software Bill of Materials (SBOM). Although an SBOM is invaluable for transparency and tracking component vulnerabilities, it falls short in safeguarding against manipulations within the distribution process itself. This gap highlights the need for a more comprehensive approach to cybersecurity.
Responding to these evolving threats necessitates a multifaceted security strategy. This involves complementing traditional measures with advanced and dynamic approaches. Implementing comprehensive vulnerability management, real-time threat detection systems, and continuous monitoring within the software development and deployment pipelines can provide a more robust defense.
A call to action for AppSec managers
Considering these growing threats, the role of Application Security (AppSec) Managers becomes more crucial than ever. The recent incidents involving Jenkins and TeamCity serve as stark reminders of the vulnerabilities inherent in the software supply chain. To combat this, AppSec Managers must ensure that their Software Supply Chain Security Solutions are not just robust but also backed by leading-edge research teams. It’s not enough to have strong defenses; staying ahead of the curve in terms of threat intelligence and technological advancements is key to safeguarding against such sophisticated attacks.
In conclusion, the cybersecurity community must view the incidents with Jenkins and TeamCity as a clarion call. The increasing frequency and sophistication of attacks on CI/CD platforms demand a proactive and comprehensive approach to security. It's a complex challenge, but with the right strategies and tools, organizations can protect themselves and their customers from these looming threats. As the digital world continues to evolve, so must our defenses against the ever-changing landscape of cyber threats.
如有侵权请联系:admin#unsafe.sh