2020-02-17 17:47:15 Author: medium.com(查看原文) 阅读量:632 收藏
Assignment :
During a pentest, i was auditing a web application which hosting documents and files in order to share it between the the employees (like SharePoint).after finding some XSS/CSRF bypass, there was a feature of uploading Microsoft document like .Docx.
at that moment i remember one of my friend who hacked into Facebook server just by uploading his resume with embed XML code.
Thanks to @bbuerhaus and @nahamsec for making life much easier by hosting an XXE service which can generate the Microsoft files with XXE pre- defined payload.
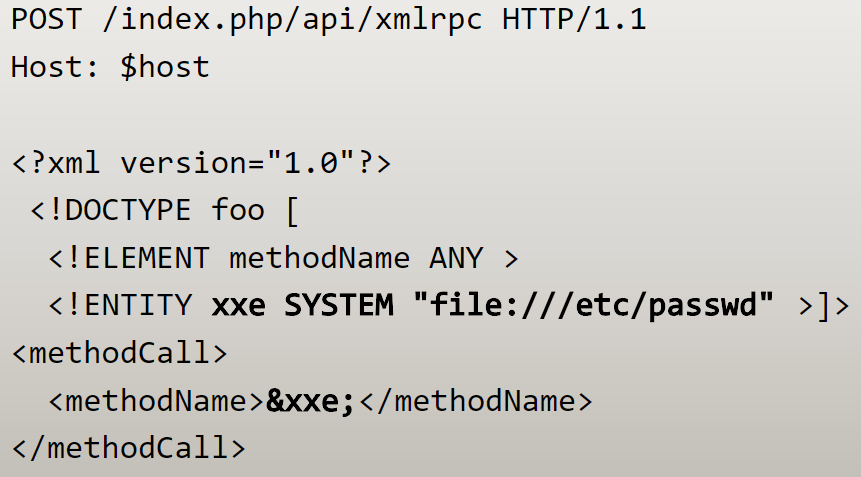
my first payload looks like :

and at that moment i was astonished because i got a hit from the server who handle the authentication WTF !!

now, i got a nice XXE but wait ..what i can do ?
i knew that i was dealing with windows system …so i could’t for example read interesting path like /etc/passwd in Linux only thing was possible /windows/win.ini …but we could do better right ;)
my dear friend @topotam77 was sitting just near to me and he told me at that time :
“the most important thing about windows is NTLM hashs”
it’s was a like brilliant idea because with some hope we can play with theses hashes, so let’s drop this arrow and see where it will stick;)
this time i changed my payload pointing to my sharing IP address :

and B00M :D

hein what else ?
well backing to the enumeration phase, which i was able to identify other servers (handle the same role for a different environment ) from SSL certificate scanning, and the most important that the SMB messages were not signing !!
arming with these info, let’s rock and roll with SMBrelay :
- first let’s try to do some basic RCE : (Ping)

got a hit in my machine :)

- not satisfied …let create a user :)

after putting it on the Admin group i could do an RDP on the server :)

- well, at that moment i didn’t know that Impacket comes with nice feature which try to dump the SAM file if we just point the IP of the relaying server without any argument :

- at this point : i had the administrator hash …then is there any chance we could leverage our attack ? the answer is yes :)
let drop our hash in the network and see what we’ve got ;)
with smb scan module in Metasploit, i got 41 hits which great :)
- after using PSExec exploit on of these servers, one of them took my complete attention :

i remember my self when i saw the output of this command :

B00M !!
this account was a member of domain Admins , let’s impersonate his session by creating another user but this time : member of domain admin ;)


let’s verify our right :

with this account i could access to all the DC, PC and even dump the NTDS.DIT file which contain all the hashes of the users :D
如有侵权请联系:admin#unsafe.sh