2024-2-16 00:36:11 Author: blog.qualys.com(查看原文) 阅读量:22 收藏
Welcome to a critical exploration of the 2023 Cyber Vulnerability Landscape, with a specific focus on the escalating threat of ransomware. I have previously shared the broader results we found in evaluating the 2023 threat landscape; this is now a deeper dive into what the data reveals specifically about ransomware.
In this rapidly evolving cybersecurity environment, understanding the nuances of ransomware attacks and their underlying vulnerabilities is crucial for robust defense strategies. This post provides practical guidance on understanding ransomware threats and outlines strategies to effectively counter them, focusing on the vulnerabilities identified in 2023 that were exploited in ransomware attacks.
Understanding Ransomware in the Current Cybersecurity Context
In 2023, an alarming 28,834 vulnerabilities were recorded, marking a significant 13% increase from the previous year. This statistic paints a vivid and concerning picture of the escalating cybersecurity challenges faced on a global scale.
Among these vulnerabilities, a critical subset is increasingly exploited in ransomware attacks. Even though only 0.07% of these vulnerabilities are involved in ransomware attacks, they play a pivotal role in shaping the ransomware landscape.
Ransomware indiscriminately targets many products, from ubiquitous platforms like Microsoft Windows to specialized ones such as Atlassian Confluence Data Center and Citrix NetScaler ADC. This extensive range, including Qlik Sense Enterprise, Apache ActiveMQ, Fortran GoAnywhere MFT, etc., underscores the far-reaching and non-discriminatory nature of ransomware threats.
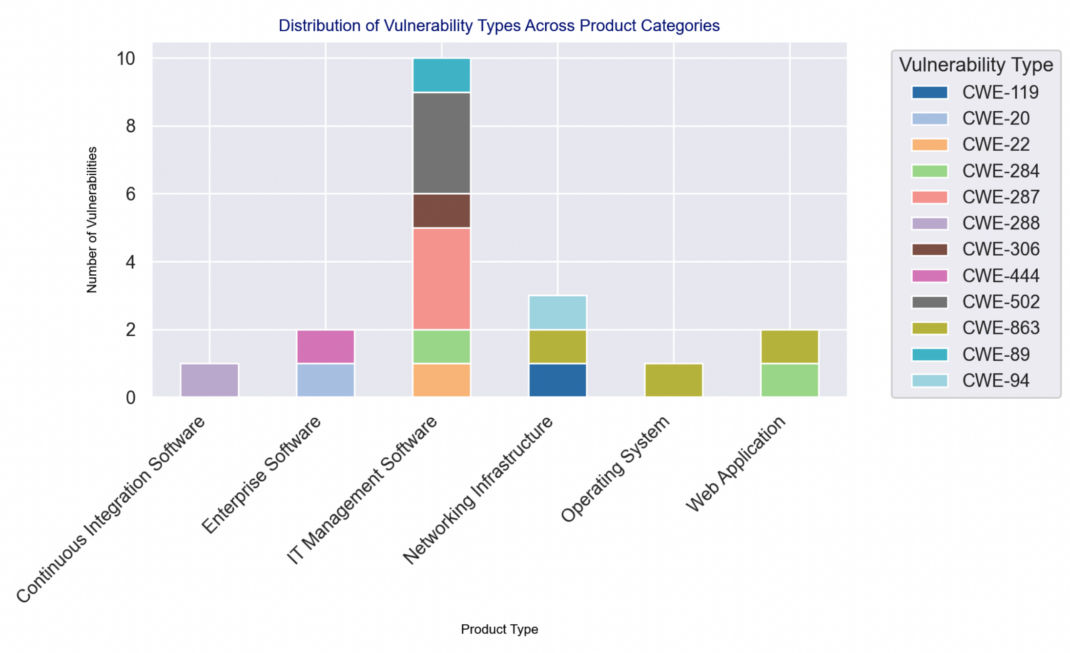
Understanding the Diverse Targets of Ransomware
Ransomware attacks are diverse, impacting everything from operating systems to web applications and networking infrastructure. This diversity indicates the sophisticated and strategic nature of ransomware attackers. Ransomware often exploits Remote Code Execution (RCE) and Privilege Escalation vulnerabilities, allowing attackers to gain control and execute malicious activities within victims’ systems. Attackers target fundamental aspects of software, exploiting deep-rooted vulnerabilities, stressing the urgent need for secure software development and effective patch management practices.
Shifting to an optimistic note, a considerable portion of vulnerabilities can be effectively mitigated through patch management. This system is not merely a fix-it tool but a proactive defense mechanism. By focusing on patch management, we can significantly address a substantial chunk of cybersecurity threats, particularly those prevalent in critical areas like Operating Systems, to bolster our defenses against potential breaches.

Another vital aspect that aids us in decoding targeting patterns is using Common Weakness Enumeration (CWE) identifiers. These identifiers serve as a systematic categorization of vulnerabilities, grouping them based on the nature of the flaws in software development that it exploited. This categorization simplifies the understanding of vulnerabilities and highlights common areas where security can be enhanced to thwart ransomware attacks. These frequently fell into the following critical categories:
- CWE-284 (Improper Access Control)
- CWE-287 (Improper Authentication)
- CWE-502 (Deserialization of Untrusted Data)
- CWE-863 (Incorrect Authorization)
Addressing these specific weaknesses is crucial for strengthening defenses against ransomware attacks.
Ransomware Trends and Defense Strategies
Given the frequency of ransomware attacks on public-facing applications, securing these platforms more robustly than ever before is imperative. The varied tactics ransomware attackers employ call for a multi-layered defense strategy designed to counter different stages of an attack. This necessity is further amplified by the fact that many ransomware attacks exploit known vulnerabilities, spotlighting the critical importance of regularly updating systems with the latest patches.
The Impact of Generative AI on Ransomware Dynamics
Generative AI is set to revolutionize the cyber threat landscape by making it easier for cybercriminals to discover and exploit vulnerabilities, leading to more frequent and sophisticated ransomware attacks. This advancement lowers the technical hurdles for attackers, enabling them to target a more comprehensive array of products and exploit zero-day vulnerabilities more adversely. It also necessitates a multifaceted defense strategy, robust vulnerability management, and urgent investment in advanced cybersecurity measures to safeguard against the growing threat posed by the enhanced capabilities of threat actors using generative AI.
The Critical Role of Patch Management in Combating Ransomware
Effective patch management can significantly mitigate the threat posed by ransomware. By addressing the vulnerabilities promptly, organizations can safeguard their systems against potential ransomware breaches. This section will delve into how effective patch management is a key weapon in the fight against ransomware.
A crucial element of this process is the “patch rate,” which plays a pivotal role in cybersecurity. It measures how quickly a system addresses vulnerabilities. A high patch rate ensures a quick and efficient response to threats, reducing risk. On the other hand, a low patch rate suggests a delayed reaction, increasing the system’s exposure to cybersecurity risks.
We utilized data on patches and Mean Time to Remediation (MTTR) for ransomware vulnerabilities in 2023 to demonstrate patch management’s effectiveness in organizational defense. The data, analyzed by the Qualys Threat Research Unit (TRU), underwent meticulous anonymization. This process guarantees that subsequent analyses remain untraceable to specific organizations or assets, ensuring confidentiality and security.
The urgency of effective patch management is further emphasized by the 2023 Qualys TruRisk Research Report findings. According to this report, weaponized vulnerabilities are typically patched within 30.6 days, but this occurs only 57.7% of the time. In contrast, attackers often weaponize these vulnerabilities in just 19.5 days. This creates a critical window of approximately 11.1 days, during which attackers can exploit these vulnerabilities before organizations initiate patching efforts. This stark discrepancy highlights the necessity for timely patch management as part of cybersecurity strategies, emphasizing the importance of minimizing the window weaponized vulnerabilities are unpatched in order to enhance security.
Mastering the Zones of Vulnerability Management
Having established the importance of patch management and its components, such as patch rate and MTTR, we now transition to a more detailed exploration of how these concepts play out in real-world scenarios. The upcoming section presents a framework that breaks down the complexity of vulnerability management into four distinct zones. Each zone represents a combination of patch rate and remediation time, offering insights into various strategies and their implications in enhancing cybersecurity measures. The chart below displays a detailed analysis of vulnerabilities associated with ransomware attacks, and each circle on the chart represents an individual vulnerability, illustrating its patch rate and MTTR.

Let’s examine these four quadrants:
Effective patch management is essential in cybersecurity and can be understood through the following:
- Vigilant Alert Zone (Top Right): Here, the vulnerabilities are addressed quickly (high patch rate), but they take a long time to fully resolve (long remediation times). It’s like firefighters arriving swiftly at a blaze but taking time to extinguish it completely.
- Optimal Security Zone (Bottom Right): This is where we aim to be. Vulnerabilities in this zone are patched swiftly and resolved quickly – a hallmark of effective vulnerability management.
- Critical Attention Zone (Top Left): A red flag area. Vulnerabilities here have low patch rates and long remediation times, posing serious security risks.
- Underestimated Risk Zone (Bottom Left): Here lie the overlooked vulnerabilities – those with low patch rates but surprisingly short remediation times. They are the hidden dangers, often ignored until they suddenly become critical.
By understanding and applying these principles, we can better prioritize risks and enhance our defenses against complex cyber threats. The battle against ransomware is crucially dependent on efficient patch management, highlighting the importance of the rapid and consistent application of patches for organizations. Prioritizing these strategies helps close vulnerability gaps and strengthen defenses against advanced ransomware threats. This proactive approach is not just a technical necessity but a fundamental pillar in securing our digital environment.
Conclusion
The 2023 cyber threat landscape, dominated by the rise of sophisticated ransomware attacks, demands an informed and proactive approach to cybersecurity. By understanding these threats and implementing targeted strategies, organizations can significantly bolster their defenses against ransomware.
Stay ahead in the battle against ransomware by staying informed and prepared. Keep an eye out for more insights, strategies, and updates on effectively combating ransomware threats.
如有侵权请联系:admin#unsafe.sh